The Hajime embedded devices worm was first written about in October. Researchers at Rapidity Networks setup honeypots hoping to capture a Mirai sample. Instead, they discovered an embedded devices worm that behaves like the Mirai but has no connection to the malware that turns IP cameras, printers and other devices running Linux into bots that can be used on large DDoS attacks. The platforms targeted by Hajime, according to Rapidity researchers, are ARMv5, ARMv7, Intel x86-64 and MIPS.
Cybereason Labs wants to build on that research by analyzing what we believe to be is a new Hajime variant that VessOnSecurity passed along to us. This new version includes code that changes iptables rules, allowing the attackers to get around firewalls while still maintaining a relatively stealthy packed ELF executable stripped from debug symbols.
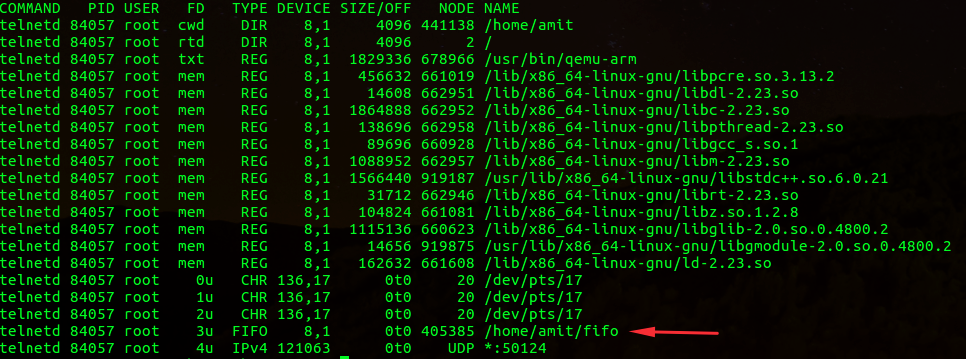
In our research, we saw that the variant also loads the iptables kernel module (if not already present) and then makes some changes to the iptables firewall. TCP ports 7547, 5555, and 5358 are dropped and a UDP port is accepted. The UDP port that’s accepted constantly changes (in one test UDP port 7042 was opened) and the same TCP ports are closed, according to our research. This variant of Hajime also creates a local ‘fifo’ pipe (using mknod) in its current working directory and calls it fifo.
To determine if your computer is infected with the new variant just look at the ports in your iptables filter output table. If the iptables rules we mentioned are changed, then your machine could be affected. Try looking for inconsistencies between running processes (by running “ps aux”) to their open file descriptors (by running “lsof -i”) and see if telnetd opens file descriptors to places it shouldn’t such as the aforementioned fifo pipe.

If these iptables rules are changed, then your computer could be infected.
Another interesting artifact that we saw is that there was an inconsistency between the name of the process that’s showing in “ps aux.” As you can see in the image below, it’s displayed as “telnetd” while in “ps aux” it’s still listed with its original name. This might be a side effect of executing that binary with usermode emulation.