Research by: Lior Rochberger and Assaf Dahan
Introduction
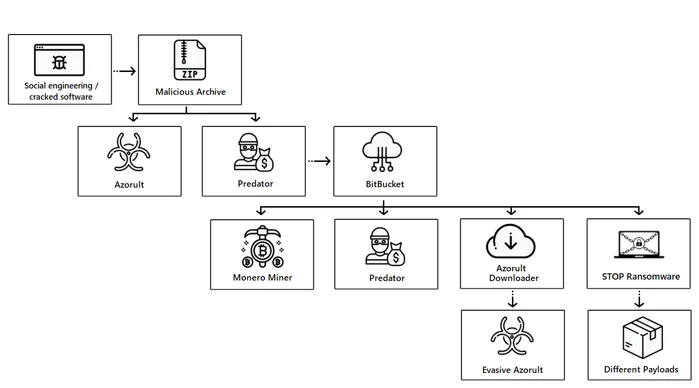
Cybereason is following an active campaign to deliver an arsenal of malware that is able to steal data, mine for cryptocurrency, and deliver ransomware to victims all over the world. Due to the variety of malware types deployed in this attack, attackers are able to hit victims from all sides and do not have to limit themselves to one attack goal or another. The payloads observed in this campaign originated from different accounts in code repository platform Bitbucket, which was abused as part of the attackers delivery infrastructure.
The following malware are deployed and updated using Bitbucket by the threat actor:
- Predator: Predator is an information stealer that steals credentials from browsers, uses the camera to take pictures, takes screenshots, and steals cryptocurrency wallets.
- Azorult: Azorult is an information stealer that steals passwords, email credentials, cookies, browser history, IDs, cryptocurrencies, and has backdoor capabilities.
- Evasive Monero Miner: The Evasive Monero Miner is the dropper for a multi-stage XMRig Miner that uses advanced evasion techniques to mine Monero and stay under the radar.
- STOP Ransomware: The STOP Ransomware is used to ransom the file system and is based on an open source ransomware platform. It also has downloader capabilities that it uses to infect the system with additional malware.
- Vidar: Vidar is an information stealer that steals web browser cookies and history, digital wallets, two-factor authentication data, and takes screenshots.
- Amadey bot: Amadey bot is a simple trojan bot primarily used for collecting reconnaissance information on a target machine.
- IntelRapid: IntelRapid is a cryptocurrency stealer that steals different types of cryptocurrency wallets.
Cybereason reached out to Bitbucket Support and the malicious repositories mentioned in the report were deactivated within a few hours.
The flow of the Bitbucket multi-payload attack.
This research highlights an ongoing trend with cybercriminals where they abuse legitimate online storage platforms like Github, Dropbox, Google Drive, and Bitbucket to distribute commodity malware.
In this campaign, the attackers abuse the Bitbucket platform by creating several user accounts that are updated frequently. Regular updates to the malware stored on these accounts and the use of Themida as a packer are used to evade detection by antivirus products and thwart analysis attempts. They also use the CypherIT Autoit packer to pack Azorult and give additional layers of protection against analysis.
This research is particularly interesting because of how the attackers infect a single target machine with multiple different kinds of malware. These kinds of commodity malware are often used for a one-off infection to steal data on the machine and sell it in underground hacking communities. However, in this attack, the attackers chose to integrate malware like coin miners and ransomware, which gives them a more persistent source of revenue. Each piece of malware in this campaign makes the attack stronger, with additional capabilities and features for a greater impact.
Key Points
- Abuses resource sharing platforms: The Cybereason Nocturnus team is investigating an ongoing campaign that abuses the Bitbucket infrastructure to store and distribute a large collection of different malware. The attackers aren’t satisfied with one payload, they want to use multiple to maximize their revenue.
- Attacks from all sides: This campaign deploys an arsenal of malware for a multi-pronged assault on businesses. It is able to steal sensitive browser data, cookies, email client data, system information, and two-factor authentication software data, along with cryptocurrency from digital wallets. It is also able to take pictures using the camera, take screenshots, mine Monero, and in certain cases also deploy ransomware.
- Far Reaching: This ongoing campaign has infected over 500,000 machines worldwide thus far.
