Research by: Assaf Dahan
The Ursnif trojan (also known as Gozi ISFB) is one of the most prolific information stealing Trojans in the cybercrime landscape. Since its reappearance in early 2013, it has been constantly evolving. In 2015, its source code was leaked and made publicly available on Github, which led to further development of the code by different threat actors who improved it and added new features.
Over the past few years, Japan has been among the top countries targeted by Ursnif’s operators. In 2018, Cybereason as well as other security companies reported about attacks where Ursnif (mainly the Dreambot variant) and Bebloh (also known as URLZone and Shiotob) were operating in conjunction. In these joint campaigns, Bebloh is used as a downloader that runs a series of tests to evaluate whether it is running in a hostile environment (for example, it checks to see if it is running on a research VM). Once the coast is clear, it downloads Ursnif, which carries out its core information stealing functions.
The newly discovered Ursnif variant comes with enhanced stealing modules focused on stealing data from mail clients and email credentials stored in browsers. The revamping and introduction of new mail stealer modules puts an emphasis on the risk that trojans can pose to enterprises if corporate accounts are compromised. With more and more banking customers shifting to mobile banking and the continuous hardening of financial systems, it is not surprising that trojans are focusing more than ever before on harvesting other types of data that can also be monetized and exploited by the threat actors, including mail user accounts, contents of email inboxes and digital wallets.
Contents of this Research:
- OLD -NEW TRICKS, NEW VARIANT
- STAGE ONE: PHISHING VIA OFFICE DOCUMENTS
- MODIFIED VBA MACRO TARGETS JAPANESE USERS
- OLD VBA COUNTRY CHECK
- NEW VBA COUNTRY CHECKS
- MODIFIED VBA MACRO TARGETS JAPANESE USERS
- STAGE TWO: PARANOID POWERSHELL DOWNLOADER
- NEW LANGUAGE SETTING TEST
- GEO-IP LOCATION CHECK
- USAGE OF STEGANOGRAPHY TO HIDE THE PAYLOAD IN PLAIN SIGHT
- POWERSPLOIT REFLECTIVELY LOADS BEBLOH
- STAGE THREE: URSNIF'S LOADER
- STAGE FOUR: URSNIF CORE PAYLOAD CLIENT.DLL
- NOTABLE CHANGES IN CORE FUNCTIONALITY
- NEW STEALTHY PERSISTENCE MECHANISM
- DETAILED PERSISTENCE CREATION LOGIC
- DETAILED PERSISTENCE REMOVAL LOGIC
- CHANGES IN THE INFORMATION STEALING MODULES
- CHANGES IN THE MAIL STEALER FUNCTIONS
- CRYPTOCURRENCY AND ENCRYPTED DRIVES STEALER
- THWARTING SECURITY PRODUCTS MODULES
- ANTI-PHISHWALL MODULE
- ANTI-RAPPORT MODULE
- CONCLUSION
- INDICATORS OF COMPROMISE
Old-New Tricks, New Variant
Since the beginning of 2019, Cybereason researchers have observed a campaign that specifically targets Japanese users across multiple customer environments. This campaign introduced a new Ursnif variant as well as improved targeted delivery methods through Bebloh.
Ursnif’s new variant main changes:
- A new, stealthy persistence mechanism (“last minute persistence”).
- New, revamped stealing modules (“#IESTEALER#”, “#OLSTEALER#”, “#TBSTEALER#”).
- Cryptocurrency and disk encryption software module (e.g Bitcoin, TrueCrypt).
- An Anti-PhishWall module to counteract PhishWall, a Japanese security product.
Enhanced country-targeted delivery methods to ensure the delivery of Bebloh include:
- Modified VBA code that specifically checks Japanese settings on the infected machine.
- PowerShell that compiles a .NET DLL to check language settings (Japanese).
- An added IP geolocation check to determine whether the infected machine is in Japan.
