The modern security toolkit is varied by necessity, with different tools required to effectively perform different tasks. As part of a successful defense-in-depth strategy, often deep-dive analysis is needed to fully understand and respond to serious events and data breaches.
While not needed for every event and every investigation, Digital Forensics and Incident Response (DFIR) is absolutely essential for infosec teams dealing with sophisticated cyber adversaries.
Detection, response, and investigation are not always straightforward and things are seldom what they appear to be at first glance. Often a deeper dive into evidence is needed to extract the full, unobstructed truth.
In the same way that forensic clues from physical crime scenes can be used to build a case either to convict or exonerate, digital forensic techniques are useful to suss out the truth relative to digital crimes, including cyberattacks and data breaches.
Every interaction on a device or endpoint leaves a trace that can be examined after the fact, which is fantastic news for investigators (and somewhat alarming to the non-tech savvy and would-be perpetrators).
DFIR is incredibly useful to create a full, clear, and accurate picture of what took place leading up to the incident, answering relevant questions like: Who was patient zero? What was the full scope and impact of the attack? What steps were taken by adversaries while in an environment? And most importantly, how do we comprehensively respond and recover?
Endpoint Detection and Response (EDR) and DFIR are complementary technologies. In the physical world of investigation, EDR can be compared to surveillance, where bad actors can be studied both live and through footage from the past to deconstruct an incident. In the same way that surveillance has limitations when analyzing a crime scene, EDR without DFIR can be limited in digital investigations.
Law enforcement must dive deep into crime scene evidence to lift fingerprints, analyze DNA samples, and study the scene in a granular way. DFIR accomplishes the same goals through thorough analysis in the digital space and is especially useful in the event of a data breach or serious incident.
Good DFIR can be difficult to find in today’s crowded security marketplace. For practitioners, implementing DFIR can be difficult due to the massive skills gap and workforce shortages in cybersecurity, with many reports indicating roughly 3.5 million unfilled positions globally.
With Tier I expertise hard to find and retain, many organizations find it next to impossible to fill Tier III incident response roles. The Tier III analysts tend to be the most qualified, having acquired a particular set of skills over the years through a battle-tested career.
Even if staffing requirements were fully met to be able to introduce or enhance DFIR, good DFIR capabilities are not a given from vendors, with most opting to provide DFIR through outside services rather than enabling an internal IR team with tools.
Most DFIR tools are siloed and operate independently of an EDR solution, complicating the deployment and investigation. Teams may need to deploy as many as a dozen individual IR tools for a given investigation, with no way to centralize investigation results. This slows the investigation process rather than streamlines it.
Given this reality, investigations can take weeks for a single incident. The first 72 hours are absolutely critical, and IR teams should strive to make meaningful steps in the investigation within the first 3 days of the response.
There is a common misperception that if you have EPP/EDR in place, DFIR is unwieldy and unnecessary. The reality is that EDR and DFIR are related, complementary technologies that are meant to sit side-by-side.
DFIR capabilities allow IR teams to go deep, be surgical in their collection of evidence, and respond thoroughly in ways that are beyond the scope of a fast-moving EDR. Only together can these technologies create a clear picture of what took place in an IT environment and permanently remediate.
Cybereason DFIR unleashes the full potential of the MalOp
Not only do we value the role forensics has to play in modern cyber investigations, but we have also gone to great lengths to automate DFIR where possible - something historically difficult to accomplish given the tedious nature of forensic investigations.
Cybereason DFIR is still all about the MalOp™ (malicious operation), a fully contextualized view of a detected threat with the root cause, timeline, scope, outbound connections, tools used by attackers, and one-click response, displayed in a highly digestible view for security analysts. The MalOp Detection Engine detangles the knots of what happened and all the steps taken by an adversary while active in their intrusion.
Cybereason DFIR feeds a treasure trove of forensic data to the MalOp Detection Engine to create an even more contextualized, enriched, and correlated view of the attack. This approach simplifies DFIR for less mature teams without in-house Tier III expertise, allowing more junior analysts to take meaningful response actions using forensic data through the intuitive MalOp™ UI view.
