This month Cybereason has released some exciting new features that bring additional functionalities that drastically improve how defenders can predictively prevent, detect and respond to known and emerging threats.
This release was packed with enhancements including new user roles, groups and logic to support federated management and automation from the platform, deeper data analysis, rapid investigation improvements, advanced exclusion controls, and much more.
Customers can read the complete release notes on The Nest. For this post, we’ll focus on the improvements in the areas of prevention, detection and response:
Preventative Controls:
Decrease attack surface with Endpoint Controls enhancements
The Cybereason Endpoint Controls are highly effective at reducing the overall attack surface and preventing threats that would be propagated through these vectors.
We’ve expanded this functionality to Linux, added support for a broader set of devices including Media Transfer Protocol (MTP) devices, and added configurable permissions so we can now control if a USB mass storage device is permitted for full access, read-only or completely blocked from use.
Learn more about Cybereason Endpoint Controls here.
Prevent script-based attacks with improvements to fileless protection
Cybereason has been leading the industry with our ability to block fileless attacks by monitoring .NET and PowerShell scripts for anomalous behavior.
With this release, we now also integrate with Microsoft Antimalware Scan Interface (AMSI) on Windows systems. Cybereason can now additionally protect against attacks that exploit JScript, VBScript, Office macros and Windows Management Instrumentation (WMI).
Learn more about Cybereason Fileless Protection here.
Improve the posture of Linux systems with proactive scanning and machine isolation
Building upon the execution protection our NGAV offers for Linux, you can now proactively schedule scans or request on-demand scans to identify malicious files on Linux machines before execution.
Cybereason customers have enjoyed the ability to isolate Windows machines that have been impacted by malicious activity as an effective method to contain threats. With this release, Linux machines can now also be isolated.
Learn more about Cybereason NGAV here.
Detection
Decrease investigation time with improved MITRE tagging and investigation
MITRE ATT&CK provides a common language across the industry, allowing defenders to join together in the fight against malicious actors.
We’ve improved the way MITRE ATT&CK tactics, techniques, and sub-techniques are shown in the Cybereason MalOp™. These details are now shown as an interactive tag, delivering deeper context and providing a direct link to MITRE’s website for further details:
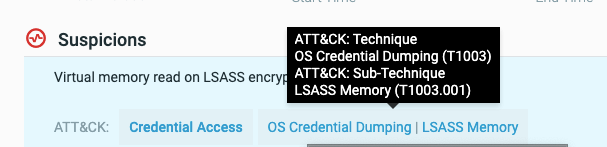
We’ve also improved our investigation interface to enable searching across all activity in your environment using the shorthand MITRE ID:
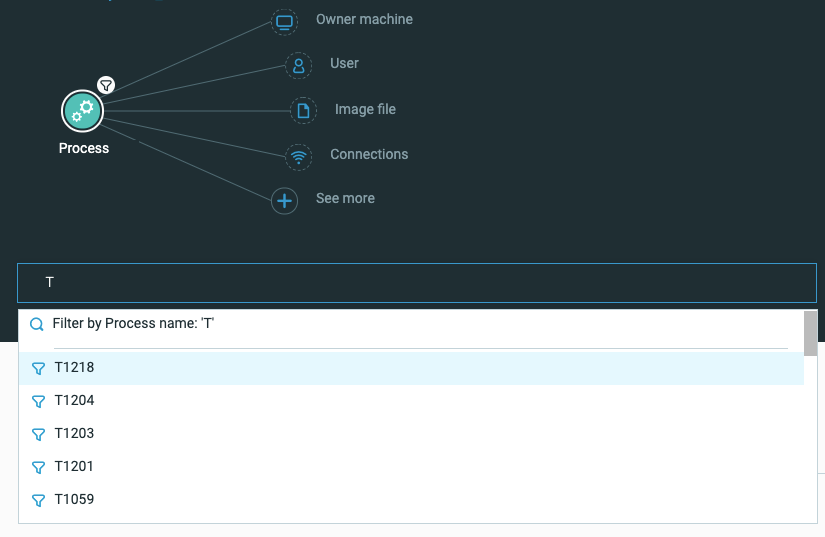
Searching across the threat data for occurrences of a MITRE ATT&CK technique
Learn more about our MalOp here, and our results in the most recent MITRE test here.
New OS Support
With this release we now support the deployment of sensors on machines running the following operating systems:
-
- Windows 11
- Windows 10 21H1
- SLES 15
A full list of supported operating systems is available for customers in the Nest.
Response
Respond faster with incident response tools deployment
Incident responders around the world deploy Cybereason as their core technology platform during incident response engagements. Many responders will often look to employ additional tools they have built in-house, acquired from an open-source project, or purchased from a third-party vendor.
With this new release, you can now upload and deploy incident response tools to any machine with a Cybereason sensor installed. After the tool deployment completes, you can run the tool using the tool’s native functionality and commands, and collect the results after the tool finishes running.
This level of flexibility is unparalleled by other solutions leveraged in incident response engagements--providing the full suite of tooling your team needs to contain, scope and remediate an attack.
Prevention, Detection and Response
This latest release is our next step to empowering defenders and reversing the adversary advantage. Customers can read the complete release notes in The Nest.
Cybereason is dedicated to teaming with defenders to end ransomware attacks on the endpoint, across the enterprise, to everywhere the battle is taking place. Learn more about the recently released Cybereason Predictive Ransomware Protection solution, browse our ransomware defense resources, or schedule a demo today to learn how your organization can benefit from an operation-centric approach to security.
