The Cybereason Global Security Operations Center (GSOC) Team issues Threat Analysis Reports to inform on impacting threats. The Threat Analysis Reports investigate these threats and provide practical recommendations for protecting against them.
In this Threat Analysis Report, the Cybereason GSOC investigates the Ragnar Locker malware family, a ransomware and a ransomware operator which has recently claimed to have breached DESFA, a Greek pipeline company.
This report provides context over this recent breach as well as an overview of the Ragnar Locker ransomware through a dynamic analysis and a reverse engineering analysis.
Key Findings
- Breach of a Pipeline Company : DESFA is a strategic energy-related company that has been claimed by Ragnar Locker as their victim.
- Security Evasion Capabilities : Ragnar Locker checks if specific products are installed, especially security products (antivirus), virtual-based software, backup solutions and IT remote management solutions.
- Ransomware Actors Targeting the Energy Sector : This is the second important pipeline company that has been hit by ransomware, along with Colonial Pipeline. Furthermore, four energy companies have been hit recently by ransomware, including three in Europe.
- Active for Three Years : Ragnar Locker is both a ransomware group and the name of the software in use. They have been running since 2019 and targeting critical industries. They use the double extortion scheme.
- Excluding the Commonwealth of Independent States : Ragnar Locker avoids being executed from countries since the group is located in the Commonwealth of Independent States (CIS).
The Cybereason Defense Platform can effectively detect and prevent Ragnar Locker ransomware:
Cybereason Defense Platform Detects and Blocks Ragnar Locker Ransomware
Introduction
The Cybereason GSOC is investigating the Ragnar Locker ransomware following a recent breach that was reported by Ragnar Locker, on a Greek pipeline company named DESFA:

Ragnar TOR page claiming they breached DESFA
This is not the first occurrence of ransomware attacks on pipeline companies: Colonial Pipeline was breached in March 2021, and this event still haunts industrial companies due to the impact it had on production.
Additionally, this is one of the four energy providers that were hit by ransomware recently, including other ones in Europe:
Finally, Greece has an extremely strategic place for energy since gas from other places (Israel, for instance) flows to Europe.
Ragnar Locker is ransomware that has been in use since at least December 2019, and is generally aimed at English-speaking users. The Ragnar Locker ransomware has been on the FBI’s radar since the gang breached more than fifty organizations across ten critical infrastructure sectors.
Ragnar Locker matches both the name of the ransomware group and the name of the ransomware binary. In this Threat Analysis Report, we detail the mechanisms driving Ragnar Locker through dynamic and static analysis of two samples.
Technical Analysis
The corresponding samples of Ragnar Locker that we analyzed differentiate themselves from the other ransomwares by their size (from 53KB to 100KB):
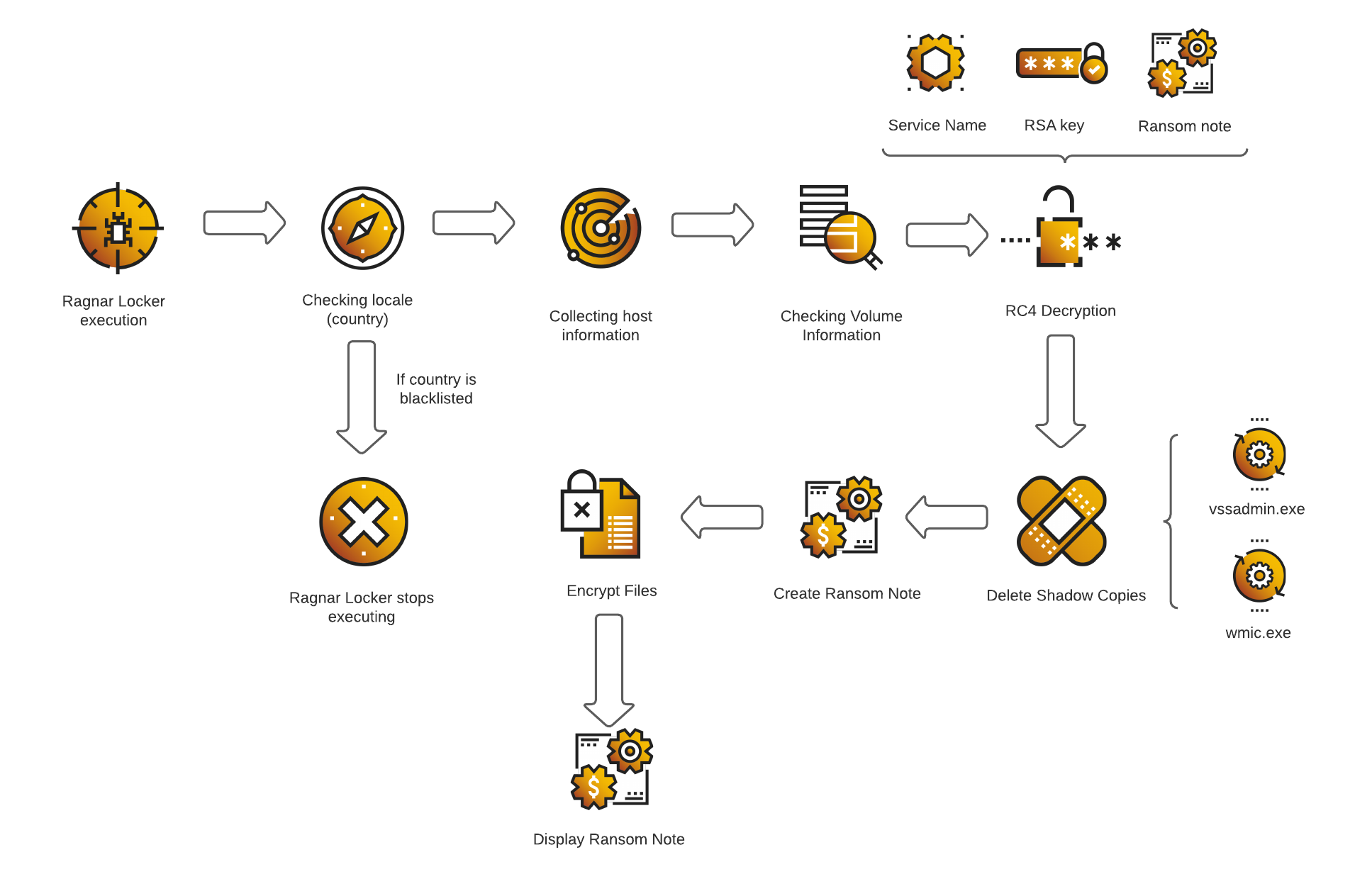
Ragnar Locker Execution Flow
In the following sections, we first analyze Ragnar Locker dynamically through the Cybereason Defense Platform. Next, we analyze Ragnar Locker more deeply, through static analysis.
Analysis with the Cybereason Defense Platform
In this section, we analyzed the sample used in the attack through our Cybereason Defense Platform.
