emotet explained
- This campaign adapts Emotet as a dropper for the TrickBot trojan. TrickBot then steals sensitive information and downloads the Ryuk ransomware.
- This research gives unique detail to each phase of the campaign, from Emotet’s use as an infrastructure to deliver TrickBot, to TrickBot’s information stealing capabilities, lateral movement, and use as a downloader for Ryuk, and finally to Ryuk’s ransomware capabilities.
- As a modular trojan, TrickBot is evolving all the time. In past research, it has been used to download the Ryuk ransomware. In this campaign, it is used to deliver a one-two punch to the victim. Not only does it steal personal data and credentials including passwords, mail files, browser data, registry keys, and more, but it also downloads Ryuk, which encrypts their machine and ransoms their data for payment.
- This campaign targets companies in Europe and the USA, and signals a change in trend for Emotet and TrickBot, which are both well-known trojans.
- In this attack, Emotet is used as a dropper for the TrickBot trojan instead of performing its own malicious activities as a trojan.
- TrickBot has evolved to include advanced capabilities like password collecting, detection evasion, the launching of an Empire PowerShell backdoor, and the ability to download the Ryuk ransomware. In addition, it has a module that allows an attacker to remotely view and control a victims desktop.
- This campaign used many advanced persistence, lateral movement, and detection evasion measures, including attempts to disable Windows Defender, the use of EternalBlue to spread, and the stopping of multiple services and processes related to anti malware products.
Full research on the Emotet-TrickBot-Ryuk campaign can be found here.
The Triple Threat Campaign of emotet, trickbot, and ryuk
