Cybereason Security Services issue Threat Analysis reports to inform on impacting threats. The Threat Analysis reports investigate these threats and provide practical recommendations for protecting against them.
In this Threat Analysis report, Cybereason Security Services investigates HardBit Ransomware version 4.0, a new version observed in the wild.
KEY POINTS
- Binary Obfuscation Enhancement: Unlike previous versions, HardBit Ransomware group enhanced the version 4.0 with passphrase protection. The passphrase needs to be provided during the runtime in order for the ransomware to be executed properly. Additional obfuscation hinders security researchers from analyzing the malware.
- HardBit Binary Comes In Two Flavors: HardBit Ransomware group provides operators with CLI or GUI versions of the ransomware. Providing choices likely allows the group to expand their market to different skill sets of operators. Depending on the technical skill level of the operator, GUI is more intuitive on what and how it can be executed.
- Common Delivery And Obfuscation Method: Like with other Ransomware, Neshta is responsible for delivering HardBit. The HardBit ransomware itself is a .NET binary, obfuscated by a packer named Ryan-_-Borland_Protector Cracked v1.0, and it is likely a modified version of Open Source .NET packer ConfuserEx. The packer has been around for several years and utilized by various .NET malwares such as RedLine Infostealer.
INTRODUCTION | What is Hardbit?
HardBit Ransomware has rapidly evolved its arsenal in the past few years. The ransomware group emerged back in 2022, and the versions have been updated to 4.0 at the time of this writing. Like many ransomware groups, the goal is financial gain via extortion and many of the TTPs introduced in this analysis overlap with different ransomware operators. However, the group’s communications methods, as well as their tools, differentiate them from well known ransomware groups.
HardBit Ransomware Group
HardBit Ransomware emerged in October 2022 and unlike other ransomware groups, they do not appear to have leak sites and hence do not resort to typical double extortion methods. HardBit Ransomware group’s main tactics are as follows:
- Stealing and encrypting victims’ data, then demanding ransom payment
- Threatening and conducting additional attacks against the victim if the ransom demand is not met
The group’s primary communication method is via peer-to-peer instant messaging system, TOX, with the ransom note providing the TOX ID.
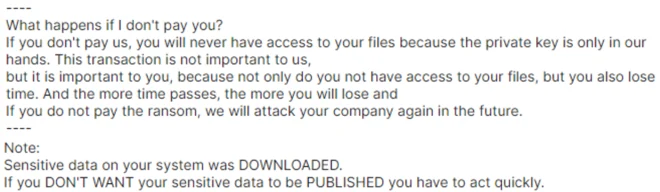
Hardbit Ransom Note Snippet
HardBit Ransomware group’s method of initial infection is not well known. Although, the methodologies are likely similar to that of other ransomware groups, which this report details in a later section. The group shares similarities with LockBit Ransomware, such as:
- Group Name
- Group Image/Icons
- Image Fonts
- Ransom Notes
Although relations between HardBit Ransomware and LockBit Ransomware are unknown, it is evident that the group is inspired by LockBit. These similarities may be part of the “marketing” tactics utilized by the group to conduct imitation of more well-known ransomware actors.
TECHNICAL ANALYSIS
Cybereason divides this section into two subsections.
- Observed TTPs (Tactics, Techniques and Procedures): highlights TTPs utilized by HardBit Ransomware operators
- Malware Analysis: covers malware analysis for binaries related to HardBit Ransomware
Observed TTPs | Initial Access
While the initial attack vector remains unconfirmed at the time of this writing, Cybereason hypothesizes that the threat actors gain an initial foothold into the victim’s environment through brute force of an open RDP and SMB service. In fact, the environment observed multiple login failures from known brute forcing IP addresses.
SMB Session Authentication Failure
Client Name: \\{ATTACKER_IP_ADDRESS}
Client Address: {ATTACKER_IP_ADDRESS}
User Name:
Session ID: 659798714482733
Status: 3221225581 (3221225581)
SPN: session setup failed before the SPN could be queried
SPN Validation Policy: 0
Example SMB Session Authentication Failure
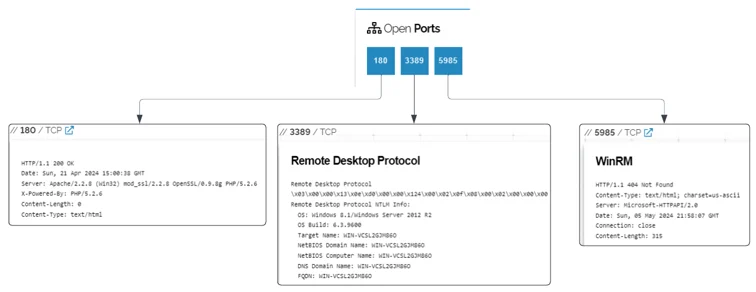
Open Ports Detected On The Brute Forcing Server
Credential Access
Threat actors prepared for Lateral Movement by conducting credential theft via Windows credential dumping tool Mimikatz and RDP brute forcing tool NLBrute. Threat actors first deployed their own BAT script via a zip file named 111.zip, which contained BAT script !start.bat and Mimikatz binaries. Mimikatz, being an OS credential dumping tool, gets executed via !start.bat and dumps the output into file Result.txt. This output file gets parsed and prettified by miparser.vbs.
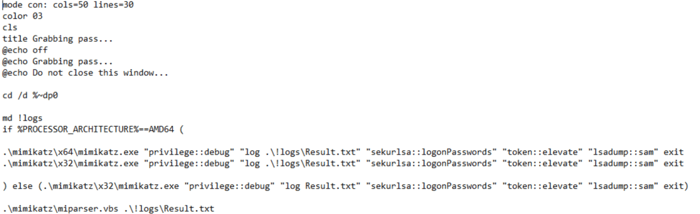
Snippet Of !start.bat File
Cybereason has observed this script various times in the past by different ransomware operators. Aside from Mimikatz, the script attempts to execute two additional tools to conduct credential theft.
- LaZagne: Open source password recovery tool. Supports Linux, Windows, and OSX.
- NirSoft: Freeware utilities for Windows. The tool consists of various password recovery tools via browser or client applications.
