In this Threat Analysis report, Cybereason investigates the the Phorpiex botnet that delivers LockBit Black Ransomware (aka LockBit 3.0).
January 28, 2025 / 9 minute read

In this Threat Analysis report, Cybereason investigates the the Phorpiex botnet that delivers LockBit Black Ransomware (aka LockBit 3.0).
January 28, 2025 / 9 minute read

In this Threat Analysis report, Cybereason investigates the rising activity of the malware LummaStealer.
December 17, 2024 / 14 minute read

In this Threat Analysis report, Cybereason investigates incidents relating to the Andromeda backdoor and a new cluster of C2 servers.
December 3, 2024 / 8 minute read

In this Threat Analysis report, Cybereason investigates the Ransomware-as-a-Service (RaaS) known as Beast and how to defend against it through the Cybereason Defense Platform.
October 18, 2024 / 5 minute read

In this report, Cybereason confirms the ties between Cuckoo Spear and APT10 Intrusion Set by tying multiple incidents together and disclosing new information about this group’s new arsenal and techniques.
October 4, 2024 / 13 minute read

Should businesses prioritize cloud-based or on-premise cybersecurity solutions, or are CIOs being influenced by a variety of strategic factors and opting for a hybrid approach?
September 18, 2024 / 7 minute read

In this report, Cybereason confirms the ties between Cuckoo Spear and APT10 Intrusion Set by tying multiple incidents together and disclosing new information about this group’s new arsenal and techniques.
September 13, 2024 / 11 minute read

Some CISOs I know work on a premise that for every one new technology deployed, two should be removed. I wonder if we tried to apply a similar principle to the operational aspects of cybersecurity, how far we could progress.
August 1, 2024 / 5 minute read

In this blog, you learn about a highly sophisticated, well-funded, and strategically motivated nation-state cybersecurity threat called cuckoo spear.
July 25, 2024 / 4 minute read

In this Threat Analysis report, Cybereason Security Services investigates HardBit Ransomware version 4.0, a new version observed in the wild.
July 10, 2024 / 14 minute read

In this Threat Analysis report, Cybereason Security Services investigate the rising activity of the malware GootLoader. GootLoader is a malware loader known to abuse JavaScript to download post-exploitation malware/tools and persist within the infected machine.
June 25, 2024 / 11 minute read

This supply chain attack targets to compromise the integrity of Secure Shell (SSH) - a cryptographic network protocol used to operate systems using remote command execution over an unsecured network.
May 29, 2024 / 7 minute read

In this Threat Analysis Report, Cybereason’s Security Research Team explores the security implications, vulnerabilities, and potential mitigation strategies surrounding Hidden VNC (hVNC) and Hidden RDP (hRDP).
May 6, 2024 / 9 minute read

AnyDesk, one of the world’s leading providers of Remote Management and Monitoring (RMM) software, confirmed they had identified a compromise of production systems.
March 22, 2024 / 3 minute read

In this Threat Analysis Report, Cybereason Security Services examines an incident on a Linux server, which saw malicious shell (bash) executions from a Java process running Apache ActiveMQ.
March 13, 2024 / 10 minute read

In this Threat Analysis Report, Cybereason Security Services dives into the Python Infostealer, delivered via GitHub and GitLab, that ultimately exfiltrates credentials via Telegram Bot API or other well known platforms.
March 5, 2024 / 9 minute read

Learn how to detect and prevent a new attack vector being exploited in low-burn, low-cost campaigns using compromised YouTube accounts to spread malware.
February 12, 2024 / 12 minute read

Cybereason issues Threat Alerts to inform customers of emerging impacting threats, including critical vulnerabilities such as the Ivanti Connect Secure VPN Zero-Day exploitation. Cybereason Threat Alerts summarize these threats and provide practical recommendations for protecting against them.
February 6, 2024 / 9 minute read

The execution of DarkGate Loader ultimately leads to execution of post-exploitation tools such as Cobalt Strike and Meterpreter. This Threat Alert provides an overview of an attack involving DarkGate Loader.
January 29, 2024 / 2 minute read

Cybereason issues Threat Alerts to inform customers of emerging threats, including critical vulnerabilities such as CitrixBleed. Cybereason Threat Alerts summarize these threats and provide practical recommendations for protecting against them.
December 18, 2023 / 3 minute read

