En savoir plus sur la plateforme de défense Cybereason
Découvrez les fonctionnalités complètes de prévention, de détection et de réponse proposées par notre plateforme.
Lire la fiche techniqueAu-delà des flux d'alertes incessants, la plateforme Cybereason Defense détecte, analyse et met fin aux opérations malveillantes avant qu'elles ne prennent racine, permettant ainsi la neutralisation des cyberattaques en quelques minutes.
Une protection unifiée depuis les endpoints et dans tout le réseau d'entreprise




Cybereason Prevention employs a multi-layered approach that includes intelligence-based convictions to block known threats and machine learning algorithms that analyze behavioral and static attributes to instantly block fileless attacks, new malware and ransomware variants, and other novel threats.
prev
next
Cybereason Endpoint Controls delivers efficient management of specific policies, personal firewalls, and whole disk encryption across a range of device types to satisfy the strictest compliance requirements and protect sensitive data in the case of an incident or lost device.
prev
next
Cybereason EDR consolidates intelligence about each attack into a contextualized view of the full attack narrative to deliver correlated attack data in an easy-to-read, interactive graphical interface called a Malop (malicious operation) which allows implementation of remediation actions automatically or manually with a click of the mouse.
prev
next
Cybereason Mobile provides behavior-based prevention designed to detect a variety of threats including malicious app usage, suspicious north-south network connections, and a range of critical operating system vulnerabilities with no user training required, no custom rules to develop, and no signature updates or manual analysis required.
prev
next
The Cybereason Defense Platform enables your development and security teams to protect critical workloads against emerging threats and undiscovered vulnerabilities with a lightweight agent that protects your organization's public, private and hybrid cloud deployments along with on-premises data centers all managed through a single console.
prev
next
The Cybereason Nocturnus team continuously monitors the globe to proactively uncover the latest malicious operations, sophisticated threat actors, new attack methodologies and exploitable vulnerabilities so your team is prepared for emerging threats as well as provides the technical expertise for rapid containment and incident response.
prev
next
Cybereason XDR (extended detection and response) is a force multiplier for investigations into malicious operations (Malops) and delivers enhanced correlations across both Indicators of Compromise (IOCs) and more subtle Indicators of Behavior (IOBs) from across the entirety of your organization’s network whether the devices are on-premises, mobile, or in the cloud.
prev
next
The Cybereason Defense Platform delivers the rich context and event correlations for performing in-depth threat hunting to uncover even the most complex attacks, making the Cybereason Defense Platform the nexus of threat intelligence, enhanced visibility, and event correlations required to ensure a proactive security posture.
prev
next
Cybereason can quickly review your infrastructure, systems, and applications to identify instances of compromise, backdoors, unauthorized access, and anomalous activities.
prev
next
A Cyber Posture Assessment provides actionable intelligence about your organization's security operations program and actionable recommendations to improve your defense.
prev
next
Cybereason has assembled a global team of security experts with decades of incident response experience and domain knowledge in threat hunting, forensic analysis, malware analysis and reverse engineering, new system vulnerabilities, SIEM/SOC management, and more to bring about a swift resolution to cyber attacks.
prev
next
Cybereason Managed Detection and Response delivers prevention, detection, and response capabilities as a service, allowing you to uncover the most sophisticated and pervasive threats without managing it yourself.
prev
next
Cybereason is operation-centric instead of alert-centric. We instantly deliver fully contextualized and correlated insights into any MalopTM (malicious operation), detailing the full attack story from root cause to impacted users and devices, significantly reducing investigation/remediation periods from days to minutes.

Cybereason Prevention employs a multi-layered approach that includes intelligence-based convictions to block known threats and machine learning algorithms that analyze behavioral and static attributes to instantly block fileless attacks, new malware and ransomware variants, and other novel threats.
prev
next
Cybereason Endpoint Controls delivers efficient management of specific policies, personal firewalls, and whole disk encryption across a range of device types to satisfy the strictest compliance requirements and protect sensitive data in the case of an incident or lost device.
prev
next
Cybereason EDR consolidates intelligence about each attack into a contextualized view of the full attack narrative to deliver correlated attack data in an easy-to-read, interactive graphical interface called a Malop (malicious operation) which allows implementation of remediation actions automatically or manually with a click of the mouse.
prev
next
Cybereason Mobile provides behavior-based prevention designed to detect a variety of threats including malicious app usage, suspicious north-south network connections, and a range of critical operating system vulnerabilities with no user training required, no custom rules to develop, and no signature updates or manual analysis required.
prev
next
The Cybereason Defense Platform enables your development and security teams to protect critical workloads against emerging threats and undiscovered vulnerabilities with a lightweight agent that protects your organization's public, private and hybrid cloud deployments along with on-premises data centers all managed through a single console.