Ransomware Detonation
We start this analysis by detonating one sample into a constrained laboratory live environment equipped with a Cybereason sensor:
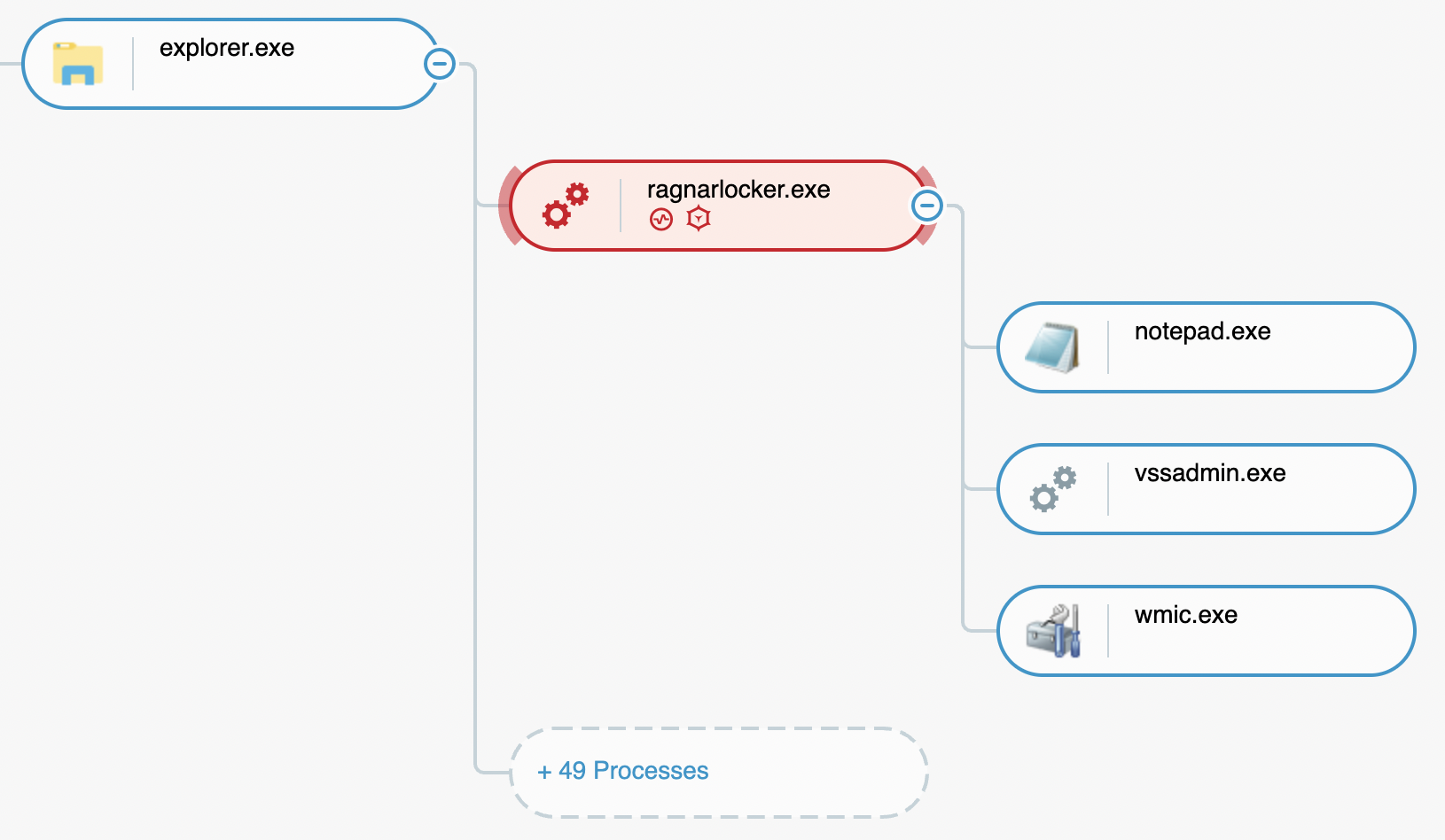
Cybereason Defense Platform process tree view
As a result of the execution, we can observe a MalOp is created with the Ransomware detection type:
 MalOp created following the launch of Ragnar Locker
MalOp created following the launch of Ragnar Locker
Further analysis of the behaviors associated with this detonation, we observe the launch of three additional processes, chronologically:
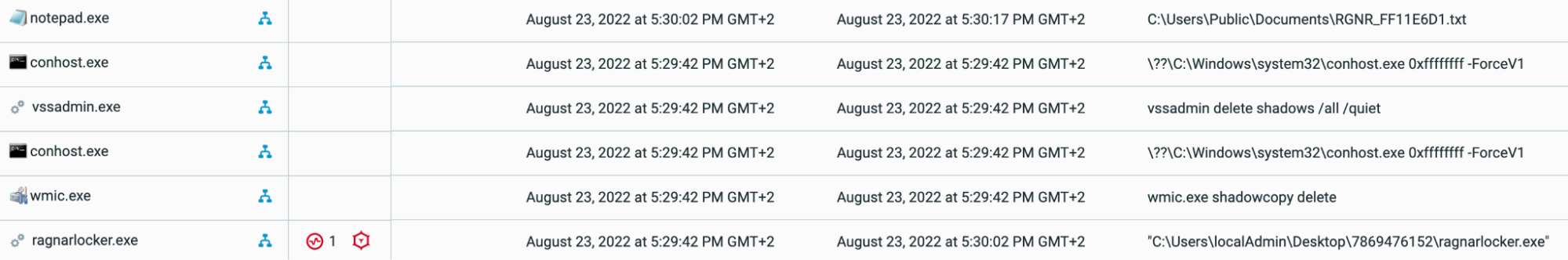
Chronologically ordered (more recent at the top) processes resulting from Ragnar Locker execution
Ragnar Locker spawns the following children process:
- wmic.exe shadowcopy delete: This system command deletes all shadow copies on the victim’s system, preventing data recovery by the victim
- vssadmin delete shadows /all /quiet: This system command also deletes shadow copies, preventing data recovery by the victim