The following chart demonstrates the infection chain observed in the latest campaign:
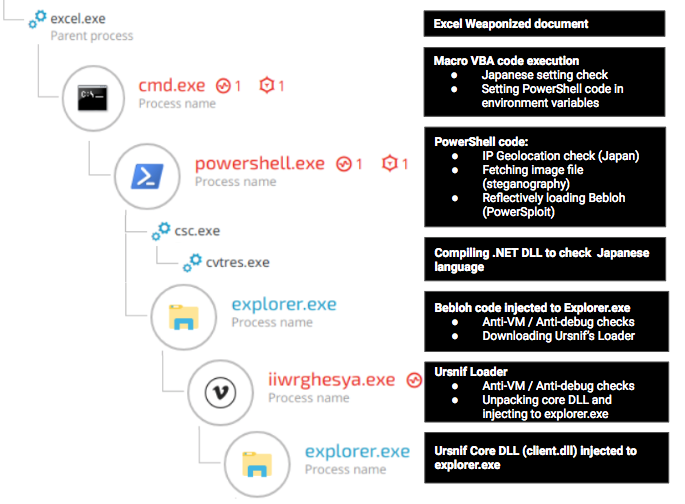
Stage One: Phishing via Office Documents
The first stage of the attack starts with a weaponized Microsoft Office document attached to a phishing email:
When the user opens the document, the Japanese text instructs the unsuspecting user to click on the Enable Content button. They expect to see a preview of a document, but instead it will execute the embedded macro code:
Weaponized Excel document that encourages the user to click on Enable Content.
Modified VBA Macro Targets Japanese Users
The macro code is obfuscated and results in the execution of several PowerShell commands. However, before the PowerShell commands are decrypted and executed, the VBA macro checks if the victim machine has Japanese country settings. This technique was previously seen in 2018, but the attackers modified the code in this version to make it less obvious and harder to detect.
Old VBA Country Check
The previous check, documented by Nao_Sec, consisted of comparing the country setting to the value of ‘81’ for Japan, using the function xlCountrySetting. If the machine doesn’t have Japanese settings, the macro code exits.
New VBA Country Checks
The new country check function in this variant makes it less obvious to understand which country is being targeted, however it can still be easily inferred with a bit of basic calculation. The new code checks the country setting, adds ‘960’ to it, and stores the new value in a parameter. In this case, the parameter is opa (81 + 960 = 1041):
The SensitiveLine() function checks if the value of “opa” is greater than ‘1039.93’, in which case, the macro code will continue. If not, the code will exit. The calculation is the following:
The value of xlBinsTypeBinSize (‘3’) * 347 - 1.07 = 1,039.93
Note: Similar techniques were implemented in a campaign that targeted Italian users, which delivered a different Ursnif variant.
Stage Two: Paranoid PowerShell Downloader
Once the macro code ensures that the machine is Japanese, it decrypts the PowerShell payload, sets it as environment variables, and executes the code:
PowerShell code hidden in environment variables.
Snipped PowerShell code.
The code is heavily obfuscated and contains a set of additional tests to ensure that the targeted machine not only has Japanese settings, but is also physically located in Japan prior to downloading Bebloh’s payload.
New Language Setting Test
Before downloading the payload, the PowerShell code runs a final language check to ensure the target is indeed Japanese. It matches the result of the Omk() function against ‘j’, for Japanese:
The file is compiled and dropped in the %temp% folder:
The decompiled code shows the Omk() function that checks the CultureInfo.CurrentCulture property:
Geo-IP Location Check
The downloader’s last test is a geolocation test using the ipinfo.io API to verify that the IP address is Japanese:
Detecting country by IP geolocation.
Usage of Steganography to Hide the Payload in Plain Sight
Once all the checks are done, the PowerShell code downloads an image file hosted on an image sharing websites such as Imgur or postimage.cc: hxxps://i.imgur[.]com/96vV0YR[.]png
Even the images have Japanese theme. ^_^
The embedded content is decrypted by the following PowerShell code, which is based on the Invoke-PSImage steganography project:
PowerSploit Reflectively Loads Bebloh
The decrypted PowerShell code embedded in the image is based on the PowerSploit framework that uses the reflective PE injection module Invoke-ReflectivePEInjection to load and execute Bebloh’s code to memory:
Excerpt from decrypted content hidden in the downloaded image.