- Modular and Constantly Updating: The attackers leverage Bitbucket to easily update payloads and distribute many different types of malware at once. In order to evade detection, they have an array of user profiles and continuously update their repositories, at times as often as every hour.
- Many kinds of malware: The attackers use the Evasive Monero Miner to steal a combination of data, mine cryptocurrency, and deploy other malware including the Vidar stealer, Amadey Bot, and IntelRapid. They also use Predator the Thief, Azorult, and the STOP ransomware over the course of their activities.
- Devastating impact: The combination of so many different types of malware exfiltrating so many different types of data can leave organizations unworkable. This threat is able to compromise system security, violate user privacy, harm machine performance, and cause great damage to individuals and corporations by stealing and spreading sensitive information, all before infecting them with ransomware.
For a synopsis of this research, check out the Bitbucket Threat Alert.
Table of Contents
- Introduction
- Key Points
- Anatomy of a Multi-Stage Attack
- Initial Compromise via Predator Infostealer
- Evasive Azorult
- STOP Ransomware and Vidar Stealer
- XMRig Miner: Old Miner New Dropper
- Deep-Dive Into the Dropper
- Conclusions
- IOCs
- MITRE ATT&CK BREAKDOWN
Anatomy of the Multi-payload Attack
Initial compromise via Predator Infostealer
This attack starts with an unsuspecting user downloading a cracked version of commercial software like Adobe Photoshop, Microsoft Office, and others. Threat actors often target users looking for “free” commercial products by bundling legitimate software with different kinds of malware. In this instance, we are seeing vast amounts of cracked software bundled with the Azorult Infostealer and Predator the Thief.
Predator the Thief is an information stealer that steals sensitive data like passwords from browsers, takes pictures, takes screenshots, and steals cryptocurrency wallets. Predator had previously been delivered via exploit kits like the RIG Exploit Kit and through phishing attacks.
When a user attempts to install the “free commercial software”, it actually drops Azorult and Predator onto the target machine. Azorult (download.exe) immediately starts stealing information and deleting its binary to cover its tracks. After Azorult executes, Predator (dowloadx.exe) creates a connection to Bitbucket to begin downloading additional payloads.
Cybereason UI: the attack tree of the execution of the malicious zip file.
We identified the download URLs for additional payloads of Azorult and the Evasive Monero Miner from a Bitbucket repository at hxxps://bitbucket[.]org/patrickhornvist/repo/ by unpacking Predator.
Deobfuscated strings in memory from downloadx.exe show download URLs of other malware.
There are multiple additional payloads on Bitbucket:
- 1.exe and 3.exe, both of which are Azorult information stealers with different hashes.
- 2.exe and 8800.exe, both of which are Predator the Thief with different hashes.
- 4.exe and 5.exe, both of which are the Evasive Monero Miner with different hashes.
- 111.exe, the STOP ransomware.
Screenshot of the Bitbucket repo: https://bitbucket[.]org/patrickhornvist/repo/downloads
Through research of other samples related to the campaign, we have identified additional Bitbucket repositories that are likely created by the same threat actor with the same set of malware samples. Judging by the number of downloads, we estimate over 500,000 machines have been infected by the campaign so far, with hundreds of machines affected every hour.
https://bitbucket[.]org/luisdomingue1/new/downloads/
https://bitbucket[.]org/BasilCowan/new/downloads/
It’s worth noting that the payloads on Bitbucket are updated almost constantly by the threat actor, sometimes as often as every few hours. This is likely done to avoid detection by traditional antivirus by replacing old binaries with fresh ones unknown to AV engines.
Evasive Azorult
Azorult is an information stealer that uses a quick and dirty approach to steal sensitive data. After it successfully steals sensitive information, it deletes any trace of itself by removing all associated files.
Attack Flow for Azorult
Predator downloads a secondary downloader which is used to download an evasive version of Azorult. In order to download Azorult, this downloader connects to hxxps://2no[.]co/2QqYb5 and downloads an encoded file in a certificate form named bolo.com.
The encoded Azorult payload, a file named bolo.com.
The downloader uses certutil.exe , a native Windows binary, to decode the payload using the living-off-the-land technique. We have previously reported how the Ramnit trojan has been decoded using this technique. The contents of the decoded payload have another layer of obfuscation as well.
The decoded Azorult payload - grol.