The Cybereason Security Services Team is investigating incidents that involve variants of the DJvu ransomware delivered via loader payloads masquerading as freeware or cracked software.
November 28, 2023 / 2 minute read

Cybereason issues Threat Alerts to inform customers of emerging impacting threats, including new ransomware actors such as the emergent group INC Ransom. Cybereason Threat Alerts summarize these threats and provide practical recommendations for protecting against them.
November 20, 2023 / 3 minute read

In this Threat Analysis report, Cybereason investigates and explores various techniques for abusing the Windows Shortcut file format.
October 6, 2023 / 3 minute read

LockBit 2.0 ransomware attackers are constantly evolving and making detection, investigation, and prevention more complex by disabling EDR and other security products and deleting the evidence to stifle forensics attempts...
August 21, 2023 / 4 minute read

This Threat Analysis Report explores widely used DLL Side-Loading attack techniques, outlines how threat actors leverage these techniques, describes how to reproduce an attack, and reports on how defenders can detect and prevent these attacks...
October 26, 2022 / 13 minute read

In this edition of the Blue Team Chronicles, we assess the capabilities of eslogger, a new built-in macOS tool, and show how defenders can use this tool to better understand malicious activities on macOS and build new detection approaches...
October 4, 2022 / 8 minute read

The Cybereason GSOC Managed Detection and Response (MDR) Team is investigating incidents that involve exploitation of the critical Microsoft Exchange vulnerabilities (CVE-2022–41040 and CVE-2022–41082) dubbed ProxyNotShell after finding them being exploited in the wild...
October 3, 2022 / 5 minute read

Cybereason GSOC team analysts have analyzed a specific technique that abuses Notepad++ plugins to evade security mechanisms, achieve persistence and deploy backdoors on targeted machines...
September 14, 2022 / 4 minute read

PlugX is a post-exploitation modular RAT (Remote Access Trojan), which is known for its multiple functionalities such as data exfiltration, keystroke grabbing, backdoor functionality, and utilizing DLL-Sideloading techniques for evading security solutions...
September 8, 2022 / 10 minute read

Ragnar Locker is a ransomware family with security evasion capabilities which is targeting the energy sector and recently claimed to have breached DESFA, a Greek pipeline company...
September 1, 2022 / 8 minute read
First observed in June 2022 in the wild, HavanaCrypt Ransomware masquerades as a legitimate Google Chrome update with sophisticated anti-analysis techniques and other functionality that may be used for data exfiltration and privilege escalation...
August 22, 2022 / 5 minute read

A new and improved Redeemer 2.0 ransomware version was released on an underground forum and is described by the developers as a “C++ no dependency ransomware with no privacy intrusions” targeting the Windows OS with support for Windows 11 systems...
August 19, 2022 / 2 minute read

Cybereason GSOC observed distribution of the Bumblebee Loader and post-exploitation activities including privilege escalation, reconnaissance and credential theft. Bumblebee operators use the Cobalt Strike framework throughout the attack and abuse credentials for privilege escalation to access Active Directory, as well as abusing a domain administrator account to move laterally, create local user accounts and exfiltrate data...
August 17, 2022 / 10 minute read

In this article we take a deeper dive into an often abused Microsoft-signed tool, the infamous rundll32.exe, which allows adversaries to execute malicious code during their offensive operations through a technique which we explain in detail...
August 9, 2022 / 10 minute read

LockBit 2.0 ransomware attackers are constantly evolving and making detection, investigation, and prevention more complex by disabling EDR and other security products and deleting the evidence to stifle forensics attempts...
July 7, 2022 / 16 minute read

Raspberry Robin involves a worm that spreads over USB devices or shared folders, leveraging compromised QNAP (Network Attached Storage or NAS) devices as stagers and an old but still effective method of using “LNK” shortcut files to lure its victims...
July 7, 2022 / 5 minute read

In just two months, Black Basta has added nearly 50 victims to their list, making them one of the more prominent ransomware gangs. The attackers infiltrate and move laterally throughout the network in a fully-developed RansomOps attack. The Cybereason Nocturnus Team assesses the threat level as HIGH SEVERITY given the destructive potential of the attacks...
June 24, 2022 / 6 minute read

