Research by: Assaf Dahan and Joakim Kandefelt
Executive Summary
For more than a decade, Brazil has been considered a major contributor to global cybercrime. Countless security reports have detailed a plethora of nefarious activities linked to Brazilian threat actors, who mainly target the financial and private sector. Brazil is particularly known for being home to huge botnets that send out spam and phishing emails and proliferate infostealers and banking Trojans. After India and China, Brazil is the world's third worst botnet infected country, according to The Spamhaus Project.
In 2018, Cybereason’s Nocturnus team analyzed numerous campaigns related to several Brazilian financial malware. This blog shows the pervasiveness of these Brazilian-made malware, which target online banking customers of over 60 banks in nearly a dozen countries throughout Latin America, Spain and Portugal. This blog continues research presented in our earlier blog and maps the evasive infection and delivery methods used by Brazilian threat actors in order to distribute malware.
MAPPING RECENT BRAZILIAN FINANCIAL MALWARE DELIVERY METHODS
The campaigns, which target customers of more than 60 banks worldwide, deliver different kinds of financial malware. Antivirus vendors have assigned this type of malware generic names like: Banload, Banbra, Bancos, Boleto, Delf and Spy.Banker. Despite the variation in the final malware payload, Cybereason identified three key stages that were common to most of the attacks involving Brazilian financial malware.
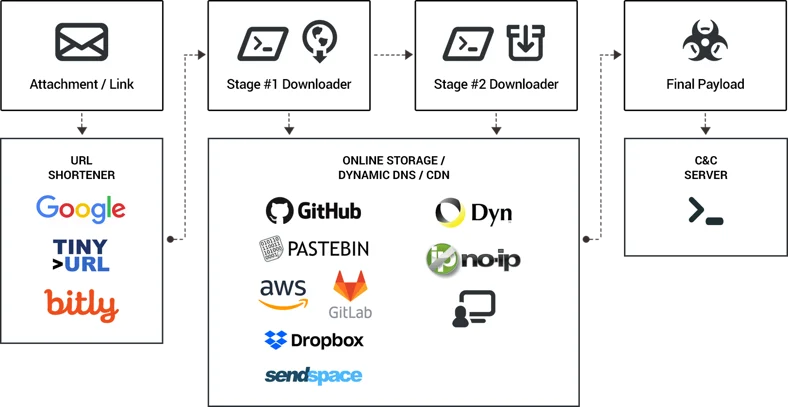
The multi-stage delivery infrastructure helps attackers to minimize the risk of detection. By implementing various evasive techniques, the attackers successfully bypass signature/heuristic-based engines, thus ensuring the delivery of the final malware. While the multi-stage delivery approach is not new in cybercrime, its adoption by Brazilian threat actors has proven to be highly effective at evading many anti-virus products, as demonstrated by the low detection rate presented in our research.
In each stage, we observed commonalities in the tools, techniques and procedures (TTPs) that are shared across campaigns. These TTPs include:
- Social engineering as an entry point
- Multiple redirections via URL shorteners and the usage of Dynamic DNS services
- Payloads hosted on legitimate online storage services and CDNs (content delivery networks)
- Obfuscated PowerShell downloaders employing command-line logging evasion
- Living off the land techniques that abuse Microsoft-signed binaries
- Abusing trusted applications via DLL hijacking
- Splitting the main payload into two or more components
Related Post-infection Malware
Our research revealed interesting aspects of the Brazilian malware ecosystem. We observed different types of Brazilian malware being used in conjunction by the same threat actor. In some of the endpoints infected with Brazilian financial malware, we noticed additional Brazilian-made malware, such as infostealers, cryptocurrency miners and a malware that steals data from Microsoft Outlook. This finding gives us a glimpse into the different ways in which threat actors can capitalize on previously gained foothold, in order to increase their potential profits.
Brazilian-made Malware, Spanish-Speaking Targets
Discussing Brazilian financial malware may imply that this threat only targets Brazilian online banking customers, but our research clearly shows that Brazilian threat actors have expanded their operation to Spanish-speaking countries in Latin America and Spain.
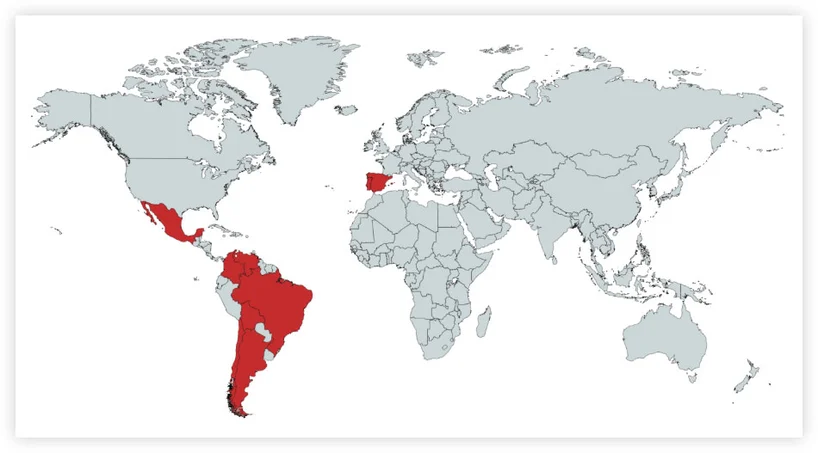
Based on the data from recent campaigns, Spain is the most second targeted country after Brazil. Other countries targeted in recent campaigns include Mexico, Argentina, Venezuela, Colombia, Bolivia and Chile.
Our research demonstrates how different types of Brazilian-made malware, originally designed to target Brazilian banking users, were repurposed to target other countries and their respective regional banks. We observed references to more than 60 banks embedded within the malware's code. (See the list of targeted banks in this section).