- notepad.exe [User path]\RGNR_AABBCCDD.txt : This command launches Notepad.exe to show the ransom note to the victim
MITRE ATT&CK lists both shadow copy deletion techniques:
Looking at the “Ragnar Locker.exe” process, we observe that it contains 1081 file events, related to the encrypted files, and their new path, for instance:
c:\users\localadmin\appdata\local\packages\microsoft.windows.cortana_cw5n1h2txyewy\localstate\devicesearchcache\appcache133057346751796032.txt.ragnar_aabbddcc
New path after rename event
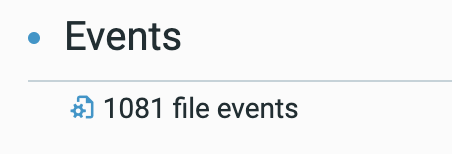
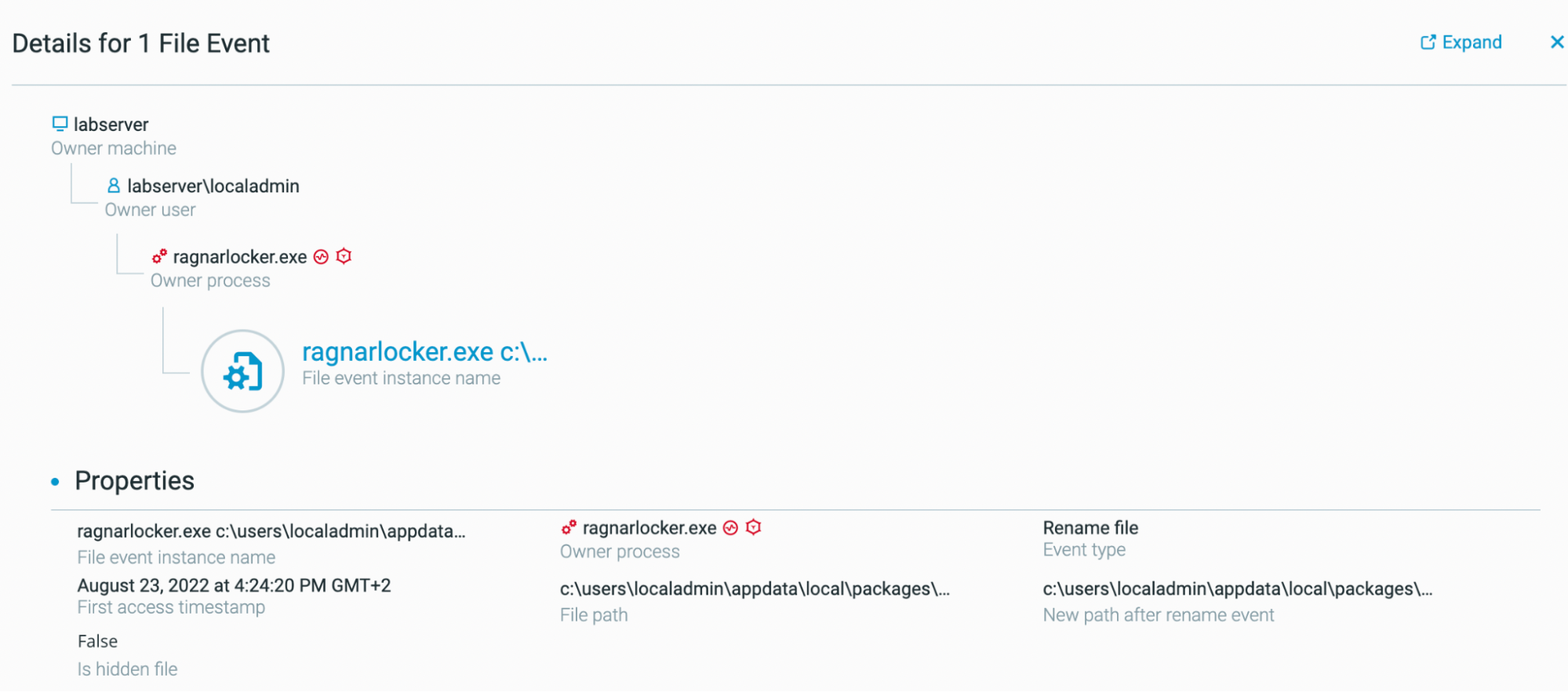 “Ragnar Locker.exe” process properties, as seen in the Cybereason Defense Platform
“Ragnar Locker.exe” process properties, as seen in the Cybereason Defense Platform
Additional Sysmon telemetry was set up on the machine, resulting in observing the modification of strategic directories, due to the ransom note creation:
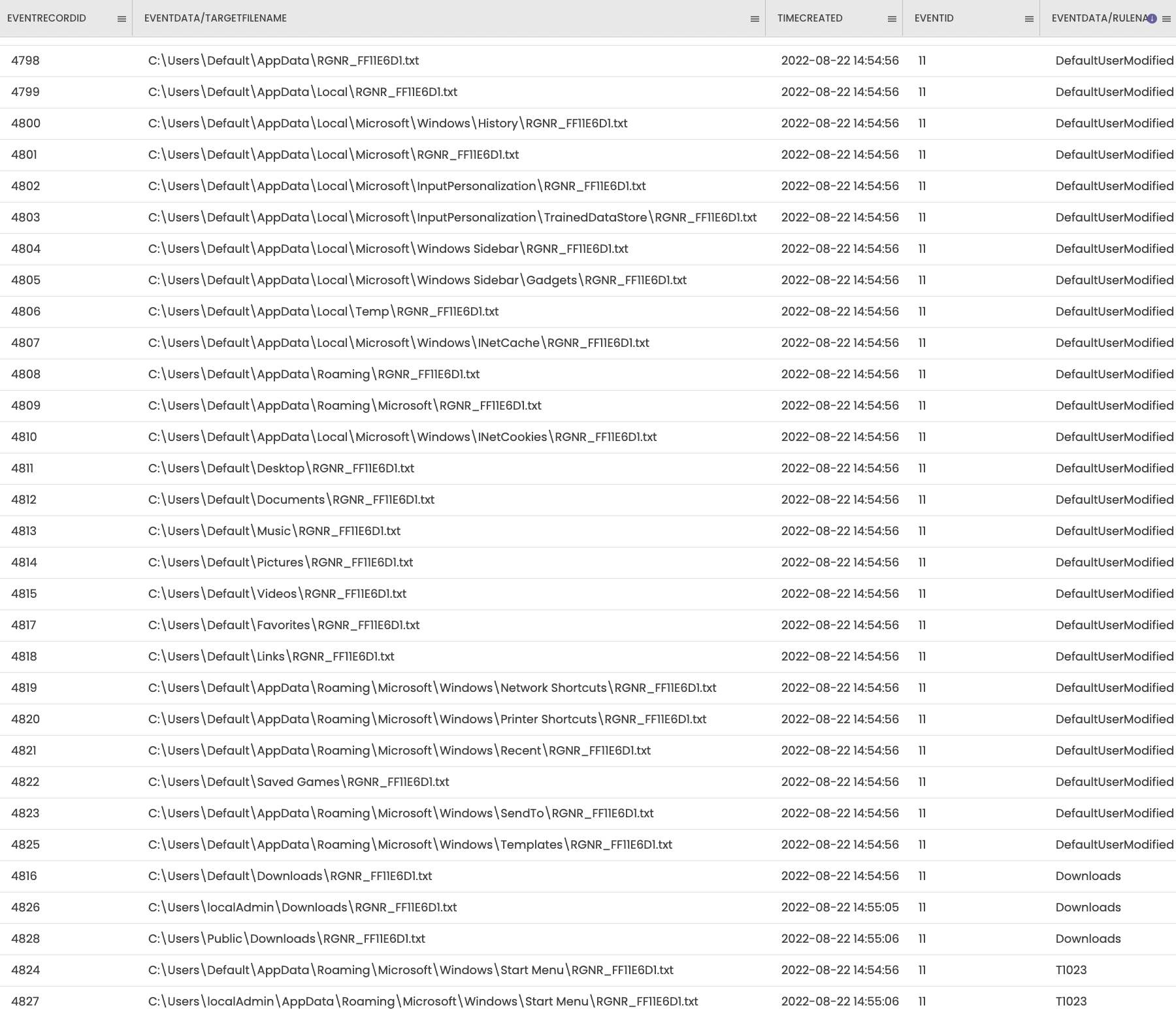
Extract from Sysmon event logs
We did not observe any network connection following the ransomware execution, nor registry value manipulation.