The AI-driven Cybereason XDR Platform detects and blocks MountLocker ransomware which launched back in September 2020. Since then, the attackers have rebranded the operation as AstroLocker, XingLocker, and now in its current phase, the Quantum Locker...
May 9, 2022 / 5 minute read

Cybereason recently an attack assessed to be the work of Chinese APT Winnti that operated undetected, siphoning intellectual property and sensitive data - the two companion reports examine the tactics and techniques of the overall campaign as well as more detailed analysis of the malware arsenal and exploits used...
May 4, 2022 / 4 minute read

Cybereason investigated multiple intrusions targeting technology and manufacturing companies located in Asia, Europe and North America. Based on the findings of our investigation, it appears that the goal behind these intrusions was to steal sensitive intellectual property for cyber espionage purposes...
May 4, 2022 / 11 minute read

This APT-C-23 campaign involves of two previously undocumented malware strains dubbed Barb(ie) Downloader and BarbWire Backdoor, which use an enhanced stealth mechanism to remain undetected - in addition, Cybereason observed an upgraded version of an Android implant dubbed VolatileVenom...
April 6, 2022 / 11 minute read

The surge of Emotet attacks targeting Japanese organizations in the first quarter of 2022 is a continuation of the earlier Emotet activity, with some changes in the malware deployment process. The Cybereason XDR Platform detects and blocks Emotet malware...
March 7, 2022 / 3 minute read

BlackCat Ransomware gained notoriety quickly leaving a trail of destruction behind it, among its recent victims are German oil companies, an Italian luxury fashion brand and a Swiss Aviation company. Cybereason XDR detects and blocks BlackCat Ransomware...
March 1, 2022 / 7 minute read

Ukrainian officials attributed the attack to Russia “preparing the ground” for a military invasion with nasty wipers dubbed WhisperGate and HermeticWiper. Cybereason Anti-Ransomware and Anti-MBR corruption technology detects and blocks WhisperGate and HermeticWiper...
February 15, 2022 / 2 minute read

Prior to the deployment of the Lorenz ransomware, the attackers attempt to infiltrate and move laterally throughout the organization, carrying out a fully-developed RansomOps attack - the Cybereason XDR Platform fully detects and prevents the Lorenz ransomware...
February 8, 2022 / 7 minute read

Cybereason discovered an undocumented RAT dubbed StrifeWater attributed to Iranian APT Moses Staff who deploy destructive ransomware following network infiltration and the exfiltration of sensitive data...
February 1, 2022 / 7 minute read

Cybereason discovered a new toolset developed by Iranian APT Phosphorus which revealed a connection to Memento ransomware and includes the newly discovered PowerLess Backdoor that evades detection by running PowerShell in a .NET context...
February 1, 2022 / 8 minute read

After exploitation of ProxyShell, attackers used Exchange to distribute phishing emails with the QBot payload and DatopLoader, a loader previously used to distribute the Cobalt Strike malware...
January 11, 2022 / 10 minute read

This report provides analysis on the evolution of configuration and implementation aspects of the StealBit malware developed by the LockBit ransomware group to exfiltrate sensitive data from targets for double extortion purposes…
December 16, 2021 / 20 minute read

Since the first Twitter post about this most recent discovery, the team at G DATA and the Cybereason SOC team have seen multiple Emotet samples in the wild, particularly between November 21-23, confirming that Emotet is reemerging...
December 9, 2021 / 3 minute read

The research findings highlight a disconnect between the risk ransomware poses to organizations during these off-hour periods and their preparedness to respond during weekends and into the holiday season...
November 17, 2021 / 4 minute read

This report provides an overview of key features of the Snake #malware and similarities discovered in the staging mechanisms with two other information-stealing malware variants, FormBook and Agent Tesla...
October 28, 2021 / 16 minute read

A threat actor has implanted malicious code in UAParser.js, a JavaScript library that parses User-Agent data where the implanted code deploys cryptocurrency-mining and information-stealing malware on compromised systems...
October 27, 2021 / 3 minute read