One Source-code, Many variants
Cybereason analysts were able to trace the origin of various Brazilian malware to a Remote Access Tool (RAT), whose source code is publicly available on Github. While the identity of the author is known, there is no proof that this author has a direct link to the financial malware discussed in this blog. Cybereason estimates that the publicly-available source code was repurposed by different threat actors who later added banking modules as well as anti-analysis features, that were present in the financial malware analyzed in this blog.
Table of Contents
Multi-Stage Delivery Infrastructure
Chained Delivery: an Evasive Network Pattern
Main Entry Point: Phishing Emails
Stage #1: Obfuscated Downloader Scripts
Evading Command-line Detection using Environment Variables
Living Off the Land: Abusing Microsoft-Signed Applications
Stage #2: PowerShell Downloader
Stage #3: Main Payload Execution
Abusing Trusted Applications via DLL-Hijacking
Splitting the Payload - Because Two is Better than One!
Using Rundll32.exe to execute the Main Payload
Related Post-Infection Payloads: Outlook Malware & InfoStealers
Distribution of Additional Malware
Brazilian-made Malware, Spanish-Speaking Targets
Brazilian-Made Malware, Originally made to target Brazilian Users
Back to the Source: Open-Source RAT, Many Variants
Multi-Stage Delivery Infrastructure
Over the course of 2017-2018, Cybereason observed many variations to the infection flow. However, there seems to be a basic formula that most infections adhere to:
Infection Vector: The infection chain starts with a phishing email masquerading as a legitimate business invoice. The email body usually contains either a link or an attachment (pdf, zip, batch script, html) that will fetch or run the first stage downloader.
Stage 1 - Downloader: An obfuscated script or downloader command (.cmd, .lnk, .vbs, .js) is used to download the second stage payload. The downloader often points to a shortened URL that redirects to a Web hosting service, dynamic DNS or CDN to fetch the second stage payload.
Stage 2 - Downloader: Mostly an obfuscated PowerShell script that downloads the main payload. In some cases the second stage downloader has additional functionality, such as creating persistence and performing anti-analysis checks.
Stage 3 - Main Payload: Main malware payload that steals online banking data from the targeted banks found in the malware configuration. The configuration is either embedded in the binary or downloaded from a command-and-control server. Most payloads are Windows executable binaries, developed in Delphi.
Chained Delivery: an Evasive Network Pattern
During our analysis of these campaigns, Cybereason observed many legitimate services that the threat actors chained together to deliver financial malware. These services include several URL shorteners, Dynamic DNS, online storage services, and CDNs (Brazilian threat actors have been known to use CDNs to deliver malware).
Using these different services together makes the generated network traffic appear legitimate, increasing the chances that it won’t be flagged by IOC/heuristic-based engines. This technique seems to bypass many network security products, antivirus programs and may even evade some security analysts.
Example 1: Multi-stage delivery as observed in network traffic
URL Shortener → Dropbox → URL Shortener → Facebook CDN → Malicious Site/C2 Gate
Example 2: Multi-stage delivery as observed in network traffic
URL Shortener → Dynamic DNS → URL Shortener → Github → Malicious Site/C2 Gate
Table of common services being used as part of the threat actor’s infrastructure
| URL shorteners | goo.gl, bit.ly, tinyurl.com, bit.do |
| Online storage | dropbox.com, sendspace.com, gitlab.com, github.com, amazonaws.com,000webhostapp, pastebin.com, googleusercontent.com |
| CDNs | cdn77.org, cdn.fbsbx.com (Facebook’s CDN) |
| Dynamic DNS | publiccloud.com.br, ddns.net, game-server.cc (dyndns), hopto.org, no-ip.org |
Example of first stage payload hosted on Gitlab:
hxxps://gitlab[.]com/faturavivodigitalabi0x/210820148vivox/raw/master/cliente_anexo_seguro_senha_1425.rar
The extracted content is an obfuscated .cmd scriptlet with a very low detection rate:
Main Entry Point: Phishing Emails
Cybereason found that phishing emails were used for the initial infection. The email body usually contains either an attachment or a link to a URL shortener that points to hosting websites where the first stage payload is stored. The payloads often masquerade as Flash/Java updates.
Most emails share a similar subject line and allege to be invoices (“FATURA” in Portuguese). Another common theme is spoofing emails to make them look like they came from VIVO, Brazil’s largest telecommunications company.
Example 1: Spoofed VIVO Emails and Fake Invoices
The infection chain starts after the user opens the PDF attached to the spoofed email:
Examination of the PDF reveals a stream containing a shortened URL:
Once the user clicks anywhere on the PDF, the code will fire a request to the shortened URL, which at the time of the detection had zero antivirus detections:
The URL resolves to the following DropBox URL that hosts a ZIP file containing the first stage downloader script:
hxxps://ucf18b68308d0a38b496c554353b[.]dl[.]dropboxusercontent[.]com/cd/0/get/AOAYxd4VLLCvZ5lZ_2VQLUD93KO_p8GEm42Z-uFIqBoBSf_XFcMeFA-vgnvGhpvTKabzARrr6NPIvETHkG7jSg_35Bo9ablTRfbK2tPVbsQukqfuMMvtDljNN8nnTt9Ahp-eRqczHWhm-qaGp2BfJ2ZRMIuM3hXRbcl3NXQ-agrbpgO6NuMoA-w24mRfR3FZBfE/file?dl=1
File name: 2Via-Fatura-13082018.zip
Example 2: .lnk file downloaded from a Web-hosting website
In one recently observed campaign, the victims were led to this file sharing website URL and encouraged to download a ZIP file:
The ZIP file holds a .lnk file (arq1561.lnk) that contains an obfuscated downloader payload:
Once users click on the .lnk file, it spawns cmd.exe and powershell.exe processes, which download a secondary payload:
Additionally, an Internet Explorer instance launches and loads a legitimate Adobe website, probably to allay any suspicions that the users have about the downloaded file and to distract them from what’s going on in the background:
Stage 1: Obfuscated Downloader Scripts
In 70 percent of the infections, the infection chain traces back to three main file extensions: .bat, .cmd and .lnk. The scripts are usually contained in an archive (.rar/.zip) to bypass email and spam filters. In addition to the batch files, we also observed other extensions, such as .exe (Windows Executable) and .chm (compiled HTML), sent over as email attachments.
