The Cybereason Global Security Operations Center (SOC) issues Cybereason Threat Alerts to inform customers of emerging impacting threats. The Alerts summarize these threats and provide practical recommendations for protecting against them.
What’s Happening?
The Cybereason GSOC Managed Detection and Response (MDR) Team is investigating incidents that involve exploitation of the critical Microsoft Exchange vulnerabilities - CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207, also known as ProxyShell.
The exploitation of the ProxyShell vulnerabilities enables attackers to execute arbitrary commands on compromised systems, which may lead to full system compromise and/or the deployment of malware.
The attack scenario that the Cybereason MDR team investigated involves malicious actors exploiting the ProxyShell vulnerabilities and subsequently deploying the LockFile ransomware on the compromised hosts.
Key Observations
-
- The critical Microsoft Exchange vulnerabilities - CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207, also known as ProxyShell, enable attackers to execute arbitrary commands on compromised systems. This may lead to full system compromise and/or deployment of malware. Microsoft provided a patch for the ProxyShell vulnerabilities as part of the May security update.
- The Cybereason MDR team has observed malicious actors deploying ransomware after exploiting the ProxyShell vulnerabilities, in particular, the LockFile ransomware.
- The LockFile ransomware is a relatively new ransomware on the threat landscape, first observed compromising systems in July 2021. The actors behind the ransomware are known to be active in multiple geographical regions, such as the Americas and the Asia-Pacific (APAC) region.
Analysis
Malicious actors that have exploited the ProxyShell vulnerabilities typically deploy web shells at compromised Microsoft Exchange servers in order to conduct further post-exploitation activities, such as downloading and executing additional payload. Adversaries often deploy web shells in the form of .aspx files and place them in directories associated with the Microsoft Internet Information Services (IIS) component, such as inetpub\wwwroot\aspnet_client. The commands that malicious actors execute via the web shells are executed from the context of the w3wp.exe process, a worker process for IIS.
The Cybereason MDR team has observed malicious actors executing the wget utility, a free utility for non-interactive download of files from the Internet, in order to download from an attackers’ controlled endpoint an executable file that exploits the vulnerability CVE-2021-36942.
This vulnerability is also known as PetitPotam. The vulnerability enables attackers to compromise machines that run the Active Directory Certificate Service, typically Active Directory Domain Controllers. Due to their strategic relevance in an Active Directory domain, malicious actors use compromised Domain Controllers for lateral movement, that is, to compromise all machines that are part of the Active Directory domain:
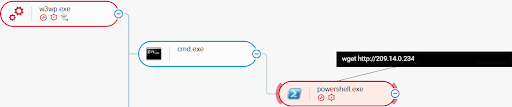
The executable file that the malicious actors download and exploits the PetitPotam vulnerability is efspotato.exe. The actors then execute efspotato.exe in order to compromise a Domain Controller and ultimately deploy the LockFile ransomware to the machines that are part of the Active Directory domain:
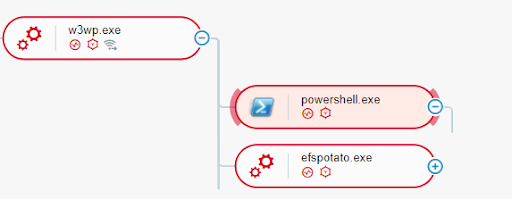
The LockFile ransomware is a relatively new ransomware on the threat landscape, first observed compromising systems in July 2021. The actors behind the ransomware are known to be active in multiple geographical regions, such as the Americas and the Asia-Pacific (APAC) region. When the malicious actors execute the LockFile ransomware, the ransomware creates multiple cmd.exe processes.
One such process executes the ping command, pinging the local loopback address - 127.0.0.1, whereas the rest spawn wmic.exe processes. The wmic.exe processes terminate processes whose names contain specific substrings, such as sqlservr, oracle, and virtualbox, likely in order for the operating system to release files used by these processes for encryption by the ransomware:
The LockFile ransomware then enumerates and encrypts files. LockFile changes the filename extension of the encrypted files to .lockfile:
After encrypting files, the LockFile ransomware displays the ransom note to the users with the mshta utility. The ransom note is stored in the %PUBLIC% folder in the form of an .hta file. The mshta utility executes .hta files:
Cybereason Recommendations
Cybereason recommends the following:
-
- Patch the ProxyShell vulnerabilities. Microsoft provided a patch for the ProxyShell vulnerabilities as part of the May security update.
- Examine for anomalous .aspx files directories associated with the Microsoft Internet Information Services (IIS) component, in which adversaries often deploy web shells after exploiting ProxyShell. These include: inetpub\wwwroot\aspnet_client, \Program Files\Microsoft\Exchange Server\V*\FrontEnd\HttpProxy\owa\auth\inetpub\wwwroot\aspnet_client\, \Program Files\Microsoft\Exchange Server\V*\FrontEnd\HttpProxy\owa\auth\, and subdirectories of \Users\All Users\.
- Enable the Anti-Ransomware feature of the Cybereason platform by setting it to Suspend or Prevent. The Cybereason platform detects the LockFile ransomware.
- Threat Hunting with Cybereason: The Cybereason MDR team provides its customers with custom hunting queries for detecting specific threats - to find out more about threat hunting and Managed Detection and Response with the Cybereason Defense Platform, contact a Cybereason Defender here.
- For Cybereason customers: More details available on the NEST including custom threat hunting queries for detecting this threat.
About the Researchers:
Aleksandar Milenkoski, Senior Threat and Malware Analyst, Cybereason Global SOC
Eli Salem, Senior Security Analyst, Cybereason Global SOC
