Cybereason issues Threat Alerts to inform customers of emerging impacting threats, including critical vulnerabilities such as the Ivanti Connect Secure VPN Zero-Day exploitation. Cybereason Threat Alerts summarize these threats and provide practical recommendations for protecting against them.
WHAT'S HAPPENING?
Cybereason Security Services and Incident Response Teams are investigating incidents that involve exploitation of recently disclosed vulnerabilities in Ivanti VPN appliances, not patched at the time of disclosure (zero-days).
On 10 January 2024, Ivanti disclosed two critical vulnerabilities identified as CVE-2023-46805 and CVE-2024-21887 affecting their Connect Secure and Policy Secure solutions, urging customers to apply immediate mitigations. These vulnerabilities pose severe risks, enabling unauthorized command execution and system access on Internet-facing security devices. Following the disclosure, both Volexity and Mandiant released reporting revealing that widespread exploitation of these vulnerabilities began as early as December 2023.
On 16 January 2024, a third party released a public Proof of Concept (PoC) resulting in further escalation of exploitation. Adding to the current threat, on January 31st, Ivanti announced two more vulnerabilities, CVE-2024-21888 (a privilege escalation flaw) and CVE-2024-21893 (a SSRF web vulnerability) amplifying the need for both action and heightened security awareness as efforts by the manufacturer remain underway to develop and deliver appropriate mitigations.
Impact
CVE-2023-46805 and CVE-2024-21887 have enabled attackers to conduct a range of malicious activities, significantly impacting the security posture of affected organizations.
CVE-2023-46805, an authentication-bypass vulnerability, allows attackers to gain unauthorized access to the VPN appliances by circumventing authentication mechanisms. This vulnerability compromises the integrity of secure VPN tunnels, exposing private internal networks to potential espionage and data theft.
CVE-2024-21887, a command-injection vulnerability, permits authenticated attackers to execute arbitrary commands on the system. This level of access provides attackers with the capability to steal sensitive configuration data, manipulate existing system files, download additional malicious payloads, and establish reverse tunnels for persistent access and data exfiltration.
In incidents observed by Volexity, attackers exploited these vulnerabilities to modify legitimate Ivanti Connect Secure components. Specifically, attackers were seen backdooring the compcheckresult.cgi file, available from the web interface of the VPN device, to enable remote command execution and altering JavaScript files within the Web SSL VPN component to capture and exfiltrate user login credentials. This allowed attackers not only to maintain persistent access within the network but also to escalate privileges and move laterally, targeting sensitive internal systems and data.
The additional vulnerabilities disclosed by Ivanti on 31 January 2024, CVE-2024-21888 and CVE-2024-21893, also allow for unauthenticated remote command execution with elevated privileges, thereby increasing the attack surface for malicious actors.
The impact of these vulnerabilities is profound, enabling attackers to bypass multi-factor authentication, steal confidential information, establish covert command and control channels, and potentially disrupt critical operations.
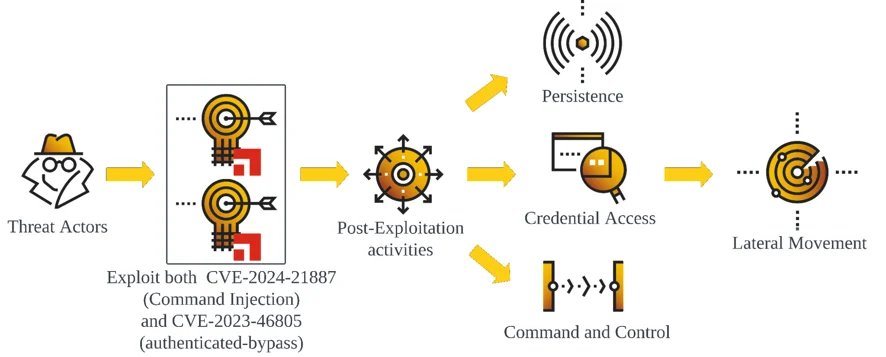
Attack Flow Diagram Related To CVE-2023-46805 & CVE-2024-21887
Attribution
Analysis by Mandiant indicates that these vulnerabilities have been first actively exploited by a suspected China-nexus espionage threat actor, known as UNC5221, as well as other uncategorized threat groups through automated methods.
This broad exploitation activity underscores the attractiveness of these vulnerabilities to a wide range of actors, including state-sponsored groups and cybercriminals, for objectives ranging from strategic intelligence gathering to financial gain.
KEY OBSERVATIONS
The investigation into the exploitation of Ivanti vulnerabilities has yielded several critical observations, shedding light on the tactics, techniques, and procedures (TTPs) employed by attackers, as well as the broader implications of these security breaches.