Although NirSoft and LaZagne execution is supported, HardBit did not deploy and utilize these two tools.
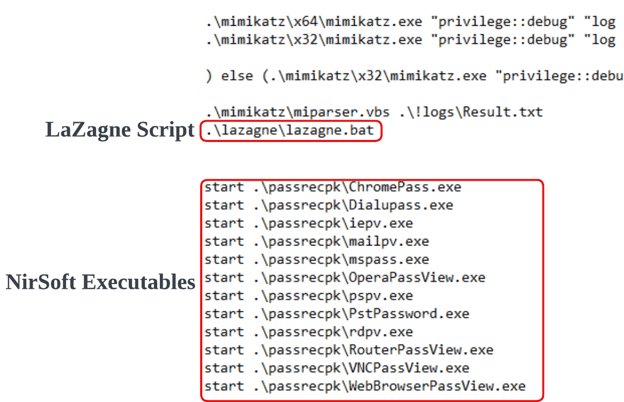
Snippet Of !start.bat For LaZagne And NirSoft Execution
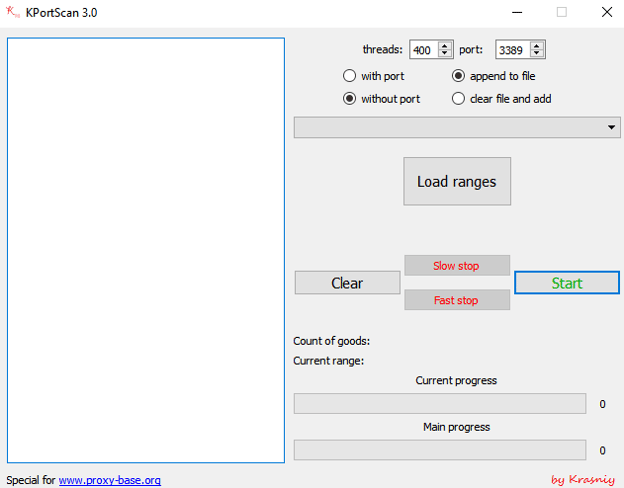
The Threat Actors also utilized NLBrute, an RDP brute forcing tool that first appeared in 2016. Threat actors visited picofile[.]com, a Farsi language file sharing site, via browser to download NLBrute. Different ransomware operators in the past have also abused this site to deliver their tools such as KPortScan 3.0, which has also been seen used by HardBit ransomware during incidents.
Discovery
In support of Lateral Movement, the threat actors retrieved Network Discovery tools from the Internet. Specifically, threat actors were observed retrieving three network scanning tools.
Threat actors were specifically spotted accessing the downloading sites of these tools via browsers. Similar to NLBrute, KPortScan 3.0 is a popular port scanning tool utilized by ransomware operators. Threat actors visited different sites to download the port scanning tools by doing simple browser search with search queries such as “advance port scanner” and “kportscan picofile”. Threat actors' use of KPortScan 3.0 in combination with NLBrute indicate focused effort on RDP discovery.
Source: https://thedfirreport.com/2021/11/15/exchange-exploit-leads-to-domain-wide-ransomware
Threat actors also brought 5-NS new.exe, which is a malicious network shares scanning tool. The tool appears to be employed by various ransomware operators in the past such as Dharma Ransomware, LockBit Ransomware, and Phobos Ransomware.
 NS-5 new.exe Execution Snippet Observed In VirusTotal
NS-5 new.exe Execution Snippet Observed In VirusTotal
Lateral Movement
Equipped with harvested credentials and a list of relevant target machines, the Threat Actors leverage RDP to move laterally within the victim’s corporate network. This method was observed to identify and infect as many machines as possible within a victim’s corporate environment.
Collection / Data Exfiltration
Precise collection and data exfiltration methods have yet to be identified.
Impact
Ransomware operators deploy HardBit packed Neshta onto infected machines to conduct encryption of the machines. HardBit ransomware deploys four files onto the machines including the ransomware binary itself. The details of the files are discussed in the HardBit 4.0 Analysis section.
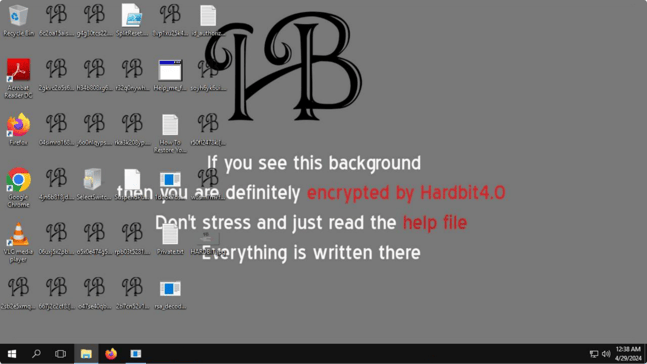
HardBit Ransomware Encrypting The Target Machine
Malware Analysis | Neshta
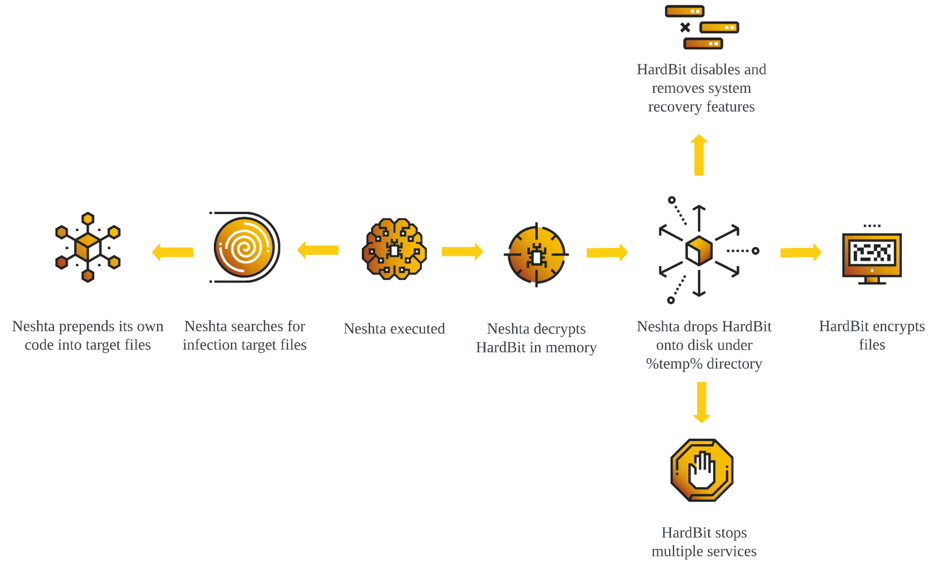
HardBit Packed Neshta Execution Flow
Neshta is a virus known to be active since 2003. The virus’ main role is to infect legitimate files and maintain persistence within the infected machines. Within recent years, threat actors started to utilize the virus as a dropper and deploy secondary malware, especially ransomware. In this variant, Neshta contains a packed HardBit binary which gets dropped to the %TEMP% directory during the execution.