The combination of downloaders bundled in archives proved to be highly effective at bypassing antivirus products. Many of the analyzed payloads had a low detection rate, ranging between 0-17, out of 59 antivirus vendors.
Evading Command-line Detection using Environment Variables
Most of the first stage payloads consisted of an obfuscated script or a set of obfuscated commands. The batch script below uses an obfuscation that gradually builds up its payload, as detailed in this blog. The PowerShell payload is set as an Environment Variable (in this case the variable is called “system”):
This obfuscation type appears to be adopted from Daniel Bohannon’s Invoke-Obfuscation project. Once PowerShell is executed, the actual downloader payload does not appear in the process’ command-line arguments:
PowerShell command-line arguments: -nop -win 1 -
However, by examining the environment variables at runtime, one can observe the downloader command set to the “system” environment variable:
Based on our observations, this technique is widely-used by Brazilian threat actors, and provides yet another testimony to the efforts made by the threat actors to evade both static detection by using obfuscation as well as detection based on command-line logging by using environment variables.
Living Off the Land: Abusing Microsoft-Signed Applications
The Brazilian threat actors seem keenly aware of the trendy usage of Microsoft-signed and trusted binaries (aka LOLBins) to download or execute payloads. In addition to the commonly seen PowerShell and Windows script engines, we observed other Microsoft binaries being used across different campaigns.
Example #1: Using msiexec.exe as a Downloader
The above .lnk file spoofs an Internet Explorer shortcut. Once executed, a secondary payload is downloaded, extracted and executed using Microsoft’s msiexec.exe:
Target command:
The shortened URL resolves to the following URL (FaceBook's CDN):
hxxps://cdn[.]fbsbx[.]com/v/t59.2708-21/38622203_278626666261527_5981472121300189184_n.txt/loader.msi.1415.txt?_nc_cat=0&oh=f3e5a4d4218591d13784015d95f5a798&oe=5B73C975&dl=1t
The downloaded payload is an msiexec file, which serves as a container that deploys the “windows.bat” in %appdata%:
Contents of the batch file:
The deobfuscated payload is the following PowerShell downloader command stored in an environment variable (“day”):
This downloader fetches another PowerShell payload, which ultimately drops the main payload.
Example #2: Using Certutil as a Downloader
The above RAR archive contains a .lnk file, which upon execution will download a payload using Microsoft’s Certutil.exe with the “-URLCache” and “-f” flags:
The executed command will download and launch a batch file (secondary downloader):
Example #3: Using Certutil to base64 Payloads
We observed a .lnk file that included the following command, which uses Microsoft’s Certutil to decode a base64 payload:
The decoded payload is further obfuscated with simple caret obfuscation (^):
The deobfuscated command downloads a secondary payload:
Stage #2: PowerShell Downloader
Our investigation showed variation in the types of second stage downloaders across different campaigns. The main purpose of the second stage downloaders is to fetch an additional payload, in many cases the main payload. Some secondary downloaders showed additional capabilities, such as persistence creation, UAC bypass and anti-research checks.
Example #1: Persistence and fetching secondary payload
The following second stage downloader is a PowerShell script that checks for an existing infection, drops a batch file that checks for values in the registry, drops a .lnk file that points to the aforementioned batch file for persistence and fetches a secondary xor-encrypted payload from the same remote server. The script has low detection rate (3/54):
Initially, the script checks for a likely previous infection by searching for a file name with the day’s date (in the form of yyyymmdd) in the %temp% directory and, if this file is unavailable, it downloads a bitwise XOR-encrypted payload:
The full batch file script is built dynamically by the PowerShell script. Here we see it being built with environment variables as seen in other instances throughout the different campaigns.
The .lnk file is created via Windows Script Host (commonly referred to as Wscript) and is used for persistence, as it will point to the batch file when executed (the $cmdFileName variable contains the path to the batch file) :
The script uses a scheduled task to bypass UAC (User Account Control). The created batch file is executed once, and then the task is deleted to remove as much evidence as possible:
Contents of batch file:
Example #2: Obfuscated Downloader with Anti-Virtual Machine Checks
While analyzing an incident, we found the following PowerShell script, which looked different from the previous downloader. The script was likely obfuscated by the ISESteroids PowerShell extension, which provides a built-in obfuscation feature. The script had a particularly low detection rate (2/57):
After deobfuscating the script, this downloader conducted a few anti-virtual machine checks. These checks are part of the threat actors’ evasion techniques and attempt to prevent researchers from studying the main payload. As seen below, the script will attempt to use WMI to query for these virtualization products: VirtualBox, VMware Virtual Platform, Virtual Machine, HVM DOMU:
Once the “coast is clear”, the script will create persistence via a .lnk file, which will execute the malware via Rundll32.exe.
Stage #3: Main Payload Execution
The campaign’s main payloads consisted mostly of common Brazilian malware that antivirus vendors generically name Banload, Banbra, Bancos, Boleto, Delf and Spy/Banker. Brazilian financial malware is known for its effectiveness in overcoming multi factor authentication (MFA), by implementing sophisticated social-engineering tricks to extract SMS codes and other security tokens information, using overlay screens as previously shown.
Cybereason identified variations in the way that the main payloads were executed. In this part, we will examine executions that involve abuse of trusted third-party applications via DLL hijacking as well as using built-in Microsoft-signed binaries (also known as “LOLBins”) to execute the malware code. Using these techniques lowers the risk of detection.
