We are excited to announce that Cybereason has been named a strong performer, with the highest score in the “current offering” category amongst 11 other vendors in The Forrester Wave™: Endpoint Detection & Response Q1 2020. We are proud of this achievement not only because of the hard work of our team, but also because we believe that it represents our continual commitment to deliver the innovation truly needed in this ever-changing threat landscape.
In this report, Forrester highlights three trends that security professionals should consider when evaluating EDR solutions, which we believe align with feedback from our customers about our EDR offering. Our takeaways from these three key trends:
Empower SOC analysts with incident-driven security analytics
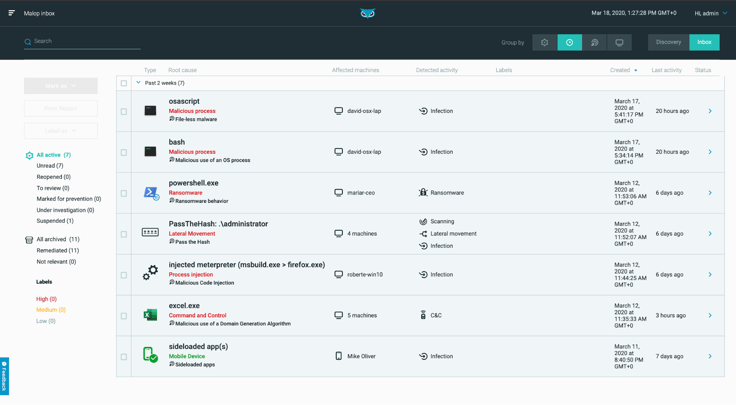
Forrester states that “the ability to leverage analytic capabilities for root-cause analysis of the events on a compromised system and associate related alerts into a single incident, potentially across the entire environment, reduces investigation time and alert volume”. One of the common challenges we often hear from the market is that analysts are overloaded with multiple disconnected alerts that result in misses and alert fatigue, only to become counterproductive. With Cybereason, analysts can easily see all related attack elements, including the root cause, all affected machines and users, incoming and outgoing communications, and a timeline of the attack. Cybereason tells the complete attack story, from detecting initial compromise and providing context for detections that are deliberately connected across the entire environment to empowering the SOC and helping eliminate analyst fatigue.
Provide A Prescriptive Remediation Plan and the ability to orchestrate
Forrester points out that “having a remediation plan that can be executed at the click of a button is part of a good EDR product’s value proposition”. At Cybereason, we agree that successfully detecting an attack is only half of the battle. When an attack is detected, it is equally important to quickly and efficiently stop it. Cybereason provides quick remediation options, including the ability to kill processes, quarantine files, remove persistence mechanisms, prevent file execution and isolate machines with a single click. An analyst can pivot directly from investigating an attack to remediating all affected machines with the single click of a button, saving time and creating a more efficient workstream for the entire team.
Facilitate advanced use cases for MITRE ATT&CK
Mapping alerts to the MITRE ATT&CK™ framework allows analysts to understand even the most complex detections at a glance, reducing the time required to triage alerts and accelerating prioritization and remediation. The Cybereason Defense Platform has proven our unique ability to deliver maximum ATT&CK coverage in real-time with unparalleled context. Every Cybereason alert is aligned to the MITRE ATT&CK framework and is able to showcase the entire kill chain within a single screen. Analysts can hunt against individual techniques, create custom detections based on ATT&CK attributions, and produce reports and recommendations for response.
As the Forrester report states, “Cybereason futureproofed their EDR product by architecting it with the vision of combining the detection analytics synonymous with the EDR market…” We at Cybereason are excited to lead the charge toward meeting enterprises’ security challenges with strong product capabilities and innovative analytics. The Cybereason Defense Platform not only helps our customers adopt best practices to address today's security problems, but also to address the emerging problems of tomorrow.
Download your complimentary copy of the “The Forrester Wave™: Endpoint Detection & Response, Q1 2020.”
Read the Report