
Threat Hunting: From LOLBins to Your Crown Jewels
In certain combinations, some chains of behavior represent an advantage to an attacker - your team must be able to differentiate between benign use vs. the abuse of legitimate tools and processes...

David Bisson
Cybercrime cost the American public over $4 billion in reported losses over the course of 2020, according to the FBI. In its Internet Crime Report 2020, the FBI’s Internet Crime Complaint Center (IC3) revealed that it had received 791,790 complaints of digital crime in 2020.
Those complaints represented a 69% increase over 2019, with reported losses for the year estimated at $4.1 billion. Sam Curry, CSO at Cybereason, suspected that those reported losses likely represent just a fraction of what the American public experienced in 2020.
“The FBI’s 2020 Internet Crime Report is a humbling reminder for the entire security industry of how widespread Internet crimes have become. The FBI’s estimate of more than $4 billion in losses from cybercrime should send shock waves through the industry” Curry explained. “However, the losses are likely 400-500 percent higher and exceed $20-$25 billion because tens of thousands of consumers and businesses that were victimized in the past year didn’t report the crimes against them.”
Several threats stood out in the IC3 report. One of those was the incessant stream of scams and fraud attempts that leveraged COVID-19 as a lure in order to target both businesses and individuals. Indeed, the IC3 revealed that it had received 28,500 digital crime complaints associated with the pandemic during the year.
Many of those fraud attempts sought to capitalize on the attention surrounding the Coronavirus Aid, Relief and Economic Security Act (CARES Act). This commonly took the form of digital fraudsters trying to collect unemployment insurance benefits in the name of their victims.
The IC3 elaborated on one such campaign of unemployment insurance fraud in its report:
Complaints have been filed from citizens in several states describing fraudulently submitted online unemployment insurance claims using their identities. Many victims of this identity theft scheme did not know they had been targeted until they attempted to file their own legitimate claim for unemployment insurance benefits. At that time, they received a notification from the state unemployment insurance agency, received an IRS Form 1099-G showing the benefits collected from unemployment insurance or were notified by their employer that a claim had been filed while the victim is still employed.
Other times, attackers misused people’s identities in an attempt to steal personal information so that they could apply for loans or grants. Curry wasn’t surprised that digital attackers developed so many ways to prey upon the pandemic. He also didn’t hold back on what he thought about those malicious actors.
“COVID-19 related scams were naturally a popular theme for cyber criminals,” he pointed out. “Direct threats to hospitals, pharma and research companies should be declared acts of war as it is unconscionable for these profiteers to be disrupting the development and distribution of vaccines.”
Another threat that stood out in the IC3 report was ransomware. Over the course of 2020, the IC3 received 2,474 complaints of ransomware. It estimated the combined losses of those attacks at $29.1 million, though the total cost of ransomware attacks for the year was likely much higher.
