Managed Detection and Response (MDR) isn’t a new concept. Organizations of all shapes and sizes work with security vendors to help manage their network security and address common use cases such as; talent shortages, operations teams that are stretched thin, alert fatigue, and 24x7 threat hunting and remediation.
What is new is when a security vendor can take an existing solution and super-charge it to deliver more dynamic results. When evaluating MDR solutions, it is important to understand that the end result is just as critical as how it is delivered. Organizations should be looking for two key outcomes: speed and efficacy. In other words: how fast can a threat or malicious operation (MalOp™) be detected and how fast can it be remediated.
Cybereason realizes this and does MDR differently. Included in every MDR package is a proprietary technology called the MalOp Severity Score (MOSS), which aids analysts and security teams with the ability to conduct lightning-quick triage and results in reduced time to remediation.
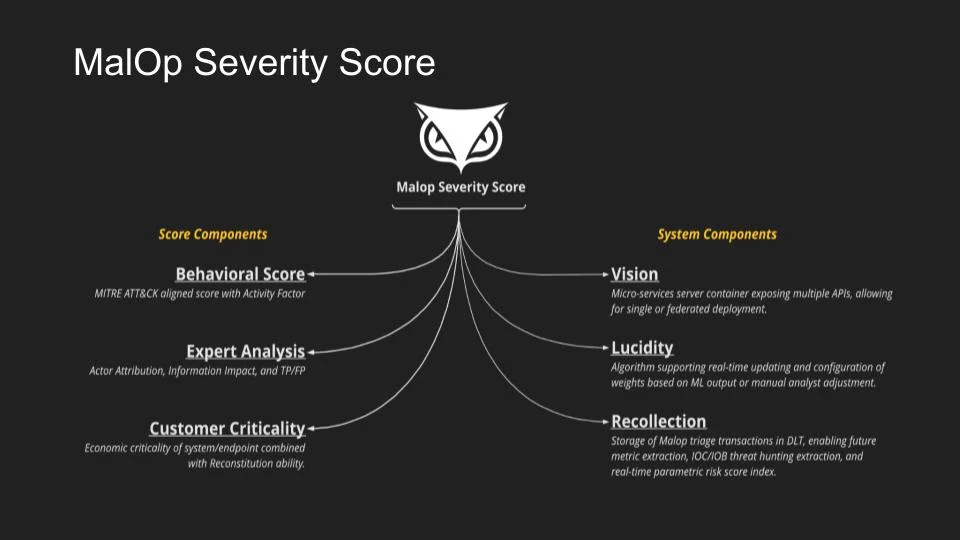
The MalOp Severity Score is an aggregate of three key components from every MalOp, and from there generates a criticality score that determines what actions are taken next. The MalOp Severity Score is comprised of:
MalOp Behavior: The behavioral severity score for a MalOp is mapped to the MITRE ATT&CK Framework and looks at infiltration points, lateral movement, attack techniques, and potential targets within the environment. This allows analysts to understand and assess the seriousness of an event.
Expert Analysis: Based on the information gathered through behavioral analysis, Cybereason security analysts conduct root-cause analysis and triage verification. In this stage, analysts are able to use identifiable markers of an attack for adversary attribution.
Customer Criticality: During the onboarding process, the Cybereason Managed Services Delivery Team will work with the customer to identify critical assets and endpoints - an example of this is an executive’s laptop will likely be deemed more critical than an intern’s laptop. Based on this information, analysts will be able to look at which assets have been compromised, identify potential accounts and endpoints that attackers could pivot to, and understand what potential intellectual property and information are at risk. The result is understanding the impact on the customer’s organization.
The key customer benefit of the MalOp Severity Score is that every MalOp undergoes the same in-depth analysis and triage process that will quickly assess the criticality of every MalOp:
Once a MalOp Severity Score has been assigned to the operation, remediation begins. If a MalOp is deemed critical, the Cybereason Extended Response (XR) actions automatically kick in.
Cybereason Extended Response actions are directly dictated by the MalOp Severity Score. These two features work hand-in-hand and ensure that immediate action is taken for any critical MalOp, stopping an attack in its tracks and preventing any further spread or lateral movement.
While remediation actions have automatically begun, the Cybereason Managed Services Team will reach out to the customer to notify them of the attack. Data and threat intelligence gathered throughout the triage process will provide actionable feedback in which security teams will be able to leverage during the remediation cycle.
Together the MalOp Severity Score and Extended Response capabilities will deliver the ability to:
- Detect a MalOp in < 1 minute
- Triage the MalOp in < 5 minutes
- Remediate the MalOp in < 30 minutes
With today’s sophisticated adversaries and advanced persistent threats, every second is critical. The ability to efficiently detect and respond to a MalOp has never been more important to the security of an organization.
Cybereason is dedicated to teaming with defenders to end attacks on the endpoint, across enterprise, to everywhere the battle is taking place. Learn more about Cybereason MDR here or schedule a demo today to learn how your organization can benefit from an operation-centric approach to security.