The unpacked payload dumped from the injected explorer.exe indicates that the payload is in fact Bebloh:
Once Bebloh is injected to explorer.exe, it downloads Ursnif’s loader payload from the C2 server:
Bebloh drops Ursnif depicted through a malicious PowerShell process and child processes shown in the Cybereason Defense Platform.
Stage Three: Ursnif’s Loader
Ursnif’s loader unpacks the main payload (client.dll / client64.dll), which is embedded in the loader’s PE resource section (RT_RCDATA):
32-bit and 64-bit version of client.dll.
Prior to its decryption, the loader conducts a series of tests to determine whether the loader is running in a hostile environment, namely, whether it is being debugged or run in a sandbox or virtual machine. For example, Bebloh runs the following checks:
- A Xeon CPU check to determine whether it is running on a server, laptop, or PC.
- A virtualization vendor check to determine whether it is running in vbox, qemu, vmware or on a virtual hd.
- A timing check (RDTSC with CPUID to force a VM exit and to thwart debuggers and sandboxes).
The following is an example of virtualization checks using the SetupDiGetClassDevsA() and SetupDiGetDeviceRegistryPropertyA() APIs to query hardware information stored in the Windows registry:
If any of the above tests returns positive, the loader displays an error message and terminate the process:
Error message displayed upon VM detection.
If all the tests check out, it will proceed and inject Ursnif’s core DLL to the main explorer.exe process.
Stage Four: Ursnif Core Payload client.dll
The injected DLL payload includes an interesting PDB path of client64.dll, suggesting that it is Gozi ISFB version 3:
PDB path: c:\isfb3\x64\Release\client.pdb.
Its build number (version number) extracted from memory indicates that its version “300035”:
The compilation date is 22/02/2019, which also suggests that it was compiled recently:
We have found an earlier sample of the same variant in the wild with a compilation timestamp that dates to July 2018, suggesting that the variant first emerged in 2018:
Notable Changes in Core Functionality
Throughout the years, Ursnif’s code original code has changed to introduce different strains and new features. For a detailed analysis of Ursnif’s previous versions and functionality, please see the following write-ups by Vitali Kremez, Mamoru Saito and Maciej Kotowicz.
Based on our code analysis, the newly observed variant bears great resemblance to the Dreambot variant. However, it lacks some commonly observed built-in features like the Tor client and VNC module. The new variant exhibits several new or revamped features, such as:
- A new persistence mechanism (last minute persistence that resembles Dridex’s persistence).
- Revamped and new stealer modules (IE Stealer, Outlook Stealer, Thunderbird Stealer).
- A cryptocurrency and disk encryption software module.
- An Anti-PhishWall module to counteract PhishWall, a Japanese security product.
New Stealthy Persistence Mechanism
One of the most noticeable changes observed in this new variant is the implementation of a new persistence mechanism designed to evade detection.
The newly observed persistence mechanism is based on the "last minute persistence" model. This model creates its persistence at the very last moment before the system shuts down. Once the system is rebooted and the loader injects the core DLL to explorer.exe, it immediately deletes its registry autorun key along with the files stored in %appdata%. Similar implementations have been used by Dridex and Bebloh banking trojans in the past.
it is interesting to mention that the above mention persistence is different than the fileless persistence mechanism reported by Cisco and other researchers between December 2018 and February 2019. The previous technique relied on a PowerShell script stored in the registry. Upon boot, it dynamically loads and injects the core DLL to explorer.exe using the QueueUserAPC injection technique.
The following is a chart that demonstrates the “last minute persistence” creation and removal logic on an infected machine:
Detailed Persistence Creation Logic
- The malware creates an invisible window used for internal communication between the trojan’s different components:
- Ursnif uses this window among other things in order to catch the WM_QUERYENDSESSION message. This message is typically sent when the system is about to shut down, thus alerting the malware of an imminent shutdown:
- Once Ursnif is made aware of the shutdown message, it creates an autorun registry key along with files in the %appdata% folder, based on information found in the Install key found in - HKCU\Software\AppDataLow\Software\Microsoft\{GUID}\Install
Booting the machine in Safe Mode, can reveal the created persistence, as it prevents any program from running automatically when the user logs on:
.lnk and .exe file in %appdata% created before the system shuts down.
