With over 1,100 employees and 2,100 endpoints, Olist needed to gain visibility into their attack surface, and staff to investigate and respond to incidents. Learn how a combination of the Cybereason Defense Platform and MDR services increased visibility and led to security performance improvements.
Read NowENDPOINT
CONTROLS
Cover security requirements and address compliance needs with controls tied to different types of devices, implement personal firewall policies, and audit disk encryption.
Why Cybereason Endpoint Controls?
Securely Manage Every Endpoint
Satisfy strict security, compliance and access control requirements to protect sensitive data in the event of an incident or lost device.
Centralized Policy Enforcement
One console provides a granular view of controls across each endpoint through a single agent for prevention, EDR and analytics capabilities.
It's All About Real Control
Empower security teams to control inbound and outbound network connections and create custom rules for your organization’s unique processes.
Key Capabilities
Securely Manage Endpoints
Manage specific policies, maintain a granular view of device controls, the implementation of personal firewalls and to take an audit of whole disk encryption across a range of device types. These features help satisfy the strictest of security, compliance and access control requirements to protect sensitive data in the case of an incident or lost device.
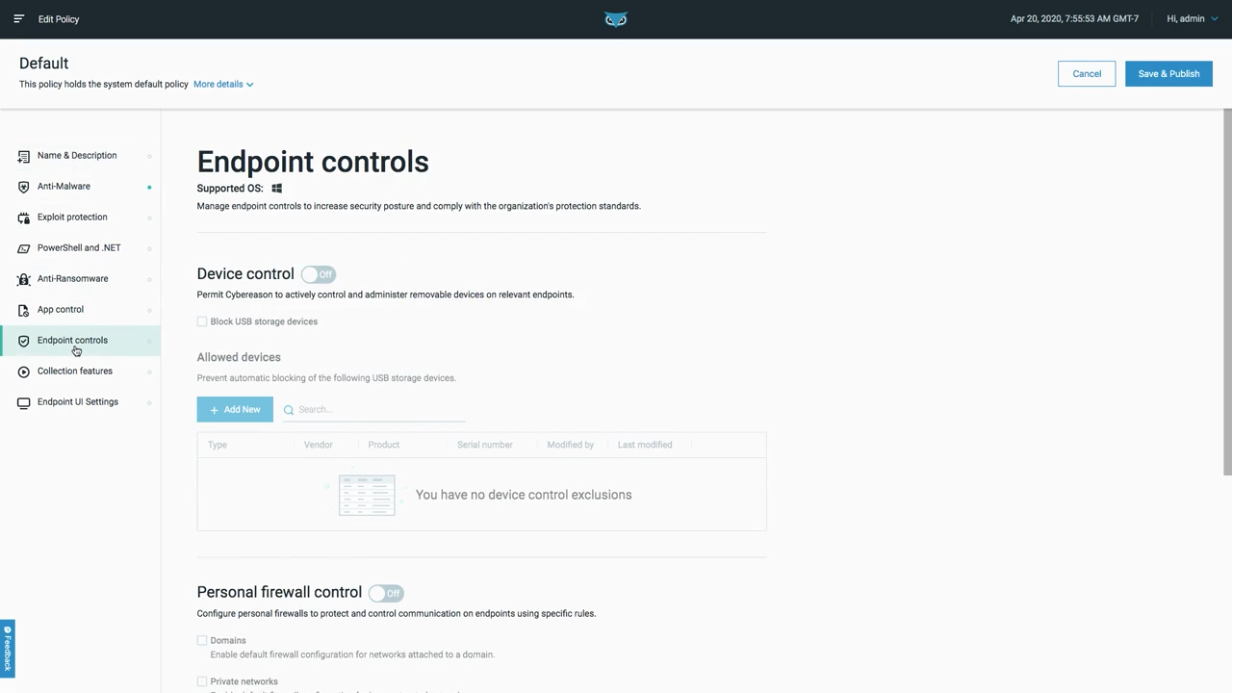
Granular Endpoint Controls
With Cybereason Endpoint Controls, security and compliance teams can manage all policies within a single UI to realize a consolidated policy administration workflow that provides security administrators a granular view into what policies are in place at the individual device level.
