
Cybereason XDR for Cloud Workloads: A New Approach to Cloud Security
Cybereason XDR for Cloud Workloads secures cloud workloads, containers and hosts at unparalleled speed and scale...

Cody Queen
Defenders around the world need innovative tools to stop sophisticated attacks. Cybereason is excited to announce Behavioral Execution Prevention (BEP), a new layer of NGAV defense designed to stop phishing attacks, zero-day attacks, and drive-by attacks.
BEP stops threats posed by malicious actors who use trusted operating system software and native processes to conduct malicious operations. BEP is able to stop malicious actors earlier in the kill chain and ensures trusted system resources are not exploited and used to conduct attacks.
Behavioral Execution Prevention leverages Endpoint Detection and Response (EDR) detections to generate preventative heuristics for the Cybereason NGAV suite. It is designed to identify anomalies as early as process creation, thus greatly reducing the attack surface.
Attackers frequently use legitimate operating system software or third-party software to deliver and spread malware. This abuse of legitimate software functions includes the execution of malicious payloads, launch of malicious droppers, download of macros, and obfuscation of data all designed to achieve persistence and exfiltrate data.
The bottom line is that these techniques allow attackers to move more quickly than before, making it more critical for organizations to block them earlier in the kill chain and stop attacks before they rise to the level of requiring human intervention.
Traditional antivirus tools often fail to identify attacks that originate from trusted and native processes. Behavioral Execution Prevention uses a sophisticated set of rules to prevent the abuse of legitimate software. BEP works by leveraging data patterns and rules to detect abnormalities in image metadata and names, command line commands, and process hierarchies to effectively stop attackers in their tracks.
Another powerful aspect of BEP is the ability to continue operating in the event the endpoint is disconnected from the platform, such as working offline. This ensures that malicious actors cannot take advantage of disrupted operations to launch complex attacks and overwhelm an organization's defenses.
For many years, signature-based antivirus tools dominated the cybersecurity market. This traditional approach was always flawed because once the attackers created new techniques and methods these AV tools immediately became outdated.
The market then moved to EDR. This technology was a vast improvement over traditional AV products but many solutions struggled to keep up with the evolving TTPs (Tactics, Techniques, and Procedures) of threat actors. In addition, traditional EDR tools detect threats already inside the machines and networks of organizations being attacked but don’t offer prevention capabilities.
NGAV solutions are the latest step in the evolution of prevention technologies. While not new, NGAV technology must remain ever-evolving to respond to dynamic threats that exist in the real world.
NGAV focuses on using artificial intelligence and machine learning to look for patterns of behavior and signatures of techniques that malicious actors use in order to block threats more quickly, especially the newest malware and ransomware, not yet known to the cybersecurity community:
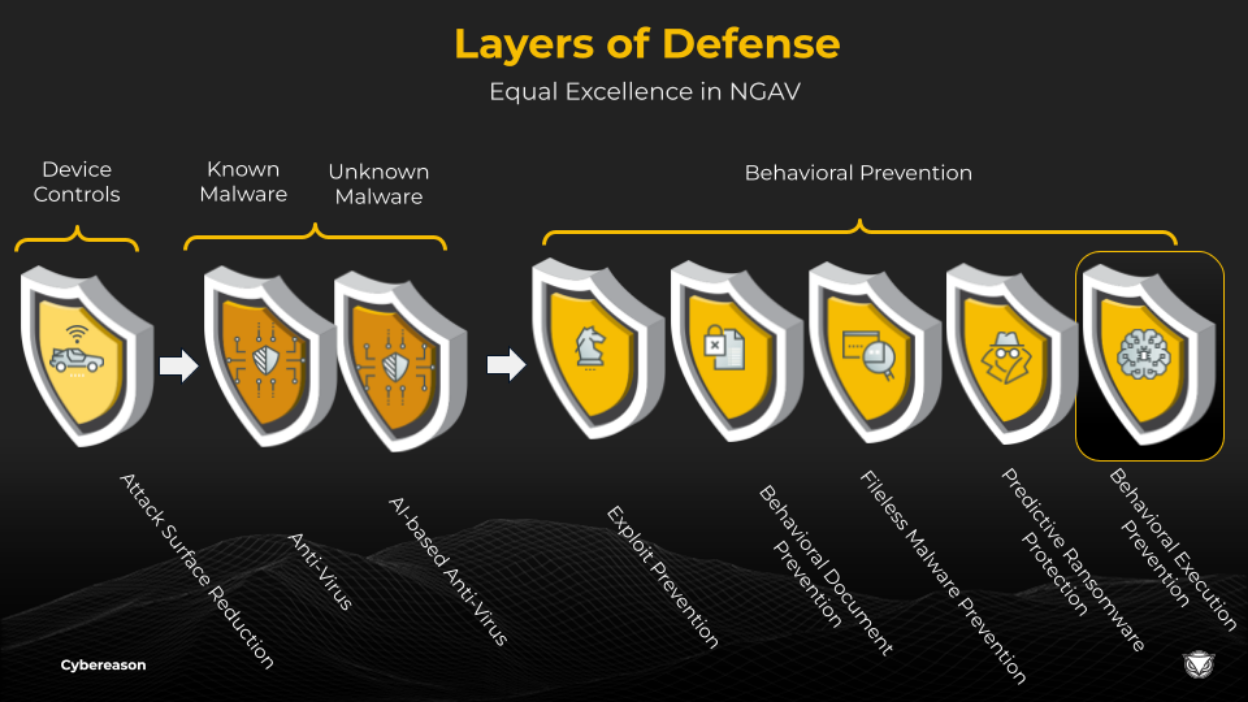 The Cybereason Layered Defense Approach
The Cybereason Layered Defense Approach
Behavioral Execution Prevention is designed to reduce the attack surface and decrease the time needed for Cybereason’s NGAV product to block the malicious activity, reducing the burden on security practitioners and allowing them to focus on the most complex and pressing problems they face.
This is why prevention is so powerful. Security analysts already have a difficult enough job to do without being distracted by alerts. Behavioral Execution Prevention is designed to empower these security professionals with tools to reduce the burden of an alert-centric and intervention-heavy NGAV solution.
If you are interested in learning more about this product and its capabilities, request a demo today. Cybereason is dedicated to teaming with defenders to end attacks on the endpoint, across the enterprise, to everywhere the battle is taking place.

Cody Queen is a Product Marketing Manager at Cybereason leading the go-to-market strategy for NGAV, endpoint protection and cloud workload security solutions. Before joining Cybereason, Cody led and supported product launches for Dell Technologies in their APEX Cloud and security business, primarily around managed data center services. He also brings over 10 years of experience in the public sector planning for, managing and responding to security threats against the United States.
All Posts by Cody Queen
Cybereason XDR for Cloud Workloads secures cloud workloads, containers and hosts at unparalleled speed and scale...

In this webinar we will hear from Cybereason CTO and co-founder Yonatan Striem-Amit about how threats are changing; Tim Amey, Field CTO about how Cybereason prevention layers stop malware in its tracks; and Cody Queen, Product Marketing Manager share the latest prevention tools developed by Cybereason to stop the most novel attack techniques...

Cybereason XDR for Cloud Workloads secures cloud workloads, containers and hosts at unparalleled speed and scale...

In this webinar we will hear from Cybereason CTO and co-founder Yonatan Striem-Amit about how threats are changing; Tim Amey, Field CTO about how Cybereason prevention layers stop malware in its tracks; and Cody Queen, Product Marketing Manager share the latest prevention tools developed by Cybereason to stop the most novel attack techniques...
Get the latest research, expert insights, and security industry news.
Subscribe