Feeding forensic data through the MalOp™ Detection Engine unleashes the full potential of the MalOp:
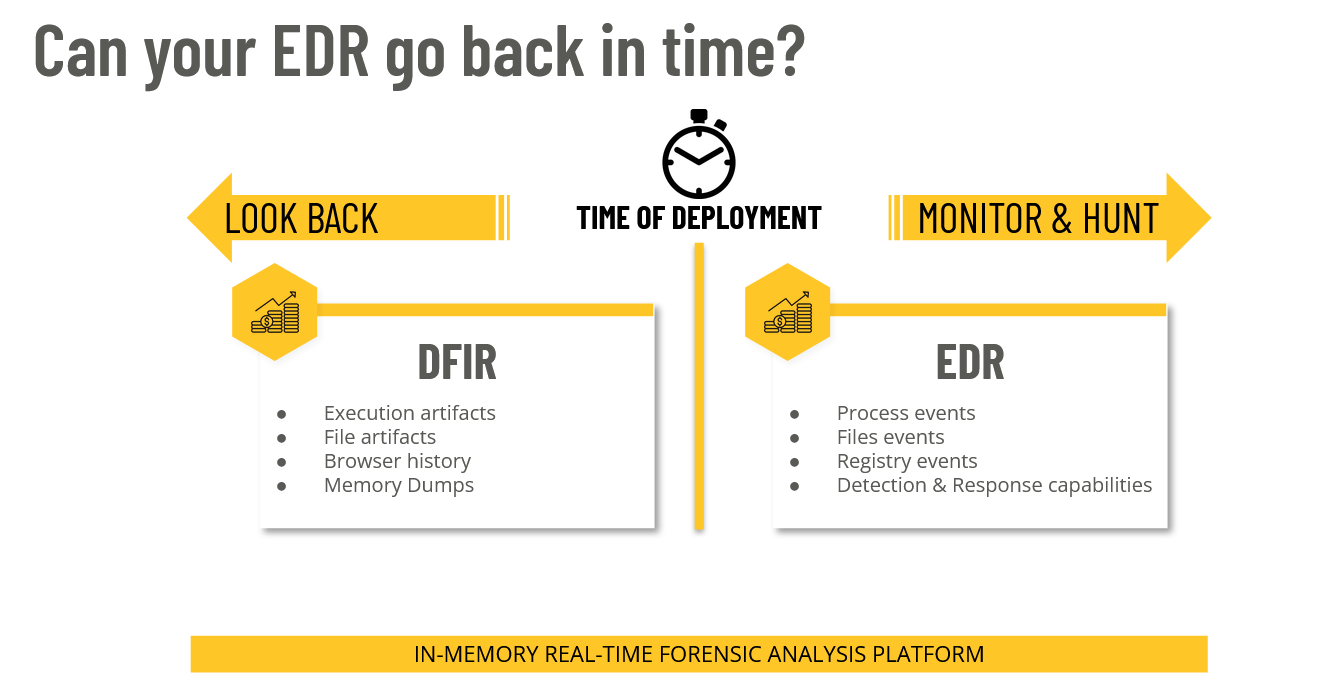
Analysts can also leverage this forensic data to go back in time. Every digital interaction leaves traces that can be examined after the fact to better understand what took place before a team had visibility into the environment.
In theory, analysts can view forensic artifacts on the disc and see a detailed forensic record that goes back to when a machine was unwrapped and plugged in for the first time, unless there was a wipe and reimage of that device.
Experts need expert tools
The granular nature of forensic investigations means that IR practitioners need more advanced tools to collect and splice data for investigations. Many common EPP/EDR solutions are overly simplistic for DFIR, complicating investigations and leading to dead ends. Teams need tools that are suited for deep-dive analysis, which Cybereason provides through a single sensor and a single console.
Cybereason DFIR includes four primary components:
Live Forensics. IR teams are fully enabled to pull forensic data to enhance visibility and aid in the investigation. Analysts can benefit from memory dumps, artifact analysis (Strings, Registry artifacts, PreFetch, event logs, and many others) for low-level analysis. This is especially useful for post-mortem investigations where IR personnel might want to deep dive into the patient zero of a data breach and answer useful questions like - how did the intruder get in? What vulnerabilities led to the intrusion? What was the impact and path of the attacker? Are there new IOCs from this event we can search against the enterprise? How was the malware or ransomware programmed to operate?
Live File Search. File analysis is a critical component of DFIR investigations. Cybereason allows teams to search for and analyze any file in the environment, without the need for prior collection. This file search capability extends to any file on any machine across the enterprise and can be searched for based on a wide range of criteria, including file name, file size, hash value, and other attributes. Collection and File Download can be performed after a positive search.
IR Tools Deployment. There are many DFIR tools available to assist with investigations. Many of these DFIR tools are licensed and built by software companies, but others are open source and limited in scope — more of a widget than a software solution. DFIR investigations may require dozens of different tools to be deployed to the impacted machines within the scope of the investigation, and deployment can be a massive roadblock. With time being of the essence, Cybereason streamlines the deployment of adjacent IR tools using the Cybereason sensor. Teams can push out as many tools as needed quickly and efficiently, and centralize investigation results within the Cybereason platform. This capability is API-based and open to nearly any commonly used IR or forensic investigation tool, allowing for maximum flexibility.
ExpressIR. IR Partners and MSSP organizations routinely perform breach recovery for victim organizations that contract their assistance. Deploying the investigation environment and all of the necessary tools can be time-consuming and tedious. Cybereason ExpressIR enables IR partners to rapidly deploy a pre-provisioned incident response environment to the victim organization in a matter of hours, meaning that our partners can go from the initial scoping call with the breached organization to investigation in the same day - a massive boost in efficiency and improved mean-time-to-response (MTTR).
Technology + People + Processes
The technology to perform successful DFIR is obviously important, but on par in importance is the knowledge and the processes that guide forensic investigations. DFIR skills are specialized and not widely available, with IR personnel extremely difficult to recruit and retain.
Investigative know-how is gained after years of experience, and the tribal knowledge of the community is often undocumented and passed along informally within an organization. Many teams lack the internal maturity, skills, and processes for DFIR and rely heavily on outside partners to meet their needs.
Cybereason boasts industry-leading IR talent, with many of the brightest minds in the space fueling our engineering and services. In the event of a breach that requires post-mortem analysis, teams that feel outmatched and outclassed by adversaries can fully recover, investigate, augment staffing, and implement processes based on the lessons learned in the investigation to avoid a breach through similar vectors moving forward.
Cybereason is the de facto DFIR partner via our massive advantages with the technology. Rather than a neglected area of our product and services portfolio, DFIR is a cornerstone to our strategy and we have built an EDR platform that enables DFIR boosted by services to reduce mean-time-to-response and fully recover from a data breach.
Cybereason is dedicated to teaming with defenders in both the public and private sectors to end cyber attacks from endpoints to the enterprise to everywhere. Learn more about the Cybereason DFIR advantage here or schedule a demo today to learn how your organization can benefit from an operation-centric approach to security.