- Sophisticated Exploitation Techniques: Chained usage of CVE-2023-46805 and CVE-2024-21887, along with the subsequently disclosed CVE-2024-21888 and CVE-2024-21893, highlights a sophisticated approach to exploiting multiple layers of vulnerabilities. The attackers' ability to bypass authentication controls and execute commands remotely demonstrates a deep understanding of the affected systems. This is further evidenced by the attackers' strategic manipulation of Ivanti components, such as the backdooring of the compcheckresult.cgi file and the alteration of JavaScript files to capture credentials, facilitating both persistent access and lateral movement within compromised networks.
- Automation and Broad Targeting: Increase in automated attacks following the public disclosure of Proof-of-Concept (PoC) code suggests that cybercriminals are leveraging these vulnerabilities at scale. The broad targeting, irrespective of geography or sector, indicates that attackers are casting a wide net, aiming to exploit any vulnerable Ivanti appliance accessible online. This shift towards automated exploitation underlines the critical need for organizations to apply mitigations promptly and thoroughly.
- Evasion Techniques: The attackers' efforts to modify legitimate system files and insert web shells for backdoor access highlight a concerted effort to evade detection. The specific targeting of the Ivanti Integrity Checker Tool, by making modifications that falsely report no findings of compromise, demonstrates an advanced level of cunning designed to sustain access over time without detection.
- Credential Theft and Session Hijacking: The exploitation activities have had significant implications for credential security and session integrity. By capturing and exfiltrating user credentials, attackers have been able to bypass multi-factor authentication mechanisms, hijack legitimate user sessions, and gain unauthorized access to sensitive systems and data. This capability poses a grave threat to organizational security, potentially leading to extensive data breaches and unauthorized access to critical resources.
- Response and Mitigation Challenges: The evolving nature of the threat actors' techniques and the subsequent disclosure of additional vulnerabilities complicate response and mitigation efforts. Organizations are challenged not only to patch and mitigate known vulnerabilities but also to anticipate and defend against evolving attack methodologies and assume breach of the network if one of their Ivanti devices was identified as compromised. The necessity of a factory reset for compromised devices, along with the replacement of certificates and the resetting of passwords and API keys, underscores the complexity and operational impact of adequately responding to these incidents.
Threat / Vulnerabilities Analysis
The four vulnerabilities of the Ivanti Connect Secure VPN Zero-Day Exploitation can be combined together to perform remote control execution, privilege escalation as well as exfiltration of sensitive data, ultimately leading to threat actors accessing the victim’s internal network.
Vulnerability CVE-2023-46805 - Authentication Bypass
This vulnerability allows an unauthenticated attacker to access restricted resources by bypassing control checks. The exploit utilizes path traversal attack by sending a GET request to Ivanti Connect Secure public facing endpoint with URL path /api/v1/totp/user-backup-code.
The path traversal attack allows an attacker to access the contents of the system folder:
- /api/v1/totp/user-backup-code/../../system/system-information
- /api/v1/totp/user-backup-code/../../system/maintenance
- /api/v1/totp/user-backup-code/../../system/maintenance/archiving
- /api/v1/totp/user-backup-code/../../system/maintenance/archiving/cloud-server-test-connection
Ivanti has released a patch for the vulnerability by defining an accepted list of permitted values (whitelisting).
Vulnerability CVE-2024-21887 - Remote Code Execution
This vulnerability allows an authenticated attacker to send specially crafted requests and execute arbitrary commands on the appliance. The attacker accesses the endpoint /api/v1/license/ via path traversal vulnerability (CVE-2023-46805) and sends a GET request with the attacker's payload appended to the endpoint for post-exploitation.
- /api/v1/totp/user-backup-code/../../license/keys-status/<shell>
Vulnerability CVE-2024-21888 - Privilege Escalation
The vulnerability in the web component of the Ivanti Connect Secure and Ivanti Policy Secure Gateway enables an authenticated user to gain admin privileges.
Vulnerability CVE-2024-21893 - Authentication Bypass Through SSRF Vulnerability
The vulnerability in Ivanti SAML component implementation allows an unauthenticated attacker to access certain restricted resources by utilizing server-side request forgery. The vulnerability affects the Ivanti Connect Secure, Ivanti Policy Secure, and Ivanti Neurons devices.
SAML is a standard used by single sign-on (SSO) providers to authenticate users. Ivanti Connect Secure uses SAML to implement web browser SSO. Ivanti Connect Secure Entity can configure SAML service provider, SAML Identity provider or both. Based on the patch file analysis, the following SAML CGI links have been patched for the SSRF attack vulnerability.