Execute HardBit
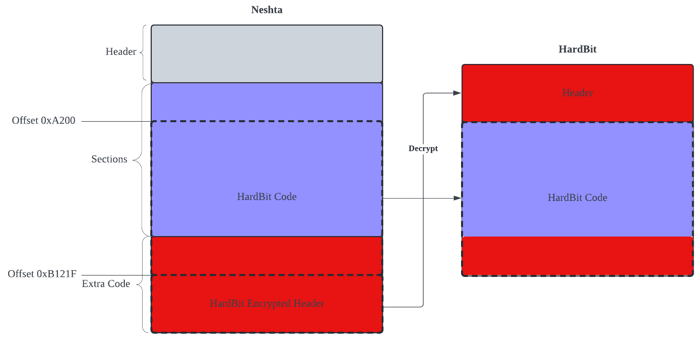
Neshta Dropping HardBit
Neshta takes the following steps to make preparations to dump HardBit Ransomware binary onto disk.
- Opens Neshta binary file with CreateFileA
- Reads offset 0xB121F of Neshta binary file with length of 41 KB (0xA200) by utilizing combinations of SetFilePointer and ReadFile
- Decrypts read data from offset 0xB121F, which is a header of the HardBit binary
- Writes a decrypted offset 0xB121F onto HardBit binary by WriteFile
- Reads another offset 0xA200 with length of 684 KB (0xA701F) by utilizing combinations of SetFilePointer and ReadFile.
- Appends offset 0xA200 to HardBit binary
The observed version of Neshta dumps the HardBit Ransomware binary onto the %TEMP% directory with the same filename as the original Neshta binary. Once the dumping of HardBit Ransomware is complete, Neshta proceeds to execute HardBit Ransomware via ShellExecuteA.
Post Dump Of Ransomware
Aside from dumping the HardBit binary, the main functionalities of Neshta have not changed. Prior to infecting the legitimate files, Neshta proceeds to create persistence mechanism by copying itself as svchost.com to the %SYSTEMROOT% and updates registry key HKLM\SOFTWARE\Classes\exefile\shell\open\command to run copied svchost.com every time the executable is launched. Neshta also proceeds to create a mutex with name starting with MutexPolesskayaGlush*.*<0x90>svchost.com to prevent the duplicate execution.
The execution flow enters the infection phase of the files. Neshta conducts the following steps during this phase.
- Opens and reads target file’s header from offset 0x0 to 0xA200
- Encrypts the header from the target file
- Reads Neshta header allocated in BSS section at runtime at offset 0x0xA698
- Replaces target file’s header with Neshta header from BSS section
- Appends the rest of legitimate code as well as encrypted header
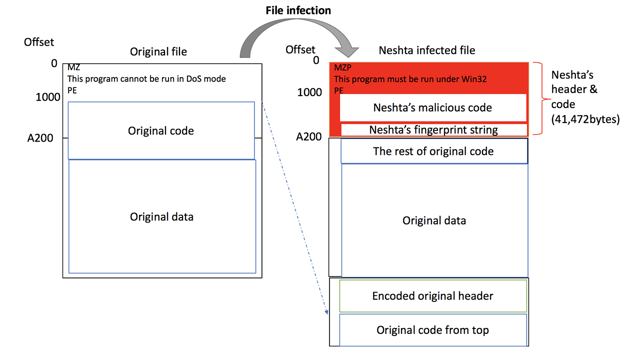
Source: https://blogs.blackberry.com/en/2019/10/threat-spotlight-neshta-file-infector-endures
Neshta targets executable under any of the following directories.
HardBit 4.0 Analysis | Execution Overview
HardBit appears to provide two different versions of the tool, CLI and GUI versions. Threat actors provide the following files in order to allow operators to conduct their attack.
|
File Type
|
Summary
|
|
Authorization ID text file
|
Authorization ID provided by the HardBit binary
|
|
Configuration File ※
|
Optional HardBit configuration file.
|
|
HardBit CLI binary
|
CLI binary for HardBit 4.0
|
|
HardBit GUI binary
|
GUI binary for HardBit 4.0
|
|
Private Key text file
|
Private Key used to decode the Authorization ID
|
|
RSA decoder binary
|
Tool to decode authorization id with provided Private Key.
|
※ HardBit binary does not require this file and Cybereason did not observe this file in observed incident.
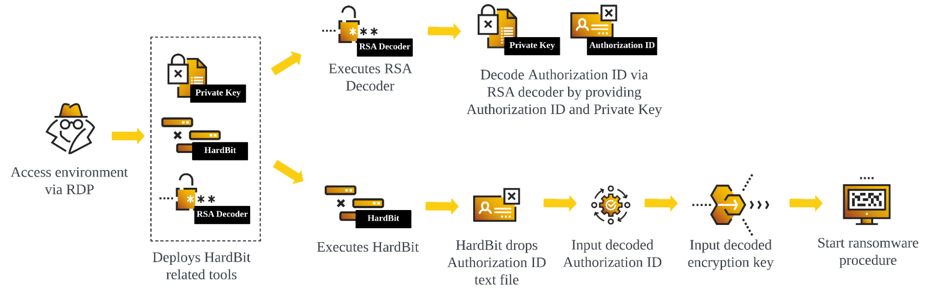
HardBit Ransomware Execution Procedure
Threat actors have a choice to choose between the CLI and the GUI version of the HardBit. In order to execute the binary, threat actors need to provide a decoded authorization ID. The authorization ID can be retrieved by decoding the encoded authorization ID within the id_authorization.txt with private key within Private.txt. Unlike the rest of the files listed in the table where it is likely brought by the attacker, id_authorization.txt gets dumped on the same execution path as the HardBit binary. Both CLI and GUI versions of HardBit binary dumps id_authorization.txt at runtime, getting updated every execution. To ease the decoding process, HardBit Ransomware group provides the GUI to decode authorization ID.