Registry Autorun key created before the system shuts down.
Detailed Persistence Removal Logic
Once the system boots and the user is logged on, the loader runs and injects the core DLL to explorer.exe. Once the trojan’s code runs:
- It checks for the existence of the “ProgMan” window, indicating that the explorer.exe process is running:
- It checks whether the malware code is running from the same process (explorer.exe), likely as an anti-debugging measure:
- It deletes registry keys and the %appdata% folder where the .lnk and .exe files exist based on the on the Install key in HKCU\Software\AppDataLow\Software\Microsoft\{GUID}.
Changes in the Information Stealing Modules
The new variant (V3) exhibits changes in the code of its stealer modules in comparison with:
- Dreambot (unpacked client.dll - 2bcb80182ed4ca4701ab0bcd750d5aacac83d77)
- Gozi ISFB 2.16 / 2.17 (unpacked client.dll - 74e7453b33119de1862294e03bf86cc7623d558b)
Changes in the Mail Stealer Functions
The new variant’s mail stealing functionality seems to have undergone a major update that includes enhancements and some new functionality, like: a Microsoft Outlook stealer, an Internet Explorer stealer, and a Mozilla ThunderBird stealer.
Excerpt of the mail stealer’s main function.
The following comparative chart demonstrates the changes to the main mail stealing functions between recent variants:
#OLSTEALER# - the Revamped Outlook Stealer
The new OLSTEALER module enumerates stored Microsoft Outlook accounts on the infected machine:
This new variant adds support for multiple Microsoft Outlook versions, as opposed to previous versions that typically support one or two versions:
In addition, it adds the capability to locate Microsoft Outlook’s .PST and .OST file extensions:
#TBSTEALER# - Mozilla ThunderBird Stealer
This variant adds the capability to steal data from the Mozilla ThunderBird mail client, stored in:
- Thunderbird Stored Credentials (logins.json)
- ThunderBird Personal Address Book (abook.mab)
Extracting ThunderBird user credentials.
#IESTEALER# - Internet Explorer Stealer
The newly added, built-in module steals data stored in Internet Explorer, such as:
- HKCU\Software\Microsoft\Internet Explorer\TypedURLs (Autocomplete typed URLs)
- HKCU\Software\Microsoft\Internet Explorer\IntelliForms\Storage2 (AutoComplete Data, including stored credentials)
- CLSID_CUrlHistory (Browsing History)
CryptoCurrency and Encrypted Drives Stealer
The new variants seems to add the ability to steal data from cryptocurrency wallets as well as disk encryption software:
Digital currency wallets:
- Electrum Bitcoin wallet, Bitcoin wallet, Multibit-hd (a deprecated Bitcoin wallet), Bither Bitcoin wallet, mSigna Bitcoin wallet, Jaxx multi-currency digital wallet, and Bitcoin Armory wallet.
Disk Encryption Tools:
Thwarting Security Products Modules
Anti-PhishWall Module
The new variant adds a built-in anti-PhishWall module to its capabilities. PhishWall is an anti-phishing and anti-MITB (Man-in-the-Browser) product created by Japanese cybersecurity company Securebrain. The product is quite popular in Japan and is even recommended by several banks and financial institutions as a protection against banking trojans, and more specifically, Gozi.
In light of the product’s popularity in Japan, it is not surprising that the new Ursnif variant added an Anti-PhishWall module similar to other trojans in the past such as Shifu and Bebloh.
This module runs extensive tests to detect and disable the PhishWall product and browser plugin:
1. It checks the registry for if the PhishWall key is present. If it is present, it locates the sbpwu.exe process and terminates it.
2. It checks for a second process (“PhishWall5.1.exe”) and attempts to terminate it.
3. It enumerates Firefox’s browser extensions for the PhishWall extension “\extensions\info.asia@securebrain.co.jp.xpi”. If it finds it, it will attempt to terminate Firefox.
4. Lastly, it attempts to locate the following CLSID in the registry, which are associated with PhishWall:
Important note: The author of this article did not test the Anti-PhishWall code and cannot attest to its validity or quality.