To execute the decoded payload, the malware launches the Autoit compiler, which the threat actor renamed to lsm.com. AutoIt is a freeware scripting language used to automate the Windows GUI and general scripting. It is compatible with all versions of Windows with no prerequisites, which makes it a useful tool for attackers looking to create malware.
Cybereason UI: the attack tree of the evasive Azorult execution.
Once executed, Azorult scans the file system and searches for sensitive data like browser data, cookies, email clients and cryptocurrency wallets. It copies this data to the %TEMP% directory, packs it, and sends it to the attacker. Once all information has been exfiltrated, Azorult removes all data copied to %TEMP% and deletes its binary to cover its tracks.
STOP Ransomware and the Vidar Stealer
The STOP Ransomware was first discovered in 2018, but began its most aggressive campaigns in early 2019. Over the year, it evolved to strengthen its encryption and evade detection, and at one point was even used to deliver Azorult onto victim’s systems.
Predator downloads the STOP Ransomware from Bitbucket (111.exe) and executes it. STOP gathers information about the target machine by accessing api.2ip.ua and checks to see if it is running on a VM.
STOP creates a folder in %AppData%, copies its binary there, and changes access control to the file using icacls so others cannot access it.
STOP creates a RUN registry key and a scheduled task to execute itself every five minutes. While running, it connects to the C2 server, sends the C2 the MD5 hash of the MAC address, and downloads a key for file encryption.
STOP also downloads additional payloads onto the machine, including:
- hxxp://ring2[.]ug/files/cost/updatewin2.exe
- hxxp://ring2[.]ug/files/cost/updatewin1.exe
- hxxp://ring2[.]ug/files/cost/updatewin.exe
- hxxp://ring2[.]ug/files/cost/3.exe
- hxxp://ring2[.]ug/files/cost/4.exe
- hxxp://ring2[.]ug/files/cost/5.exe
updatewin.exe and updatewin2.exe help STOP evade detection, and the other payloads are independent pieces of malware: the Visel Trojan, the infamous Vidar stealer, and several other files.
Cybereason UI: the process tree of STOP Ransomware and Vidar stealer.
Vidar is a well-known information stealer that collects system information, passwords from browsers, email, and two-factor authentication software data. It stores stolen data in a randomly named folder in %ProgramData% and sends the info to its C2 server, besfdooorkoora[.]com. After the data is sent to the attacker, the malware stops the process and deletes its payload from the machine (5.exe).
Evasive Monero Miner: Old Miner, New Dropper
Ever since the rise of Bitcoin, miners have gained popularity in the underground community, becoming one of the best sellers for attackers looking to make an easy profit. In this campaign, attackers continue this trend by distributing an Evasive Monero Miner.
The Evasive Monero Miner is a dropper that drops a version of the infamous, open source XMRig miner based on its original source code. An older version of the Evasive Monero Miner was first submitted to VirusTotal in late 2018, but was not discovered until December 2019 after a massive campaign that infected machines all over the world.
The dropper is packed with Themida, a powerful packer with anti-debug features and a way of packing that intentionally makes it difficult to manually unpack. It uses an Autoit compiled script to unpack and download the XMRig miner. The dropper also uses several evasive techniques it uses to avoid detection, including code injection, file renaming, encoded files, non-executable extensions, and the ability to connect through Tor.
Deep Dive into the Monero Dropper
When the Evasive Monero Miner is first executed, it drops several files in the %TEMP% folder:
- CL_Debug_Log.txt
- CR_Debug_Log.txt
- Asacpiex.dll (same as CR_Debug_Log.txt)
CL_Debug_Log.txt is the binary for the 7zip executable renamed to hide its activity. It extracts and decodes a 7zip archive named CR_Debug_Log.txt. CR_Debug_Log.txt extracts a 32-bit and 64-bit version of the payload of the miner, 32.exe and 64.exe, into %TEMP%.
After extracting the payload, the dropper deletes the encoded archive CR_Debug_Log.txt and checks if the machine’s architecture is 32-bit or 64-bit. Depending on the results of the check, it copies the relevant binary, renames it helper.exe, and saves it in \AppData\Roaming\Microsoft\Windows.