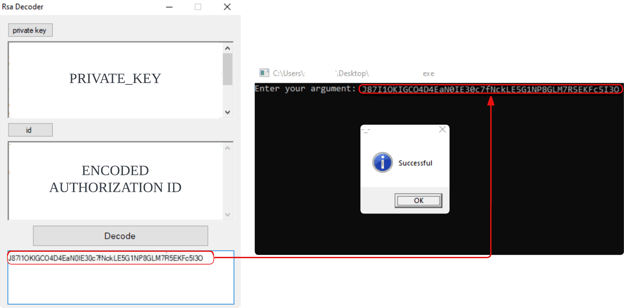
Inputting Decoded Authorization ID Into CLI Version Of HardBit
Once threat actors successfully input the decoded authorization ID, HardBit prompts for an encryption key to encrypt the files on the target machines and it proceeds with Ransomware procedure.
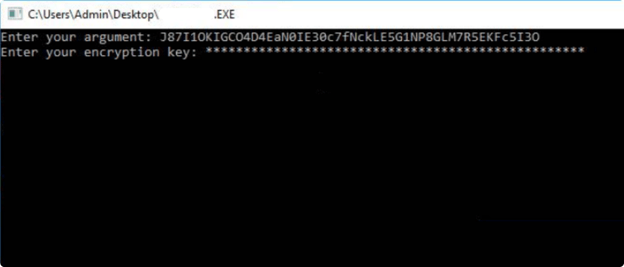
Inputting Encryption Key Into CLI Version Of HardBit
The GUI version of HardBit is also the same, requiring both decoded Authorization ID and encryption key.
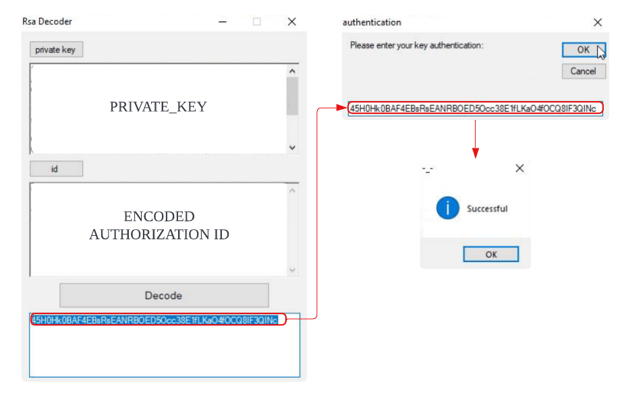
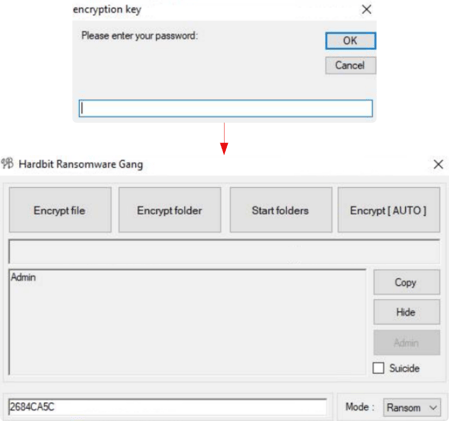
Inputting Decoded Authorization ID And Encryption Key Into GUI version Of HardBit Prompt
It is worth noting that all the binaries are packed by Neshta, including RSA Decoder binary. This implies every binary that gets executed has the same deployment activity mentioned in the Neshta section.
Disable Windows Defender
HardBit contains features to disable Windows Defender by updating the registry. The observed behaviors are as follows.
|
Registry
|
Summary
|
|
HKLM\SOFTWARE\WOW6432Node\Microsoft\Windows Defender\Features\TamperProtection
|
HardBit disables Tampering Protection by updating this registry
|
|
HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\DisableAntiSpyware
|
HardBit disables Anti-Spyware feature by updating this registry
|
|
HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection\DisableBehaviorMonitoring
|
HardBit disables Real-Time monitoring feature by updating three registries, including this registry
|
|
HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection\DisableOnAccessProtection
|
HardBit disables Real-Time monitoring feature by updating three registries, including this registry
|
|
HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection\DisableScanOnRealtimeEnable
|
HardBit disables Real-Time monitoring feature by updating three registries, including this registry
|
Once the ransomware completes the registry update, it checks the configuration via powershell Get-MpPreference -verbose command.
Ransomware also executes PowerShell’s Set-MpPreference to disable Windows Defender. The execution consists of following command-line parameters.
|
Parameter
|
Summary
|
|
DisableArchiveScanning
|
Disable scan against archive files.
|
|
DisableBehaviorMonitoring
|
Disables behavior monitoring.
|
|
DisableBlockAtFirstSeen
|
Disables block at first seen.
|
|
DisableIntrusionPreventionSystem
|
Disables a protection feature against exploitation of known vulnerabilities.
|
|
DisableIOAVProtection
|
Disables scanning of files.
|
|
DisablePrivacyMode
|
Disable privacy mode.
|
|
DisableRealtimeMonitoring
|
Disables real-time monitoring.
|
|
DisableScriptScanning
|
Disable the scan against scripts during the malware scans.
|
|
HighThreatDefaultAction
|
Specifies automatic remediation action to take for a high level threat, and in this it will not take any remediation action and allow its execution.
|
|
LowThreatDefaultAction
|
Specifies automatic remediation action to take for a low level threat, and in this it will not take any remediation action and allow its execution.
|
|
MAPSReporting
|
Specifies the type of membership in Microsoft Active Protection Service. The setup is made to not send any information to Microsoft.
|
|
ModerateThreatDefaultAction
|
Specifies automatic remediation action to take for a moderate level threat, and in this it will not take any remediation action and allow its execution.
|
|
SevereThreatDefaultAction
|
Specifies automatic remediation action to take for a severe level threat, and in this it will not take any remediation action and allow its execution.
|
|
SignatureDisableUpdateOnStartupWithoutEngine
|
Disables definition updates on startup when set to true.
|
|
SubmitSamplesConsent
|
Specifies user consents on submitting certain samples. The setup is made to not ever send the samples.
|
Service Stop
Like other ransomware groups, HardBit also stops multiple services prior to encrypting the target machine to ensure the successful execution. The ransomware stops the service via net.exe stop {service_name} /y, which is spawned as a child process. Refer to APPENDIX for a list of targeted services.