Abusing Trusted Applications via DLL-Hijacking
As discussed in an earlier blog, the Brazilian threat actors seem quite fond of leveraging DLL-hijacking techniques against trusted security vendors, including Avira and McAfee, and trusted technology companies like VMware, NVIDIA, HP, Realtek and Adobe.
Splitting the payload - Because Two is Better than One!
We noticed that the Brazilian threat actors evolved how they implemented DLL-hijacking. Earlier infections that used this technique implemented a classic approach of deploying a vulnerable trusted binary along with a fake DLL. This TTP was previously documented being used in the context of Brazilian financial malware. In some cases, the fake DLL was even signed with revoked or self-signed certificates in an attempt to further lower the possibility of detection.
Newer samples observed in 2017 and 2018 added another layer of evasion by splitting the malware payload into two components:
- Loader: A fake DLL that loads the encrypted malware payload to memory, decrypts and executes it.
- Malware payload: Encrypted file that cannot run on its own and is dependent on the loader.
This codependency between the loader and the encrypted payload makes the detection and analysis of this malware harder. For the malware to run, it requires that both files reside in the same folder. In most cases, the loader DLL will also validate that it is running in the context of the vulnerable application, or else it will crash.
Example #1: Remoto Overlay RAT Abusing Avira via DLL Hijacking
An email attachment sent to a user contained a .lnk file, which executed the following commands that led to a download of a binary (reymr.exe):
The binary is a signed Avira product renamed by the attackers, as indicated by the file metadata. See this VirusTotal link for more information:
Further investigation showed that along with reymr.exe, the PowerShell script also dropped the following files:
| File Name | Purpose | SHA-1 |
| reymr.exe | Legitimate Avira.SystrayStartTrigger signed binary | 762BF93E6265B4E74BD0BFCAA447F1A619DB2F58 |
| msvcr120.dll | Legitimate Microsoft® C Runtime Library | F19E9D8317161EDC7D3E963CC0FC46BD5E4A55A1 |
| msvcp120.dll | Legitimate Microsoft® C Runtime Library | EFD1E306C1092C17F6944CC6BF9A1BFAD4D14613 |
| avira.oe.nativecore.dll | Malicious DLL exploiting Windows Search order Hijacking to execute malware. Decrypts the contents of RestartManagerUninstall.mui | 312F4DC26FD0C277F9727CE3B943123CBEB127C1 |
| RestartManagerUninstall.mui | Encoded blob loaded after avira.oe.nativecore.dll with Trojan functionality | 9A944B0933F004DB012DB202BF5C2BE1E231FBB5 |
Reymr.exe includes avira.oe.nativecore.dll in its import table:
The main payload was identified as the Remote Overlay RAT, previously discussed here.
Using Rundll32.exe to execute the Main Payload
In some recent spam campaigns that we monitored, the malware authors favored the built-in Rundll32.exe to launch the loader DLL payload. Once the DLL is executed, it will load and decrypt a second (sometimes even a third) encrypted binary, which is the malware main payload.
Example #1: Financial Trojan launched by Rundll32
In this example, we can see a PowerShell process that was spawned by cmd.exe as a result of a .lnk file execution. PowerShell downloads a secondary payload from a malicious website:
Download URL: hxxp://barca21[.]zapto[.]org/barca21/vx1.txt
The PowerShell payload drops and extracts a ZIP file containing the following files:
| File Name | Purpose | SHA-1 |
| Yaew.toib | Loader binary (DLL) | 3F9E9BD8330660B0DA23EE8D54787A44E53DDF65 |
| Yaew1.toib | Encrypted financial Trojan payload (DLL). Exported function: OCSVFWBO56 | 87DBACFE8727B9DA1EACE101BEE84D06388FA7B6 |
| G | Encryption & configuration data | D5E3969BB36A675CF9CE60A88ABB5C8DE7C3BD80 |
Command line:
"C:\Windows\System32\rundll32.exe" C:\Users\Public\YAEW.TOIB ,,, OCSVFWBO56
The unpacked payload seems to be a variant of a Brazilian Remote Overlay RAT:
Example #2: Rundll32 injecting Main Payload to Windows Media Player
In this example, we will follow the execution starting from the second stage PowerShell downloader:
The network PCAP shows a second stage PowerShell that downloads a ZIP file (PK signature):
The zip file contains OAzBrxSXRoTOBssa.dll and OAzBrxSXRoTOBssa.
List of dropped files:
| File Name | Purpose | SHA-1 |
| 1010180844353.bmp | Zip (dropped by PowerShell) | 3344EF3B32DF03057721ED6E76F276B9073A0932 |
| OAzBrxSXRoTOBssa.dll | Malware loader exported function: dGuCCzlxnosaJBpk | C523C65C7BD9EE09360C24BC706985BA5361D724 |
| OAzBrxSXRoTOBssa | Encrypted payload | 1A86E3D82AF58DA6A3CC5B3849B7D81565945433 |
The PowerShell script extracts its contents and runs the DLL via rundll32.exe, pointing to the exported function “dGuCCzlxnosaJBpk”:
Executed command:
Once the loader decrypts the main payload (OAzBrxSXRoTOBssa), it injects the malicious code to Windows Media Player:
The Injected PE (MZP header) is mapped into the memory space of Windows Media Player:
The dumped payload shows indications that the malware was likely compiled on a machine with Brazilian Portuguese language settings, as can be found in the the RC_DATA resource section:
Once executed, the malware sends an initial beacon via a POST request to the command-and-control server:
$_POST=&plug=NAO&sowin=Windows%207%20Professional%20-%206.1%20-%20760
Related Post-Infection Payloads: Outlook Malware & InfoStealers
Other Brazilian malware that was related to the malware we analyzed was also found on the compromised machines. These post-infection payloads provide a glimpse into the Brazilian malware ecosystem and, to some extent, offer an understanding of what the threat actors are after.
