Over the last few months, the Cybereason Nocturnus Team has been tracking the activity around the RansomEXX ransomware. It has been active since 2018, but came to fame in 2020 in attacks on major organizations such as the Texas Department of Transportation. RansomEXX started as a Windows variant, but a Linux variant was discovered earlier this year.
Key Findings
Human-operated targeted attacks: RansomEXX is being used as a part of multi-staged human-operated attacks targeting various government related entities and tech companies. It is being delivered as a secondary payload after initial compromise of the targeted network.
Disables security products: The Windows variant has a functionality that was seen before in other ransomware, disabling various security products for a smooth execution on the infected machine.
Multi-Platform: RansomEXX started solely as a Windows variant, but later a Linux variant was added to the arsenal, sharing similarities with its predecessor.
Fileless ransomware: RansomEXX is usually delivered as a secondary in-memory payload without ever touching the disk, which makes it harder to detect.
Detected and prevented: The Cybereason Defense Platform fully detects and prevents the RansomEXX ransomware.
Background
TheRansomEXX family, also known as Defray777 and Ransom X, runs as a solely in-memory payload that is not dropped to disk, making it highly evasive. RansomEXX was involved in three major attacks in 2020 against Texas TxDOT in May of 2020, against Konica Minolta in the end of July, and against Brazil's court system in the beginning of November.
In addition, last December RansomEXX operators published stolen credentials from Embraer, one of the largest aircraft makers in the world, on its own leaks website as part of the ongoing double extortion trend.
In mid 2020, a Linux variant of RansomEXX emerged. This variant, despite sharing similarities with the Windows variant, is simpler than its predecessor and lacks many features such as disabling security software and command and control communication. There are decryptors for both variants, and the threat actors send paying victims a private key to decode their files.
RansomEXX Analysis
This analysis focuses on the Windows variant of RansomEXX, which can be classified as fileless malware because it is reflectively loaded and executed in memory without touching the disk. Analysis of this sample reveals that it is partially obfuscated but includes indicative information such as the “ransome.exx” string that can be seen hard coded in the binary:
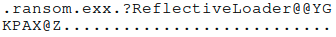
ransom.exx string hardcoded in the binary
Upon execution, RansomEXX starts decrypting some strings necessary for its operation:
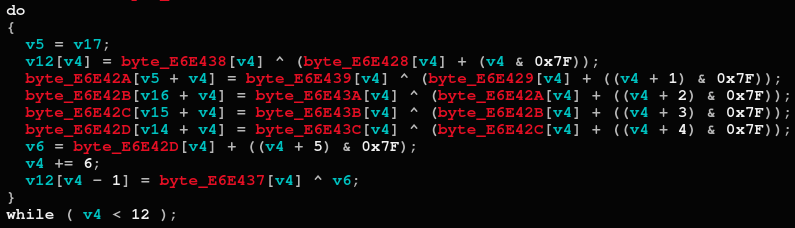
RansomEXX’s strings decryption routine
The mutex the malware creates is generated from the GUID of the infected machine:

The GUID generated on the infected machine
The decrypted strings at this point include mainly logs:
Decrypted logging string
RansomEXX spawns a separate thread in the background to handle the logging process.
When debugging the sample, the logs themselves can be seen in the console:
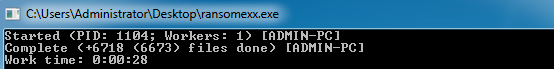
Logging as seen in the command line
The malware then continues with terminating processes and system services that may interfere with the execution, but excludes those that are relevant for its execution:
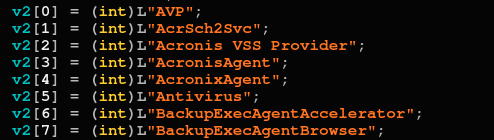
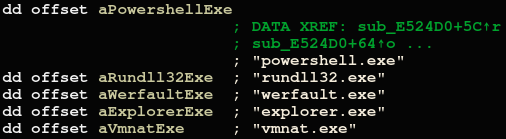
Some of the terminated services as well as processes excluded from termination
Cybereason detects the execution of RansomEXX together with the below listed commands that are executed post-encryption. These commands’ role is to prevent the victim from restoring their system by deleting backups, Windows error recovery etc. Cybereason also detects this malicious usage of Windows utilities:
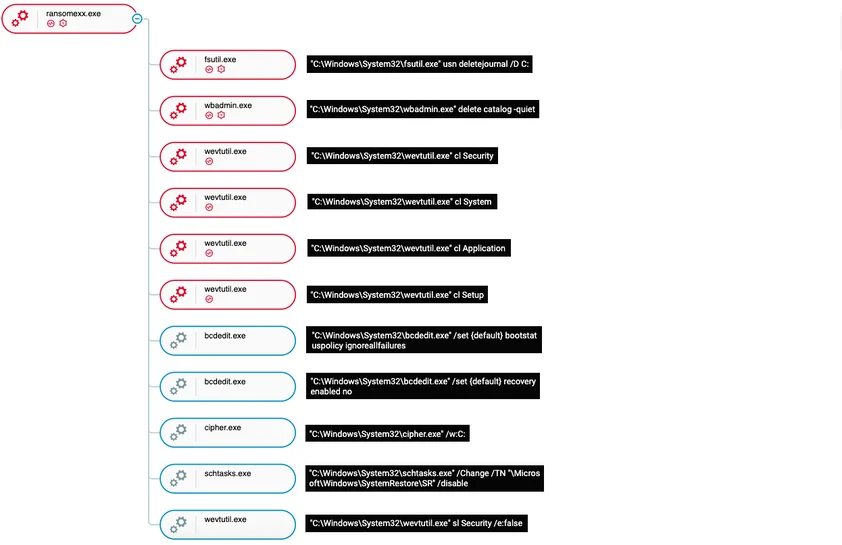
RansomEXX’s attack tree as seen in the Cybereason Defense Platform
The depicted above commands are as follows:
|
Command
|
Action
|
|
"C:\Windows\System32\fsutil.exe" usn deletejournal /D C:
|
fsutil.exe deletes the Update Sequence Number journal
|
|
"C:\Windows\System32\wbadmin.exe" delete catalog -quiet
|
wbadmin.exe deletes the backup catalog
|
"C:\Windows\System32\wevtutil.exe" cl Setup
"C:\Windows\System32\wevtutil.exe" cl System
"C:\Windows\System32\wevtutil.exe" cl Application
"C:\Windows\System32\wevtutil.exe" cl Security |
wevtutil clears event logs
|
"C:\Windows\System32\bcdedit.exe" /set {default} bootstatuspolicy ignoreallfailures
"C:\Windows\System32\bcdedit.exe" /set {default} recoveryenabled no |
bcdedit disable recovery mode
|
|
"C:\Windows\System32\cipher.exe" /w:C:
|
cipher overwrites deleted data in drive C
|
|
"C:\Windows\System32\schtasks.exe" /Change /TN "\Microsoft\Windows\SystemRestore\SR" /disable
|
schtasks disables the system restore scheduled task
|
|
"C:\Windows\System32\wevtutil.exe" sl Security /e:false
|
wevtutil disables the security event logs
|