Ransomware Note
A few seconds following the ransomware execution , as seen from the process tree, Ragnar Locker drops a ransomware note configured with the name of the victim, named “RGNR_AABBCCDD.txt”, and opens a Notepad with this file:
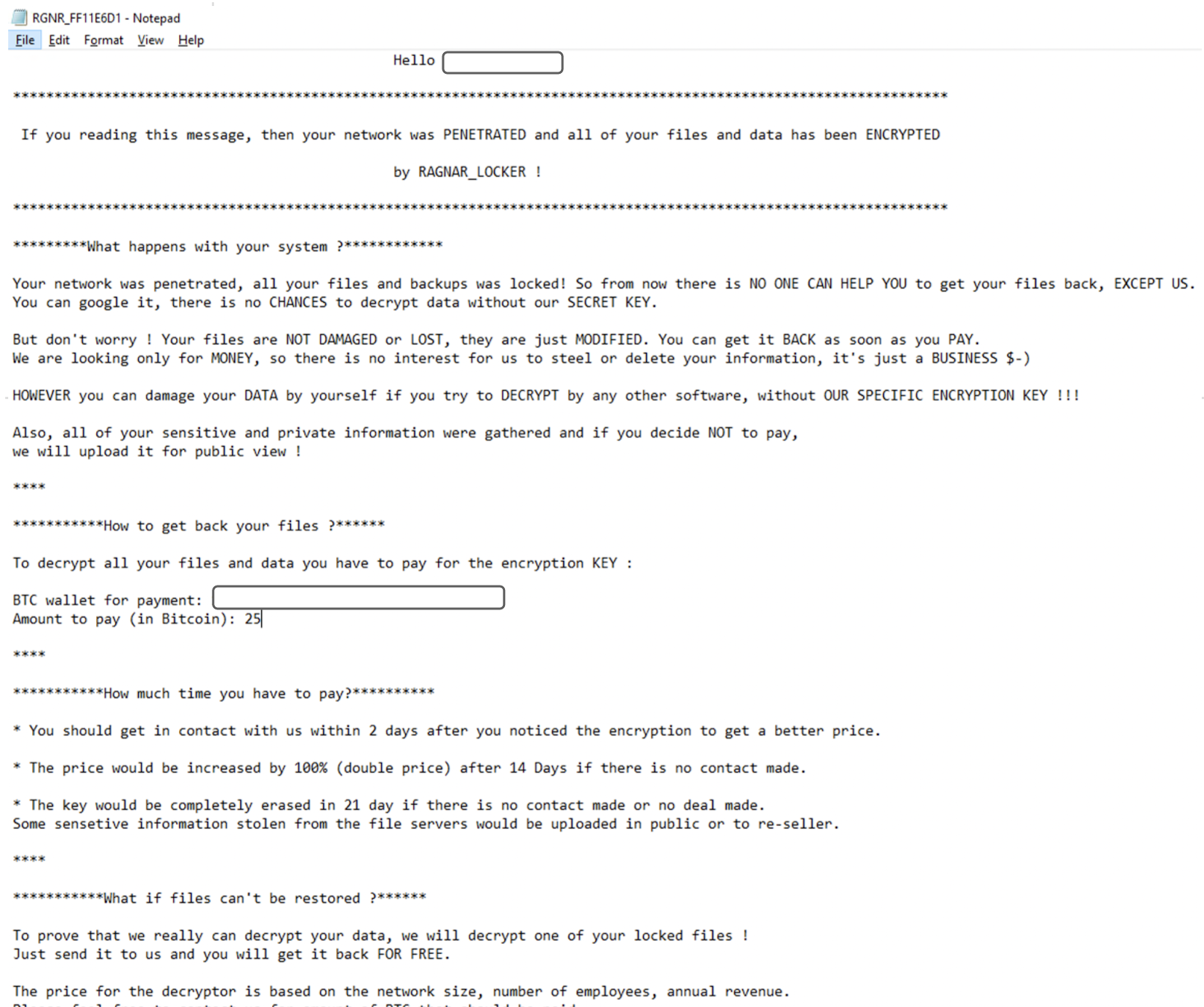 Ransomware Note as seen by the victim
Ransomware Note as seen by the victim
Ragnar Locker Sample Reverse Engineering
In this section, we analyzed the sample used in the attack, this time through static analysis and advanced dynamic analysis, allowing us to dig deeper into this binary’s goal and mechanisms.
Checking System Location
The first activity Ragnar Locker perform is to check if the infected machine’s locale matches with one of the following countries:
- Azerbaijan
- Armenia
- Belarus
- Kazakhstan
- Kyrgyzstan
- Moldova
- Tajikistan
- Russia
- Turkmenistan
- Uzbekistan
- Ukraine
- Georgia
If this matches, Ragnar Locker does not execute and the process is terminated. This list matches with the countries found in the Commonwealth of Independent States CIS:
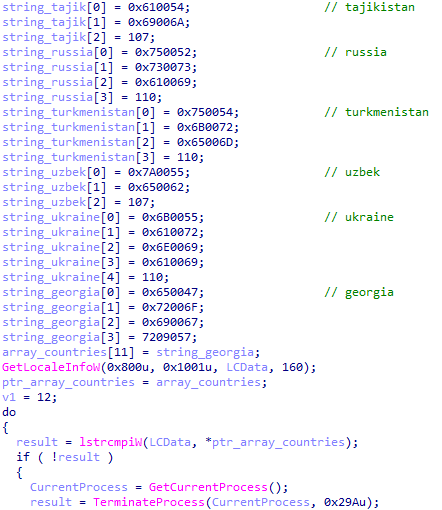
Ragnar Locker check countries locale value through GetLocaleInfoW
Collecting Host Information
Next, the ransomware extracts information about the infected machine. First, it collects the computer name and the user name using the API calls GetComputerNameW and GetUserNameW.
Then, the ransomware queries the registry to collect the machine GUID and Windows version:
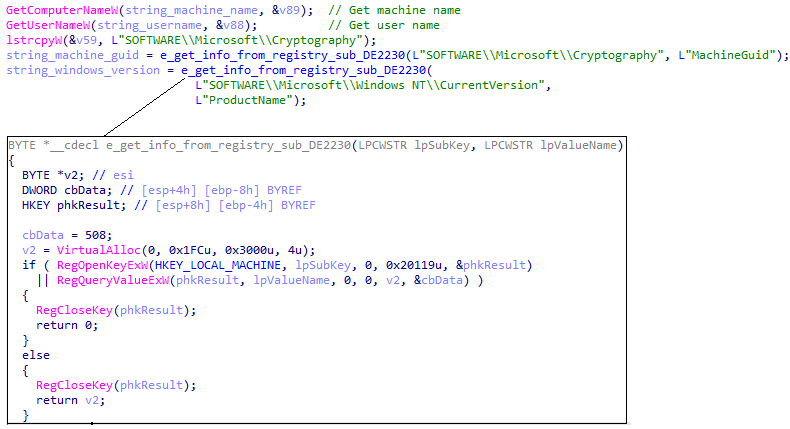 Collecting info on the host
Collecting info on the host
This collected information is concatenated and goes through a custom hashing function, in order to conceal the data:
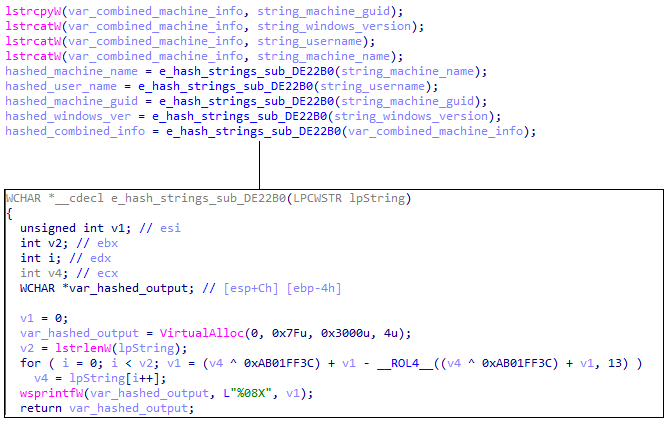 Ragnar Locker custom hashing algorithm
Ragnar Locker custom hashing algorithm
Ragnar Locker then creates a new event using the CreateEventW API call, and uses the combined hashes as the name of the event:
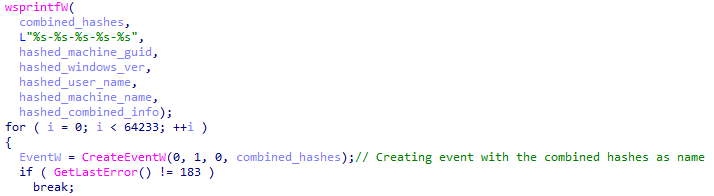 Creating event with combined hashes (static view)
Creating event with combined hashes (static view)
When running the sample through a debugger, the combined hashes look as following:
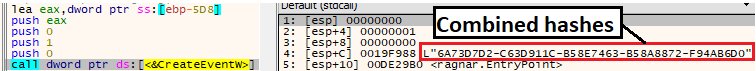 Creating event with combined hashes (dynamic view)
Creating event with combined hashes (dynamic view)
File Volumes Identification
Next, Ragnar Locker attempts to identify the existing file volumes on the host. It uses the Windows APICreateFileW to:
- Get a handle to a physical drive
- Query the drive using DeviceIoControl
- Iterate through the volumes using FindFirstVolumeA and FindNextVolumeA
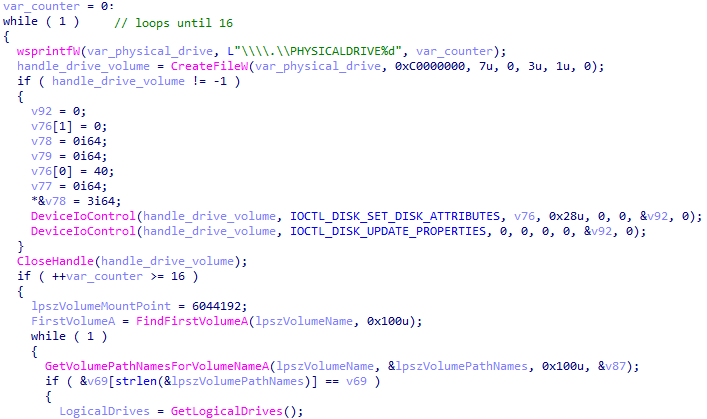 Iterating through machine volumes
Iterating through machine volumes
Embedded RC4 Content
Ragnar Locker contains hidden content embedded in the binary sections. Ragnar Locker decrypts this content during runtime using the RC4 cryptographic algorithm:
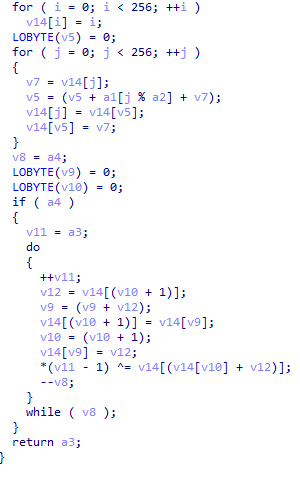 Custom RC4 algorithm
Custom RC4 algorithm
The custom RC4 algorithm function is executed several times and decrypts a list of services names:
- vss, sql, memtas, mepocs, sophos, veeam, backup, pulseway, logme, logmein, connectwise, splashtop, kaseya, vmcompute, Hyper-v, vmms, Dfs.
