Introduction
- Earlier this year, Cybereason launched its latest honeypot to analyze the tactics, techniques, and procedures used by state-sponsored groups and cyber crime actors to target critical infrastructure providers. This honeypot was a follow up to a previous successful honeypot launched two years ago in 2018 looking at the same industry. The honeypot was built to look like an electricity company with operations in North America and Europe.
- In this new research, the Cybereason team identified multiple attackers executing ransomware operations involving data theft, the stealing of user credentials, and lateral movement across the victims network to compromise as many endpoints as possible. This includes critical assets like the domain controllers, which could take between several minutes to several hours to properly infiltrate.
- Ransomware capabilities were deployed early on in the hacking operation, but it was not immediately detonated. The ransomware was designed to detonate only after preliminary stages of the attack finished across all compromised endpoints in order to achieve maximum impact on the victim.
- This operational attack pattern attempts to impact as many victim assets as possible, representing a higher risk to organizations compared to ransomware attacks that impact the single machine they initially access. However, this operational pattern also represents an opportunity for defenders with a rapid detection and response process to detect the attack at its early stages and respond effectively before ransomware is able to impact the environment.
- Given the results of this research, we conclude that multistage ransomware attacks on critical infrastructure providers are increasingly dangerous and more prevalent.
Check out a condensed, high level version of this report on our threat alerts page.
Background
We live in a world of insecurity where hackers have the advantage over the vast majority of enterprises trying to protect their computer networks. No where is that more evident than with critical infrastructure providers, who are facing a constant barrage of cyberattacks from motivated and oftentimes well-funded groups of cybercriminals and state-sponsored actors.
According to the Department of Homeland Security, critical infrastructure includes ‘the vast network of highways, connecting bridges and tunnels, railways, utilities and buildings necessary to maintain normalcy in daily life. Transportation, commerce, clean water and electricity all rely on these vital systems.’
For years, the most controversial attacks against critical infrastructure were those on the control system of a dam in New York and the shutdown of Ukraine’s power grid. More recently, however, surgical ransomware attacks against companies in the utility and energy sector have dramatically increased. Just this year, Portugal’s largest energy provider EDP fell victim to a ransomware attack where the attackers threatened to release 11 terabytes of sensitive corporate information if an $11 million ransom wasn’t paid.
Also this year, the Israeli government stopped a major cyberattack on its water systems and Iran was likely behind it as reported by media outlets. Add to the list Mexican oil company Pemex, as they were attacked according to Reuters with threats made to cripple the company’s customers.
A Multistage Ransomware Attack: The Cybereason ICS Honeypot 2020
Stage 1
The ICS honeypot environment went live earlier this year and had a network architecture that was masquerading to be part of an electricity generation and transmission provider’s network, including an IT environment, an OT environment and HMI (human machine interface) management systems. The environment employed customary security controls including segmentation between the different environments.
The ransomware attack began by exploiting publicly accessible remote administration interfaces to gain initial access. These remote administration interfaces are often created by network operators to allow technicians to remotely connect to the network and resolve IT tasks and issues.
Based on data collected in real time from the substation's honeypot environment, the attacker was able to brute force the Administrator’s account password and log in remotely. This can be seen in the screenshot below, taken from the Cybereason Defense Platform via Remote Desktop Protocol (RDP).
Once able to log in, the attacker uploaded and executed a PowerShell script that creates a backdoor user (called “admin”) using the net.exe command. The backdoor user was created for persistence purposes so that the attacker could continue their operation unnoticed without indicating to the target that the legitimate administrator account is being used abnormally.
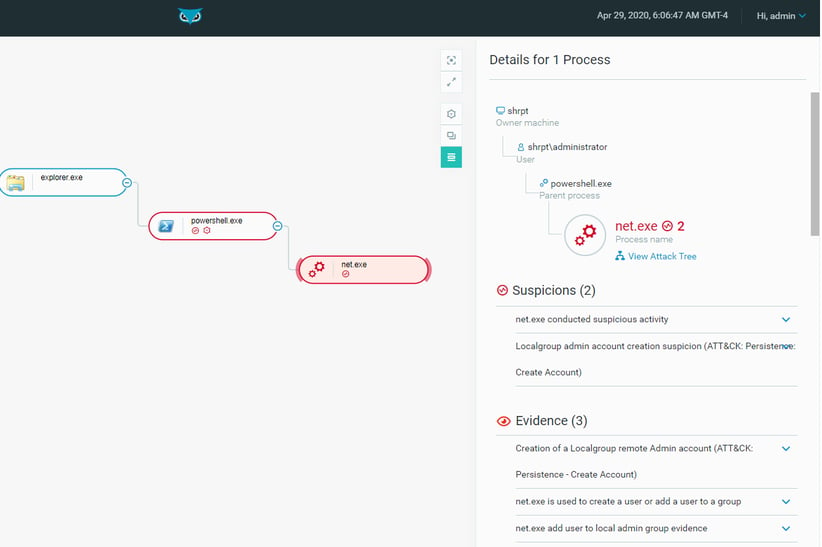
Figure 1: Initial Access via a Compromised RDP Interface to create a backdoor user.
Stage 2
The attack leveraged the established persistence to log back into the compromised server and upload additional attack tools using PowerShell.
One of the uploaded tools was the user credential-stealing tool Mimikatz, which was used to steal user credentials from the compromised server. The user credentials were then used to attempt to move laterally to the domain controllers that are part of the operational backbone of the network, by using the PsExec remote execution utility.