The highly-targeted attacks against aerospace and telecoms firms by new Iranian threat actor MalKamak includes newly discovered malware that evaded security tools since 2018 and abuses Dropbox services for command and control...
October 6, 2021 / 16 minute read

The PYSA ransomware gang uses tools like Koadic, PsExec and Mimikatz for credential theft and lateral movement before executing PowerShell scripts that stop or remove system security mechanisms like Windows Defender...
September 27, 2021 / 10 minute read

The Cybereason GSOC Managed Detection and Response (MDR) team is investigating CVE-2021-40444, a critical vulnerability in the Microsoft Hypertext Markup Language (MSHTML) web content rendering engine that Microsoft Office applications use...
September 10, 2021 / 3 minute read

The exploitation of the ProxyShell vulnerabilities enables attackers to execute arbitrary commands on compromised systems, which may lead to full system compromise and/or the deployment of malware...
August 30, 2021 / 3 minute read

Following the rise of the new LockBit2.0 and the attack against the global IT company Accenture, this report provides detailed information about the attack process and how the Cybereason Defense Platform detects and prevents this threat at several stages...
August 24, 2021 / 6 minute read

Cybereason discovered several previously unidentified attack campaigns targeting the telecoms industry across Southeast Asia assessed to be the work of several prominent Chinese APT groups...
August 3, 2021 / 27 minute read

The Cybereason Defense Platform detects and prevents Prometheus ransomware, a relatively new variant first observed in February of 2021 that has impacted more than 40 companies...
July 15, 2021 / 10 minute read

Cybereason detects and blocks REvil ransomware, protecting our customers and those of our Managed Services Provider partners in the wake of the Kaseya supply chain attacks...
July 6, 2021 / 5 minute read

PrintNightmare is a critical vulnerability in the Windows Print Spooler service that allows attackers to execute arbitrary code on target systems with administrative privileges...
July 2, 2021 / 3 minute read

SolarMarker enables attackers to execute commands, PowerShell scripts, and Windows executables on compromised systems, and to deploy additional malware...
June 23, 2021 / 3 minute read

A new global research study conducted by Cybereason reveals that the majority of organizations suffered significant business impact following a ransomware attack...
June 16, 2021 / 2 minute read

LemonDuck is a cryptocurrency-mining malware that in addition to mining, also spreads in a network after the initial infection with the goal to increase the number of systems that participate in its mining pool. ..
May 19, 2021 / 3 minute read
The campaign uses a disk space filler utility, a scenario not typical for ransomware where the disk space filler utility continuously writes files on a victim’s hard disk volumes until no free disk space is left available...
May 10, 2021 / 2 minute read

In a highly targeted operation by a Chinese APT, a newly discovered backdoor dubbed PortDoor is being used in attacks targeting a Russian defense contractor...
April 30, 2021 / 7 minute read

Cybereason Nocturnus Team has been tracking the Avaddon Ransomware since June 2020 and the double extortion model...
April 27, 2021 / 4 minute read

The multi-stage cryptocurrency botnet has been observed exploiting the Microsoft Exchange vulnerabilities associated with the HAFNIUM attacks to penetrate networks...
April 22, 2021 / 15 minute read

DarkSide ransomware follows the double extortion trend where the threat actors first exfiltrate the data and threaten to make it public if the ransom demand is not paid, rendering backing up data as a precaution against a ransomware attack moot...
April 1, 2021 / 6 minute read

The NetWalker ransomware has been targeting organizations in the US and Europe including several healthcare organizations, despite several known threat actors publicly claiming to abstain from targeting such organizations due to COVID-19.
February 16, 2021 / 4 minute read

The Cybereason Nocturnus Team has been tracking the activity around the RansomEXX, being used as a part of multi-staged human-operated attacks targeting various government related entities and tech companies.
January 26, 2021 / 4 minute read

Since first emerging in May 2020, the ransomware operators (aka. the Conti Gang) claim to have over 150 successful attacks with millions in extortion fees. Download the Indicator's of Compromise to search for Conti in your own environment.
January 12, 2021 / 5 minute read

Over the course of December, 2020, the Cybereason Nocturnus Team has been tracking down cyber crime campaigns related to the holiday season, and more specifically to online shopping. Download the Indicator's of Compromise to search for Dridex in your own environment.
December 24, 2020 / 6 minute read

