DarkSide is a relatively new ransomware strain that made its first appearance in August 2020. DarkSide follows the RaaS (ransomware-as-a-service) model, and, according to Hack Forums, the DarkSide team recently made an announcement that DarkSide 2.0 has been released. According to the group, it is equipped with the fastest encryption speed on the market, and even includes Windows and Linux versions.
The team is very active on hack forums and keeps its customers updated with news related to the ransomware. In an effort to grow and expand their operations, the group has started an affiliates program for potential users.
Like many other ransomware variants, DarkSide follows the double extortion trend, which means the threat actors not only encrypt the user’s data, but first exfiltrate the data and threaten to make it public if the ransom demand is not paid. This technique effectively renders the strategy of backing up data as a precaution against a ransomware attack moot.
DarkSide is observed being used against targets in English-speaking countries, and appears to avoid targets in countries associated with former Soviet Bloc nations. The ransom demand ranges between US$200,000 to $2,000,000, and according to their website, the group has published stolen data from more than 40 victims, which is estimated to be just a fraction of the overall number of victims:
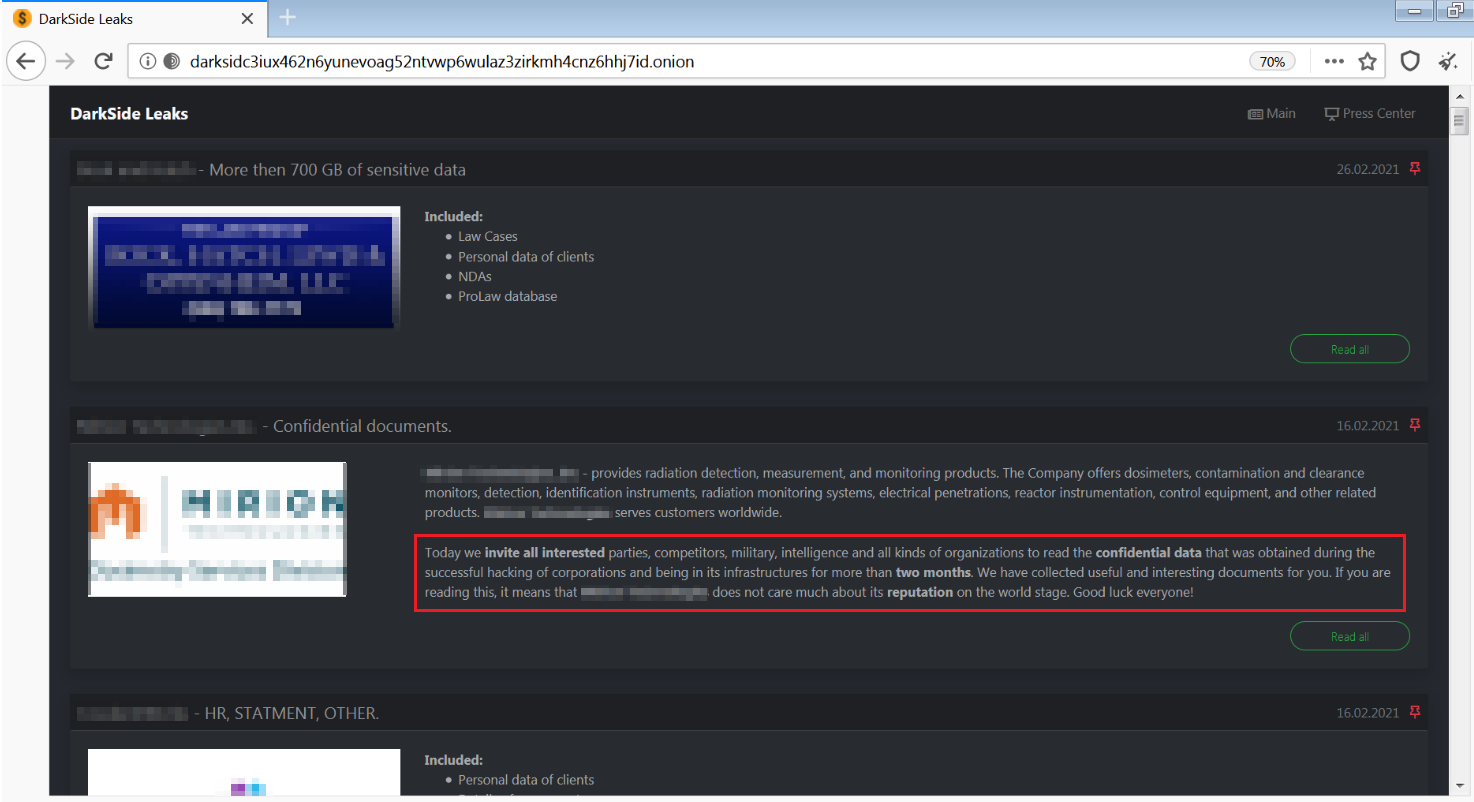
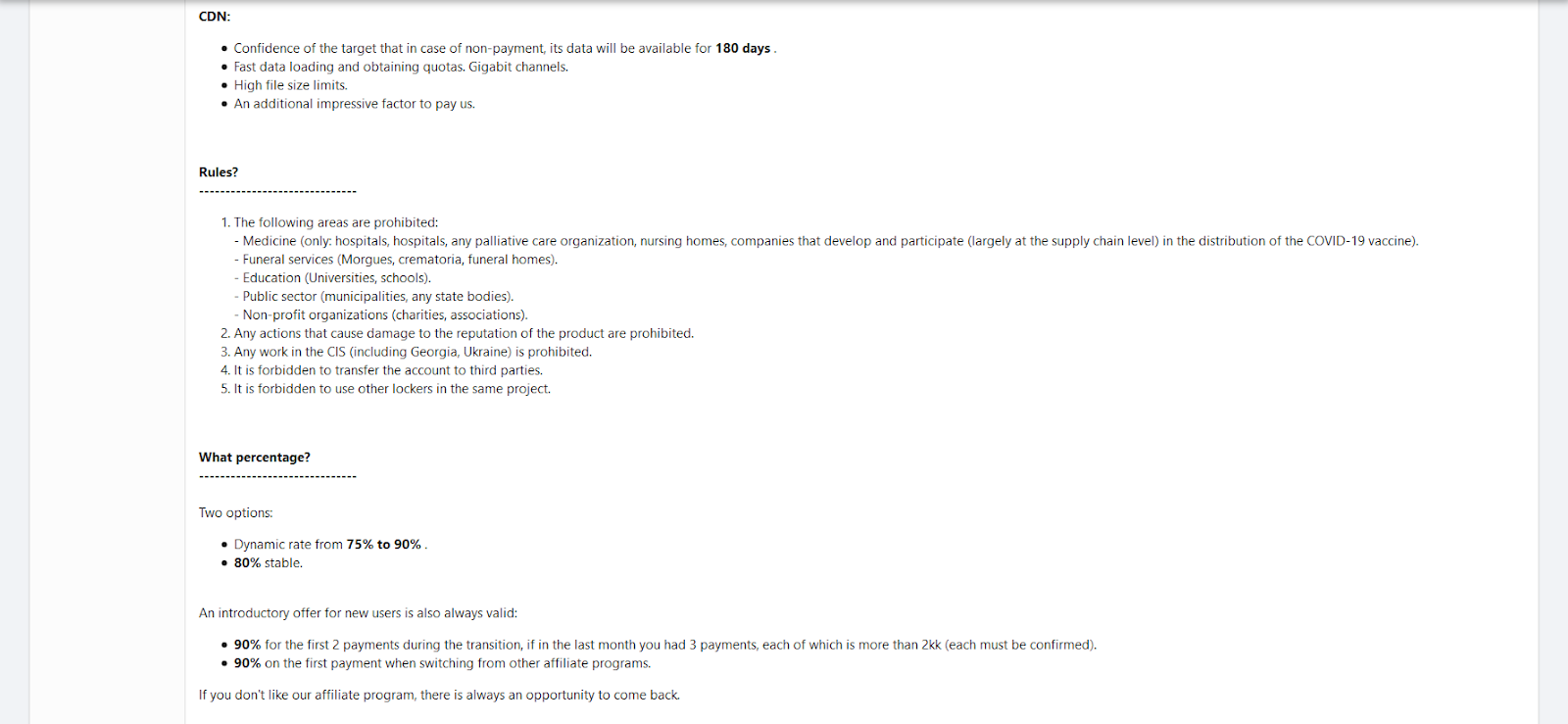
Unlike many ransomware variants such as Maze, which was employed to successfully attack suburban Washington schools, the group behind DarkSide appears to have a code of conduct that prohibits attacks against hospitals, hospices, schools, universities, non-profit organizations, and government agencies:
Key details
• Emerging Threat: In a short amount of time, the DarkSide group has established a reputation for being a very “professional” and “organized” group that has potentially generated millions of dollars in profits from the ransomware.