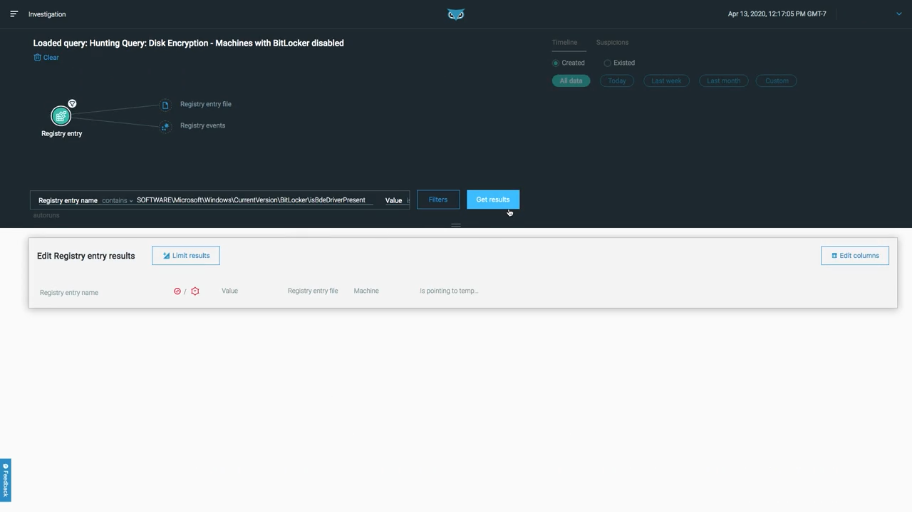
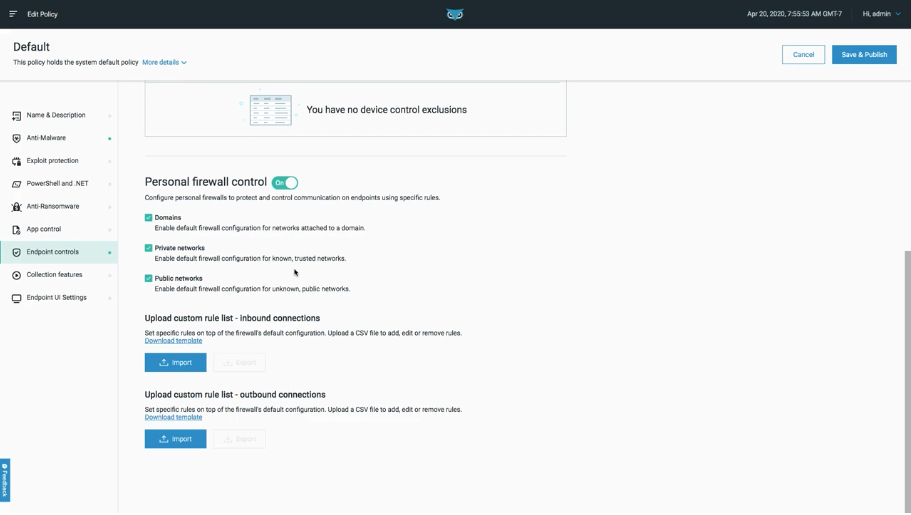
Security With Compliance
With Cybereason Endpoint Controls, your security and compliance teams are able to enforce a Zero Trust approach with the option to swiftly isolate compromised devices. Security teams can also restrict both inbound and outbound network connections and create custom rules to fit your organization’s unique business processes.
Related Resources
Download the results summary to see why Cybereason is the only security vendor that provides unparalleled attack protection by combining 9 independent prevention layers, ensuring that your business achieves its goals, and bad actors don’t.
Read the ResultsCybereason makes sense of complex data relationships and behaviors to stitch together the separate components of an attack, including all users, devices, identities, and network connections into an operation-centric view we call The MalOp™.
Learn More