Emotet was first discovered in 2014 as a trojan used to steal banking credentials. More recently, it has been used as a dropper of other trojans. It has introduced several advanced capabilities over the years due to its modular structure, including an installation module, banking module, and DDoS module. Emotet is mainly distributed through phishing emails using various social engineering techniques.
TrickBot was first discovered in 2016 as a modular trojan inspired by Dyreza, another trojan and data stealer. TrickBot uses mimikatz to harvest emails and other credentials. Some variants have been known to steal from Bitcoin wallets as well. Although trojans typically target individuals to steal bank account credentials, the TrickBot trojan in this research is being used to also deliver secondary malware.
Ryuk ransomware was first detected in August of 2018 in targeted attacks through an unknown infection method. It was able to gain access via Remote Desktop Services or other direct methods, and from there stole credentials and targeted high-profile data and servers to extort ransoms. By January 2019, an active campaign of the Ryuk ransomware was discovered targeting victims who were previously attacked by TrickBot. Previous research also showed campaigns of Emotet-TrickBot-Ryuk used to deploy and initiate the Ryuk ransomware. Those differ from the campaign mentioned in this research, as this campaign describes each phase of the attack in detail, as well as the use of TrickBot to steal sensitive information before deploying Ryuk to ransom victims data.
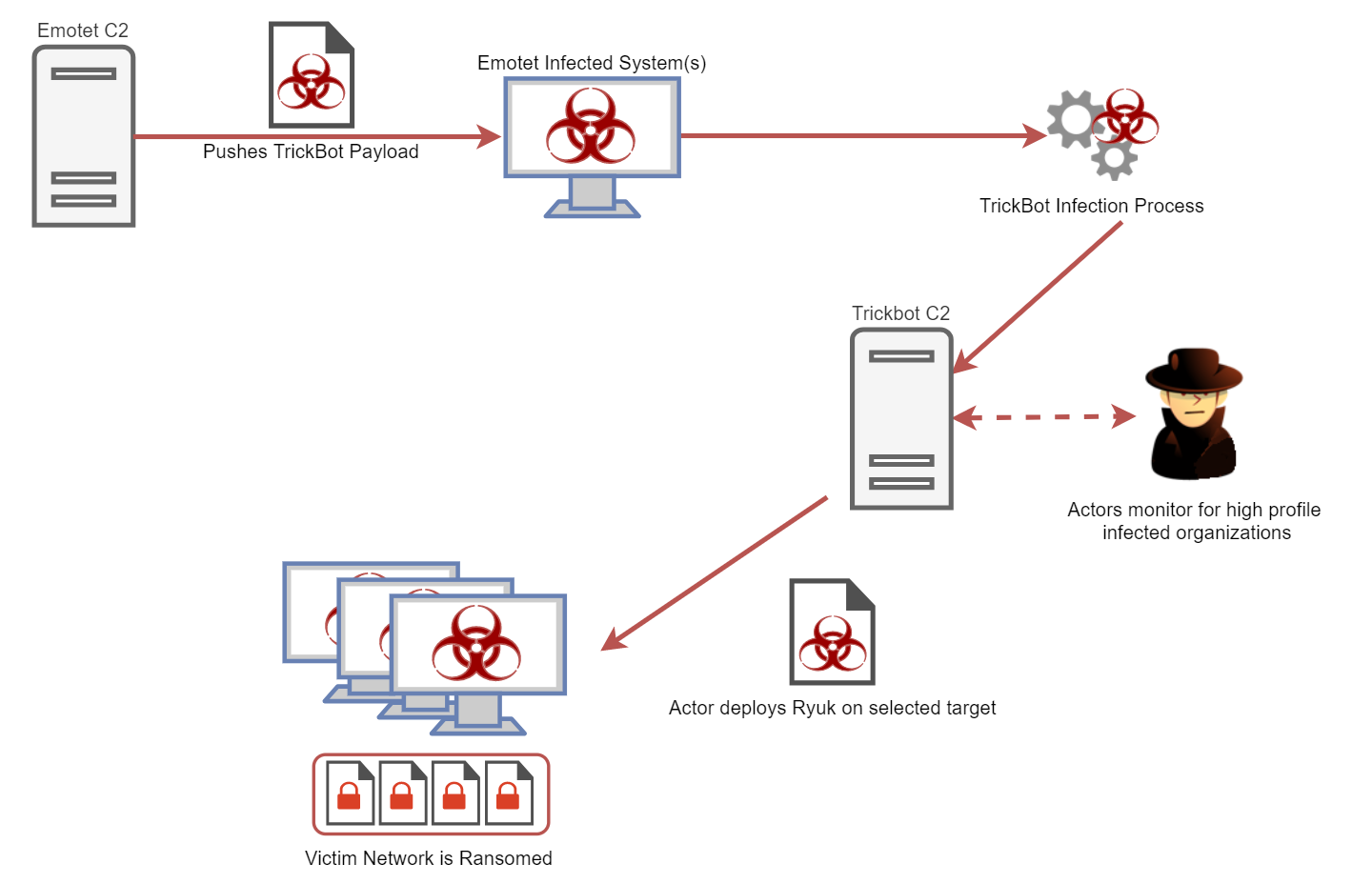
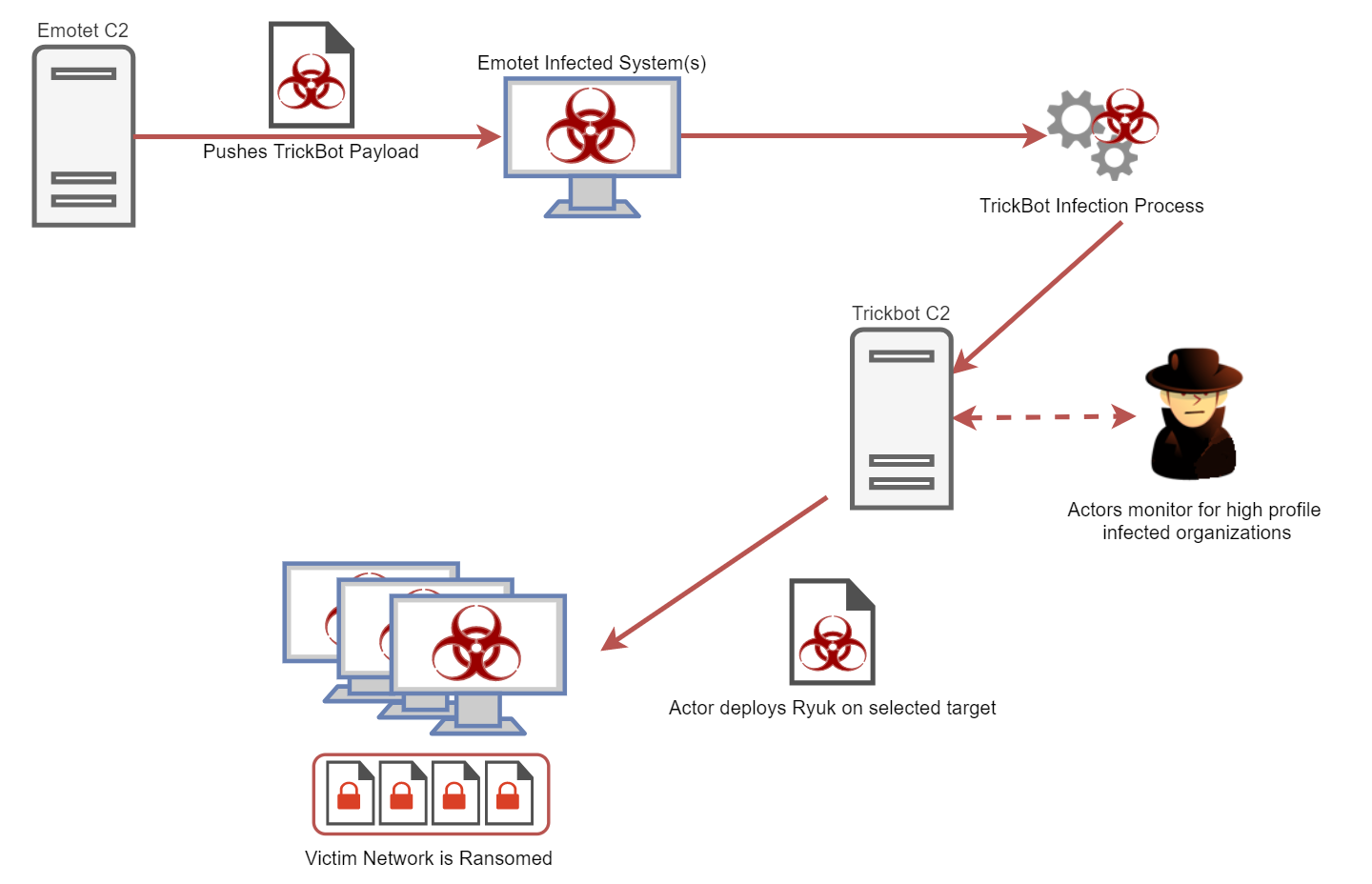
Flow of the attack as Emotet delivers TrickBot, which delivers Ryuk. Workflow chart originally created by the Kryptos Logic team for their blog on the same topic.