• High Severity: The Cybereason Nocturnus Team assesses the threat level as HIGH given the destructive potential of the attacks.
• Human Operated Attack: Prior to the deployment of the ransomware, the attackers attempt to infiltrate and move laterally throughout the organization, carrying out a fully-developed attack operation.
• Aiming Towards the DC: The DarkSide group is targeting domain controllers (DCs), which puts targets and the whole network environment at great risk.
• Detected and Prevented: The Cybereason Defense Platform fully detects and prevents the DarkSide ransomware.
Cybereason Blocks DarkSide Ransomware
The DarkSide group is a relatively new player in the game of ransomware. Despite being a new group, though, the DarkSide team has already built itself quite a reputation for making their operations more professional and organized. The group has a phone number and even a help desk to facilitate negotiations with victims, and they are making a great effort at collecting information about their victims - not just technical information about their environment, but more general information about the company itself, like the organization’s size and estimated revenue.
By collecting information about the victims, the group is making sure the ransomware is only used against the “right targets.” The group claims they only target large, profitable companies in their ransomware attacks, and claim to have extorted millions of dollars from companies in an effort to "make the world a better place." The group even wrote in a forum that "some of the money the companies have paid will go to charity… No matter how bad you think our work is, we are pleased to know that we helped change someone's life. Today we sended (sic) the first donations."
The attackers posted tax receipts for their donations
The Darkside group has reportedly tried to donate around $20,000 in stolen bitcoin to different charities, but the charities refused to accept the funds because of the source.
Breaking Down the Attack
Downloading the Ransomware
After gaining an initial foothold in the network, the attackers start to collect information about the environment and the company. If it turns out that the potential target is on the attacker’s list of prohibited organizations to attack (ie: hospitals, hospices, schools, universities, non-profit organizations, or government agencies), they don’t move forward with the attack.
If not on the prohibited list, the attackers continue to carry out the operation:
• The attackers begins to collect files, credentials and other sensitive information, and exfilitrate it.
• The attackers use PowerShell to download the DarkSide binary as “update.exe” using the “DownloadFile” command, abusing Certutil.exe and Bitsadmin.exe in the process:
In addition to downloading the DarkSide binary into the C:\Windows and temporary directories, the attacker also creates a shared folder on the infected machine and uses PowerShell to download a copy of the malware there.
Conquering the Domain Controller
After successfully gaining a foothold on one machine in the environment, the attacker begins to move laterally in the environment, with the main goal of conquering the Domain Controller (DC).
