Today, we are happy to announce that the Cybereason Defense Platform has been evaluated by MITRE ATT&CK to illustrate how we approach threat detection in the context of the MITRE ATT&CK framework. This open and transparent methodology for evaluating vendor capabilities seeks to educate and bolster the defender based on real threat actors. This deeply resonates with our vision to reverse the adversary advantage by empowering the defender, which is why Cybereason chose to participate for the second year in a row.
The MITRE ATT&CK evaluation further demonstrates Cybereason’s leading detection and response capabilities, even against the most advanced threat actors. Our close alignment to the MITRE ATT&CK framework is showcased in our platform to provide analysts with immediate context and a common language around which to communicate about attacks.
In this round of evaluations, vendors were tested against the tactics and techniques used by APT29, a group that security analysts widely believe operates on behalf of the Russian government and compromised the Democratic National Committee starting in 2015.
“We view the evaluations as a collaborative process to help the participating vendors improve their products, which ultimately makes cyberspace safer for everyone,” said Frank Duff, ATT&CK Evaluations lead. “Taken as a whole, the results indicate that the participating vendors are beginning to understand how to detect the advanced techniques used by groups like APT29, and develop products that provide actionable data in response for their users.”
MITRE developed and maintains ATT&CK based on open source reporting of adversary tactics and techniques. ATT&CK is freely available, and is widely used by defenders in industry and government to find gaps in visibility, defensive tools, and processes as they evaluate and select options to improve their network defense.
Cybereason’s results in the MITRE ATT&CK Round II evaluations showcase Cybereason’s superior visibility, real-time detection capabilities, and valuable contextual alerts.
Superior Visibility
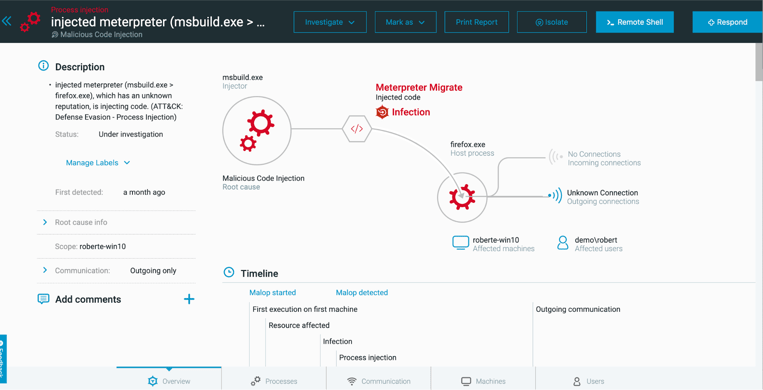
The Cybereason Defense Platform provides superior visibility with detailed context for every incident. Analysts can view the entire process tree with a complete timeline of events for all malicious activity across every machine and every process. Cybereason enables security teams to thoroughly see and stop attacks, even against advanced threat actors.
Real-time Detections
The Cybereason Defense Platform prioritizes real-time detections. Cybereason is powered by the Cybereason Cross-machine Correlation Engine, a dynamic data model that provides detailed, correlated, and enriched data from every endpoint in real time. This engine drives our impressive 1:150,000 endpoint to analyst ratio and low false positive rate, reducing the workload on security teams while raising their productivity.
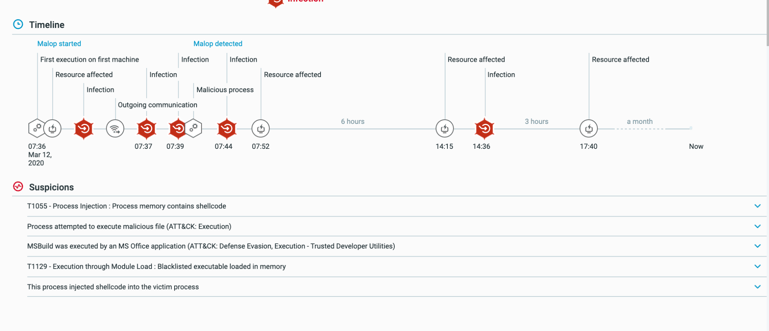
We provide defenders alerts with as much information as possible as quickly as possible to empower analysts to resolve incidents faster and more completely.
The Full Context of an Attack
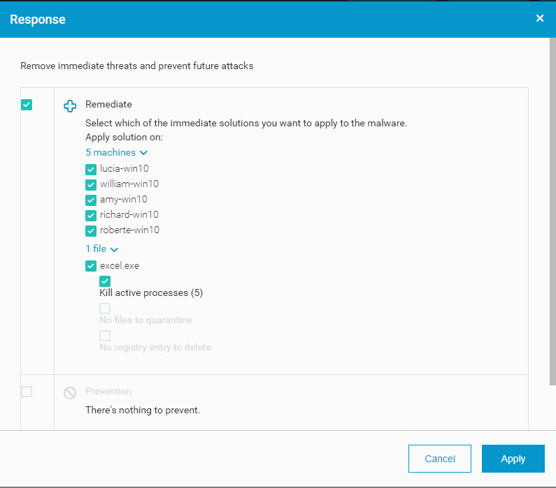
The Cybereason Malop gives security teams the full context of an incident across all affected machines and automatically pinpoints techniques at each stage of the kill chain. Upon receiving a Malop, analysts can quickly remediate in a single click, reducing mean time to remediate.
Closing Thoughts
The ability to publicly test the Cybereason Defense Platform against real-life attack scenarios is a rare opportunity, and we pride ourselves on having built our platform from the ground up with real-life attack scenarios in mind. We look forward to working with the MITRE ATT&CK team again for the third round of evaluations later this fall.
For more information about how we integrate MITRE ATT&CK into our security operations, read our white paper on Five Stages to a Closed-looped Security Process with MITRE ATT&CK.