This lateral movement attempt failed in the honeypot environment, as none of the user accounts the attacker was able to steal credentials from were permitted to access the domain controllers.
Figure 2: The Attacker steals user credentials from the server using Mimikatz and attempts to move laterally by using the PsExec remote execution utility.
Stage 3
The malware continues to try to move laterally on the network by leveraging a network scanner to discover additional endpoints.
Figure 3: The attacker uses a network scanner to discover additional endpoints.
Stage 4
Once these other activities are complete, the ransomware detonates on all compromised endpoints.
This activity points to an interesting trend in ransomware attacks. Instead of focusing on a single stage, deploy and detonate approach to ransomware, attackers are using multiple stages to ensure as much financial gain as possible. They not only deploy ransomware, but they also move laterally to affect as many machines as possible and steal credentials before ultimately detonating the ransomware.
Best practices and tips for critical infrastructure operators
Today, many of the networks protecting critical infrastructure providers are old and fragile. While it may seem as though some attackers are more interested in taking control of a network and extorting a ransom, just as many groups continue to test the resiliency of systems. It is only a matter of time before a catastrophic event occurs, putting a nation in the dark or causing damage to the integrity of our electricity networks, water systems, or SCADA networks.
In order to prevent this, we recommend three key best practices:
1. Establish Cyber Incident Response Tools and Procedures across both IT and OT networks with the goal to minimize Mean-Time-To-Response:
Minimizing damage and preventing an ICS network from being taken offline is essentially the cat and mouse game being played by attackers and defenders. To keep hacking groups at bay, organizations need to minimize the time it takes to respond to a threat. This can be achieved by deploying threat hunting services around the clock.
2. Establish Unified Security Operation Center and workflows across both IT and OT environments:
Operating a unified security operations center (SOC) provides visibility into the IT and OT environments because attackers are looking to use IT environments as gateways into OT environments. Some companies may already have a network operations center monitoring the OT environment, but a combined SOC lets operators see all operations as they move through the network.
3. Design and Operate with Resiliency in Mind:
Resiliency and security can no longer be an afterthought. As new critical infrastructure systems are built and installed, legacy networks will be retired and taken offline. It is very important for next-generation systems to be built with resiliency and security in mind. The design and ongoing operation of the system must take into consideration what security threats will become commonplace in the months and years ahead.
- Partner with Experts: Be sure to partner with experts with vast knowledge of ICS threats. The public and private sector need to work together closely to protect this industry. Partner with a security company that can stay ahead of new threats and help operators address issues in real time.
- Test, Test, Test: It is critical that regular testing be a focal point in this sector. Tabletop exercises that enable a red and blue team to role play different catastrophic scenarios and the real time response to those scenarios is critical when having to actually have to deal with a threat in real time. Never underestimate the value of tabletop exercises in shoring up weakened defenses and helping executives understand the importance of security.
Cybereason Honeypot Comparison | 2018 vs. 2020
In 2018, Cybereason created a honeypot resembling a major, well-known electricity provider. In less than two days, attackers got into the environment and conducted reconnaissance activities to find an entry point from the IT environment to the OT environment. Based on the tooling installed by the attackers, Cybereason determined that a black market seller had discovered the environment and was intending to sell it on xDedic.
The seller installed backdoors by creating additional users, another indicator that the asset was being prepared for sale on xDedic. The backdoors allow an attacker to access the honeypot even in the event of a change in administrator passwords. While it was live, the environment was hit with multiple different types of malware, including cryptominers, phishing, DDoS attempts, and other activity that Internet-connected assets typically experience.
Cybereason concluded that the activity in the environment suggested there is an increased risk for critical infrastructure operators. Since honeypot ICS networks continue to be at risk, Cybereason can say with confidence that adversaries are unleashing a constant barrage of ransomware attacks on this sector.
In previous honeypot research Cybereason conducted, and in particular the 2018 ICS network honeypot, we also saw a series of ransomware attacks. These attacks included the typical file encryption capability and, in several cases, self-propagation capabilities that leveraged known operating system vulnerabilities to deliver file encryption.
In comparing the 2018 honeypot to more recent observations in our 2020 honeypot, we have recognized that several ransomware attacks added hacking operations capabilities to their typical file encryption capabilities. We expect this is an attempt to amplify the impact of the attack on the victim, drive up ransomware costs for the victim, and increase the victim’s inclination to pay the ransom.
Conclusion
This research has shown a change over the past two years, as attackers move towards multistage ransomware attacks as part of hacking operations. Ransomware threats to critical infrastructure providers should be a top concern for security teams.
One of the trends that we are seeing in the ICS space and in general, is fewer new strains of ransomware in 2020, yet the existing strains rakes more gains. Hackers do this by better targeting and making more money from each target. We can expect to see an increase in multistage ransomware embedded into hacking operations in the foreseeable future.
Also, attackers are succeeding in these operations by breaking in and debilitating the business, making huge claims, but then in addition, the entities that often pay the ransoms are insurance companies. The more we see headlines, the more companies will pay for insurance, which will increase the number of attacks. It will continue to increase until the cost of the insurance becomes comparable to the cost of fixing the problem.
Looking for more insights on combating modern ransomware? Check out our live panel Q&A with Rich Rushing - CISO at Motorola Mobility; Bob Bigman - former CISO of the CIA; and Israel Barak - CISO at Cybereason.