The Cybereason Nocturnus team has been tracking the activity of the Cl0p ransomware, a variant of CryptoMix ransomware. Download the Indicator's of Compromise to search for Cl0p in your own environment...
December 23, 2020 / 3 minute read

On December 13, 2020, IT infrastructure management provider SolarWinds issued a Security Advisory regarding their SolarWinds Orion Platform after experiencing a “highly sophisticated” supply chain attack.
December 22, 2020 / 2 minute read

Security researchers observed a politically motivated APT called “Molerats” using three new malware variants to conduct espionage in the Middle East. Download the Indicator's of Compromise to search for Molerats in your own environment.
December 15, 2020 / 3 minute read

Ryuk ransomware is most often seen as the final payload in a larger targeted attack against a corporation, and since its return in September, it has been mainly delivered via TrickBot or BazarLoader infections.
December 10, 2020 / 3 minute read
The Cybereason Nocturnus Team has identified an active espionage campaign employing three previously unidentified malware variants that use Facebook, Dropbox, Google Docs and Simplenote for command & control and the exfiltration of data from targets across the Middle East.
December 9, 2020 / 2 minute read

There have been reports of MedusaLocker attacks across multiple industries, especially the healthcare industry which suffered a great deal of ransomware attacks during the COVID-19 pandemic.
November 19, 2020 / 4 minute read

The Cybereason Nocturnus Team has identified an active campaign targeting customers of a larger e-commerce platform with newly identified multi-stage malware that evades antivirus tools dubbed Chaes.
November 18, 2020 / 2 minute read
The Cybereason Nocturnus Team has been tracking a North Korean cyber espionage group known as Kimsuky and has identified a new spyware suite along with new attack infrastructure.
November 2, 2020 / 14 minute read

Nocturnus has been tracking the Evilnum group, targeting financial technology companies to spy and steal passwords, documents, browser cookies, email credentials and more.
September 3, 2020 / 9 minute read

Learn how the Bazar malware is sent via phishing emails that take advantage of the ongoing coronavirus pandemic, employee payroll reports, and customer complaints.
July 16, 2020 / 14 minute read

The Cybereason Nocturnus team is investigating a new campaign involving FakeSpy, an Android mobile malware used to steal SMS messages, send SMS messages, steal financial data, read account information and contact lists, steal application data, and do much more.
July 1, 2020 / 10 minute read

Earlier this year, Cybereason launched its latest honeypot to analyze the tactics, techniques, and procedures used by state-sponsored groups and cyber crime actors to target critical infrastructure providers.
June 11, 2020 / 6 minute read

The Valak Malware is a sophisticated malware that can steal enterprise mailing information and passwords along with the enterprise certificate. This has the potential to access critical enterprise accounts, causing damage to organizations, brand degradation, and ultimately a loss of consumer trust.
May 28, 2020 / 13 minute read

The Cybereason Nocturnus team is investigating EventBot, a new type of Android mobile malware. EventBot abuses accessibility features to steal user data from financial applications, read user SMS messages, and steal SMS messages to allow the malware to bypass two-factor authentication.
April 30, 2020 / 12 minute read

Cybereason Nocturnus is investigating a campaign where attackers are trojanizing multiple hacking tools with njRat, allowing the attackers to completely take over the victim’s machine.
March 10, 2020 / 8 minute read
Cybereason's Nocturnus team has been tracking recent espionage campaigns specifically directed at entities and individuals in the Palestinian territories.
February 13, 2020 / 7 minute read

Cybereason's Nocturnus team has been tracking recent espionage campaigns specifically directed at entities and individuals in the Palestinian territories.
February 13, 2020 / 11 minute read

Cybereason is following an active campaign to deliver multiple different types of malware to victims all over the world. This attack is able to steal data, mine for cryptocurrency, and in specific cases deliver ransomware.
February 5, 2020 / 9 minute read