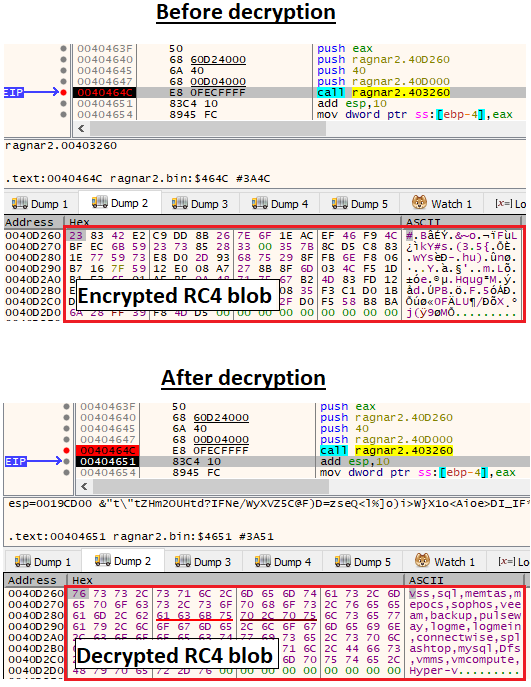 Decrypted RC4 services names
Decrypted RC4 services names
Then, Ragnar Locker iterates through the running services of the infected machines. If one of the decrypted services is found, Ragnar Locker terminates it:
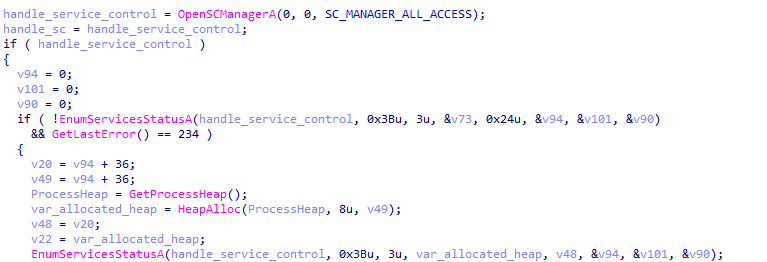 Enumerating the machine’s services
Enumerating the machine’s services
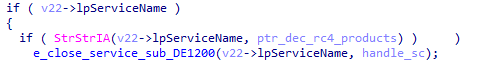 Checking if the targeted service exist
Checking if the targeted service exist
Ragnar Locker then decrypts an embedded RSA public key:
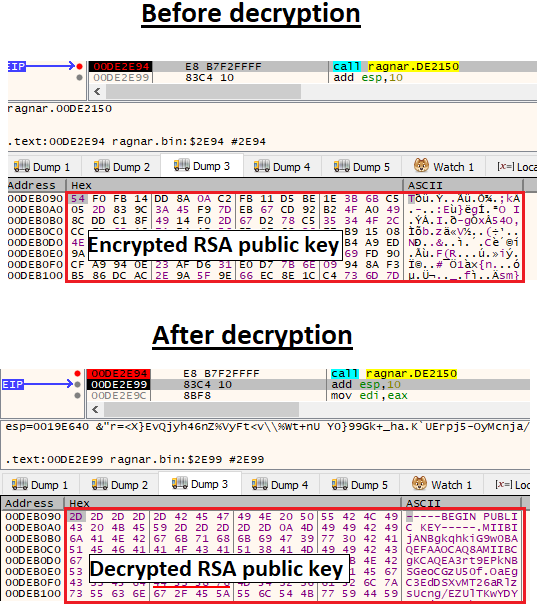 Decrypted RSA public key
Decrypted RSA public key
After decrypting the public key, Ragnar Locker passes the key to another function that prepares the key for further use:
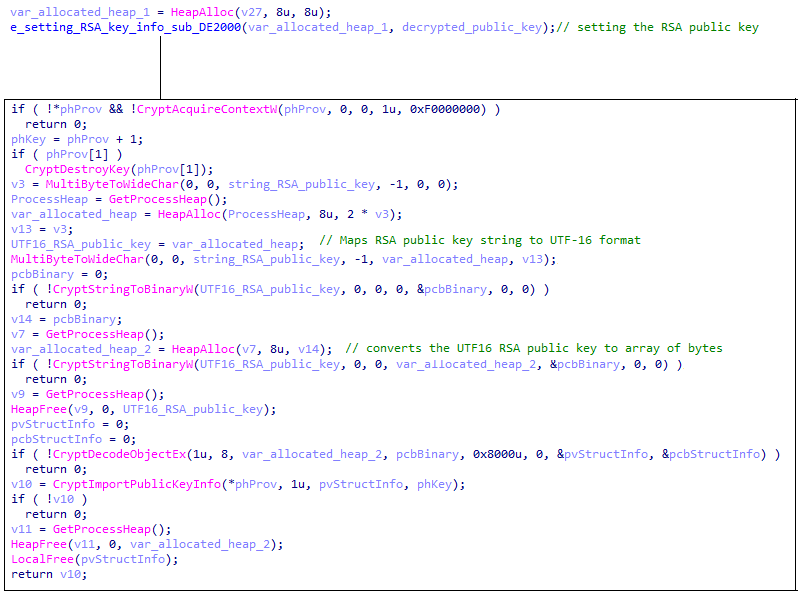 Preparing the key for encryption
Preparing the key for encryption
Lastly, Ragnar Locker decrypts the ransom note’s content:
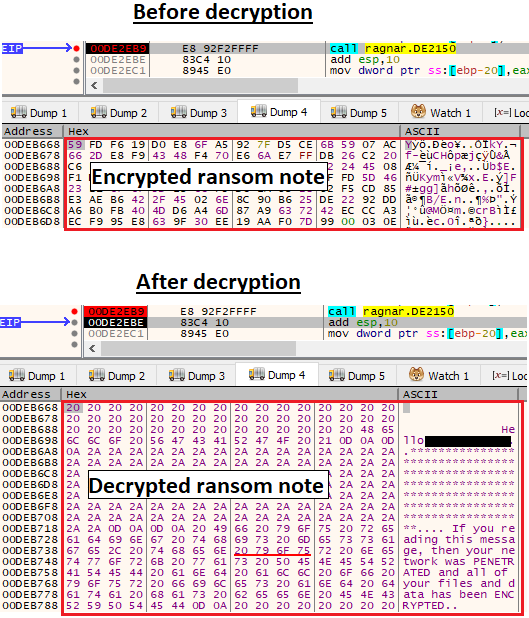 Decrypted ransom note through the RC4 routine
Decrypted ransom note through the RC4 routine
Deleting Shadow Copies
In order to delete the machine’s shadow copies, Ragnar Locker executes the processes vssadmin.exe and Wmic.exe with the following command lines:
- Vssadmin delete shadows /all /quiet
- Wmic.exe shadowcopy delete
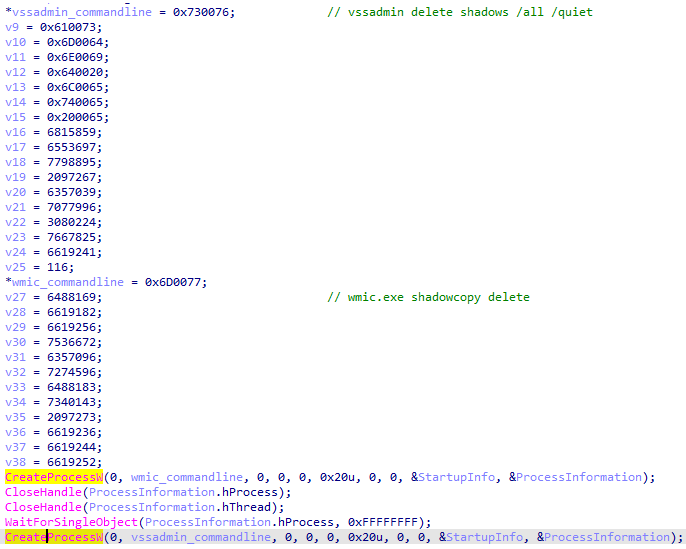
Deleting shadow copies using Wmic and Vssadmin
Creating the Ransom Note
Ragnar Locker generates the ransom note file name through the following algorithm:
- It gets the computer name using the API call GetComputerNameW
- It hashes the computer name using the custom hashing algorithm mentioned above
- It concatenates the strings “\\“, “RGNGR_”, “.txt” with the hashed computer name
- It completes the full name by concatenating the path “C:\Users\Public\Documents”, resulting in “C:\Users\Public\Documents\RNGR_[hash].txt”
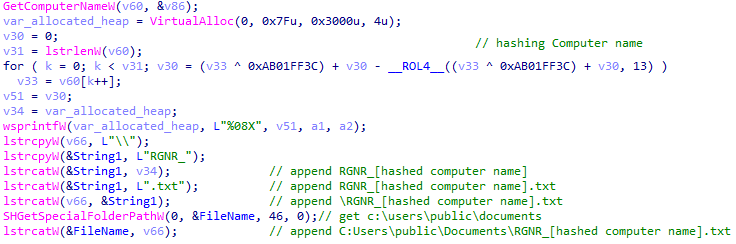 Preparing the txt file that holds the ransom note
Preparing the txt file that holds the ransom note
Eventually, Ragnar Locker calls CreateFileW to create the requested text file with the required path. Ragnar Locker then writes a decrypted ransom note at this path.