In addition to the banking Trojans, we found that the same campaigns were distributing cryptocurrency miners, infostealers and malware that targets Microsoft Outlook. Malware that targets Outlook is a particular concern since it poses a major risk to organizations worldwide. The malware contains features that leverage Outlook’s functions, like the ability to query victims’ contact lists. Threat actors usually use this information for spam campaigns, but can also sell it on the dark market to other attackers who want information on an organization they’re planning to attack.
Distribution of Additional Malware
Following is an example of a malware which was designed to steal credentials using Overlay phishing, as well as downloading additional malware. The malware and its auxiliary components were found in %programdata%:
| File name | Purpose | SHA-1 |
| Rltkapo32.exe | Renamed authentic Microsoft’s Certmgr.exe | F18EEBAEA4460B057F5B49E8239779F1C0C05BB9 |
| Cryptui.dll | Fake DLL, serves as a loader and injector | D3AE2843261528D8B4A5D6070661FE302E7A1FA9 |
| Rltkapo32.driver | Main payload | 036B68413E64BE54A919916A7360B2B4142E59D0 |
| Borlndmm.dll | Legitimate Delphi Borland Library | 76E3A2004E5BA7F5126FAC9922336F38E928D733 |
As seen before, Brazilian threat actors often exploit DLL hijacking, and this time the vulnerable application was Windows’ “certmgr.exe” (aka, Certificate Manager Tool). The fake DLL (cryptui.dll) loaded and injected to svchost.exe the main malware payload (Rltkapo32.driver):
Examination of svchost's injected payload, shows that the Delphi malware will try to present a fake Login form to its victims, in order to steal their credentials (possibly even organizational credentials):
The injected svchost process communicates with the C2 servers and downloads a second payload :
Examination of the dumped injected payload, shows that the Delphi malware will try to present a fake Login form to its victims, in order to steal their credentials (possibly even organizational credentials):
Mathilde.exe is an SFX file which extracts a script called “linsoldo.cmd”, which is a PowerShell downloader:
The script fetches an Outlook stealer PowerShell script hosted on an Amazon S3 bucket.
Outlook POWERSHELL Stealer
The downloaded PowerShell script (“Outpos.data“) is designed to steal information from Microsoft Outlook clients and users’ harvest emails addresses. Its main capabilities:
- Receive encoded commands from the C&C server
- Gather information from Outlook (Contact list, mailboxes, emails, Outlook folders)
- Write collected data to a .txt file in %temp% folder
- Post data to the C&C server over HTTP
Excerpt from the PowerShell script shows the exfiltration data:
Also interesting to notice the comments in Portuguese left by the malware’s Author:
The data is posted to a server (18.188.80.202), running a server that runs XAMPP. The error message, we can see an admin panel referencing the name “coringa”, as can be seen below:
“Coringa” is likely a reference to a Brazilian RAT called “Coringa-RAT”, whose source code is publicly available. It is likely that the threat actors are using the RAT in other campaigns as well. Cybereason, however, did not observe a direct use of Coringa-RAT in the aforementioned campaigns.
Contents of Amazon S3 Bucket
The URL from which the Outlook malware was downloaded points to an Amazon S3 Bucket:
The bucket contains several kinds of Brazilian malware, such as: second stage downloaders, Outlook mail stealer and also a Brazilian banking trojan (Remote Overlay RAT):
| File Name | Purpose | SHA-1 |
| outpos.data | Outlook mail stealer (PowerShell script) | 0657FAA51EB8417A2D63388A9BA37997A2B5F323 |
| image2.png | Zip file contains vulnerable NVIDIA binary and Brazilian financial malware |
B92AE70321CDB6644196DFB9827C89166AD07A3A |
| bol.png | PowerShell Downloader | 16FAEF11D46CFBCAFE8B58064C2C38B96950BE9C |
| Poratal.txt / Testefad.txt | PowerShell Downloader | E138609B66FC6B9C6C688DE6B5DC094A782C6474 |
| jardilhas.mcas | PowerShell Downloader | 0C2CD86F1838A48E2B71430D3314182CC2318914 |
| Cadeagod.maz | PowerShell Downloader | C80AD41891EFE21798CC8F04B73CC64F4D883EA1 |
| jasonfsa.vom | PowerShell Downloader | 174FF790DBFB5053755D5164B26CA90F1A4D7CB8 |
| juremal4l3l.dfas | PowerShell Downloader | D89AEFC78440710DDF0CFC91FF3BB590FF7D1C4F |
| mortlin.sdo | PowerShell Downloader | 9BDB62C5871E45AF57F4D9A1D94C446627FC2ECF |
The unpacked payload of the Remote Overlay RAT shows that the malware targets Brazilian banks such as: CitiBank Brasil, Safra National Bank, Banco da Amazonia, Itau Brasil and Bradesco:
Brazilian-made Malware, Spanish-Speaking Targets
Cybereason analyzed multiple infections involving different Brazilian financial malware that did not target Brazilian bank users. Instead, the malware configuration was set to target bank users in Latin America and Spain. This finding bodes well with earlier research papers that discuss various aspects of Brazilian cybercrime’s role in the global threat landscape and its proliferation to various regions. Research from ESET, TrendMicro, Kaspersky and ElevenPath has more details on that topic.
The following examples, taken from infections that occurred in 2018, show that online bank users in Spanish-speaking countries are also being targeted. These countries include Argentina, Bolivia, Chile, Venezuela and Spain. Cybereason found earlier samples of Brazilian malware targeting more countries, such as Mexico, Portugal, Colombia and other Latin American countries.