Cybereason Nocturnus detected a series of attacks that started with a TrickBot infection and progressed into a hacking operation targeting sensitive financial systems using a new variant of Anchor_DNS and a new malware dubbed Anchor.
December 11, 2019 / 15 minute read
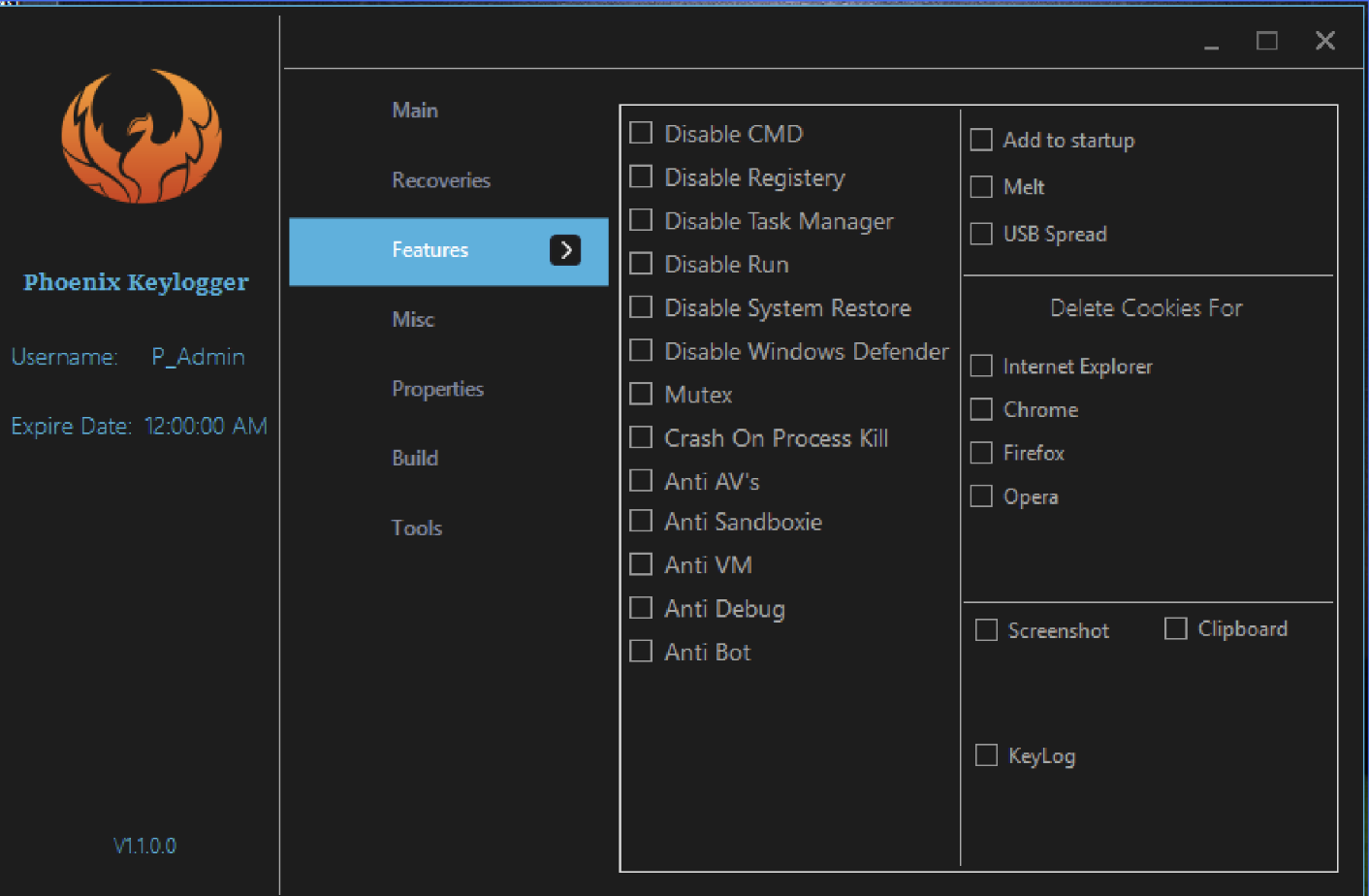
Nocturnus is tracking a new keylogger called Phoenix, packed with a myriad of information-stealing features extending far beyond logging keystrokes.
November 20, 2019 / 11 minute read
Nocturnus has investigated infections of the Raccoon stealer including its origin, team members, business model, and marketing efforts. We also cover Racoon's current capabilities and delivery methods, with a look into their future plans for the malware.
October 24, 2019 / 14 minute read
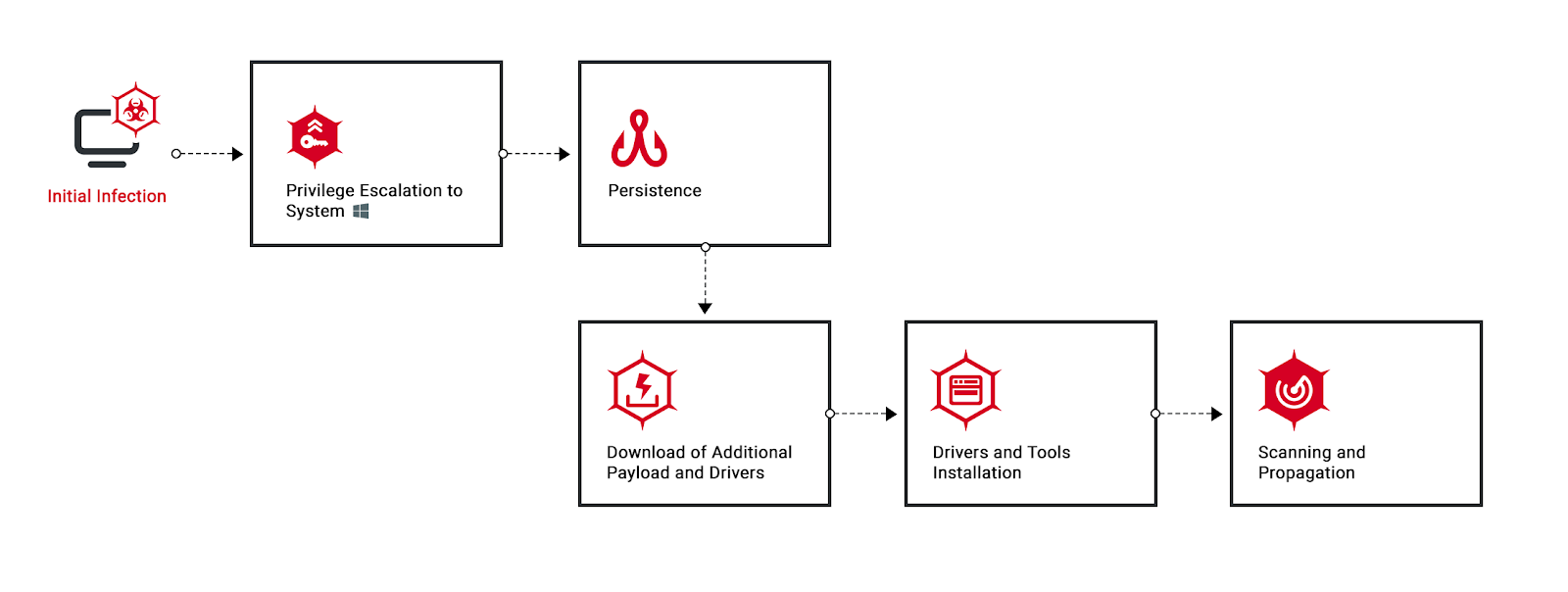
The Nocturnus team has identified variants of Glupteba that made use of an extensive arsenal, including LOLBins and a cryptocurrency miner.
September 12, 2019 / 15 minute read

Cybereason has been tracking REvil/Sodinokibi since 2019 - the Cybereason Defense Platform detects and blocks this nasty ransomware that struck meatpacker JBS...
August 5, 2019 / 8 minute read

In 2018, the Cybereason Nocturnus team identified Operation Soft Cell, an advanced, persistent attack targeting global telecommunications providers.
June 25, 2019 / 16 minute read

There’s an active, ongoing campaign exploiting a widespread vulnerability in linux email servers. Read about the attack first here.
June 13, 2019 / 6 minute read

In this research, we introduce a meticulously planned, malicious operation against a financial institution in April of 2019 by TA505.
April 25, 2019 / 11 minute read
Get the latest research, expert insights, and security industry news.
Subscribe