In addition, after writing the note, Ragnar Locker writes another smaller part starting with “---RAGNAR SECRET—-”. This part is the output of the API call CryptBinaryToStringA:
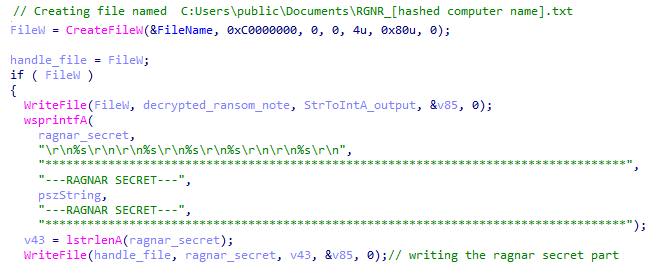 Creating the txt file that holds the ransom note
Creating the txt file that holds the ransom note
 Ragnar secret example output
Ragnar secret example output
Encrypting the Files
After creating the ransom note, the actual file encryption process ignites. First, Ragnar Locker gets the drives (except DRIVE_CDROM) and directories, and sends the string of the file to be encrypted to an encryption function.
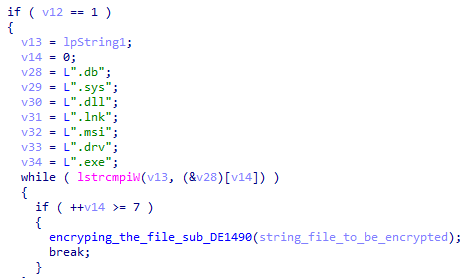
The encryption function first checks for some files to be excluded from the encryption process, those files are:
- Autoruns.inf, boot.ini, bootfront.bin, bootsect.bak, bootmgr, bootmgr.efi, bootmgfw.efi, desktop.ini, iconcache.db, ntldr, ntuser.dat, ntuser.dat.log, ntuser.ini, thumbs.db
 List of excluded files
List of excluded files
In addition, other specific processes and objects are excluded, such as:
- Windows.old, Tor Browser, Internet Explorer, Google, Opera, Opera Software, Mozilla, Mozilla Firefox, $Recycle.bin, ProgramData, All Users
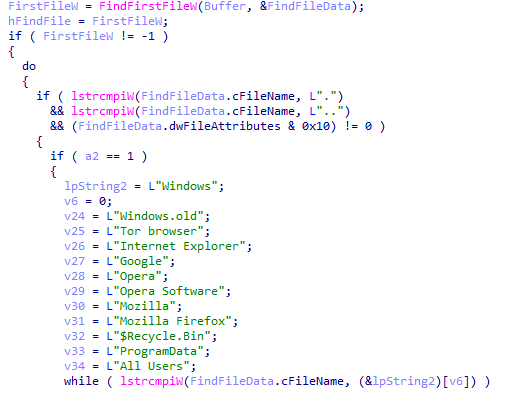 Files and processes to exclude
Files and processes to exclude
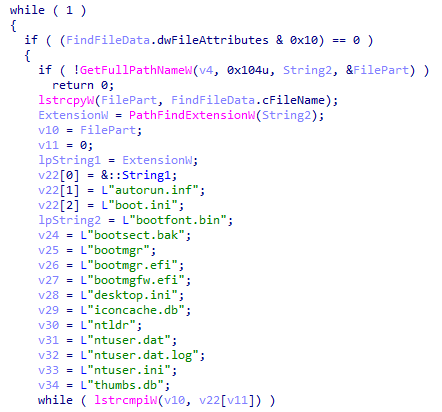
Lastly, the last checks of Ragnar Locker excludes files with the following extension:
- .db, .sys, .dll, lnk, .msi, .drv, .exe
 File extensions to exclude
File extensions to exclude
Once the file meets the criteria, the file name is sent to a function that encrypts the corresponding file using the Salsa20 algorithm. After each encryption, Ragnar Locker appends the suffix “.ragnar_[hashed computer name]” to the affected file:
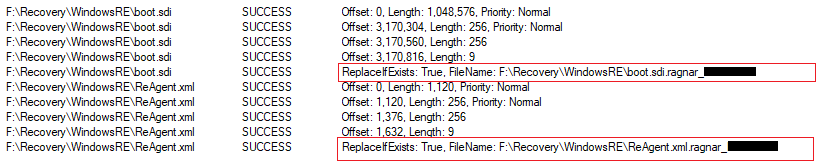 Files manipulated by encryption
Files manipulated by encryption
Displaying the Ransom Note
Following the machine encryption, Ragnar Locker creates a notepad.exe process that presents the ransom note to the user’s screen with the ransom and payment information.