Curry agreed, but stated that “the FBI measured ransomware losses strangely. I’d like more data, as $29 million is pathetically small, and we know it is much higher. Because of the popularity of ransomware attacks, it’s safe to say there were billions in losses in 2020. I am left to wonder if people who are paying ransoms aren’t reporting this to the FBI since they don’t encourage paying ransoms to threat actors. There is likely a bigger story being missed about crime being hidden by reporting practices.”
Yonatan Striem-Amit, CTO and co-founder of Cybereason, explained that the SolarWinds attack represents an escalation of a strategic advantage that malicious actors have enjoyed in the digital space for years if not decades.
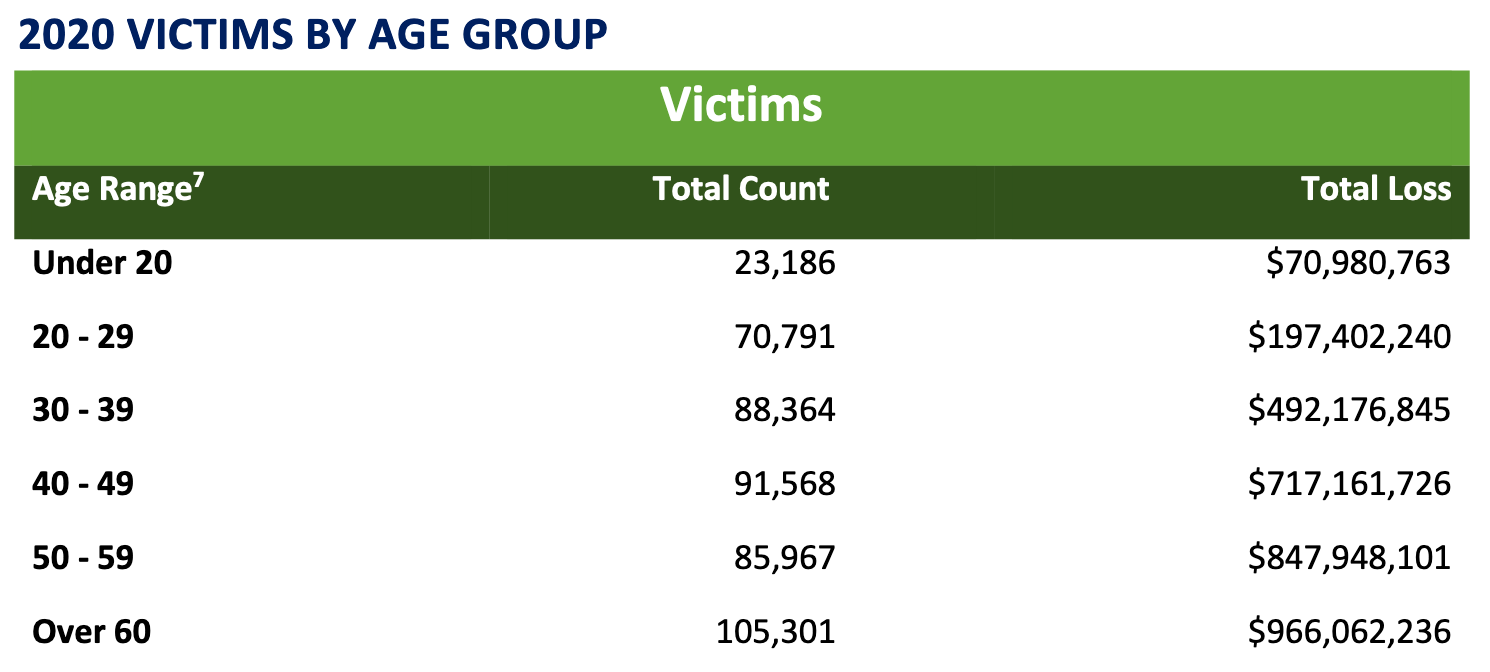 The 2020 Internet Crime Report, page 16
The 2020 Internet Crime Report, page 16
According to Curry, those statistics reflect the true nature of the digital attackers themselves.
“At the end of the day, threat actors are profiteers at heart. They are indiscriminate in the businesses and consumers they attack if they can make money,” Curry said. “They will prey on the weakest links in our global ecosystem, and because consumers and many small businesses have less robust security architecture in place, they stand to lose the most.”
IC3 is well aware of this fact. That’s part of the reason why the FBI partnered with the Department of Justice to create the Elder Justice Initiative. More information on how the two entities are working to defend seniors against financial fraud and scams is available here.
The IC3 report highlights the need for organizations to defend themselves against a growing array of digital threats and malicious actors. One of the ways they can do this is by strengthening their threat detection capabilities with crucial insight into Indicators of Behavior (IOBs). With that intelligence, they can quickly spot and respond to an attack—even if the FBI or anyone else hasn’t seen it before. All it takes is the right solution.
 David Bisson is an information security writer and security junkie. He's a contributing editor to IBM's Security Intelligence and Tripwire's The State of Security Blog, and he's a contributing writer for Bora.
David Bisson is an information security writer and security junkie. He's a contributing editor to IBM's Security Intelligence and Tripwire's The State of Security Blog, and he's a contributing writer for Bora.
He also regularly produces written content for Zix and a number of other companies in the digital security space.

David Bisson is an information security writer and security junkie. He's a contributing editor to IBM's Security Intelligence and Tripwire's The State of Security Blog, and he's a contributing writer for Bora. He also regularly produces written content for Zix and a number of other companies in the digital security space.
All Posts by David Bisson
In certain combinations, some chains of behavior represent an advantage to an attacker - your team must be able to differentiate between benign use vs. the abuse of legitimate tools and processes...

In this Threat Analysis report, Cybereason investigates the Ransomware-as-a-Service (RaaS) known as Beast and how to defend against it through the Cybereason Defense Platform.

In certain combinations, some chains of behavior represent an advantage to an attacker - your team must be able to differentiate between benign use vs. the abuse of legitimate tools and processes...

In this Threat Analysis report, Cybereason investigates the Ransomware-as-a-Service (RaaS) known as Beast and how to defend against it through the Cybereason Defense Platform.
Get the latest research, expert insights, and security industry news.
Subscribe