- Ivanti Single Sign-on page URL: https://SAMLHostName/dana-na/auth/saml-sso.cgi
- Ivanti Single Sign-out page URL: https://SAMLHostName/dana-na/auth/saml-logout.cgi
- Assertion Consumer Service URL: https://SAMLHostName/dana-na/auth/saml-consumer.cgi
- Connect Secure Entity URL: https://SAMLHostName/dana-na/auth/saml-endpoint.cgi
Known Post-exploitation
Cybereason lists some of the known post-exploitation activities reported by various security vendors. As of the writing of this report, the reported exploitation observed in the wild are the combinations of CVE-2023-46805 and CVE-2024-21887.
Coinminer
Threat actors exploited CVE-2023-46805 and CVE-2024-21887 to deliver coinminers to the Ivanti Connect Secure appliances. The known execution flow to deliver coin miners are as follows.
-
-
Exploit CVE-2023-46805 and CVE-2024-21887 to execute cURL/wget command to download and execute a shell script
-
Creates persistence via service or cron
-
Execute Coinminer
-
Coinminer Execution Flow
Credential Harvesting
Once threat actors deploy necessary tools and malwares, threat actors potentially move to the next step which is to harvest credentials. The credential harvesting can lead to lateral movement and allow threat actors to further compromise the enterprise network.
One of known credential harvesters that are deployed to the compromised Ivanti Connect Secure appliances is WARPWIRE, dubbed by Mandiant. WARPWIRE is a Javascript-based credential harvester, which targets plaintext username and passwords. The WARPWIRE captures credentials for web logon to access layer 7 applications such as RDP.
Through successful credential harvesting, threat actors can move laterally into the target network to conduct further exfiltration of credentials, such as LSASS credential dumping.
Post-Exploitation Of CVE-2023-46805 And CVE-2024-21887 Leading To Credential Dumping
Webshells
To maintain persistence within the environment, threat actors deploy webshells. Currently in the wild, there are two known types of webshells.
- LIGHTWIRE: Webshell written in Perl CGI embedded into a legitimate Secure Connect file. LIGHTWIRE intercepts requests to compcheckresult.cgi and execute obfuscated Perl code.
- WIREFIRE: Webshell written in Python, which abuses HTTP POST /api/v1/cav/client/visits before authentication. The webshell modifies the existing CAV Python package.
- BUSHWALK: Webshell written in Perl embedded into a legitimate Secure Connect file querymanifest.cgi and executes obfuscated Perl code. This webshell is able to bypass initial mitigation provided by Ivanti on 10 Jan 2024.
- CHAINLINE: Webshell written in Python embedded in a Ivanti Connect Secure Python package and it is the same Python package modified to support WIREFIRE. However unlike WIREFIRE, CHAINLINE creates its own Python file masquerading as a legitimate CAV Python package.
- FRAMETESTING: Webshell written in Python embedded in a Ivanti Connect Secure Python package. This variant is similar to WIREFIRE and CHAINLINE
CYBEREASON RECOMMENDATIONS
Cybereason recommends the following actions:
- Patch the Ivanti vulnerabilities as soon as they become available. Ivanti has released their first round of patches for specific versions of Ivanti Connect Secure (ICS) starting on Jan. 31, 2024. The remaining patches will be released on a staggered schedule for three different products. Patches are currently available for the following versions:
- Ivanti Connect Secure:
- 9.1R14.4
- 9.1R17.2
- 9.1R18.3
- 22.4R2.2
- 22.5R1.1
- ZTA: 22.6R1.3
- Ivanti Connect Secure:
- Before the patches were available, Ivanti suggested the following precautionary measures :
- Affected customers should install the mitigation immediately if a patch is not yet available for their version. Installing the mitigation is intended to prevent future exploitation of the two vulnerabilities. It is not intended to remediate or otherwise contain an existing compromised device.
- On January 20, 2024, Ivanti disclosed information about a condition that could adversely affect the mitigation, leaving appliances susceptible to vulnerabilities. This condition particularly affects customers who deploy configurations to appliances using Ivanti Neurons for Secure Access (nSA) or Pulse One. Ivanti recommends that customers refrain from pushing configurations to appliances with the XML in place until patches are applied.
- Ivanti urges its customers to initiate an assessment of their logs by utilizing the internal Integrity Checker Tool (ICT) for a comprehensive review of historical hits. In cases where the internal ICT returns no results, customers are advised to proceed with the external ICT, which is more resilient to tampering. Both Mandiant and Volexity have reported instances of threat actors trying to manipulate the internal (built-in) ICT to evade detection. Customers are encouraged to share the ICT results with Ivanti by opening a support ticket for in-depth analysis, enabling Ivanti to assess whether the appliance has been compromised and provide recommendations for subsequent actions.
- Reset the password of any local user configured on the appliance.
- Hunt proactively within the Cybereason Defense Platform, as well as their firewall logs for traffic to the WARPWIRE credential harvester C2 addresses listed in the IOCs section.