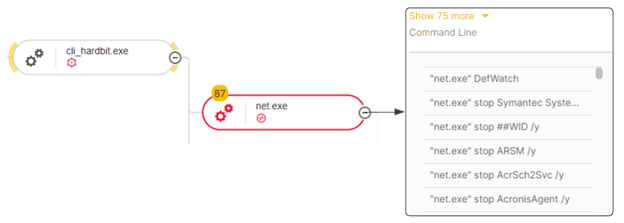
Attack Tree Of HardBit Ransomware
Inhibit System Recovery
HardBit Ransomware relies on BCDEdit, Vssadmin, WBAdmin, and WMIC to inhibit system recovery, which are common techniques amongst other ransomware groups. The observed command-line activity is as follows:
- bcdedit /set {default} bootstatuspolicy ignoreallfailures
- bcdedit /set {default} recoveryenabled no
- vssadmin delete shadows /all /quiet
- wbadmin delete catalog -quiet
Threat actors aim to delete shadow copy and backup catalogs via Vssadmin, WBAdmin, and WMIC. Once the deletion is complete, the execution flow proceeds to enable a boot configuration to ignore any failures and disable recovery option via BCDEdit. These configurations are set to ensure users can start the machine during any critical error after potential reboot of the machine due to encryption of the files and to prevent users from restoring the system.
Data Encryption
Once the necessary preparations are complete, the ransomware proceeds to encrypt target files. Similar to other ransomware, HardBit has its own exclusion list of files that are not the target of encryptions.
During the encryption process, HardBit conducts following updates on the infected machines, aside from encrypting the files.
- Update icons of infected files
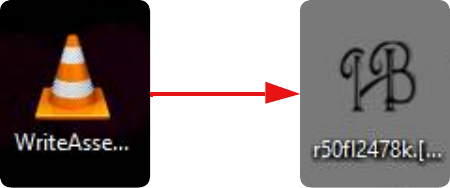
Updated Icons

HardBit Wallpaper
- Update VolumeLabel with string “Locked by HardBit”.

Updated Volume Label
- Dump message files Help_me_for_Decrypt.hta and How To Restore Your Files.txt. HardBit executes Help_me_for_Decrypt.hta and shows the message on the machine. The message contains contact information of hisenberg0gerATtutanota[.]com and hisenberg01gerATskiff[.]com.
 Snippet Of Help_me_for_Decrypt.hta
Snippet Of Help_me_for_Decrypt.hta
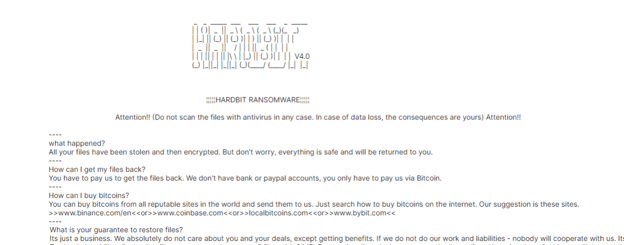
Snippet Of How To Restore Your Files.txt
The contact information appears to be the same with one of HardBit 3.0 variants and threat actors are utilizing end-to-end encrypted emails Skiff and Tuta.
Obfuscation
The binary appears to be obfuscated with Ryan-_-Borland_Protector Cracked v1.0, assumed to be a modified version of ConfuserEx, open source .NET obfuscator.
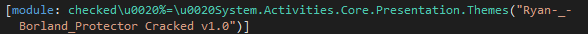
Ryan-_-Borland_Protector Cracked v1.0
Ryan-_-Borland_Protector Cracked v1.0 has been utilized by various .NET tools and malware in the wild, such as Redline Infostealer and Cyborg Ransomware as part of the obfuscation method.
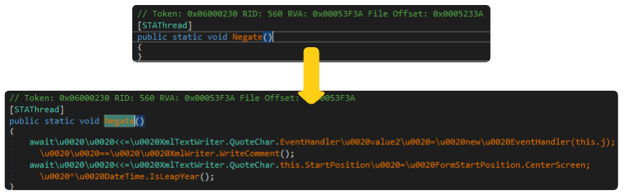
Unpacking Of HardBit Binary’s Entry Point
Ryan-_-Borland_Protector Cracked v1.0 conducts packing of the .NET binary as well as code obfuscation. Aside from ConfuserEx, obfuscator also consists of several different .NET obfuscation libraries such as DNGuard, Babel Obfuscator and Yano.
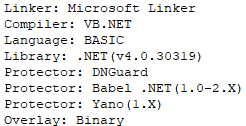
Observed .NET Obfuscation Libraries In HardBit Ransomware Binary
HardBit ransomware group started to utilize Ryan-_-Borland_Protector Cracked v1.0 from version 2.0.
Ransomware Mode
The CLI and GUI functionality are mostly the same, where GUI has more control over the execution flow of the ransomware, whereas CLI is in one execution chain. However, unlike the CLI, GUI supports different ransomware modes ransom and wiper. As the name suggests, ransom mode is to encrypt the files and wiper mode is to remove the files, resulting in wiping of the disk. Wiper mode feature needs to be enabled by the HardBit Ransomware group and the feature is likely an additional feature that operators need to purchase. If the operators need wiper mode, the operator would need to deploy hard.txt, an optional configuration file of HardBit binary and contains authorization ID to enable wiper mode.
