RESEARCH BY: AMIT SERPER AND MARY ZHAO
EXECUTIVE SUMMARY
There’s an active, ongoing campaign exploiting a widespread vulnerability in linux email servers. This attack leverages a week-old vulnerability to gain remote command execution on the target machine, search the Internet for other machines to infect, and initiates a crypto miner.
- Currently, more than 3.5 million servers are at risk worldwide.
- The attack scours the Internet for a vulnerability discovered last week, CVE-2019-10149 using already infected servers to spread to as many as possible.
- The target of this attack, exim servers, run almost 57% of the Internet's email servers.
- The attack culminates in the downloading of a coin miner payload, which as we have seen previously with WannaMine can have a negative impact on any organization.
- These kinds of attacks have big implications for organizations. The recovery process from this type of attack is costly and time consuming.
Want to read about a similar incident? Check out our breakdown on WannaMine.
SECURITY RECOMMENDATIONS
- Patch every EXIM installation you have in your organization and make sure that it is updated to the most recent version, 4.92 at the time of this writing.
- Look for any unfamiliar cronjobs in your crontab and remove them. Restore legitimate cron jobs from existing backups.
- Delete the authorized key used for SSH backdoor access.
- Kill the coinminer process and delete the coinminer.
- Check your firewall and access logs for the following hostnames:
-
- https://an7kmd2wp4xo7hpr.tor2web.su
- https://an7kmd2wp4xo7hpr.tor2web.io
- https://an7kmd2wp4xo7hpr.onion.sh
- Re-image any compromised servers.
-
INTRODUCTION
CVE-2019-10149, which was first discovered on June 5, is now being used as the vulnerability for a widespread campaign to attack exim servers and propagate across the Internet.
When first discovered by the Qualys research team, it was dubbed “The Return of the WIZard”. Successfully exploiting this vulnerability enables both local and remote command execution as root.
We are aware of an initial wave of attacks that use this vulnerability as described by Freddie Leeman on June 9, 2019. The first hacker group began pushing exploits from a C2 server located on the clear web.
A second round of attacks by a different attacker have been analyzed by the Nocturnus team.
Note: This is a very long script that downloads additional scripts and changes or adds many configurations on Linux servers. This blog has the highlights of what the script is doing to provide a fast reference guide to this attack. Some of the things that the script is doing are not documented in this blog post. The hash of the script is available at the end of this article. It has also been uploaded to VirusTotal.
THE ATTACK
The Cybereason team has discovered Monero cryptocurrency miners installed on Linux servers running vulnerable versions of Exim: aka, cryptojacking. Cryptocurrency miners are applications that use system resources without the system owner’s knowledge or consent to generate profit in the form of virtual coins.
The infection chain begins with remote command execution to download a malicious script that retrieves code from tor2web domains and uses worm capabilities to spread to other vulnerable systems.
The attackers use the victim machine to scan the Internet for other vulnerable Exim servers. Once found, the attackers will exploit the server to get remote command execution on it and downloaded a script from a tor hidden service through a tor2web service.
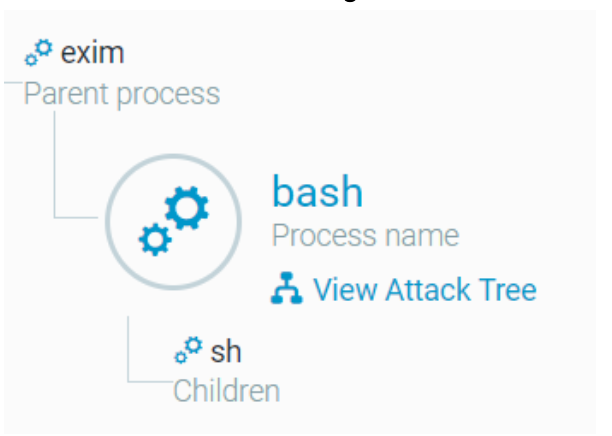
Bash as a child process of Exim as seen in the Cybereason platform.
The script has defined three tor2web ‘translation’ services,
tor2web translation services.
Rhost is the hidden service address excluding the .onion tor domain.
TOR1, TOR2, and TOR3 are the ‘translation’ services that will be concatenated later on to create a URL. They will use one of the ‘translation’ services in a round-robin sort of way.
The script looks for any running crypto miners like cryptonight, ddgs, Kerberods, and nicehash. If it finds any, it terminates them.
Next, the script ensures the HUP signal cannot be sent to it. This ensures that even if the terminal is disconnected, the script will continue to run in the background.
The attack tree as shown by the Cybereason platform.
The script generates a random string for a file name and a file created in multiple paths.
The randomly generated string for a file name.
Once the file is created, a cron job is generated to continuously download an updated version of this ‘installation’ script, save it to the randomly generated file name, and perpetually execute it.
Perpetually downloading, saving, and executing the ‘installation’ script.
Existing cron jobs are subsequently deleted.