After preparation of the environment RansomEXX encrypted the files on the victim’s machine and the following note is left on the machine:
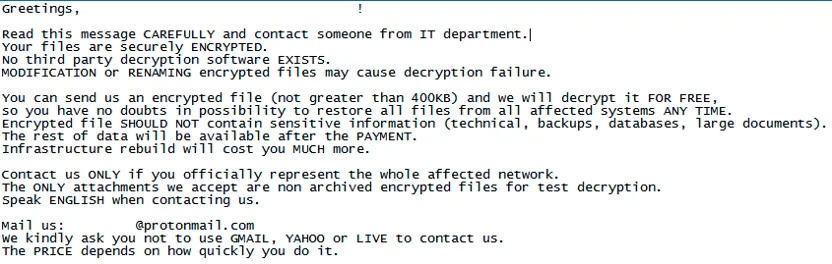
The ransom note left on the victim’s machine
The commands that disable file recovery and system restore after successfully encrypting the victim’s files, and can also be observed clearly in the sample’s code:
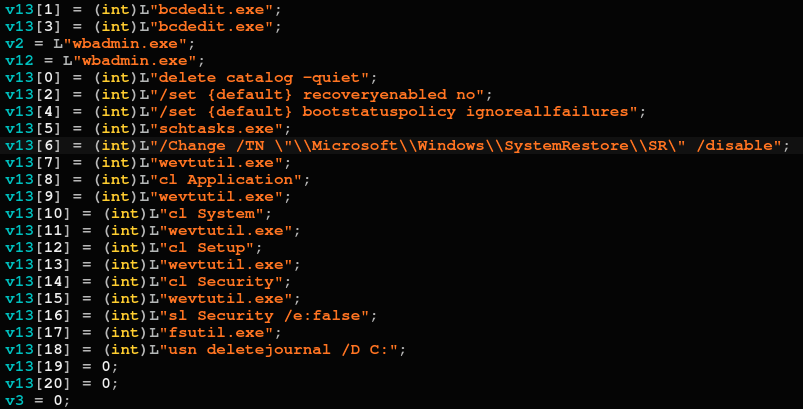
Part of the post-encryption commands in RansomEXX’s code
Cybereason Detection and Prevention
Cybereason detects the Windows utilities that are executed post-encryption as malicious and triggers a Malop(™) for all of them:
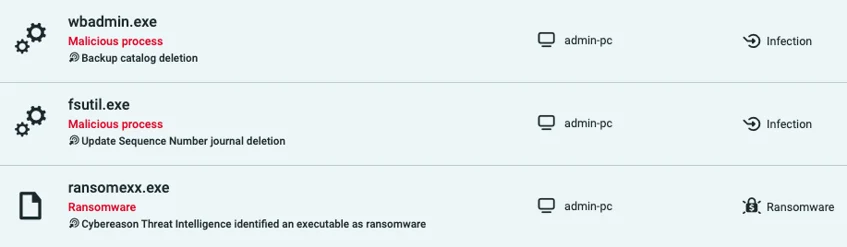
Detection of the ransomware and malicious uses of windows utilities by the Cybereason Defense Platform
Looking at the Malop that was triggered by fsutil, the evidence for malicious activity can be seen together with the suspicions mapped to the MITRE ATT&CK matrix:
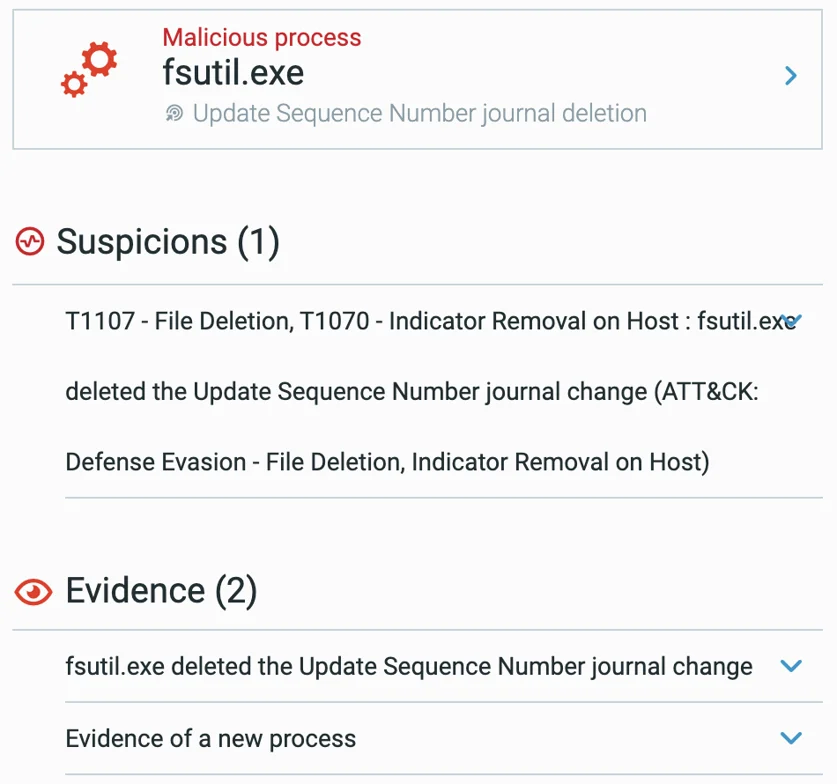
Suspicions and evidence triggered by fsutil
When Cybereason anti-ransomware prevention is turned on, the execution of the RansomEXX is prevented using the AI module:
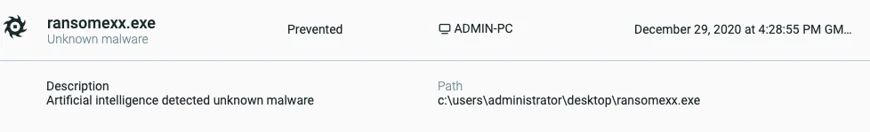
Execution prevention of RansomEXX by the Cybereason Defense Platform
Security Recommendations
• Enable the Anti-Ransomware Feature on Cybereason NGAV: Set Cybereason Anti-Ransomware protection mode to Prevent - more information for customers can be found here
• Enable Anti-Malware Feature on Cybereason NGAV: Set Cybereason Anti-Malware mode to Prevent and set the detection mode to Moderate and above - more information can be found here
• Keep Systems Fully Patched: Make sure your systems are patched in order to mitigate vulnerabilities
• Regularly Backup Files to a Remote Server: Restoring your files from a backup is the fastest way to regain access to your data
• Use Security Solutions: Protect your environment using organizational firewalls, proxies, web filtering, and mail filtering
• Indicator's of Compromise: Includes C2 Domains, IP addresses, Docx files SHA-1 hashes, and Msi files. Open the chatbot on the lower right-hand side of this blog to download your copy.
MITRE ATT&CK BREAKDOWN
Daniel Frank 
Daniel Frank is a senior Malware Researcher at Cybereason. Prior to Cybereason, Frank was a Malware Researcher in F5 Networks and RSA Security. His core roles as a Malware Researcher include researching emerging threats, reverse-engineering malware and developing security-driven code. Frank has a BSc degree in information systems.


