In this information stealing and ransoming malware research, we describe a campaign that incorporates Emotet, TrickBot, and the Ryuk ransomware. The Cybereason research team has observed this campaign across multiple customer environments since January of 2019. This malware adapts Emotet to drop TrickBot, and adapts TrickBot to not only steal data but also download the Ryuk ransomware. This attack is able to steal a significant amount of data including personal information, passwords, mail files, browser data, registry keys, and more, before encrypting the victim’s machine and ransoming their data.
Analyzing the Campaign
This attack begins with a weaponized Microsoft Office document attached to a phishing email. This file contains a malicious, macro-based code that runs and execute a PowerShell command. The PowerShell command attempts to download the Emotet payload from multiple different malicious domains.
Once Emotet has been executed, it continues its malicious activity by further infecting and gathering information on the affected machine. It also initiates the download and execution of the TrickBot trojan by communicating with and downloading from a remote C2 server.
When the Emotet payload executes, it looks to continue its malicious activity by further infecting and gathering information on the affected machine. It initiates the download and execution of the TrickBot trojan by communicating with and downloading from a pre-configured and remote malicious host.
When TrickBot executes, it creates an installation folder containing a copy of the malware, a settings.ini file, and a Data folder. settings.ini is an obfuscated file that contains an encoded BotKey. The Data folder contains TrickBot’s encrypted malicious modules and their configuration files. In order to ensure persistence, TrickBot creates a scheduled task and a service. To reduce the likelihood of being detected by an antimalware product, TrickBot also tries to disable and delete Windows Defender.
