Cybereason issues Threat Analysis reports to explore widely used attack techniques, outline how threat actors leverage these techniques, describe how to reproduce an attack, and report how defenders can detect and prevent these attacks.
In this Threat Analysis report, Cybereason investigates and explores various techniques for abusing the Windows Shortcut file format.
KEY POINTS
- Widely popular for initial infection and persistence: The Cybereason Security Services team has observed a serious uptick in malwares being delivered through shortcut files, likely due to recent changes Microsoft has made regarding macro enabled files downloaded from the internet.
- Easily combined with a variety of attack techniques: The flexibility of the file format makes it easy to use shortcut files alongside attacks such as DLL-Sideloading and “Fileless” attack types with PowerShell or Lolbins.
- Challenging to block: While this is still a binary file type, shortcut files are benign by themselves since they are simply a pointer to another resource. Shortcut files are also a key component of the Windows operating system, making it impossible to ban them outright.
WHAT’S HAPPENING?
The analysis report focuses on different use cases for short LNK files such as weaponization, investigation, detections and threat hunting. Any Windows environment would be affected by this type of file (mis)use.
RedTeam: Weaponizing LNK Files
In the full report, we cover how LNK files can be leveraged for malware delivery, from the offensive security perspective. We demonstrate how to create a LNK file that executes a malicious payload (reverse shell) and how to use LNK properties to make that persistent on the system. We also cover a few tools that automate the creation of malicious LNK files.
BlueTeam: Analysis of LNK File Attacks
In this section, we analyze well known and very pervasive attack campaigns from Astaroth, IcedID and Qbot as well as looking at the persistence technique employed by Yellow Cockatoo. We also include a static analysis of the LNK file format.
PurpleTeam: Detection and Hunting Strategies
In our final section, we cover various configuration options in the Cybereason product to make detection and hunting of LNK files more effective. Several techniques for hunting these behaviors are explored as well.
WHAT ARE LNK FILES?
Also known as a ‘link’ file, the Windows Shortcut File (LNK) is a Windows proprietary format specification that allows users to create a graphical ‘pointer’ to a file, command, network share, etc.
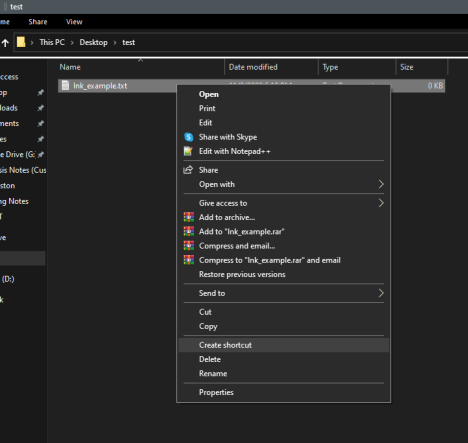
Shortcut Creation from Windows Menu
LNK files are usually created automatically in the Recent Files or Quick Access section of the Windows Explorer. They can also be created on demand by right clicking a file and selecting
Create shortcut.
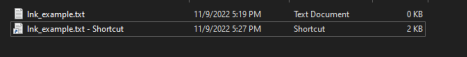
Original File and Shortcut
Shortcuts can be edited by right clicking on the LNK file and selecting Properties. This allows the user to edit the various attributes on the shortcut file such as target, directory, and icon.
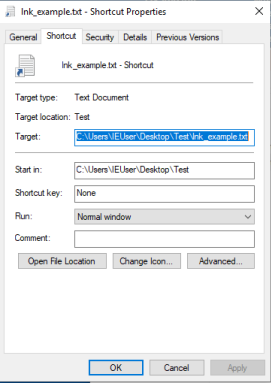
LNK File Properties
How Can LNK Files Be Abused?
As mentioned above, shortcut files are really just pointers to another resource. This makes it simple to use LNK files to:
- run specific cmd.exe commands
- run a PowerShell ‘one-liner’
- execute hidden files in a directory.
Another attribute of shortcut files is that even with “Hide Extensions for Known File Types” disabled, shortcut files never show the “.lnk” extension. This can ease phishing attacks as the shortcut and the actual file are almost identical in appearance.
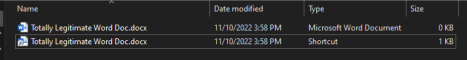
Example of Shortcut File Not Showing the “.lnk” Extension
CYBEREASON RECOMMENDATIONS
For Cybereason Customers - Baseline and enable File Event Collection in your sensor policies. This will allow you to see file creation events for non-executable files such as LNK files. For additional information, please refer to the File Events section under PurpleTeam: Detection and Hunting Strategies.
Hunt - Hunt for suspicious child processes of explorer.exe that don’t appear to have executed directly from user interaction. Correlate these timestamps with file creation events. An example use case is demonstrated in the Explorer as the initiating process section of PurpleTeam: Detection and Hunting Strategies.
Additionally, follow the campaigns of threat actors such as IcedID that utilize LNK files in their TTPs. This could point to additional techniques that could be useful in hunting activities.
Follow Security Best Practices - LNK files are usually delivered through phishing. Configure your email security device to inspect attachments and quarantine potentially suspicious content such as LNK files as attachments or archive files that contain Windows shortcuts (.lnk files).
Additional best practices can include using Group Policy to automatically show hidden files that may be delivered with LNK files and limiting access to the Windows Startup folder on end user workstations.
DOWNLOAD THE FULL THREAT ANALYSIS
This blog post is a summary of a full 47-page Threat Analysis Report (PDF)
About The Researcher
 Derrick Masters
Derrick Masters
Principal Security Analyst, Cybereason Global SOC
Derrick Masters is a Senior Security Analyst with the Cybereason Global SOC team. He is involved with threat hunting and purple teaming. Derrick's professional certifications include GCFA, GCDA, GPEN, GPYC, and GSEC.
Cybereason is dedicated to teaming with Defenders to end cyber attacks from endpoints to the enterprise to everywhere. Learn more about Cybereason XDR, check out our Extended Detection and Response (XDR) Toolkit, or schedule a demo today to learn how your organization can benefit from an operation-centric approach to security.








 Derrick Masters
Derrick Masters