In June 2014, the FBI decided to fight back against Evgeniy Bogachev and his Zeus botnet, the source of a cyber attack that caused banks to lose hundreds of millions of dollars. Unfortunately, it seems that once again, the criminals have the upper hand.
Even though the GameOver Zeus (GOZ) botnet’s core functionality is simple, it is quite difficult to detect, mostly because GOZ uses domain generation algorithms (DGA) to communicate with its Command & Control (C&C) server. While escaping common detection methodologies, GOZ systematically infiltrates and causes a massive amount of damage to financial institutions.
The FBI’s Plan of Action
GOZ’s main attack method was discovered in 2010 when the FBI announced that hackers had been sending emails containing a malicious code to targeted businesses and private users, compromising user accounts. The hackers were using account passwords and other security measures to transfer thousands of dollars at a time from bank account to bank account. Money mules were hired mostly from overseas, using false U.S. credentials and fake documents. Ultimately, there was over $70 million in damage done by GOZ in the US before the FBI was able to implement a strategy to crack down on this threat, with an estimated further attempted theft of $220 million. The malware primarily targeted private accounts, rather than corporations, in order to spread faster and more easily, which helped it remain undetected for longer.
The architecture of GOZ as presented by the FBI.
DGA-Based Malware
The DGA technique is employed by many sophisticated types of malware. It involves generating a large number of domain names that can be used as “rendezvous points” for malware and its respective operators. The malware randomly chooses a single domain and tries to communicate with it. If it fails, it tries another one, one after another, until it succeeds. The multiple potential rendezvous points make the malware very difficult to detect and block effectively. Malware operators know the list of domains that will be generated in advance, and can register any of them to establish communication with infected computers. If a particular C&C server is taken down or a domain is discovered and blocked, the operators register another domain from the list and communication resumes. This process is then repeated over and over every few hours or days.
The FBI Fights Back: Operation Tovar
In order to take down the DGA-based botnet, the FBI initiated Operation Tovar to register all the possible generated domains (over 150,000), six months in advance. This was done to block the malware’s operators from registering the domains themselves, therefore disabling the operators’ communication with their bots. In addition, this potentially allowed the FBI to detect and inform individuals and corporations targeted by the attack that were already affected.
The Supreme Court acceded to the FBI’s request and gave it the authority to register all of the generated domain names between May and November 2014. Then, around mid-November 2014, the FBI submitted a second request with an updated list of domain names for another six months.
Unfortunately, the FBI’s approach was doomed to fail from the start. While it was a significant step to prevent GOZ from continuing to cause harm, it was not bulletproof.
Why Did the FBI’s Approach Fail?
Limited Time Frame for Domain Registration
The Supreme Court’s first warrant included domains that were generated by GOZ until November 30, 2014. A few days before the warrant’s expiration date, the Supreme Court accepted the FBI’s second request (valid from November 30, 2014 until May 30, 2015). However, the FBI will have to continue submitting requests ad infinitum in order to continue battling the botnet.
A Blossom of Zeus Variants
The FBI’s act might have only accelerated the creation of new Zeus variants. In July, just one month after the warrants were submitted, Brian Krebs reported a new malware on his blog that has 90 percent of its code related to GameOver Zeus.
In addition, in December 2014, new Zeus variants were revealed. As reported on their blog, Kaspersky Lab researchers revealed a new strain of the trojan, called ‘Chthonic,’ which evolved from ZeusVM, another variant. According to the Kaspersky researchers, as a descendant of Zeus, Chthonic has targeted a large number of online-banking systems in efforts to get a hold of and use potential victims’ online banking credentials to stealthily perform financial transactions. So far, over 150 different banks and 20 payment systems spanning 15 countries have been hit.
Another interesting Zeus variant was revealed in December as well. The FBI reported that the new variant was designed to target financial mobile apps.
“One example of this type of vulnerability is the Zeus‐in‐the‐Middle malware, a mobile version of the GameOver Zeus malware, which itself was one of the most sophisticated types of malware the FBI ever attempted to disrupt,” said Joseph Demarest, Assistant Director of the FBI’s Cyber Division.
In addition, several CryptoLocker variants that we identified in our lab generated domain names using the same DGA technique, but with a different top level domain (TLD). For example, if the original CryptoLocker algorithm created the domain ‘example.com,’ this variant would create ‘example.net,’ which would lead to a similar, yet completely different domain. This variant requires a minimal change in code, and we are actually unsure of whether it was created to bypass the FBI’s actions or was intended as a polymorphic offshoot of the original CryptoLocker ransomware. Unless the FBI registers the domain names in all possible combinations, it will not be able to track the newly generated domains.
The Russians Stay Out of the Game
In order to effectively register all possible domain names that are used by DGA, it is important to cover all of the main domain registrars. Each TLD registrar (.net, .biz, .ru, .org, .info or .com) belongs to a different company that supervises its operations. Therefore, the Supreme Court had to issue a different warrant for each company, ordering them to allow the FBI to register any of the supplied generated domains in advance, on their own servers, and redirect or sinkhole these domains to an FBI-operated server.
Of the six TLDs, five belonged to American companies, all of whom automatically cooperated with the FBI. In addition, CryptoLocker used the .co.uk registrar, which is a UK-based company that joined forces with the American investigation team. However, the last registrar (.ru), was based in Russia and was unwilling to play along with the FBI’s investigation. As a result, one out of every six domains was not registered by the FBI and could still be used by the attackers.
This means that the attackers could easily regain control of the infected computers. Since the FBI did not register the .ru domains, the attackers could still register them and communicate with victim machines that may randomly choose these domains. Our research has shown that even when connected to an FBI sinkhole, GOZ continues to try to connect to additional daily-generated domains, probably because the sinkholed server does not - or cannot - masquerade as a real Zeus server. This happens at a rate of around one domain every 10 minutes.
Eventually, one of these domains will be under the .ru TLD, in which case, all the attackers have to do is register a few .ru domains and patiently wait for the malware to finally connect to one of them. Unless the infection is immediately removed, the attackers can theoretically regain control of the malware in less than a day. The attackers can then simply update the malware with a modified version that generates only .ru domains, instantaneously regaining full control.
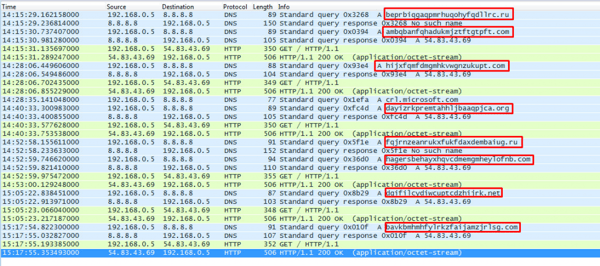
Monitoring results of GOZ communication that from our lab computer (192.168.0.5).
Each DNS request to a .ru domain was followed by a ‘no such name’ DNS response. A DNS request to non .ru domains was resolved to the IP: 54.83.43.69, the FBI’s sinkhole server, and followed by an HTTP request. Twelve to 13 minutes after each HTTP request to the FBI’s sinkhole, GOZ created a new request to another domain it generated.
Final Thoughts
While the FBI is known for its thorough investigations, in the search for GOZ botnet it was clear that their plan of action had some limitations. Law enforcement agencies around the world are becoming more active in fighting cyber crime, as was demonstrated in the recent arrest of the Ukraine Zeus “Malware Gang” by Europol. However, these efforts often come too late, when variants of the malware have already spread across the darknet. While law enforcement agency should become more active fighting these activities, companies and individuals should also deploy effective measurements of defense on their own.