Example #1: Brazilian Financial Malware targeting bank customers in Latin America and Spain
- Brazilian Banks
- Bolivian Banks
- Chilean Banks:
- Spanish Banks:
Example #2: Brazilian Spammer / Info-Stealer targeting Venezuela & Bolivia
Venezuelan Banks:
Bancaribe, Banco Fondo Común (BFC), Banco Exterior, Banco Sofitasa, BBVA Provincial, Banco Universal, Banco Industrial de Venezuela, Banesco Banco Universal, Banco Caroní, Banco Venezolano de Crédito, Banco Nacional de Crédito, El Banco Federal
Example #3: Brazilian Banker Targeting Argentinian Users
Extracted image from the malware resource, shows an overlay screen meant to bypass Multi-Factor Authentication, targeting customers of Bank of Patagonia:
List of Argentinian banks targeted by the Brazilian malware:
Argentinian Banks:
Banco Patagonia, Itaú Argentina, Standard Bank Argentina, Banco Macro, Industrial and Commercial Bank of China (Argentina), Santander Rio
Brazilian-Made Malware, Originally made to target Brazilian Users
During our investigation, it was evident that the different malware types were created by Portuguese-speaking threat authors and were originally designed to target Brazilian users. This is supported by the embedded Portuguese strings and references to specific security softwares that belong to Brazilian banks, as can be seen below:
Command & Control instructions in Portuguese:
List of commands embedded in the malware’s code shows Portuguese strings:
Excerpt from UAC-bypass procedure used by the malware (“not possible to verify UAC”):
Strings referencing specific software distributed by Brazilian banks to enhance online banking safety, such as: G-buster Plugin (GbPlugin), Aplicativo Bradesco and Aplicativo Itau.
Back to the Source: Open-Source RAT, Many Variants
Based on the functionality and string similarity, Cybereason estimates that different kinds of Brazilian malware borrowed code or even based on the source code of a Remote Access Tool (RAT) called “Delphi Remote Access PC”. The RAT is open-source and publicly available on Github. It was coded in 2015 by a Brazilian user whose Internet handle is “senjaxus”. This user also co-coded another RAT called AllaKore. The author clearly states that he is not responsible for any misuse of his code:
From Portuguese:
“This source was created by Richard Maickonn. Distribution of this source is free!Contact: senjaxus[at]gmail.com.
I AM NOT RESPONSIBLE FOR THE MISUSE OF THIS SOURCE.”
Even though the code has fully functional remote access capabilities, it does not seem to contain functionality directly related to financial malware, namely, targeting of banks or using a screen overlay social engineering. In addition, unlike typical Brazilian financial malware, the Github source code does not contain anti-analysis code, like the ability to detect virtual machines, security products or Brazilian software. It is our estimation that these features were likely added by different malware authors who repurposed the open-source RAT code.
Examples of code similarity between the Github source code and other Brazilian malware payloads:
Example #2: Brazilian malware targeting Chilean Bank Users
Example #3: MPRado Remote Access Tool
This RAT seems heavily based on the source code of Delphi Remote Access PC. This is likely a variant of the RAT:
Conclusion
In this blog, we surveyed the techniques used by Brazilian threat actors as observed by Cybereason throughout 2017-2018. We also showed how different financial malware campaigns share similar traits around delivery methods. The analysis of the tools and techniques highlights how effective these methods are at evading antivirus products, as demonstrated repeatedly by the low detection rate. In addition, we showed how Brazilian threat actors are expanding their campaigns and targeting online banking users across Latin American countries as well as Spain. Finally, we linked several payloads to an open-source RAT that was created by a Brazilian author whose code was likely repurposed and turned into various banking trojans by Brazilian threat actors.
Indicators of Compromise
Domains