TrickBot’s malicious modules are reflectively injected into legitimate processes in order to evade detection. These modules include:
- module64.dll: the TrickBot dropper to improve lateral movement and give TrickBot persistence.
- module.dll: a module to steal data from the browser including cookies, HTML5 local storage, browsing history, Flash Local Shared Objects, and URL hits.
- vncsrv.dll: a module to allow an attacker to remotely view and control a victims desktop.
- socks5dll.dll: a module to tunnel data and connections through the victim’s host.
- systemInfo.dll: a module to determine if the affected machine can be infected with Ryuk ransomware.
- mailsearcher.dll: a module to search for and collect mail files on disk to send back to the C2 server.
- loader.dll: a module to ensure other modules are successfully loaded.
- pwgrab.dll: a module to harvest user credentials from browsers, registry keys, and other programs such as Outlook.
- core-dll.dll: this module is the main TrickBot bot which is reflectively injected into Internet Explorer, Firefox, Chrome, and Opera to steal credentials.
- dll.dll: a reverse-shell module that collects information about the target machine and launches a PowerShell Empire backdoor. It also looks for valuable assets in the organization like domain controllers, file servers, and other potential Ryuk ransomware targets.
- screenLocker_x64.dll: a module for reconnaissance and credential harvesting. It uses a component of mimikatz to extract credentials from the target system.
- spreader_x64.dll: a module that spreads TrickBot by exploiting EternalBlue and uses mimikatz to perform credential threat.
Once the machine is infected with TrickBot, it begins to steal sensitive information. Meanwhile, the attackers check to see if the target machine is part of an industry they are looking to target. If it is, they download the Ryuk ransomware payload and use the admin credentials stolen using TrickBot to perform lateral movement and reach the assets they wish to infect.
The ransomware dropper Ryuk.exe checks the system architecture and drops its main payload accordingly. The dropper also stops multiple services and processes related to antimalware products by using the netstop and taskkill commands. The main Ryuk payload injects itself into multiple processes and achieves persistence using the registry.
To ensure the victim is forced to pay to decrypt the valuable files, Ryuk changes the configuration of and deletes the Virtual Shadow Copy.
Ryuk then encrypts files on the disk, changes the extension to .RYK, and drops a ransom note RyukReadMe.txt created with notepad.exe in every processed folder.
Consequences of the Emotet, TrickBot, Ryuk Campaign
Once this malware has successfully infiltrated, it will collect personal data, passwords, mail files, browser data, registry keys, and more. This type of information can give the attacker access to personal and business bank accounts, personal or work-related email correspondence, personal and business data, and more. Getting access to this kind of data can have severe business consequences. If this attack occurs on a company laptop, the attacker could gain access to company R&D, financial information, trade secrets, user data, or other sensitive information. This can result in brand degradation, loss of individual reputation, or loss of consumer trust. To compound this attack, it also downloads and spreads the Ryuk ransomware. With Ryuk, the attacker is able to encrypt the machine and ransom data back to the victim. This has the potential to cost victims significant sums of money due to downtime, recovery costs, and damage to reputation.
conclusion
This campaign is an interesting combination of Emotet, TrickBot, and Ryuk that pose significant risk for victims. It shows how attackers are becoming more daring and opting to combine multiple types of malware to achieve maximum damage.
This research shows a change in trend, as well as how attackers are becoming more advanced with their attacks. This campaign combined Emotet, TrickBot, and Ryuk to not only steal sensitive information, but also ransom the victims data. These threats result in brand degradation, damage to an organization, and damage to the individual.
This campaign again originates from a phishing attack. The use of phishing to perpetrate a widespread attack continues to be a leading issue. This will continue to be an effective attack vector until we are able to prevent human manipulation in phishing attacks.
The Cybereason team found this campaign in multiple customer environments. The Cybereason Platform was able to detect the infection, and we provided customers with a full list of remediation steps, which they used to quickly remediate the issue before being affected by the ransomware.
Full research on the Emotet-TrickBot-Ryuk campaign can be found here.