Many different security frameworks exist in the world today: ISO-17799, it’s successor ISO-27000, Cobit, NIST, and others. The latest introduction, the MITRE ATT&CK framework, is giving a new perspective on the tactical needs of security operations.
Developing a solid, closed-loop defense strategy is challenging. Prior to MITRE ATT&CK, most frameworks were designed as checklists of what defenses should be in place. They provide useful guidance, but lack the dynamism of real-world security. Beyond frameworks, it’s hard to engage in defense improvement or determine quantitative, consistent results on your defense process.
Even red team activities lack a unified language to describe what they do or how they do it with consistency. Without a shared vocabulary, their results are often murky and quantitatively immeasurable. The only other way to measure your defense is to catch real world attacks - a risky and ineffective defense strategy.
In our white paper, we share five steps necessary for creating a defensive gap assessment plan with MITRE ATT&CK. Combining TTPs with adversary emulation plans, this white paper provides the background to building threat hunting and red teaming programs based on the MITRE ATT&CK framework, with trackable, actionable results. For anyone looking to delve deeper into this aspect of MITRE ATT&CK, it's important to outline a the basic principles the white paper is built upon.
Beyond Tactics, Techniques, and Procedures
According to MITRE- “MITRE ATT&CK™ is a globally-accessible knowledge base of adversary tactics and techniques based on real-world observations.”
While this is true, the framework is much more than that. It provides the MITRE ATT&CK matrix of techniques, tactics, and procedures, as well as adversary emulation planning guidelines and adversary groups. Adversary emulation planning guidelines let your security team construct a real-world attack scenario combined with techniques, tactics, and procedures, so you can test and identify key vulnerabilities in your enterprise infrastructure.
Many organizations prioritize evaluating techniques, tactics, and procedures in their security infrastructure. This is a fundamental element to creating an effective security strategy, but it is simply one piece of a bigger puzzle. Adversary emulation planning guidelines are critical to build a closed-loop defense strategy, and adversary groups give you insight to pinpoint exactly how you should target your defense.
Choosing What Adversary Groups to Defend Against
The groups section of MITRE ATT&CK provides intelligence on almost 80 identified attacker groups coupled with known techniques used by each group and commonly targeted vertical markets and organizations. You should select specific groups you want to target with your emulation plans, starting with the groups that pose the most immediate threat to your organization. Prevent and cut the noise your team has to deal with by addressing individual groups more likely to attack your organization. For example, a healthcare organization would likely start with a group like Deep Panda (MITRE ATT&CK ID G0009), as they are well-known for their intrusion into healthcare company Anthem (see Table 1). When you select a specific group, the MITRE ATT&CK site lets you drill down into a list of the groups common techniques by identifier and a list of their commonly used software and malware.
Table 1: Example adversary groups for particular vertical markets and organization types.