www.actcontabilidadeltdarh[.]comwd1g1talvivowce98[.]ddns[.]netd1g1talvivoscaep09x[.]ddns[.]netlvivoscaep[.]ddns[.]net/financeirocontabiltda[.]comhewayo[.]comdlm[.]capemn[.]com stot[.]irrema[.]comdlm[.]nadolt[.]combacon[.]semilonn[.]com contrato-brasil[.]hopto[.]orgIrrory[.]comDlminjuado[.]comdlm[.]supote[.]compsom[.]uticis[.]commacos[.]revelf[.]coms1.sleove[.]comdlm.tinert[.]com macos.revelf[.]comjazy.othiak[.]comyipe.cebeer[.]comsecurity[.]upesse[.]comwww[.]examedoenem[.]comsso[.]anbtr[.]comWww[.]movavis[.]comWww[.]auayyertagaphgoabqigeyhsat[.]netnotificacion[.]org
URLs
hxxps://cdn[.]fbsbx.com/v/t59.2708-21/38622203_278626666261527_5981472121300189184_n.txt/loader.msi.1415.txt?_nc_cat=0&oh=f3e5a4d4218591d13784015d95f5a798&oe=5B73C975&dl=1hxxps://ucf18b68308d0a38b496c554353b[.]dl.dropboxusercontent[.]com/cd/0/get/AOAYxd4VLLCvZ5lZ_2VQLUD93KO_p8GEm42Z-uFIqBoBSf_XFcMeFA-vgnvGhpvTKabzARrr6NPIvETHkG7jSg_35Bo9ablTRfbK2tPVbsQukqfuMMvtDljNN8nnTt9Ahp-eRqczHWhm-qaGp2BfJ2ZRMIuM3hXRbcl3NXQ-agrbpgO6NuMoA-w24mRfR3FZBfE/file?dl=1hxxps://uca170a0c980fec5e870c5d85655[.]dl.dropboxusercontent[.]com/cd/0/get/AOCrXrpG7lb1--ypzOHG2PKmum07jCJFXdnpAt67PJVlnu8SKbwMoOcVlQYcsXtg_Y2OyAfmdS6_nb-LtaZ-Ya-8MchtHXmRrxiV7tQ258TGwxfyA3fqrBTLDEQG9qqd-hlKZaRg7xiu-vCg20q3SSmCJ5GNdxJlmKW81amy1wV5SNpI73Id61FE4D-Cm7SAX3Q/file?dl=1Ucb6056cad19f90f56a81cf4aabe[.]dl.dropboxusercontent[.]comhxxps://github[.]stihic[.]com/?cGBhuAyAZ6UDuIJdSOhrb8WFtI5PLgdQ2cXfe30ATnjlK6L0bndQxwBUYz4oft6IGQeMqJv/DWmhCcD1EFogJrlI+Gbc+/qcTPBalQE0BsO8jl0=hxxps://cld[.]pt/dl/download/3fffb114-0cf2-41fd-a664-dc23129a31cc/156498Arquivo521solicitado1536714090[.]rarhxxps://gitlab[.]com/diigitalvivosuxxs/22082018x/raw/master/clientes_anexo_seguro_senha_1425[.]rarhxxps://gitlab.com/faturavivodigitalabi0x/210820148vivox/raw/master/cliente_anexo_seguro_senha_1425.rarhxxps://fs13n3[.]sendspace[.]com/dlpro/60669bfbc7614b1ecb0b7988ce7b325e/5b869d74/r7un2z/clientes_anexo_seguro_senha_1425[.]rarhxxp://serasaconsumidorexperian[.]com/consumidor?download/extrato/debitos?extrato-debitos/serasaconsumidor.htmlhxxp://amazoncontabilfinan[.]com/segmentos?rastreamentoobjetos/sistemas.htmlhxxp://faturasimplesltda.com/contratohxxp://clientesemailrh.com.br/contabil/hxxp://consultafacilserasaexperian.com/clienteshxxp://serasaconsumidorexperian.com/consumidorhxxp://nfefazendaportalprincipal.com/clienteshxxps://gitlab[.]com/nfeagosto9dyur5/300882018hxxps://gitlab[.]com/faturavivodigitalabi0x/210820148vivoxhxxp://consultafacilserasaexperian.com/consumidor/?serasaconsumidor?gclid=EAIaIQobChMImqi3i4633QIVT4GRCh0ZBgZMEAAYASAAEgKpR_D_BwEhxxp://lealcontabil.com/comerciohxxp://portaltributariorhltda.com/contabilrhhttp://portaldacontabilidaderh.com/002122018455320hxxp://wsfinanceiraalfa.com/contabilrhhxxp://portaltributariorhltda.com/htb00025518hxxp://realizesolucoesfinanceirasltda.com/INBOX?PORTAL/FormularioDePesquisa.aspx?tipoconsulta=completa?C61BB027A724A032974585D278hxxp://raizcontabilrh.com/100833276hxxp://imperiocobrancasrh.com/DOCUMENTO8545006hxxps://fairsharetraining.eu/sites/default/files/p.txthxxp://icog.futtsociety.com/updt1/n.phphxxps://fairsharetraining.eu/sites/default/files/misc/ax.pnghxxps://fairsharetraining.eu/sites/default/files/misc/mg.pnghxxps://www.aguiarnopolisatacadista.com.br/stornews/?a=Z0DEXUBSWD7FE45T3JHBMMJXCW3DON98P9LY3SRThxxp://psom.uticis.com/6eKGNr74/crypted_loader_1516355349-g.cmdhxxp://psom.uticis.com/6eKGNr74/loader-gestor.lnkhxxps://gitlab.com/silvosi/ftavihxxp://corretorandremendes.com.br/images/contA/ponto.php hxxps://github.com/dantealighieriii/startup/raw/master/Actualizacion_setup.version052018.zip hxxps://github.com/dantealighieriii/startup/raw/master/Actualizacion_Complemiento%20FIashWeb.v55.3.2018.ziphxxps://raw.githubusercontent.com/dantealighieriii/startup/master/ch.csshxxps://gitlab.com/diigitals/v22082018xhxxp://ch.rmu.ac.th/wp-content/plugins/ubh/auxaudioo.jpghxxp://ch.rmu.ac.th/wp-content/plugins/ubh/home.jpghxxps://ppa1.r1-cz.storage.forpsicloud.cz/Fatura-24913089743.zip?time=636766229160513717hxxps://s3-eu-west-1[.]amazonaws[.]com/teste34s2/Outpos.datahxxp://www[.]movavis[.]com/cgi_sys/token.htmlhxxp://www[.]examedoenem[.]com/cgi_sys/token.htmlhxxp://178[.]62[.]125[.]145/streamback.zip
IP addresses
134.73.90.141134.73.90.200185.207.204.13834.199.8.144108.167.168.35178.62.125.14518.188.80.202
Hashes