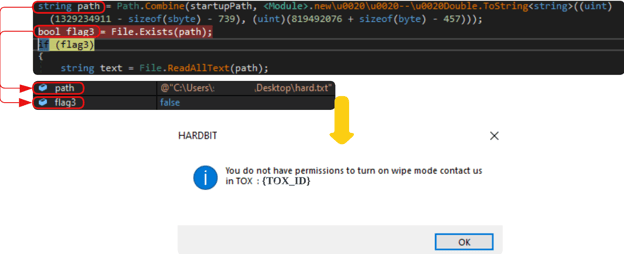
Prompt Stating Wiper Mode Is Not Supported
Operators can toggle wiper mode through the dropdown on the bottom right section of the HardBit GUI version.
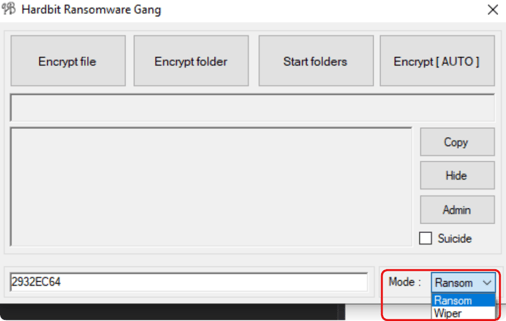
Ransomware Mode Dropdown in GUI Version Of HardBit
Once switched to wiper mode, the GUI changes all the options into wiper related actions instead of encryption. As the name suggests in each button, each activity results in wiping the disk in granular fashion.
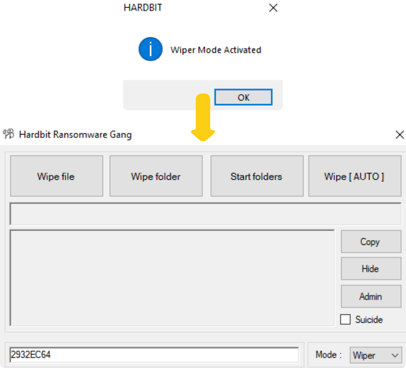
Wiper Mode Enabled In GUI Version
The GUI version also appears to have been available since version 3.0, including Wiper mode as well.
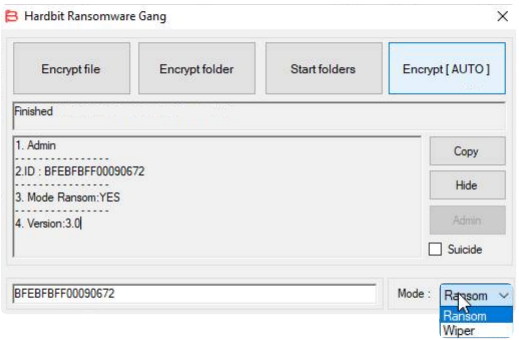
HardBit Ransomware Version 3.0 GUI
Configuration File
HardBit checks for an external configuration file hard.txt during the runtime. The file contains different configuration parameters that are relevant during the execution. The configuration checks may differ depending on the CLI or GUI version of the binary.
CLI:
GUI:
One case evaluated by Cybereason did not contain the configuration file hard.txt and the behavior of configuration parameters for CLI are unknown. However, the GUI’s configuration appears to be a flag responsible for turning on wiper mode.
Comparative Analysis
This section covers comparative analysis between HardBit Ransomware versions 2.0, 3.0 and 4.0. Aside from version 4.0, the rest of the versions are obtained from via OSINT or shared by the InfoSec community.
|
Tactics
|
HardBit 2.0
|
HardBit 3.0
|
HardBit 4.0
|
|
Disable Windows Defender
|
✔
|
✔
|
✔
|
|
Inhibit System Recovery
|
✔
|
✔
|
✔
|
|
Packed by Neshta
|
|
|
✔
|
|
Password protected
|
|
|
✔
|
|
Stop services
|
✔
|
✔
|
✔
|
|
Support HardBit GUI version
|
|
✔
|
✔
|
|
Support wiper mode
|
|
✔
|
✔
|
|
Use configuration file hard.txt
|
|
✔
|
✔
|
|
Use Ryan-_-Borland_Protector Cracked v1.0 packer
|
✔
|
✔
|
✔
|
Detection And Prevention of the HardBit Ransomware
Cybereason Defense Platform
The Cybereason Defense Platform is able to detect and prevent infections with HardBit Ransomware using multi-layer protection that detects and blocks malware with threat intelligence, machine learning, anti-ransomware, Next-Gen Antivirus (NGAV) and Variant Payload Prevention capabilities:
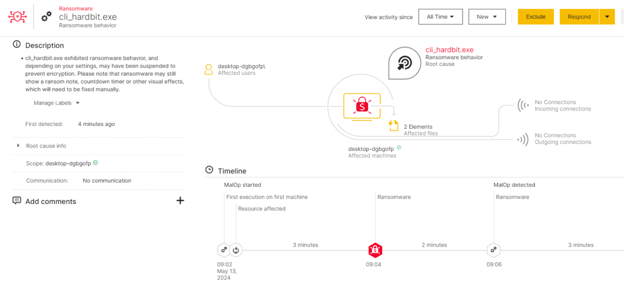
The Cybereason Defense Platform Creates MalOp Based On Ransomware Behavior
Cybereason
Cybereason recommends the following actions in the Cybereason Defense Platform:
- Enable Application Control to block the execution of malicious files.
- Enable Predictive Ransomware Protection in your environment’s policies, set the Predictive Ransomware Protection to Prevent or Quarantine with sensitivity level of Recommended.
※ Not recommended for high load servers. Use legacy Anti-Ransomware instead.
- If Predictive Ransomware Protection is not available, enable Anti-Ransomware in your environment’s policies. Set the Anti-Ransomware mode to Prevent, and enable Shadow Copy detection to ensure maximum protection against ransomware.
- Enable Variant Payload Prevention with prevent mode on Cybereason Behavioral execution prevention.
Cybereason is dedicated to teaming with Defenders to end cyber attacks from endpoints to the enterprise to everywhere. Learn more about Cybereason XDR powered by Google Chronicle as well as Cybereason SDR, check out our Extended Detection and Response (XDR) Toolkit, or schedule a demo today to learn how your organization can benefit from an operation-centric approach to security.