- As threat actors appear to be conducting various credential harvesting within the enterprise network, Cybereason recommends monitoring for potential credential dumping in the environment.
- Harden your Ivanti device using the following guidance document from Google/Mandiant: Remediation and Hardening Recommendations
- Add the aforementioned IoCs to the custom reputation with “Block & Prevent” and to filtering equipments such as Firewalls
INDICATORS OF COMPROMISE ASSOCIATED WITH POST-EXPLOITATION
Below is a list of Indicator of Compromises (IoC) associated with known post-exploitation activities of Ivanti Connect Secure vulnerabilities are as follows.
|
Type |
Value |
Comment |
|
MD5 |
8eb042da6ba683ef1bae460af103cc44 |
WARPWIRE credential harvester variant |
|
MD5 |
a739bd4c2b9f3679f43579711448786f |
WARPWIRE credential harvester variant |
|
MD5 |
a81813f70151a022ea1065b7f4d6b5ab |
WARPWIRE credential harvester variant |
|
MD5 |
b15f47e234b5d26fb2cc81fc6fd89775 |
WARPWIRE credential harvester |
|
MD5 |
d0c7a334a4d9dcd3c6335ae13bee59ea |
WARPWIRE credential harvester |
|
MD5 |
e8489983d73ed30a4240a14b1f161254 |
WARPWIRE credential harvester variant |
|
MD5 |
3045f5b3d355a9ab26ab6f44cc831a83 |
CHAINLINE web shell |
|
MD5 |
3d97f55a03ceb4f71671aa2ecf5b24e9 |
LIGHTWIRE web shell |
|
MD5 |
2ec505088b942c234f39a37188e80d7a |
WARPWIRE credential harvester variant |
|
MD5 |
465600cece80861497e8c1c86a07a23e |
FRAMESTING web shell |
|
IP |
8[.]137[.]112[.]245 |
Malware Hosting |
|
IP |
50[.]215[.]39[.]49 |
Malware Hosting |
|
IP |
146[.]0[.]228[.]66 |
Malware Hosting |
|
IP |
186[.]179[.]39[.]235 |
Malware Hosting |
|
IP |
91[.]92[.]254[.]14 |
Malware Hosting |
|
IP |
159[.]65[.]130[.]146 |
Malware Hosting |
|
IP |
173[.]220[.]106[.]166 |
Malware Hosting |
|
IP |
45[.]61[.]136[.]14 |
Malware Hosting |
|
URL |
symantke[.]com |
WarpWire C2 |
|
URL |
Secure-cama[.]com |
WarpWire C2 |
|
URL |
request[.]data |
WarpWire C2 |
|
URL |
miltonhouse[.]nl |
WarpWire C2 |
|
URL |
logclear[.]pl |
WarpWire C2 |
|
URL |
line-api[.]com |
WarpWire C2 |
|
URL |
entraide-internationale[.]fr |
WarpWire C2 |
|
URL |
ehangmun[.]com |
WarpWire C2 |
|
URL |
duorhytm[.]fun |
WarpWire C2 |
|
URL |
clicko[.]click |
WarpWire C2 |
|
URL |
clickcom[.]click |
WarpWire C2 |
|
URL |
areekaweb[.]com |
WarpWire C2 |
REFERENCES
- https://www.volexity.com/blog/2024/01/10/active-exploitation-of-two-zero-day-vulnerabilities-in-ivanti-connect-secure-vpn/
- https://www.volexity.com/blog/2024/02/01/how-memory-forensics-revealed-exploitation-of-ivanti-connect-secure-vpn-zero-day-vulnerabilities/
- https://www.mandiant.com/resources/blog/suspected-apt-targets-ivanti-zero-day
- https://www.mandiant.com/resources/blog/investigating-ivanti-zero-day-exploitation
- https://www.cisa.gov/news-events/directives/supplemental-direction-v1-ed-24-01-mitigate-ivanti-connect-secure-and-ivanti-policy-secure
ABOUT THE RESEARCHERS
Nick Mangano is a Senior GSOC Analyst with the Cybereason Global SOC team. He is involved with active MalOp investigation and remediation. Previously, Nick worked as a Security Analyst with Seton Hall University while completing his undergraduate degree. Nick holds an Accounting and Information Technology Degree as well as a Cybersecurity Certification from Seton Hall University. He is interested in malware analysis as well as digital forensics.
Hema Loganathan is a GSOC Analyst with the Cybereason Global SOC team. She is involved in MalOp Investigation, Malware Analysis, Reverse Engineering and Threat Hunting. Hema has a Master of Science degree in Information Systems.
Kotaro is a CTI Analyst with the Cybereason Security Operations team. He is involved in threat hunting, threat intelligence enhancements and Extended Detection and Response (XDR). Kotaro has a bachelor of science degree in information and computer science.
