Kia Motors America stated that a ransomware attack was not the apparent cause of an extended systems outage affecting the automobile dealer’s IT systems. It all started with an error message…
Kia Ransomware
According to Bleeping Computer, the outage started on February 13 when the Kia Owners Portal went offline and displayed the following error message:
We are currently experiencing an IT service outage that has impacted some internal networks. Our customers are our top priority, and we are working to resolve the issue quickly.
The Kia Owners Portal is a platform where owners of Kia automobiles can book an appointment with a dealer, store their insurance and/or registration information and more.
Bleeping Computer confirmed in its reporting that the outage affected the phone self-help services operated by Kia Motors America, a subsidiary of Kia Motors Corporation headquartered in Irvine, California. Those services informed callers that unspecified server issues might undermine the company’s ability to provide customer support.
The outage also affected customers’ ability to use the Kia Access with UVO Link, UVO eServices and Kia Connect mobile apps, the customer self-help website wrote. In a statement provided to Bleeping Computer, the automobile dealer did not provide any details about the cause of the outage:
KMA is aware of IT outages involving internal, dealer and customer-facing systems, including UVO. We apologize for any inconvenience to our customers and are working to resolve the issue and restore normal business operations as quickly as possible.
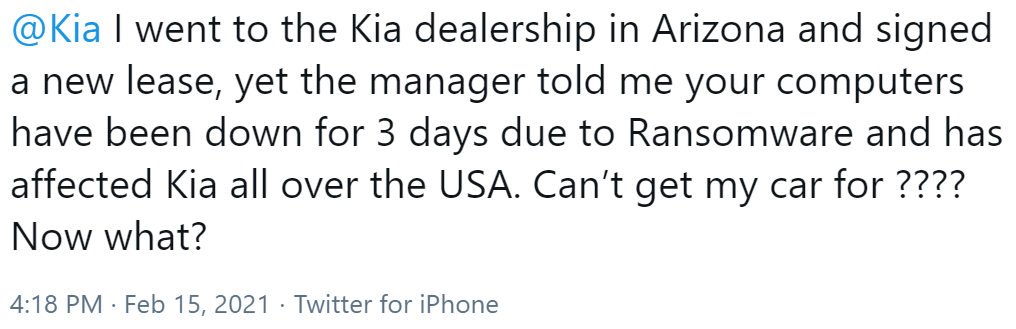
On February 16, however, a user tweeted out that they had attempted to pick up their car from one of the 800 dealerships operated by Kia Motors when a manager informed them that they couldn’t drive their car off the lot that day because a ransomware attack had knocked some of Kia’s computer systems offline:
The following day, Bleeping Computer received what appeared to be a ransom note from the DoppelPaymer ransomware group indicating that the gang had successfully attacked Hyundai Motor America, Kia’s parent company.
In their ransom message, the attackers asserted that they had stolen a “huge amount” of data from Kia Motors America and that they would release the data in 2-3 weeks unless the automobile dealer agreed to pay 404 BTC (worth more than $20 million at the time of reporting).
The nefarious individuals went on to say that they would raise the ransom demand to 600 BTC (a sum of more than $31 million) in the event that the company didn’t pay on time.
Notwithstanding that message, Kia Motors America told Bleeping Computer in a statement that it had found no evidence of a ransomware attack having affected its systems:
Kia Motors America, Inc. (“Kia”) is currently experiencing an extended systems outage. Affected systems include the Kia Owners Portal, UVO Mobile Apps, and the Consumer Affairs Web portal. We apologize for any inconvenience to affected customers, and are working to resolve the issue as quickly as possible with minimal interruption to our business. We are also aware of online speculation that Kia is subject to a “ransomware” attack. At this time, we can confirm that we have no evidence that Kia or any Kia data is subject to a “ransomware” attack.
The computer self-help website later learned that the outages had affected Hyundai Motors America including its internal dealer site, hyundaidealer.com, among some of its other systems. Even so, Hyundai Motors America also told Bleeping Computer that there was “no evidence of Hyundai Motor America’s involvement in a ‘ransomware’ attack."
The Need for Transparency in the Face of Ransomware
Sam Curry, chief security officer at Cybereason, put the potential impact of the reported attack and the outage affecting Kia Motors America into perspective:
“The devastating ransomware attack that has taken Kia Motors’ operations down to its knees is just the latest example of a financial cybercrime being perpetrated against a large company,” Curry said. “Every minute that their operations are incapacitated costs companies millions of dollars in lost business.”
In response to a security incident like a ransomware attack, some companies might be inclined to draw inward and to not offer many details to the public. They might think that they’re protecting their reputation from additional damage in doing so. But they’re actually leaving countless other organizations vulnerable to the same threat actors, according to Curry.
“It cannot be understated how important it is for companies like Kia to be open and transparent about the specific facts surrounding a cyberattack,” Curry explained. “Our industry can then quickly dissect the nature of the attack and prevent this type of system intrusion from happening to other companies. This cat-and-mouse game will only continue until we can preemptively deploy solutions that can stop it cold.”
Not all solutions provide adequate levels of defense, however. Indeed, tools that rely on Indicators of Compromise (IOCs) are ineffective against ransomware gangs like DoppelPaymer that are constantly coming up with new ways to target organizations. That’s why organizations need solutions that focus instead on Indicators of Behavior (IOBs) as a means of surfacing never before seen attacks earlier in order to remediate faster—even if an attack is completely unique to the target’s systems and no IOCs are available to leverage in defense.
Learn how Cybereason can help your organization defend against ransomware attacks, and access more ransomware resources here.
ABOUT DAVID BISSON
 David Bisson is an information security writer and security junkie. He's a contributing editor to IBM's Security Intelligence and Tripwire's The State of Security Blog, and he's a contributing writer for Bora.
David Bisson is an information security writer and security junkie. He's a contributing editor to IBM's Security Intelligence and Tripwire's The State of Security Blog, and he's a contributing writer for Bora.
He also regularly produces written content for Zix and a number of other companies in the digital security space.





 David Bisson is an information security writer and security junkie. He's a contributing editor to IBM's Security Intelligence and Tripwire's The State of Security Blog, and he's a contributing writer for Bora.
David Bisson is an information security writer and security junkie. He's a contributing editor to IBM's Security Intelligence and Tripwire's The State of Security Blog, and he's a contributing writer for Bora.