Ragnar Locker spawns this process through the following way:
- Getting a handle to the current process token
- Duplicate the token
- Setting the token to elevate privileges
- Use CreateProcessAsUserW with the elevated token
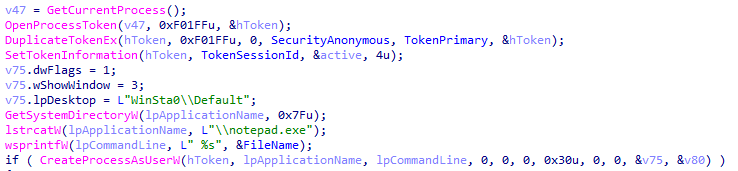 Creating notepad process to display ransom note
Creating notepad process to display ransom note
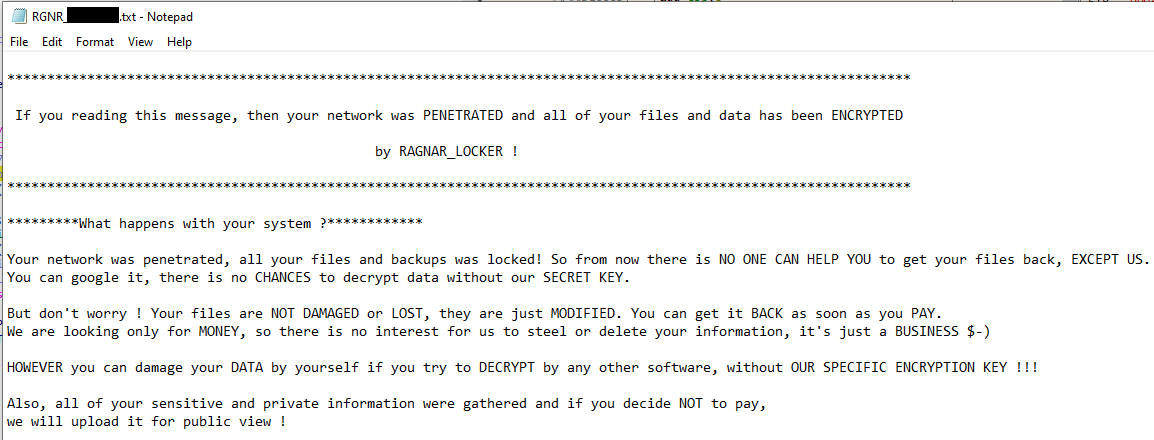 Displayed ransom note
Displayed ransom note
Detection and Prevention
Cybereason Defense Platform
The Cybereason Defense Platform is able to detect and prevent infections with Ragnar Locker ransomware, using multi-layer protection that detects and blocks malware with threat intelligence, machine learning, anti-ransomware and Next-Gen Antivirus (NGAV) capabilities:
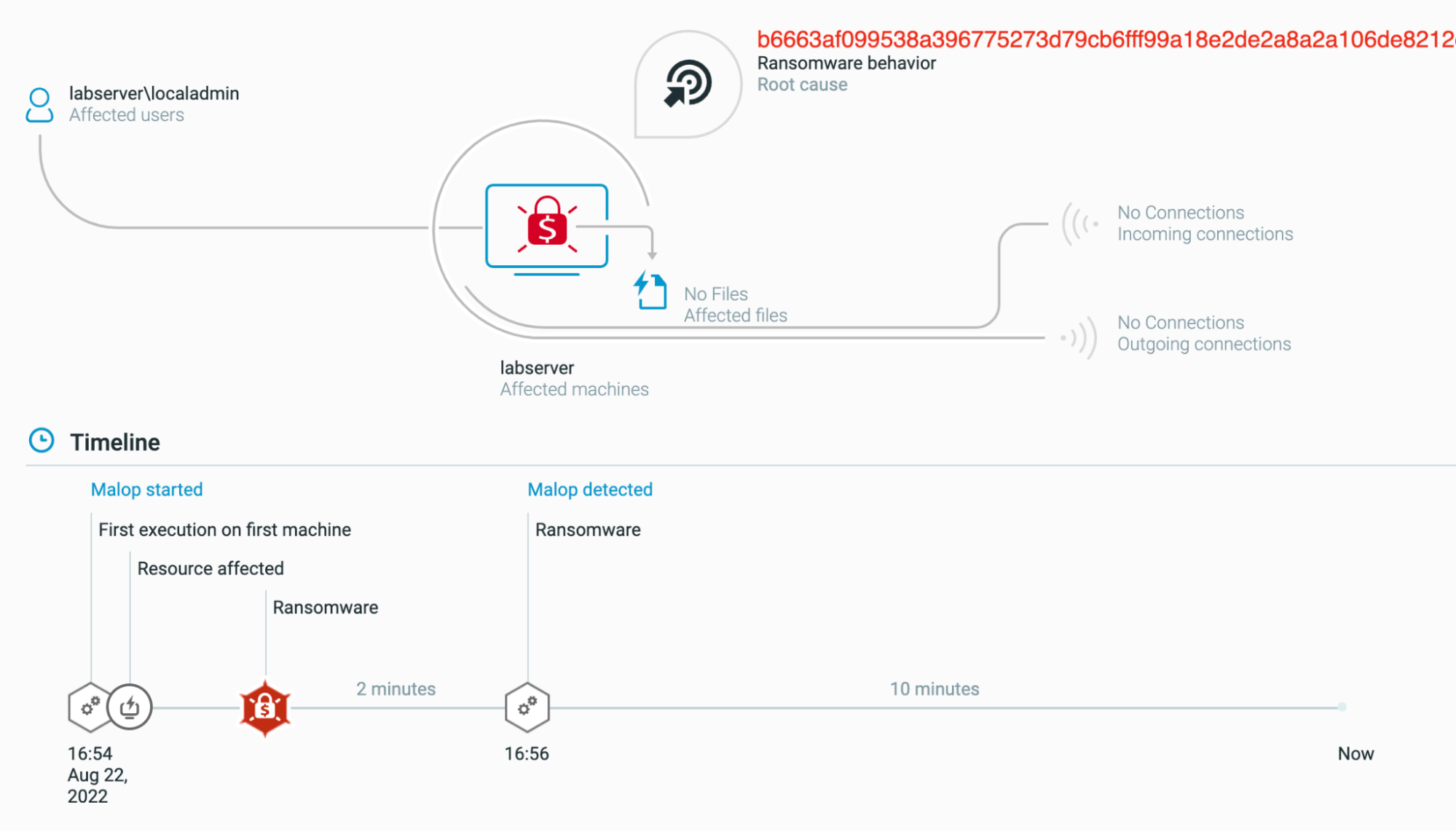
The Cybereason Defense Platform creates a MalOp and labels it as Ransomware behavior

The Cybereason Defense Platform suspends Ragnar Locker when Anti-Ransomware feature is set to “Suspend” as seen from the Cybereason Defense Platform
Cybereason GSOC MDR
The Cybereason GSOC recommends the following:
- Enable Anti-Ransomware in your environment’s policies, set the Anti-Ransomware mode to Prevent, and enable Shadow Copy detection to ensure maximum protection against ransomware.
- In the Cybereason Defense Platform, enable Application Control to block the execution of malicious files.