prev
next
The Cybereason Nocturnus team continuously monitors the globe to proactively uncover the latest malicious operations, sophisticated threat actors, new attack methodologies and exploitable vulnerabilities so your team is prepared for emerging threats as well as provides the technical expertise for rapid containment and incident response.
prev
next
Cybereason XDR (extended detection and response) is a force multiplier for investigations into malicious operations (Malops) and delivers enhanced correlations across both Indicators of Compromise (IOCs) and more subtle Indicators of Behavior (IOBs) from across the entirety of your organization’s network whether the devices are on-premises, mobile, or in the cloud.
prev
next
The Cybereason Defense Platform delivers the rich context and event correlations for performing in-depth threat hunting to uncover even the most complex attacks, making the Cybereason Defense Platform the nexus of threat intelligence, enhanced visibility, and event correlations required to ensure a proactive security posture.
prev
next
Cybereason can quickly review your infrastructure, systems, and applications to identify instances of compromise, backdoors, unauthorized access, and anomalous activities.
prev
next
A Cyber Posture Assessment provides actionable intelligence about your organization's security operations program and actionable recommendations to improve your defense.
prev
next
Cybereason has assembled a global team of security experts with decades of incident response experience and domain knowledge in threat hunting, forensic analysis, malware analysis and reverse engineering, new system vulnerabilities, SIEM/SOC management, and more to bring about a swift resolution to cyber attacks.
prev
next
Cybereason Managed Detection and Response delivers prevention, detection, and response capabilities as a service, allowing you to uncover the most sophisticated and pervasive threats without managing it yourself.
prev
next
Cybereason is operation-centric instead of alert-centric. We instantly deliver fully contextualized and correlated insights into any MalopTM (malicious operation), detailing the full attack story from root cause to impacted users and devices, significantly reducing investigation/remediation periods from days to minutes.
Tirez profit d'un système de sécurité centré sur les opérations qui fournit des visualisations des séquences d'attaques riches en contexte et corrélées à la cause première sur chaque appareil et utilisateur touchés.
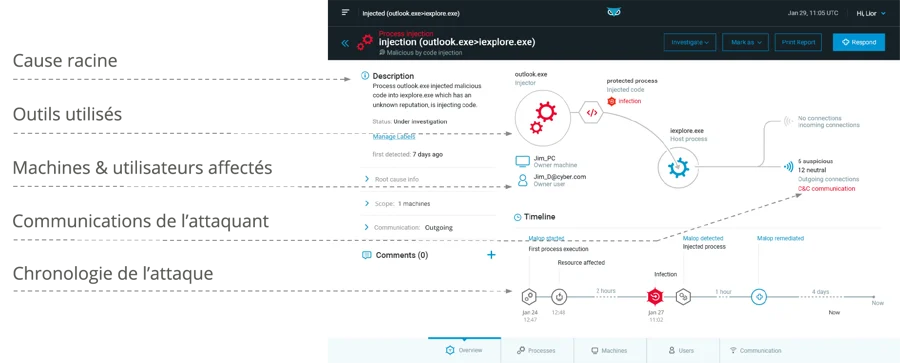
Chaque semaine, Cybereason compile 9,8 Po de données pour comprendre et retracer l’historique d'une attaque, de la cause première aux endpoints et utilisateurs affectés.
Cybereason réduit les délais d’investigation jusqu’à 93 % de sorte que les défenseurs puissent éliminer les menaces en quelques minutes au lieu de plusieurs jours.
Offrant une efficacité accrue, Cybereason permet à un seul analyste de gérer jusqu’à 200.000 endpoints, grâce à des remédiations automatisées ou guidées d'un simple clic.
Outrepassez les limites des antivirus traditionnels grâce à un système de prévention multicouches qui comprend le NGAV, l’analyse comportementale, le machine learning et les leurres, le tout relié au cyber-renseignement.
Découvrez la prévention des endpointsUne protection complète, conçue pour contrer tous types d’attaques sur les endpoints distants, sur site et sur les déploiements dans le cloud.
Découvrez les options de déploiementCorrélez le contexte d’une attaque sur tous les endpoints, via un agent léger unique et des signalements en temps réel, vous permettant de neutraliser la menace avant qu'elle n'infiltre votre infrastructure.
Découvrez la solution EDRRenforcez votre équipe de sécurité grâce à nos services de détection et de réponse gérées (MDR) qui traquent proactivement les menaces, surveillent les activités malveillantes et interceptent les attaques afin de préserver la sécurité de votre infrastructure.
Découvrez la solution MDRComptant parmi les meilleurs analystes mondiaux du cyber-renseignement, l’équipe Nocturnus de Cybereason travaille sans relâche pour dénicher les menaces émergentes et neutraliser les opérations malveillantes.
Découvrez NocturnusIdeal For
Data Sheet
Découvrez les fonctionnalités complètes de prévention, de détection et de réponse proposées par notre plateforme.
Lire la fiche technique