Once the attackers make it to the DC, they start to collect other sensitive information and files, including dumping the SAM hive that stores targets' passwords:
In addition to collecting data from the DC, the attackers use PowerShell to download the DarkSide binary from the shared folder created on the previously infected host:
The attackers also create a shared folder using the company’s name on the DC itself, and copies the DarkSide binary. Later in the attack, after all data has been exfiltrated, the attackers use bitsadmin.exe to distribute the ransomware binary from the shared folder to other assets in the environment in order to maximize the damage:
In order to execute the ransomware on the DC, the attackers create a scheduled task called “Test1” that is configured to execute the ransomware:
DarkSide Analysis
When the DarkSide ransomware first executes on the infected host, it checks the language on the system, using GetSystemDefaultUILanguage() and GetUserDefaultLangID() functions to avoid systems located in the former Soviet Bloc countries from being encrypted:
The malware doesn’t encrypt files on systems with the following languages installed:
|
Russian - 419 |
Azerbaijani (Latin) - 42C |
Uzbek (Latin) - 443 |
Uzbek (Cyrillic) - 843 |
|
Ukranian - 422 |
Georgian - 437 |
Tatar - 444 |
Arabic (Syria) - 2801 |
|
Belarusian - 423 |
Kazakh - 43F |
Romanian (Moldova) - 818 |
|
|
Tajik - 428 |
Kyrgyz (Cyrillic) - 440 |
Russian (Moldova) - 819 |
|
|
Armenian - 42B |
Turkmen - 442 |
Azerbaijani (Cyrillic) - 82C |
DarkSide then proceeds to stop the following services related to security and backup solutions:
|
vss |
sql |
svc |
memtas |
|
mepocs |
sophos |
veeam |
backup |
It then creates a connection to its C2 (command and control) server, and in different samples analyzed, the attackers use the following domains and IPs:
|
198.54.117[.]200 198.54.117[.]198 198.54.117[.]199 198.54.117[.]197 |
temisleyes[.]com catsdegree[.]com |
After uninstalling the Volume Shadow Copy Service (VSS), DarkSide then deletes the shadow copies by launching an obfuscated PowerShell script that uses WMI to delete them:
The de-obfuscated PowerShell script:
Get-WmiObject Win32_Shadowcopy | ForEach-Object {$_.Delete();}
The malware then enumerates the running processes and terminates different processes to unlock their files so it can both steal related information stored in the files and encrypt them.
DarkSide creates a unique User_ID string for the victim, and adds it to the encrypted files extension as follows:
<File_name>.{userid}. In addition, the malware also changes the icons for the encrypted files and changes the background of the desktop:
And, of course, it leaves a ransom note: “README.{userid}.TXT”:
Cybereason Detection and Prevention
The Cybereason Defense Platform is able to prevent the execution of the DarkSide Ransomware using multi-layer protection that detects and blocks malware with threat intelligence, machine learning, and next-gen antivirus (NGAV) capabilities. Additionally, when the Anti-Ransomware feature is enabled, behavioral detection techniques in the platform are able to detect and prevent any attempt to encrypt files and generates a MalopTM for it:
Using the Anti-Malware feature with the right configurations (listed in the recommendations below), the Cybereason Defense Platform will also detect and prevent the execution of the ransomware and ensure that it cannot encrypt targeted files. The prevention is based on machine learning, which blocks both known and unknown malware variants:
Prevention alert of DarkSide ransomware as shown in the Cybereason Defence Platform
Cybereason user notification for preventing the execution of DarkSide
Security Recommendations
• Enable the Anti-Ransomware Feature on Cybereason NGAV: Set Cybereason Anti-Ransomware protection mode to Prevent - more information for customers can be found here
• Enable Anti-Malware Feature on Cybereason NGAV: Set Cybereason Anti-Malware mode to Prevent and set the detection mode to Moderate and above - more information can be found here
• Keep Systems Fully Patched: Make sure your systems are patched in order to mitigate vulnerabilities
• Regularly Backup Files to a Remote Server: Restoring your files from a backup is the fastest way to regain access to your data
• Use Security Solutions: Protect your environment using organizational firewalls, proxies, web filtering, and mail filtering
MITRE ATT&CK TECHNIQUES
|
Lateral Movement |
Execution |
Persistence |
Defense Evasion |
Credential Access |
Discovery |
Command and Control |
Impact |
|
|
|||||||
|
|