We believe it is crucial to take a hard look at your enterprise and identify key adversary groups for you to focus your defense. While it would be optimal to create AEPs for all of the groups identified in the MITRE ATT&CK framework, the best use of your resources is to focus on the groups that target your organization or data. If your organization has the resources to manage AEPs for all the adversary groups, that’s ideal, but not easily achieved. In maintaining a good defense, it’s crucial to reduce manual effort while maintaining visibility.
Learning More About the Five Stages of a Closed-loop Security System
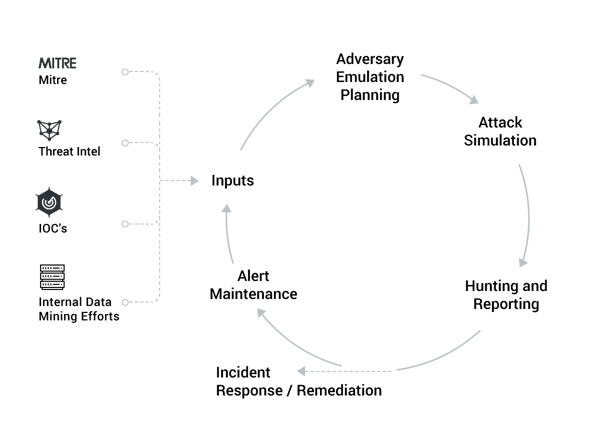
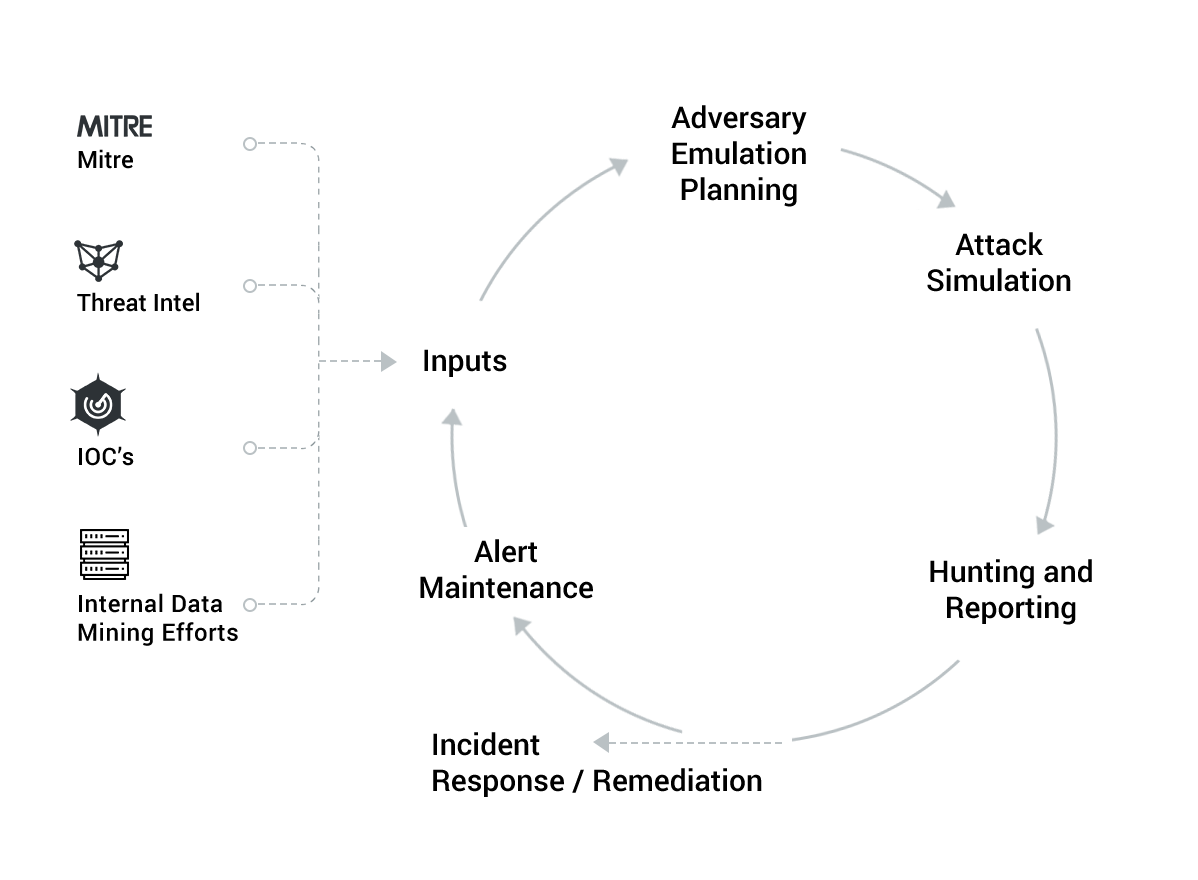
Our white paper gives you detailed information on all five stages, including Inputs, Adversary Emulation Planning, Attack Simulation, Hunting and Reporting, and Alert Maintenance.
Step 1: Inputs
When it comes to creating an effective improvement cycle for hunting, alerting, and response, you should always have more inputs than solely MITRE ATT&CK. Additional, more traditional feeds can inform the cycle with data for more effective decisions on alerting and defenses. This can include threat intel, indicators of compromise, and data mining efforts.
Step 2: Adversary Emulation Planning
It’s crucial to construct AEPs for each of the adversary groups most likely to attack your enterprise. It’s best to focus on the groups that target your organization type or data. You should refresh AEPs at least annually and track their status in a table or other tool.
Step 3: Attack Simulation
Use internal or external red team resources to construct attack simulations that follow the emulation plans in both technology and process as closely as possible. It is vital that your red team exercises simulate actual attack resources like external command and control systems, proper infiltration and exploitation, and data exfiltration. If you don’t execute the steps of the adversary emulation plan, it can mean missed steps in an actual attack, which can have extreme consequences.
Step 4: Hunting and Reporting
At a minimum, red teams should use the advanced emulation plans and TTPs for execution and should actively report on the success of their activities. Your evaluation should inevitably result in tooling improvements. Each simulation should be quantitatively scored, and reports should include descriptions of the executed attack plans, the results of the attacks, and the remediation steps you should take to close any gaps.
Step 5: Alert Maintenance
Construct a process and technology improvement plan based on the results and the TTPs identified during your red team activities. Process improvement plans should be flexible enough to incorporate the results of several simulations, as changes per simulation can significantly influence technology decisions. Improving your alerts stems from the quality of your reporting.
More than this, gain valuable example inputs, adversary emulation plans, attack simulations, hunting and reporting tables, and alert maintenance priorities as a solid basis to build your defense system.
Understand the connection between techniques, tactics, and procedures, advanced persistent threat groups, and adversary emulation planning guidelines to implement an integrated, effective security strategy targeted for your vertical. This process gives you valuable visibility into your system so you are able to build a closed-loop improvement cycle for your security operations.
To learn more about how to use MITRE ATT&CK to effectively improve your enterprise-level security, download our white paper today.
Download the Five Stages to Create a Strategic, Closed-loop Security Process with MITRE ATT&CK white paper.