Cybereason UI: attack tree of the execution of the XMRig Miner Dropper
The dropper also creates an XML file in %TEMP% named SystemCheck.xml along with a scheduled task SystemCheck that runs the XML file every minute.
The XML file is configured to run helper.exe with the argument -SystemCheck:
How Sys5emCheck.xml executes helper.exe.
helper.exe is a compiled Autoit script. The script sets a few variables for the malware configuration, including:
- Command line parameter
- TCP Protocol
- The mining pool for the miner, with port manip2[.]hk:7777.
- A list of processes it must check to see if it is being analyzed.
- Two URL paths public2/udp.txt and public2/32/32.txt, or fpublic2/64/64.txt for the 64-bit version.
- A password DxSqsNKKOxqPrM4Y3xeK that, based on the name of the variable, is used to decrypt an archive.
helper.exe decompiled code: the variables setting.
helper.exe contains two embedded binaries built during execution, the first of which is a 7zip binary.
helper.exe decompiled code: 7Zip binary embedded code.
The second is an encoded 7zip archive for a Tor client named Tor.tmp. Tor.tmp is decoded using the embedded password in helper.exe and extracted to \AppData\Roaming\Microsoft\Windows\Tor\.
helper.exe decompiled code: Tor client embedded code.
Cybereason UI: command line used to extract the Tor.tmp archive.
The dropper checks for various antivirus engines on the target machine, as well as if the SmartScreen feature of Windows Defender exists. SmartScreen is used to protect against phishing and various malware websites.
The helper.exe decompiled code: an embedded list of security products.
helper.exe holds four domains encoded in Base64:
helper.exe decompiled code: embedded Base64 encoded domains.
The decoded domains:
- bgpaio75egqvqigekt5bqfppzgth72r22f7vhm6xolzqd6ohroxs7pqd[.]onion
- jr2jjfxgklthlxh63cz3ajdvh7cj6boz3c3fbhriklk7yip4ce4vzsyd[.]onion
- uovyniuak3w4d3yzs4z4hfgx2qa6l2u6cx4wqsje4pmnmygc6vfddwqd[.]onion
- Rcjndzwubq5zbay5xoqk4dnc23gr4ifseqqsmbw5soogye6yysc7nkyd[.]onion
The dropper uses the Tor client to connect to one of the decoded domains, combined with the URL paths, and downloads the contents into a file named SysBackup.tmp and the malware version into a file name upd.version to the target machine. Both of these files are created under \AppData\Roaming\Microsoft\Windows\.
helper.exe decompiled code: creating the GET request that downloads the XMRig miner - SysBackup.tmp.
After the file is downloaded, the dropper terminates tor.exe.
Sysbackup.tmp houses a bytes array for the XMRig miner executable.
XMRig file properties.
helper.exe spawns attrib.exe and injects the XMRig miner code into memory.
XMRig code floating in memory of attrib.exe. Taken using Process Hacker.
The dropper executes attrib.exe with a command line that specifies the mining pool and the wallet where the miner will add its resources.
helper.exe decompiled code: building the command line for attrib.exe.
Closing Thoughts
Attackers continue to abuse legitimate online storage platforms for their own gain. By storing malicious payloads on trusted platforms, attackers can bypass security products to exploit the trust given to legitimate online services. In addition, it provides the attackers with another way of reducing the risk of exposure to their C2 server infrastructure through separating the delivery infrastructure (online storage platforms) from the C2 server infrastructure.
In some ways, this attack takes persistent revenue to the next level. These attackers infect the target machine with different kinds of malware to get as much sensitive data as possible, alongside miner capabilities and ransomware capabilities. This attack is the epitome of “have your cake and eat it too”, with attackers layering malware for maximum impact.
Attackers continue to evolve and look for more effective ways to make a profit. They are finding that, when their tools fail, they can use legitimate ones instead. Security practitioners must find ways to evolve faster and ensure the security of these trusted resources so we can stay ahead of these threats.
The best way to defend against an attack like this is to use an iterative security process. Learn more in our whitepaper, "Unleashing the true potential of MITRE ATT&CK."
Indicators of compromise
Click here for a full list of the IOCs (PDF).
MITRE ATT&CK BREAKDOWN
|
Initial Access |
Execution |
Persistence |
Privilege Escalation |
Defense Evasion |
Credential Access |
Collection |
C&C |