Deleting existing cron jobs.
The script downloads busybox’s rm, crond, and crontab implementations.
The script downloading rm, crond, and crontab.
Once the cron jobs are added, the script adds an RSA SSH authentication key into the SSH server.
The SSH authentication key found in the public/private key authentication file.
The script configures the SSH server to accept root logins, RSA authentication, PAM and password authentication.
Configuring the SSH server to accept root logins, RSA authentication, PAM and password authentication.
After additional housekeeping operations like deleting temporary files, changing permissions, etc., the script downloads another script from the same server entitled ‘main’.
Note: If SSH is not installed on your server, the script will determine which Linux distribution is installed and install an openssh server using the appropriate package management system (pacman, yum, apt-get, etc).
The ‘main’ Script
Note: In its original form, main is Base64 encoded and must be decoded in order to analyze it.
To start, main determines the Linux distribution on the target machine by executing uname -a and storing it’s output in local variable $ARCH. It looks for the string “alpine” in the output, and if it is present, it overwrites local variable $Pref.
Overwriting $Pref if “alpine” is in the output.
$Pref is used later on to determine which kind of coinminer payload to download.
The script looks for other coin miners running in the background, or orphaned processes related to a previous infection, and if any are found, they are terminated.
The script creates a watchdog with variable $wdog0 that checks if there are any processes running and, if none are running, it downloads the main script, decode it and execute it with a bash process.
The script creating the watchdog.
The script has a function e() which runs an inline python script that is Base64 encoded. Once decoded and executed, the script downloads another Base64 blob that decoded into a python script that is a port scanner and exploiter. This scanner-exploiter generates IP addresses while skipping the private IP prefixes. It connects to vulnerable redis hosts to distribute it’s crypto miner through redis in a very similar fashion to this RedisWannaMine campaign.
Downloading the Coinminer
So far, we have discussed the infrastructure work of the operation to establish the coinminer. This next part revolves around downloading the coinminer.
The $Pref variable is used to determine which version of the coinminer the script should download.
The coinminer hidden using a nifty trick.
In the script, there are Windows icon (.ico) files.
The Windows icon files.
- ${Pref}64x75.ico - The 64-bit Payload
- ${Pref}32x75.ico - The 32-bit Payload
Identifying the value of the ${Pref} variable.
The value of ${Pref} can be a or r depending on the operating system version that’s detected by the script. The script uses this to determine the URL of the file to be downloaded and downloads it manually.
The downloaded file is a .ico file.
Identifying the file as a .ico file.
The file has the correct .ico file header of 00 00 01 00.
The hexdump of the .ico file.
The file has an actual icon of the GitHub logo.
The icon of the .ico file.
This explains why the .ico file is detected as an .ico file. In addition, there is another file header hiding further down in the .ico file in offset 4028.
Identifying the file as a zip file.
The file has a pkzip header, which means that this file, while pretending to be an icon file, is actually a zip file. When unzipping the file, it asks for a password.
Trying to unzip the file and being asked for a password.
The password is in the script.
The password for the zip file is located in the script.
Conveniently, the password is “no-password”.
The contents of the zip file.
The file’s strings reveals that this is a UPX packed file.
Identifying the file as a UPX packed file.
In unpacking the UPX, it becomes clear the file is a dynamically-linked x86-64 ELF executable that is stripped from symbols. The strings section reveals that this is an xmr (Monero) coin miner.
The strings section of the unpacked UPX.
Once installed on the infected system, the coin miner makes DNS queries for a newly-registered domain that uses a TLD for the Soviet Union.
Domain for DNS queries.
Conclusion
It is clear that the attackers went to great lengths to try to hide the intentions of their newly-created worm. They used hidden services on the TOR network to host their payloads and created deceiving windows icon files in an attempt to throw off researchers and even system administrators who are looking at their logs.
The prevalence of vulnerable exim servers (3,683,029 across the globe according to Shodan) allows attackers to compromise many servers in a relatively short period of time, as well as generate a nice stream of cryptocurrency revenue. We highly recommend following the security recommendations above to prevent any damage from taking place.
Want to understand how to improve your defense?
IOCs
- Coinminer:
md5: b7d96358d06e3bb12055d2e48c4b9796,
sha1: 0e0d47bf6d025b7936e1ed1308fff1b16ee70239 - Ldm (script):
Md5: b6bb1379b8cb85e14eb71ca8c5ba8a0d
Sha1: 2e89482a14591ade097d252a43d9c1804462ebe6
- Main (script):
Md5: 4cec7074f456a0ba7ccc3e5991cce0e3
Sha1: d0a6f47669e07d938317ba8bf6ecb8d4fbdcfe7f
- Domain - c2 for coinminer
timesync[.]su - Domains - tor2web domains for updater script:
An7kmd2wp4xo7hpr.tor2web.su
An7kmd2wp4xo7hpr.tor2web.io
an7kmd2wp4xo7hpr.onion.sh