MITRE ATT&CK MAPPING
|
Tactic
|
Techniques / Sub-Techniques
|
Summary
|
|
TA0002: Execution
|
T1047 – Windows Management Instrumentation
|
HardBit Ransomware inhibits system recovery by deleting backup catalogs via WMIC
|
|
TA0002: Execution
|
T1059.001 – Command and Scripting Interpreter: PowerShell
|
HardBit Ransomware spawns PowerShell to disable Windows Defender
|
|
TA0002: Execution
|
T1059.003 – Command and Scripting Interpreter: Windows Command Shell
|
HardBit Ransomware spawns CMD to disable recovery options via BCEdit
|
|
TA0005: Defense Evasion
|
T1140 – Deobfuscate/Decode Files or Information
|
HardBit Ransomware binary and the binary itself is packed with a .NET obfuscator Ryan-_-Borland_Protector Cracked v1.0, which is deobfuscated during the runtime
|
|
TA0005: Defense Evasion
|
T1027.002 – Obfuscated File or Information: Software Packing
|
Neshta packs HardBit Ransomware binary and the binary itself is packed with a .NET obfuscator Ryan-_-Borland_Protector Cracked v1.0
|
|
TA0005: Defense Evasion
|
T1562.001 – Impair Defenses: Disable or Modify Tools
|
HardBit Ransomware disables Windows Defender to ensure in successful encryption
|
|
TA0006: Credential Access
|
T1003.001 – OS Credential Dumping: LSASS Memory
|
HardBit Ransomware operators utilizes BAT script responsible for running Mimikatz to conduct credential dumping
|
|
TA0006: Credential Access
|
T1110 – Brute Force
|
HardBit Ransomware operators utilized NLBrute to conduct RDP brute force attack
|
|
TA0007: Credential Access
|
T1046 – Network Service Discovery
|
HardBit Ransomware operators utilized Advanced Port Scanner and KPortScan 3.0 to conduct network discovery within the corporate network
|
|
TA0008: Lateral Movement
|
T1021.001 - Remote Service: Remote Desktop Protocol
|
HardBit Ransomware operators abuses RDP to conduct lateral movements
|
|
TA0040: Impact
|
T1485 – Data Destruction
|
HardBit Ransomware GUI version supports wiper mode, which wipes the disk instead of encrypting the files
|
|
TA0040: Impact
|
T1486 – Data Encrypted for Impact
|
HardBit Ransomware by default encrypts the target machines
|
|
TA0040: Impact
|
T1489 – Service Stop
|
HardBit Ransomware abuses net.exe to stop the relevant services to ensure in successful encryption
|
|
TA0040: Impact
|
T1490 – Inhibit System Recovery
|
HardBit Ransomware inhibits system recovery by by deleting shadow copy and backup catalogs, as well as disabling recovery options via BCDEdit, Vssadmin, WBAdmin, and WMIC
|
About The Researchers
 Kotaro Ogino, CTI Analyst
Kotaro Ogino, CTI Analyst
Kotaro is a CTI Analyst with the Cybereason Security Operations team. He is involved in threat hunting, threat intelligence enhancements and Extended Detection and Response (XDR). Kotaro has a bachelor of science degree in information and computer science.
 Koshi Oyama, Incident Response Investigator
Koshi Oyama, Incident Response Investigator
Koshi is an IR Analyst with the Cybereason Security Services team. He previously worked as a CSIRT of a large telecom company and is now working at Cybereason to help customers handle, investigate and recover from cybersecurity incidents.
APPENDICES | Target Service(s)
|
Service Name
|
|
##WID
|
|
AcronisAgent
|
|
AcrSch2Svc
|
|
apache24
|
|
ARSM
|
|
avpsus
|
|
backup
|
|
BackupExecAgentAccelerator
|
|
BackupExecAgentBrowser
|
|
BackupExecDiveciMediaService.
|
|
BackupExecJobEngine
|
|
BackupExecManagementService
|
|
BackupExecRPCService
|
|
BackupExecVSSProvider
|
|
bedbg
|
|
BMR Boot Service
|
|
CAARCUpdateSvc
|
|
CASAD2DWebSvc
|
|
ccSetMgr
|
|
Culserver
|
|
dbeng
|
|
dbsrv12
|
|
DefWatch
|
|
EPSecurityService
|
|
EraserSvc11710
|
|
Exchange
|
|
FCS
|
|
FishbowlMySQL
|
|
Intuit
|
|
Intuit.QuickBooks.FCS
|
|
macmnsvc
|
|
McAfeeDLPAgentService
|
|
McTaskManager
|
|
memtas
|
|
mepocs
|
|
mfewc
|
|
MSExchange
|
|
MSExchange$
|
|
msftesql
|
|
msmdsrv
|
|
MSSQL
|
|
MSSQL$
|
|
MSSQL$KAV_CS_ADMIN_KIT
|
|
MSSQL$MICROSOFT
|
|
MSSQL$MICROSOFT##SSEE
|
|
MSSQL$SBSMONITORING
|
|
MSSQL$SHAREPOINT
|
|
MSSQL$VEEAMSQL2012