Anti-Rapport Module
While Ursnif’s alleged Anti-Rapport module is not new, it is quite rare to see this module among the variants that hit Japan recently. Rapport is an endpoint protection product by IBM’s Trusteer. Over the years, there have been several types of malware that claimed to bypass or disable Rapport.
This Ursnif variant comes with an Anti-Rapport module which seems heavily based, on Carberp’s Anti-Rapport code. This code was leaked in 2013 and is publicly available on Github.
Excerpt from the Anti-Rapport code found in the new variant:
The variant’s code shows great resemblance to Carberp’s code on Github:
Important note: The author of this article did not test the Anti-Rapport code and cannot attest to its validity or quality.
Conclusion
Ursnif and Bebloh continue to be among the most common information stealing trojans that target Japanese users. The development cycle and the introduction of targeted delivery techniques and variants observed in Japan is quite frequent. It changes tactics every one to two months, in an attempt to evade detection by traditional security products and some sandbox solutions.
What stands out in these campaigns is the great effort made by threat actors to target Japanese users, using multiple checks to verify that the targeted users are Japanese. These multiple tests prove to be quite effective not only in targeting the right crowd, but also in evading security products such as sandboxes, since the malicious code will not run unless the country/language settings are properly configured. We assess that this new wave of country-based targeted delivery is likely to become more and more popular in future campaigns.
Lastly, our research demonstrates that the new variant seems to be quite unique and customized for Japan. It comes with robust information stealing features that focus on mail data, new evasive persistence mechanism and a module to bypass a Japanese security product. Some of the new features of this variant seem to draw inspiration from other trojans that are popular in Japan, such as Bebloh and Shifu. According to Cybereason's telemetry, this variant has been spotted only in Japan so far. It is interesting to see whether this new strain of Ursnif will emerge in other geographical regions.
We have an on-demand webinar all about this research online.
Indicators of Compromise
Excel Document (Macro)
DA85A7DE0B48881EF09179B800D033F27E8F6A01
6BEF7B72A0D314393FAE5F7915A5440DF2ABCF5F
A1CC4B824A35B5E1A016AA9AC0FAC0866C66BFFC
12E6EEA2EC60AC530CB6F683619ED4F571558C3F
F23EDE071D9F0274430D06E2C6E33FF1B1803C5F
B4707DA9396F1BBD3179A10F58815F1E58AC02FA
.NET language checker
Ettivyph.dll - 14181A8F9ACF8B3C55076BEF21217EAF83062B5A
Ursnif Loader (1st Stage):
gyehtuegg.exe - 2B21C3237105DEE871C252633AE65125E78AC23E
Ewwhuptgfq.exe - 99882D848ADF3818AD758B951303F12649967247
Ehuwowstsg.exe - 6EABB986CBA048EE1B81BD884F6ABDD38B7CB5DA
Iiwrghesya.exe - F1F6E136EEAC66278359EB6DAF406FD8504107DB
Bthcan32.exe - C8488A58B5ECE9104AEFBBBB0334199E2E3C3D56
Awerwyae.exe - 610B9128E56D488C7C2C700BD6C45A0250312129
Winklogon.exe - 1D78AA605450C5C02D23BD065996A028A59DE365
FEWPSQUUST.EXE - 8BB7240A38534881FDE3ADD2179EF9E908A09BE8
1770BE655DB3AC9B6561F2CC91DD9CD5DEA3D69B
0147FCC93C78A823BE94191FAE8A105549390C03
Unpacked Loader (dumped from memory)
1BB1BDA50D3C7BAD92872C4FE334203FB706E7C3
Client64.dll (dumped from memory)
8F6536397DC5E0D7699A1B2FDE87220C5D364A20
B6CB96E57951C123B9A5F5D6E75455AFF9648BCB
Client.dll (dumped from memory)
35F7AD2300690E0EB95F6F327ACA57354D8103FF
Domains
baderson[.]com
Mopscat[.]com
Gorsedog[.]com
Pintodoc[.]com
Ropitana[.]com
Pirenaso[.]com
Papirosn[.]com
delcapen[.]com
Steganography URLs
hxxps://i.imgur[.]com/96vV0YR[.]png
hxxp://oi65[.]tinypic[.]com/2z8thcz[.]jp