934B2F43B1D6F54A2BFD0552C853D7274C3BAB40FAFE2261493FF6F4D10613610FD44CBB203C551A48D3A9C5D38924378E4BF4F73305D448ACED93DFC635004C61BF47A3986DAD5F849F46C5EF80D88BF76C3965A659D56E1DAA5E459A41566F75B198146C8580FFE068FBE7F2D770151D061EF58B8F226435870453F773C81EC08B8D96B1365C238CA81502A4E58D55B619D467D3AA73A714AE72591204BDB6899CFEC36BF3168FD19F6D476C6BF6494967B53D5B230EFF33DA4965717AB27895390EC0DB67A65BE9C6E2F1A963A14943AB330534EC2393E8474284AF5CCC1139860CEA9FCDD5935DDAC26688D529A36FE66ADC814C646ADBE60CAAA8CC9CB043AE2DB7861CE18011DA0B5EA25174A6F53A424DC3BC243551A99ADBD24D516541F78D73275573AF861578DF53F40083477836F7DDAE3A7C04D95E12F9BFF5EA6640059E8D0E444F857B52935886E9139BECC673018A54120A96B0350CCB157698FE87A5849374ECF022C2620BA4C6BBF1C33C0820756E0372961AB1C3F6F7879A4DAE7954EF52E086FF5ABCB89D4A6087076879C74BBFC635D7D5D86D00B694DA2BA65EBF2034CBE7E6F6A0D1365912DC8486D2F07D242AF0C4A576A721EC3B0BBA97D46FF3C082BC32BABC87076879C74BBFC635D7D5D86D00B694DA2BA65EEEEBD1B7262C718D429E9A460D4D8DF2917B071A2AE7385E5E783CD0C9BB99AE7B3D213388B81A35E6763D651C9B6FFFF9B88A1AE9A6E6C21F42B1210F75C296C68077F90F6BC4B7DDFD056F075C75461110D1D26366C952BBCE99EF2824E432078AC36463BE4BCA20E2592C8254ECAFE3D6BF82A69B11B4FB7CD98EF272E3A9B70CEACC4225C6B3601BF5868E25BE3BE7A15B2DAAE9EE096DB404B562618B10A22A6B89BA4BC0FBF86ABB8248EE4576E1AB0EBF3F9E9BD8330660B0DA23EE8D54787A44E53DDF6587DBACFE8727B9DA1EACE101BEE84D06388FA7B6B47F58266C2485EAFC2C7ED6FF674A3494C0E0E58744F0FB86C2B1712200A42030D54C4E793BDD99B73457CB139D9E721FDBB2F4C19359A4C03DA5CDFECBB2E7443DEC83531F715DA5C3F256FA8451314378C517B373F1BCF712938C6076A5EF660C8A50AC60733518E7FE6E03E567B6A79CA15139BFEDCA5595E36B048248092E65433A2781ECA87A6E6FC3471ED26615AC8D6AC59AA8724FA3306B8BF9EE3684502808DA59E62B661B731198DACD64EBEA5ED1A1438D683D4C905072C834DD8857970B97EC3AAFC80AD41891EFE21798CC8F04B73CC64F4D883EA1174FF790DBFB5053755D5164B26CA90F1A4D7CB8D89AEFC78440710DDF0CFC91FF3BB590FF7D1C4F9BDB62C5871E45AF57F4D9A1D94C446627FC2ECF0C2CD86F1838A48E2B71430D3314182CC2318914A97B6D83589DA0ACD60E87EA9B29B84516DF7E52892895391FF68725464107C537CAAB7E668B3F79C9E7B7C2490DF4CD75F0E7BC6A32D09AD000033A984DAE40F09C25C8BFE6BD07729D924C81FB5EAE07CAFE5D2303A3B2F5F0DDFE052F42117A70F7AA56B235985199D0DBAF8EA75B6704AF2841CB50D7844342CC4B0A5FFF222A146DCE05A3E30A068F49A5DFB83E73E1FEF0286DD515267B58A3FB4F1F555B8DF646C2AE5EE9CD11B598FA0631AF41578C9743FFAA59F3B82E0BC181F6FACFEAB014854949153A089B4AE0BC22E6939D3F2A70BFF8C2FBAB1C9A3C2069113E58B6403EE7CDDC1ECB33D72F6D9EA6BAAD23A6A7644FDCC1B24D43294D04E001BA328BABA1D7D72DD5F9F56EE8AFF820A24BB5FADBE24984861586C2769E10F7EA86588F0037A1F553809A87358CC245FDF172EC532C2B1C729E1A6F9CB18E92CAF0270E1F02BB84DB85F6B4CA30DD76F16D1CB3E420AA5D6B3EC9564C46B51A2743AD50B1985AABC5BFDFE65003AA6ABDEA85B56ED56E9376C7D47E65C8A8EFC670E5AD5C5322A2B2D89DB2F2B05CBBBCD44E5670753DBD0C75D75F184493514EC4A3784AA92E0761261BB8129E0FAB239C794DBC33010FFABC647BBCD54191057D38C114B54406B61CF848091DA3A8EC8FC9CC870FC34E4A4D604A0510AB5B3567E1CF7D85375F020CCC3E302F3949CF5732A64E3D5613532F91010754332A6E1CA1BC2E2408BDDAB73F58BD58ABEA4F9D7D5EA9F776E4D1B6136508774AA547C0D8FA34E74BE8FD958A6752393EBE234061AE9808FEF74BBC97CA500EC940F3EF05C523C65C7BD9EE09360C24BC706985BA5361D7241A86E3D82AF58DA6A3CC5B3849B7D815659454334C10EB17482865A1E0546B07997C7A76C137FE04AAF27E727B9F661BC4C0D35C309937F4C28E3BFF762BF93E6265B4E74BD0BFCAA447F1A619DB2F58F19E9D8317161EDC7D3E963CC0FC46BD5E4A55A1EFD1E306C1092C17F6944CC6BF9A1BFAD4D14613312F4DC26FD0C277F9727CE3B943123CBEB127C19A944B0933F004DB012DB202BF5C2BE1E231FBB586C7312D9E786D89FC12973B7584F6CAF39805C3E2F7257C50DBAC0ADC8DF48E514AF2AB9917EF9A3723E2A328AAFB359116DFC987222C5001BF59D7D5E3969BB36A675CF9CE60A88ABB5C8DE7C3BD803344EF3B32DF03057721ED6E76F276B9073A093252E2268A7FDBB324B3B8A78DDBDC91D05A83FE69036B68413E64BE54A919916A7360B2B4142E59D0D3AE2843261528D8B4A5D6070661FE302E7A1FA9B92AE70321CDB6644196DFB9827C89166AD07A3AB953DCF386FD2BC3E586BE2724557D5E72903B330657FAA51EB8417A2D63388A9BA37997A2B5F32315166EF05CB3278E388C46359835A64CFB4D29EC0657FAA51EB8417A2D63388A9BA37997A2B5F323B92AE70321CDB6644196DFB9827C89166AD07A3A16FAEF11D46CFBCAFE8B58064C2C38B96950BE9CE138609B66FC6B9C6C688DE6B5DC094A782C6474250ABE43477D34023E71469BB97B8BA9B434A5621FECA0C9E12B110F16CFB6A4CC7556B90FFAE5F6