- To hunt proactively, use the Investigation screen in the Cybereason Defense Platform and the queries in the Hunting Queries section to search for machines that are potentially infected with Ragnar Locker. Based on the search results, take further remediation actions, such as isolating the infected machines and deleting the payload file.
Cybereason is dedicated to teaming with defenders to end cyber attacks from endpoints to the enterprise to everywhere. Schedule a demo today to learn how your organization can benefit from an operation-centric approach to security.
MITRE ATT&CK Mapping
IOCs
|
Indicators
|
Indicator type
|
Description
|
|
041fd213326dd5c10a16caf88ff076bb98c68c052284430fba5f601023d39a14
|
SHA256
|
Ragnar Locker Binary
|
|
04c9cc0d1577d5ee54a4e2d4dd12f17011d13703cdd0e6efd46718d14fd9aa87
|
SHA256
|
Ragnar Locker Binary
|
|
0766beb30c575fc68d1ca134bd53c086d2ce63b040e4d0bbd6d89d8c26ca04f6
|
SHA256
|
Ragnar Locker Binary
|
|
0aaa7a3596af6b1aae02b6e6ca878045360d467f96b0687363a9dce19ea60a36
|
SHA256
|
Ragnar Locker Binary
|
|
10f9ad4e9f6e0dc1793be80203b258f8c5114d01cb17307c1b2fdcca37d4edf9
|
SHA256
|
Ragnar Locker Binary
|
|
1318f8a4566a50537f579d24fd1aabcf7e22e89bc75ffd13b3088fc6e80e9a2a
|
SHA256
|
Ragnar Locker Binary
|
|
1472f5f559f90988f886d515f6d6c52e5d30283141ee2f13f92f7e1f7e6b8e9e
|
SHA256
|
Ragnar Locker Binary
|
|
1602d04000a8c7221ed0d97d79f3157303e209d4640d31b8566dd52c2b09d033
|
SHA256
|
Ragnar Locker Binary
|
|
30dcc7a8ae98e52ee5547379048ca1fc90925e09a2a81c055021ba225c1d064c
|
SHA256
|
Ragnar Locker Binary
|
|
3b43751ed88e4d1f82cf52ca2d4477e3e35c35f08c1b4e3ab21c80720601e804
|
SHA256
|
Ragnar Locker Binary
|
|
3bc8ce79ee7043c9ad70698e3fc2013806244dc5112c8c8d465e96757b57b1e1
|
SHA256
|
Ragnar Locker Binary
|
|
5469182495d92a5718e0e1dcdf371e92b79724e427050154f318de693d341c89
|
SHA256
|
Ragnar Locker Binary
|
|
5fc6f4cfb0d11e99c439a13b6c247ec3202a9a343df63576ce9f31cffcdbaf76
|
SHA256
|
Ragnar Locker Binary
|
|
60233700ee64b9e5d054fa551688e8617328b194534a0fe645411685ce467128
|
SHA256
|
Ragnar Locker Binary
|
|
63096f288f49b25d50f4aea52dc1fc00871b3927fa2a81fa0b0d752b261a3059
|
SHA256
|
Ragnar Locker Binary
|
|
68eb2d2d7866775d6bf106a914281491d23769a9eda88fc078328150b8432bb3
|
SHA256
|
Ragnar Locker Binary
|
|
6fd4ec6611bf7e691be80483bcf860e827d513df45e20d78f29cf4638b6c20e8
|
SHA256
|
Ragnar Locker Binary
|
|
7af61ce420051640c50b0e73e718dd8c55dddfcb58917a3bead9d3ece2f3e929
|
SHA256
|
Ragnar Locker Binary
|
|
91128776769d4f78dd177695df610463a0b05e2174ba76d0489b976b99cae223
|
SHA256
|
Ragnar Locker Binary
|
|
9416e5a57e6de00c685560fa9fee761126569d123f62060792bf2049ebba4151
|
SHA256
|
Ragnar Locker Binary
|
|
9706a97ffa43a0258571def8912dc2b8bf1ee207676052ad1b9c16ca9953fc2c
|
SHA256
|
Ragnar Locker Binary
|
|
9b62cdb57f4c34924333dfa3baefd993efeab68109580b682b074f0e73b63983
|
SHA256
|
Ragnar Locker Binary
|
|
9bdd7f965d1c67396afb0a84c78b4d12118ff377db7efdca4a1340933120f376
|
SHA256
|
Ragnar Locker Binary
|
|
a8ee0fafbd7b84417c0fb31709b2d9c25b2b8a16381b36756ca94609e2a6fcf6
|
SHA256
|
Ragnar Locker Binary
|
|
ac16f3e23516cf6b22830c399b4aba9706d37adceb5eb8ea9960f71f1425df79
|
SHA256
|
Ragnar Locker Binary
|
|
afab912c41c920c867f1b2ada34114b22dcc9c5f3666edbfc4e9936c29a17a68
|
SHA256
|
Ragnar Locker Binary
|
|
b0d8f9aa9566245362d7e7443ab4add80ce90fbdf35a30df9a89e9dae5f22190
|
SHA256
|
Ragnar Locker Binary
|
|
b6663af099538a396775273d79cb6fff99a18e2de2a8a2a106de8212cc44f3e2
|
SHA256
|
Ragnar Locker Binary
|
|
b670441066ff868d06c682e5167b9dbc85b5323f3acfbbc044cabc0e5a594186
|
SHA256
|
Ragnar Locker Binary
|
|
b72beb391c75af52c6fb62561f26214b682f12d95660b128d9e21e18e3bff246
|
SHA256
|
Ragnar Locker Binary
|
|
c2bd70495630ed8279de0713a010e5e55f3da29323b59ef71401b12942ba52f6
|
SHA256
|
Ragnar Locker Binary
|
|
ce33096639fb5c51684e9e3a7c7c7161884ecad29e8d6ad602fd8be42076b8d4
|
SHA256
|
Ragnar Locker Binary
|
|
cf5ec678a2f836f859eb983eb633d529c25771b3b7505e74aa695b7ca00f9fa8
|
SHA256
|
Ragnar Locker Binary
|
|
dd5d4cf9422b6e4514d49a3ec542cffb682be8a24079010cda689afbb44ac0f4
|
SHA256
|
Ragnar Locker Binary
|
|
ec35c76ad2c8192f09c02eca1f263b406163470ca8438d054db7adcf5bfc0597
|
SHA256
|
Ragnar Locker Binary
|
About the Researchers
 Eli Salem, Principal Security Analyst, Cybereason Global SOC
Eli Salem, Principal Security Analyst, Cybereason Global SOC
Eli is a lead threat hunter and malware reverse engineer at Cybereason. He has worked in the private sector of the cyber security industry since 2017. In his free time, he publishes articles about malware research and threat hunting.
 Loïc Castel, Principal Security Analyst, Cybereason Global SOC
Loïc Castel, Principal Security Analyst, Cybereason Global SOC
Loïc is a Principal Security Analyst with the Cybereason Global SOC team. Loïc analyses and researches critical incidents and cybercriminals, in order to better detect compromises. In his career, Loïc worked as a security auditor in well-known organizations such as ANSSI (French National Agency for the Security of Information Systems) and as Lead Digital Forensics & Incident Response at Atos. Loïc loves digital forensics and incident response, but is also interested in offensive aspects such as vulnerability research.






































 Eli Salem, Principal Security Analyst, Cybereason Global SOC
Eli Salem, Principal Security Analyst, Cybereason Global SOC Loïc Castel, Principal Security Analyst, Cybereason Global SOC
Loïc Castel, Principal Security Analyst, Cybereason Global SOC