|
|
MSSQLFDLauncher$SBSMONITORING
|
|
MSSQLFDLauncher$TPSAMA
|
|
MSSQLServerADHelper100
|
|
MVArmor
|
|
MVarmor64
|
|
mysql57
|
|
MySQL57
|
|
NetBackup BMR MTFTP Service
|
|
PDVFSService
|
|
QBCFMonitorService
|
|
QBFCService
|
|
QBIDPService
|
|
QBVSS
|
|
QLADHLP
|
|
QuickBooks
|
|
RTVscan
|
|
SavRoam
|
|
SavRoam
|
|
SAVService
|
|
sophos
|
|
Sophos AutoUpdate Service
|
|
Sophos Device Control Service
|
|
Sophos System Protection Service
|
|
sql
|
|
sqladhlp
|
|
sqlagent
|
|
SQLAgent$ECWDB2
|
|
SQLAgent$KAV_CS_ADMIN_KIT
|
|
SQLAgent$PROFXENGAGEMENT
|
|
SQLAgent$SBSMONITORING
|
|
SQLAgent$SHAREPOINT
|
|
SQLAgent$SOPHOS
|
|
SQLAgent$SYSTEM_BGC
|
|
SQLAgent$VEEAMSQL2012
|
|
sqlbrowser
|
|
SQLBrowser
|
|
Sqlservr
|
|
SQLWriter
|
|
stc_raw_agent
|
|
svc$
|
|
Symantec System Recovery
|
|
tomcat6
|
|
veeam
|
|
VeeamDeploymentService
|
|
VeeamNFSSvc
|
|
VeeamTransportSvc
|
|
vmware
|
|
vmware-converter
|
|
VSNAPVSS
|
|
vss
|
|
vtMgr
|
|
WSBExchange
|
|
YooBackup
|
|
YooIT
|
|
zhudongfangyu
|
|
Zoolz Service
|
Target Process(es)
|
Process Name
|
|
360Doctor
|
|
360Se
|
|
acwebbrowser
|
|
ADExplorer
|
|
ADExplorer64
|
|
ADExplorer64a
|
|
Adobe
|
|
AdobeCollabSync
|
|
AdobeIPCBroker
|
|
agntsvc
|
|
AutodeskDesktopApp
|
|
Autoruns
|
|
Autoruns64
|
|
Autoruns64a
|
|
Autorunsc
|
|
Autorunsc64
|
|
Autorunsc64a
|
|
avz
|
|
axlbridge
|
|
bedbh
|
|
benetns
|
|
bengien
|
|
beserver
|
|
BrCcUxSys
|
|
CagService
|
|
calc
|
|
Cloud
|
|
CoreSync
|
|
Creative
|
|
Culture
|
|
dbeng50
|
|
dbsnmp
|
|
Defwatch
|
|
DellSystemDetect
|
|
dumpcap
|
|
encsvc
|
|
EnterpriseClient
|
|
excel
|
|
fbguard
|
|
fbserver
|
|
fdhost
|
|
fdlauncher
|
|
firefox
|
|
GDscan
|
|
GlassWire
|
|
GWCtlSrv
|
|
Helper
|
|
httpd
|
|
infopath
|
|
InputPersonalization
|
|
isqlplussvc
|
|
j0gnjko1
|
|
java
|
|
koaly-exp-engine-service
|
|
msaccess
|
|
mspub
|
|
mydesktopqos
|
|
mydesktopservice
|
|
mysqld
|
|
node
|
|
notepad
|
|
notepad++
|
|
ocautoupds
|
|
ocomm
|
|
ocssd
|
|
onedrive
|
|
onenote
|
|
ONENOTEMwsa_service
|
|
oracle
|
|
outlook
|
|
powerpnt
|
|
ProcessHacker
|
|
Procexp
|
|
Procexp64
|
|
procexp64a
|
|
procmon
|
|
procmon64
|
|
procmon64a
|
|
pvlsvr
|
|
QBDBMgr
|
|
QBDBMgrN
|
|
QBIDPService
|
|
qbupdate
|
|
QBW32
|
|
Raccine
|
|
Raccine_x86
|
|
RaccineElevatedCfg
|
|
RaccineSettings
|
|
RAgui
|
|
raw_agent_svc
|
|
rCtrlCntr
|
|
RdrCEF
|
|
RTVscan
|
|
sam
|
|
Service
|
|
SimplyConnectionManager
|
|
SimplySystemTrayIcon
|
|
sqbcoreservice
|
|
sqlbrowser
|
|
sqlmangr
|
|
Sqlservr
|
|
Ssms
|
|
steam
|
|
supervise
|
|
sync
|
|
synctime
|
|
Sysmon
|
|
Sysmon64
|
|
SystemExplorer
|
|
SystemExplorerService
|
|
SystemExplorerService64
|
|
taskbar
|
|
tbirdconfig
|
|
tcpview
|
|
tcpview64
|
|
tcpview64a
|
|
tdsskiller
|
|
TeamViewer
|
|
TeamViewer_Service
|
|
thebat
|
|
thunderbird
|
|
TitanV
|
|
tomcat6
|
|
Totalcmd
|
|
Totalcmd64
|
|
tv_w32
|
|
tv_x6
|
|
VeeamDeploymentSvc
|
|
visio
|
|
vsnapvss
|
|
vss
|
|
vxmon
|
|
wdswfsafe
|
|
winword
|
|
WireShark
|
|
wordpad
|
|
worker
|
|
wuauclt
|
|
wxServer
|
|
wxServerView
|
|
xfssvccon
|
|
ZhuDongFangYu
|
Exclusion List | File Extensions
|
File Extension
|
|
adv
|
|
ani
|
|
bin
|
|
cmd
|
|
com
|
|
cur
|
|
deskthemepack
|
|
diagcab
|
|
diagcfg
|
|
diagpkg
|
|
dll
|
|
DLL
|
|
drv
|
|
exe
|
|
EXE
|
|
hlp
|
|
hta
|
|
icl
|
|
icns
|
|
ico
|
|
ics
|
|
idx
|
|
key
|
|
lnk
|
|
lock
|
|
mod
|
|
mpa
|
|
msc
|
|
msp
|
|
msstyles
|
|
msi
|
|
msu
|
|
nls
|
|
nomedia
|
|
ocx
|
|
pdb
|
|
pl
|
|
prf
|
|
ps1
|
|
rom
|
|
rtp
|
|
scr
|
|
search-ms
|
|
shs
|
|
spl
|
|
sys
|
|
theme
|
|
themepack
|
|
wpx
|
Files
|
File Name
|
|
autorun.inf
|
|
boot.ini
|
|
bootfont.bin
|
|
bootsect.bak
|
|
d3d9caps.dat
|
|
desktop.ini
|
|
GDIPFONTCACHEV1.DAT
|
|
hard.txt
|
|
HARDBIT.jpg
|
|
Help_me_for_Decrypt.hta
|
|
How To Restore Your Files.txt
|
|
iconcache
|
|
ntldr
|
|
ntuser.dat
|
|
ntuser.ini
|
|
thumbs.db
|
































 Kotaro Ogino, CTI Analyst
Kotaro Ogino, CTI Analyst Koshi Oyama, Incident Response Investigator
Koshi Oyama, Incident Response Investigator
